List of PlugIn IDs
The following plugin IDs have problems associated with them. Select the ID to review more detail.
Plugin id#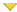 | # of issues | Plugin name | Severity |
|---|---|---|---|
| 47763 | 1 | iTunes < 9.2.1 'itpc:' Buffer Overflow Vulnerability (uncredentialed check) | High Severity problem(s) found |
| 47606 | 2 | D-Link DCC Protocol Security Bypass | High Severity problem(s) found |
| 45391 | 1 | iTunes < 9.1 Multiple Vulnerabilities (uncredentialed check) | High Severity problem(s) found |
| 44340 | 1 | CentOS Update Set | High Severity problem(s) found |
| 42411 | 2 | Microsoft Windows SMB Shares Unprivileged Access | High Severity problem(s) found |
| 41061 | 1 | iTunes < 9.0.1 PLS File Buffer Overflow (uncredentialed check) | High Severity problem(s) found |
| 40887 | 1 | MS09-050: Microsoft Windows SMB2 _Smb2ValidateProviderCallback() Vulnerability (975497) (uncredentialed check) | High Severity problem(s) found |
| 11522 | 1 | Linksys Router Default Password (admin) | High Severity problem(s) found |
| 53360 | 1 | PolarSSL Diffie-Hellman Key Exchange Security Bypass Vulnerability | Medium Severity problem(s) found |
| 51893 | 1 | OpenSSL SSL_OP_NETSCAPE_REUSE_CIPHER_CHANGE_BUG Ciphersuite Disabled Cipher Issue | Medium Severity problem(s) found |
| 51892 | 1 | OpenSSL SSL_OP_NETSCAPE_REUSE_CIPHER_CHANGE_BUG Ciphersuite Change Issue | Medium Severity problem(s) found |
| 51192 | 7 | SSL Certificate signed with an unknown Certificate Authority | Medium Severity problem(s) found |
| 45411 | 1 | SSL Certificate with Wrong Hostname | Medium Severity problem(s) found |
| 43156 | 1 | NTP ntpd Mode 7 Error Response Packet Loop Remote DoS | Medium Severity problem(s) found |
| 42873 | 3 | SSL Medium Strength Cipher Suites Supported | Medium Severity problem(s) found |
| 35291 | 1 | SSL Certificate Signed using Weak Hashing Algorithm | Medium Severity problem(s) found |
| 26928 | 2 | SSL Weak Cipher Suites Supported | Medium Severity problem(s) found |
| 26919 | 2 | Microsoft Windows SMB Guest Account Local User Access | Medium Severity problem(s) found |
| 20007 | 2 | SSL Version 2 (v2) Protocol Detection | Medium Severity problem(s) found |
| 12218 | 11 | mDNS Detection | Medium Severity problem(s) found |
| 12217 | 1 | DNS Server Cache Snooping Remote Information Disclosure | Medium Severity problem(s) found |
| 11213 | 1 | HTTP TRACE / TRACK Methods Allowed | Medium Severity problem(s) found |
| 10882 | 1 | SSH Protocol Version 1 Session Key Retrieval | Medium Severity problem(s) found |
| 10723 | 1 | LDAP Server NULL Bind Connection Information Disclosure | Medium Severity problem(s) found |
| 10722 | 1 | LDAP NULL BASE Search Access | Medium Severity problem(s) found |
| 10595 | 1 | DNS Server Zone Tranfer Information Disclosure (AXFR) | Medium Severity problem(s) found |
| 53335 | 3 | RPC portmapper (TCP) | Low Severity problem(s) found |
| 51891 | 4 | SSL Session Resume Supported | Low Severity problem(s) found |
| 50845 | 2 | OpenSSL Detection | Low Severity problem(s) found |
| 50686 | 4 | IP Forwarding Enabled | Low Severity problem(s) found |
| 47605 | 1 | D-link Click 'n Connect Daemon Detection | Low Severity problem(s) found |
| 46215 | 1 | Inconsistent Hostname and IP Address | Low Severity problem(s) found |
| 46212 | 1 | PVS Proxy Detection | Low Severity problem(s) found |
| 46180 | 1 | Additional DNS Hostnames | Low Severity problem(s) found |
| 45590 | 16 | Common Platform Enumeration (CPE) | Low Severity problem(s) found |
| 45433 | 1 | Memory Information (via DMI) | Low Severity problem(s) found |
| 45432 | 1 | Processor Information (via DMI) | Low Severity problem(s) found |
| 45410 | 1 | SSL Certificate commonName Mismatch | Low Severity problem(s) found |
| 44391 | 1 | Linksys Router Detection | Low Severity problem(s) found |
| 44319 | 1 | D-Link Router Detection | Low Severity problem(s) found |
| 44318 | 2 | HNAP Detection | Low Severity problem(s) found |
| 43829 | 2 | Kerberos Information Disclosure | Low Severity problem(s) found |
| 43111 | 1 | HTTP Methods Allowed (per directory) | Low Severity problem(s) found |
| 43067 | 12 | Web Application Tests Disabled | Low Severity problem(s) found |
| 42825 | 1 | Apple TV Detection | Low Severity problem(s) found |
| 42410 | 1 | Microsoft Windows NTLMSSP Authentication Request Remote Network Name Disclosure | Low Severity problem(s) found |
| 42263 | 2 | Unencrypted Telnet Server | Low Severity problem(s) found |
| 39521 | 2 | Backported Security Patch Detection (WWW) | Low Severity problem(s) found |
| 39520 | 10 | Backported Security Patch Detection (SSH) | Low Severity problem(s) found |
| 35716 | 24 | Ethernet Card Manufacturer Detection | Low Severity problem(s) found |
| 35712 | 2 | Web Server UPnP Detection | Low Severity problem(s) found |
| 35373 | 1 | DNS Server DNSSEC Aware Resolver | Low Severity problem(s) found |
| 35371 | 1 | DNS Server hostname.bind Map Hostname Disclosure | Low Severity problem(s) found |
| 35351 | 1 | System Information Enumeration (via DMI) | Low Severity problem(s) found |
| 34098 | 1 | BIOS version (SSH) | Low Severity problem(s) found |
| 33276 | 1 | Enumerate MAC Addresses via SSH | Low Severity problem(s) found |
| 30218 | 2 | Terminal Services Encryption Level is not FIPS-140 Compliant | Low Severity problem(s) found |
| 26920 | 4 | Microsoft Windows SMB NULL Session Authentication | Low Severity problem(s) found |
| 26917 | 2 | Microsoft Windows SMB Registry : Nessus Cannot Access the Windows Registry | Low Severity problem(s) found |
| 25701 | 1 | LDAP Crafted Search Request Server Information Disclosure | Low Severity problem(s) found |
| 25240 | 1 | Samba Server Detection | Low Severity problem(s) found |
| 25221 | 15 | Remote listeners enumeration | Low Severity problem(s) found |
| 25220 | 19 | TCP/IP Timestamps Supported | Low Severity problem(s) found |
| 25203 | 1 | Enumerate IPv4 Interfaces via SSH | Low Severity problem(s) found |
| 25202 | 1 | Enumerate IPv6 Interfaces via SSH | Low Severity problem(s) found |
| 24786 | 2 | Nessus Windows Scan Not Performed with Admin Privileges | Low Severity problem(s) found |
| 24260 | 15 | HyperText Transfer Protocol (HTTP) Information | Low Severity problem(s) found |
| 22964 | 52 | Service Detection | Low Severity problem(s) found |
| 22869 | 1 | Software Enumeration (SSH) | Low Severity problem(s) found |
| 21745 | 1 | Authentication Failure - Local Checks Not Run | Low Severity problem(s) found |
| 21643 | 8 | SSL Cipher Suites Supported | Low Severity problem(s) found |
| 21208 | 2 | Skype Stack Version Detection | Low Severity problem(s) found |
| 20870 | 1 | LDAP Server Detection | Low Severity problem(s) found |
| 20217 | 1 | iTunes Music Sharing Enabled | Low Severity problem(s) found |
| 20108 | 1 | Web Server / Application favicon.ico Vendor Fingerprinting | Low Severity problem(s) found |
| 20094 | 4 | VMware Virtual Machine Detection | Low Severity problem(s) found |
| 19772 | 2 | Skype Detection | Low Severity problem(s) found |
| 19506 | 27 | Nessus Scan Information | Low Severity problem(s) found |
| 19288 | 4 | VNC Server Security Type Detection | Low Severity problem(s) found |
| 17975 | 1 | Service Detection (GET request) | Low Severity problem(s) found |
| 17651 | 1 | Microsoft Windows SMB : Obtains the Password Policy | Low Severity problem(s) found |
| 15588 | 2 | Web Server SSL Port HTTP Traffic Detection | Low Severity problem(s) found |
| 13855 | 1 | Microsoft Windows Installed Hotfixes | Low Severity problem(s) found |
| 12634 | 1 | Authenticated Check: OS Name and Installed Package Enumeration | Low Severity problem(s) found |
| 12053 | 7 | Host Fully Qualified Domain Name (FQDN) Resolution | Low Severity problem(s) found |
| 11936 | 22 | OS Identification | Low Severity problem(s) found |
| 11933 | 1 | Do not scan printers | Low Severity problem(s) found |
| 11819 | 2 | TFTP Daemon Detection | Low Severity problem(s) found |
| 11197 | 7 | Multiple Ethernet Driver Frame Padding Information Disclosure (Etherleak) | Low Severity problem(s) found |
| 11153 | 1 | Service Detection (HELP Request) | Low Severity problem(s) found |
| 11140 | 1 | Web Server UDDI Detection | Low Severity problem(s) found |
| 11111 | 10 | RPC Services Enumeration | Low Severity problem(s) found |
| 11026 | 1 | Wireless Access Point Detection | Low Severity problem(s) found |
| 11011 | 7 | Microsoft Windows SMB Service Detection | Low Severity problem(s) found |
| 11002 | 4 | DNS Server Detection | Low Severity problem(s) found |
| 10940 | 1 | Windows Terminal Services Enabled | Low Severity problem(s) found |
| 10884 | 4 | Network Time Protocol (NTP) Server Detection | Low Severity problem(s) found |
| 10881 | 11 | SSH Protocol Versions Supported | Low Severity problem(s) found |
| 10863 | 3 | SSL Certificate Information | Low Severity problem(s) found |
| 10860 | 2 | SMB Use Host SID to Enumerate Local Users | Low Severity problem(s) found |
| 10859 | 2 | Microsoft Windows SMB LsaQueryInformationPolicy Function SID Enumeration | Low Severity problem(s) found |
| 10785 | 4 | Microsoft Windows SMB NativeLanManager Remote System Information Disclosure | Low Severity problem(s) found |
| 10758 | 1 | VNC HTTP Server Detection | Low Severity problem(s) found |
| 10736 | 19 | DCE Services Enumeration | Low Severity problem(s) found |
| 10663 | 1 | DHCP Server Detection | Low Severity problem(s) found |
| 10428 | 1 | Microsoft Windows SMB Fully Accessible Registry Detection | Low Severity problem(s) found |
| 10407 | 2 | X Server Detection | Low Severity problem(s) found |
| 10400 | 1 | Microsoft Windows SMB Registry Remotely Accessible | Low Severity problem(s) found |
| 10397 | 1 | Microsoft Windows SMB LanMan Pipe Server Listing Disclosure | Low Severity problem(s) found |
| 10395 | 2 | Microsoft Windows SMB Shares Enumeration | Low Severity problem(s) found |
| 10394 | 4 | Microsoft Windows SMB Log In Possible | Low Severity problem(s) found |
| 10386 | 4 | Web Server No 404 Error Code Check | Low Severity problem(s) found |
| 10342 | 5 | VNC Software Detection | Low Severity problem(s) found |
| 10287 | 25 | Traceroute Information | Low Severity problem(s) found |
| 10281 | 2 | Telnet Server Detection | Low Severity problem(s) found |
| 10267 | 13 | SSH Server Type and Version Information | Low Severity problem(s) found |
| 10223 | 3 | RPC portmapper Service Detection | Low Severity problem(s) found |
| 10150 | 4 | Windows NetBIOS / SMB Remote Host Information Disclosure | Low Severity problem(s) found |
| 10147 | 1 | Nessus Server Detection | Low Severity problem(s) found |
| 10114 | 17 | ICMP Timestamp Request Remote Date Disclosure | Low Severity problem(s) found |
| 10107 | 16 | HTTP Server Type and Version | Low Severity problem(s) found |
| 10028 | 1 | DNS Server BIND version Directive Remote Version Disclosure | Low Severity problem(s) found |
Port cifs (445/tcp)
Plugin ID: 10395
Microsoft Windows SMB Shares Enumeration
Synopsis
It is possible to enumerate remote network shares.
List of Hosts Plugin Output Plugin Output
192.168.1.30
Here are the SMB shares available on the remote host when logged as dtwzdicm:
- IPC$
- media
- backup
192.168.1.215
Here are the SMB shares available on the remote host when logged as unwnbojz:
- IPC$
- share
- iTunesMusic
- ADMIN$
- C$
Description
By connecting to the remote host, Nessus was able to enumerate
the network share names.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port (0/tcp)
Plugin ID: 33276
Enumerate MAC Addresses via SSH
Synopsis
This plugin enumerates MAC addresses on a remote host.
List of Hosts Plugin Output
192.168.1.13
The following MAC addresses exist on the remote host :
- 00:A0:CC:3D:B3:BA (interface eth0)
- 00:17:31:03:14:1F (interface eth1)
Description
By connecting to the remote host via SSH with the supplied
credentials, this plugin enumerates MAC addresses.
Solution
Disable any unused interfaces.
Risk Factor
None
Plugin last modification date: 2011/03/21
Port msrdp (3389/tcp)
Plugin ID: 10940
Windows Terminal Services Enabled
Synopsis
The remote Windows host has Terminal Services enabled.
List of Hosts
192.168.1.215
Description
Terminal Services allows a Windows user to remotely obtain a graphical
login (and therefore act as a local user on the remote host).
If an attacker gains a valid login and password, he may be able to use
this service to gain further access on the remote host. An attacker
may also use this service to mount a dictionary attack against the
remote host to try to log in remotely.
Note that RDP (the Remote Desktop Protocol) is vulnerable to
Man-in-the-middle attacks, making it easy for attackers to steal the
credentials of legitimate users by impersonating the Windows server.
Solution
Disable Terminal Services if you do not use it, and do not allow this
service to run across the Internet.
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (8834/tcp)
Plugin ID: 10386
Web Server No 404 Error Code Check
Synopsis
The remote web server does not return 404 error codes.
List of Hosts Plugin Output
192.168.1.13
The following title tag will be used :
200 Unauthorized
Description
The remote web server is configured such that it does not return '404
Not Found' error codes when a nonexistent file is requested, perhaps
returning instead a site map, search page or authentication page.
Nessus has enabled some counter measures for this. However, they
might be insufficient. If a great number of security holes are
produced for this port, they might not all be accurate.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/03
Port www (443/tcp)
Plugin ID: 10386
Web Server No 404 Error Code Check
Synopsis
The remote web server does not return 404 error codes.
List of Hosts Plugin Output Plugin Output
192.168.1.79
The following title tag will be used :
Redirect
192.168.1.26
CGI scanning will be disabled for this host.
Description
The remote web server is configured such that it does not return '404
Not Found' error codes when a nonexistent file is requested, perhaps
returning instead a site map, search page or authentication page.
Nessus has enabled some counter measures for this. However, they
might be insufficient. If a great number of security holes are
produced for this port, they might not all be accurate.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/03
Port www (80/tcp)
Plugin ID: 10386
Web Server No 404 Error Code Check
Synopsis
The remote web server does not return 404 error codes.
List of Hosts Plugin Output
192.168.1.79
The following title tag will be used :
Redirect
Description
The remote web server is configured such that it does not return '404
Not Found' error codes when a nonexistent file is requested, perhaps
returning instead a site map, search page or authentication page.
Nessus has enabled some counter measures for this. However, they
might be insufficient. If a great number of security holes are
produced for this port, they might not all be accurate.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/03
Port ldap (389/tcp)
Plugin ID: 25701
LDAP Crafted Search Request Server Information Disclosure
Synopsis
It is possible to discover information about the remote LDAP server.
List of Hosts Plugin Output
192.168.1.180
[+]-namingContexts:
| DC=tx,DC=hec,DC=net
| CN=Configuration,DC=tx,DC=hec,DC=net
| CN=Schema,CN=Configuration,DC=tx,DC=hec,DC=net
| DC=DomainDnsZones,DC=tx,DC=hec,DC=net
| DC=ForestDnsZones,DC=tx,DC=hec,DC=net
Description
By sending a search request with a filter set to 'objectClass=*', it
is possible to extract information about the remote LDAP server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (0/tcp)
Plugin ID: 24786
Nessus Windows Scan Not Performed with Admin Privileges
Synopsis
The Nessus scan of this host may be incomplete due to insufficient
privileges provided.
List of Hosts Plugin Output Plugin Output
192.168.1.30
It was not possible to connect to \\NAS-MAIN-OFFICE\ADMIN$
192.168.1.215
It was not possible to connect to \\MEDIA1\ADMIN$
Description
The Nessus scanner testing the remote host has been given SMB
credentials to log into the remote host, however these credentials
do not have administrative privileges.
Typically, when Nessus performs a patch audit, it logs into the
remote host and reads the version of the DLLs on the remote host
to determine if a given patch has been applied or not. This is
the method Microsoft recommends to determine if a patch has been
applied.
If your Nessus scanner does not have administrative privileges when
doing a scan, then Nessus has to fall back to perform a patch audit
through the registry which may lead to false positives (especially
when using third party patch auditing tools) or to false negatives
(not all patches can be detected thru the registry).
Solution
Reconfigure your scanner to use credentials with administrative
privileges.
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dns (53/tcp)
Plugin ID: 11002
DNS Server Detection
Synopsis
A DNS server is listening on the remote host.
List of Hosts
192.168.1.180
192.168.1.10
Description
The remote service is a Domain Name System (DNS) server, which
provides a mapping between hostnames and IP addresses.
Solution
Disable this service if it is not needed or restrict access to
internal hosts only if the service is available externally.
Risk Factor
None
Plugin last modification date: 2011/03/11
Port cifs (445/tcp)
Plugin ID: 10785
Microsoft Windows SMB NativeLanManager Remote System Information Disclosure
Synopsis
It is possible to obtain information about the remote operating
system.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.30
The remote Operating System is : Unix
The remote native lan manager is : Samba 3.0.34
The remote SMB Domain Name is : ENTERPRISE
192.168.1.215
The remote Operating System is : Windows 5.1
The remote native lan manager is : Windows 2000 LAN Manager
The remote SMB Domain Name is : MEDIA1
192.168.1.180
The remote Operating System is : Windows Server (R) 2008 Standard 6001 Service Pack 1
The remote native lan manager is : Windows Server (R) 2008 Standard 6.0
The remote SMB Domain Name is : TX
192.168.1.16
The remote Operating System is : Windows 7 Ultimate 7600
The remote native lan manager is : Windows 7 Ultimate 6.1
The remote SMB Domain Name is : O-REN
Description
It is possible to get the remote operating system name and
version (Windows and/or Samba) by sending an authentication
request to port 139 or 445.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/17
Port x11 (6002/tcp)
Plugin ID: 10407
X Server Detection
Synopsis
An X11 server is listening on the remote host
List of Hosts Plugin Output
192.168.1.14
X11 Version : 11.0
Description
The remote host is running an X11 server. X11 is a client-server
protocol that can be used to display graphical applications running on
a given host on a remote client.
Since the X11 traffic is not ciphered, it is possible for an attacker
to eavesdrop on the connection.
Solution
Restrict access to this port. If the X11 client/server facility is not
used, disable TCP entirely.
Risk Factor
Low/ CVSS Base Score: 2.6
(CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/11
Port x11 (6001/tcp)
Plugin ID: 10407
X Server Detection
Synopsis
An X11 server is listening on the remote host
List of Hosts Plugin Output
192.168.1.14
X11 Version : 11.0
Description
The remote host is running an X11 server. X11 is a client-server
protocol that can be used to display graphical applications running on
a given host on a remote client.
Since the X11 traffic is not ciphered, it is possible for an attacker
to eavesdrop on the connection.
Solution
Restrict access to this port. If the X11 client/server facility is not
used, disable TCP entirely.
Risk Factor
Low/ CVSS Base Score: 2.6
(CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/11
Port roku_control (8080/tcp)
Plugin ID: 17975
Service Detection (GET request)
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.237
The remote service appears to be a control channel for a Roku
Streaming Player. Not only does the the banner reveal the Device ID
associated with the player as well as its Ethernet and Wifi MACs
addresses, but it's also possible to control the device by sending
commands such as 'press up' and 'press home' to this service.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/11
Port ldap (389/tcp)
Plugin ID: 20870
LDAP Server Detection
Synopsis
There is an LDAP server active on the remote host.
List of Hosts
192.168.1.180
Description
The remote host is running a Lightweight Directory Access Protocol, or
LDAP, server. LDAP is a protocol for providing access to directory
services over TCP/IP.
Solution
n/a
See also
http://en.wikipedia.org/wiki/LDAP
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (0/tcp)
Plugin ID: 25220
TCP/IP Timestamps Supported
Synopsis
The remote service implements TCP timestamps.
List of Hosts
192.168.1.80
192.168.1.66
192.168.1.65
192.168.1.60
192.168.1.30
192.168.1.26
192.168.1.237
192.168.1.234
192.168.1.233
192.168.1.227
192.168.1.215
192.168.1.19
192.168.1.180
192.168.1.18
192.168.1.16
192.168.1.14
192.168.1.11
192.168.1.10
192.168.1.1
Description
The remote host implements TCP timestamps, as defined by RFC1323. A
side effect of this feature is that the uptime of the remote host can
sometimes be computed.
Solution
n/a
See also
http://www.ietf.org/rfc/rfc1323.txt
Risk Factor
None
Plugin last modification date: 2011/03/20
Port (0/tcp)
Plugin ID: 12053
Host Fully Qualified Domain Name (FQDN) Resolution
Synopsis
It was possible to resolve the name of the remote host.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.80
192.168.1.80 resolves as xbox-main-office.
192.168.1.66
192.168.1.66 resolves as johnnymo.
192.168.1.60
192.168.1.60 resolves as paimei.
192.168.1.13
192.168.1.13 resolves as gogo.
192.168.1.11
192.168.1.11 resolves as hanzo.
192.168.1.10
192.168.1.10 resolves as madmonk.
192.168.1.1
192.168.1.1 resolves as linky.
Description
Nessus was able to resolve the FQDN of the remote host.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (0/tcp)
Plugin ID: 19506
Nessus Scan Information
Synopsis
Information about the Nessus scan.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.98
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:53
Scan duration : 284 sec
192.168.1.95
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:53
Scan duration : 155 sec
192.168.1.80
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:53
Scan duration : 89 sec
192.168.1.79
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:53
Scan duration : 328 sec
192.168.1.66
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : Detected
Scan Start Date : 2011/4/13 12:53
Scan duration : 114 sec
192.168.1.65
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:53
Scan duration : 270 sec
192.168.1.60
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:53
Scan duration : 101 sec
192.168.1.30
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:53
Scan duration : 208 sec
192.168.1.26
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : Detected
Scan Start Date : 2011/4/13 12:53
Scan duration : 155 sec
192.168.1.249
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:57
Scan duration : 548 sec
192.168.1.245
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
WARNING : no port scanner was enabled during the scan. This may
lead to incomplete results
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:56
Scan duration : 13 sec
192.168.1.238
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:56
Scan duration : 72 sec
192.168.1.237
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:56
Scan duration : 129 sec
192.168.1.234
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:56
Scan duration : 141 sec
192.168.1.233
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : Detected
Scan Start Date : 2011/4/13 12:56
Scan duration : 61 sec
192.168.1.227
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:56
Scan duration : 142 sec
192.168.1.215
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:55
Scan duration : 266 sec
192.168.1.203
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:55
Scan duration : 103 sec
192.168.1.19
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : Detected
Scan Start Date : 2011/4/13 12:53
Scan duration : 176 sec
192.168.1.180
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:53
Scan duration : 214 sec
192.168.1.18
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : Detected
Scan Start Date : 2011/4/13 12:53
Scan duration : 67 sec
192.168.1.16
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/13 12:53
Scan duration : 192 sec
192.168.1.14
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : Detected
Scan Start Date : 2011/4/13 12:53
Scan duration : 78 sec
192.168.1.13
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : netstat
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : Detected
Scan Start Date : 2011/4/13 12:53
Scan duration : 381 sec
192.168.1.11
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : Detected
Scan Start Date : 2011/4/13 12:53
Scan duration : 253 sec
192.168.1.10
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : Detected
Scan Start Date : 2011/4/13 12:53
Scan duration : 74 sec
192.168.1.1
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104120034
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : default
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : disabled
Web application tests : disabled
Max hosts : 80
Max checks : 5
Recv timeout : 5
Backports : Detected
Scan Start Date : 2011/4/13 12:53
Scan duration : 308 sec
Description
This script displays, for each tested host, information about the scan itself:
- The version of the plugin set
- The type of plugin feed (HomeFeed or ProfessionalFeed)
- The version of the Nessus Engine
- The port scanner(s) used
- The port range scanned
- The date of the scan
- The duration of the scan
- The number of hosts scanned in parallel
- The number of checks done in parallel
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/19
Port cifs (445/tcp)
Plugin ID: 26917
Microsoft Windows SMB Registry : Nessus Cannot Access the Windows Registry
Synopsis
Nessus is not able to access the remote Windows Registry.
List of Hosts Plugin Output Plugin Output
192.168.1.180
Could not connect to the registry because:
Could not connect to \winreg
192.168.1.16
Could not connect to the registry because:
Could not connect to \winreg
Description
It was not possible to connect to PIPE\winreg on the remote host.
If you intend to use Nessus to perform registry-based checks, the
registry checks will not work because the 'Remote Registry Access'
service (winreg) has been disabled on the remote host or can not be
connected to with the supplied credentials.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/27
Port (8834/tcp)
Plugin ID: 24260
HyperText Transfer Protocol (HTTP) Information
Synopsis
Some information about the remote HTTP configuration can be extracted.
List of Hosts Plugin Output
192.168.1.13
Protocol version : HTTP/1.1
SSL : yes
Keep-Alive : no
Options allowed : (Not implemented)
Headers :
Date: Wed, 13 Apr 2011 16:57:08 GMT
Server: NessusWWW
Connection: close
Expires: Wed, 13 Apr 2011 16:57:08 GMT
Content-Length: 6518
Content-Type: text/html
Cache-Control:
Expires: 0
Pragma :
Description
This test gives some information about the remote HTTP protocol - the
version used, whether HTTP Keep-Alive and HTTP pipelining are enabled,
etc...
This test is informational only and does not denote any security
problem.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/14
Port (8060/tcp)
Plugin ID: 24260
HyperText Transfer Protocol (HTTP) Information
Synopsis
Some information about the remote HTTP configuration can be extracted.
List of Hosts Plugin Output Plugin Output
192.168.1.237
Protocol version : HTTP/1.1
SSL : no
Keep-Alive : no
Options allowed : (Not implemented)
Headers :
Content-Length: 1922
Server: Roku UPnP/1.0 MiniUPnPd/1.4
Cache-Control: no-cache
Content-Type: text/xml; charset="utf-8"
192.168.1.227
Protocol version : HTTP/1.1
SSL : no
Keep-Alive : no
Options allowed : (Not implemented)
Headers :
Content-Length: 1922
Server: Roku UPnP/1.0 MiniUPnPd/1.4
Cache-Control: no-cache
Content-Type: text/xml; charset="utf-8"
Description
This test gives some information about the remote HTTP protocol - the
version used, whether HTTP Keep-Alive and HTTP pipelining are enabled,
etc...
This test is informational only and does not denote any security
problem.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/14
Port (8000/tcp)
Plugin ID: 24260
HyperText Transfer Protocol (HTTP) Information
Synopsis
Some information about the remote HTTP configuration can be extracted.
List of Hosts Plugin Output
192.168.1.180
Protocol version : HTTP/1.1
SSL : no
Keep-Alive : no
Options allowed : (Not implemented)
Headers :
Date: Wed, 13 Apr 2011 20:01:05 GMT
Content-Length: 110
Content-Type: text/html;charset=utf-8
Location: http://192.168.1.180:8000/en-US/
Server: CherryPy/3.1.2
Set-Cookie: session_id_8000=147c66b05f8c9460e5c545b896de7a42ba8e5388; expires=Thu, 14 Apr 2011 20:01:05 GMT; Path=/
Description
This test gives some information about the remote HTTP protocol - the
version used, whether HTTP Keep-Alive and HTTP pipelining are enabled,
etc...
This test is informational only and does not denote any security
problem.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/14
Port (4444/tcp)
Plugin ID: 24260
HyperText Transfer Protocol (HTTP) Information
Synopsis
Some information about the remote HTTP configuration can be extracted.
List of Hosts Plugin Output
192.168.1.79
Protocol version : HTTP/1.1
SSL : no
Keep-Alive : no
Options allowed : (Not implemented)
Headers :
SERVER: ipOS/7.6 UPnP/1.0 ipUPnP/1.0
EXT:
Connection: close
Description
This test gives some information about the remote HTTP protocol - the
version used, whether HTTP Keep-Alive and HTTP pipelining are enabled,
etc...
This test is informational only and does not denote any security
problem.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/14
Port (3689/tcp)
Plugin ID: 24260
HyperText Transfer Protocol (HTTP) Information
Synopsis
Some information about the remote HTTP configuration can be extracted.
List of Hosts Plugin Output
192.168.1.234
Protocol version : HTTP/1.1
SSL : no
Keep-Alive : no
Options allowed : (Not implemented)
Headers :
Date: Wed, 13 Apr 2011 16:54:57 GMT
RIPT-Server: iTunesLib/3.0.2 (Mac OS X)
Content-Type: application/x-dmap-tagged
Content-Length: 0
Description
This test gives some information about the remote HTTP protocol - the
version used, whether HTTP Keep-Alive and HTTP pipelining are enabled,
etc...
This test is informational only and does not denote any security
problem.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/14
Port (443/tcp)
Plugin ID: 24260
HyperText Transfer Protocol (HTTP) Information
Synopsis
Some information about the remote HTTP configuration can be extracted.
List of Hosts Plugin Output Plugin Output Plugin Output
192.168.1.79
Protocol version : HTTP/1.1
SSL : yes
Keep-Alive : no
Options allowed : (Not implemented)
Headers :
Cache-control: no-cache
Server: Ubicom/1.1
Content-Type: text/html
192.168.1.26
Protocol version : HTTP/1.1
SSL : yes
Keep-Alive : yes
Options allowed : (Not implemented)
Headers :
Date: Wed, 13 Apr 2011 16:58:44 GMT
Server: Apache/2.2.8 (Ubuntu) mod_fastcgi/2.4.6 PHP/5.2.4-2ubuntu5.9 with Suhosin-Patch mod_ssl/2.2.8 OpenSSL/0.9.8g
Location: http://192.168.1.26/
Content-Length: 369
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=iso-8859-1
192.168.1.11
Protocol version : HTTP/1.0
SSL : yes
Keep-Alive : no
Options allowed : (Not implemented)
Headers :
Date: Wed, 13 Apr 2011 16:32:46 GMT
Server: Apache
Location: https://hanzo:443/sc4
Content-Length: 2
Connection: close
Content-Type: text/html
Description
This test gives some information about the remote HTTP protocol - the
version used, whether HTTP Keep-Alive and HTTP pipelining are enabled,
etc...
This test is informational only and does not denote any security
problem.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/14
Port www (80/tcp)
Plugin ID: 24260
HyperText Transfer Protocol (HTTP) Information
Synopsis
Some information about the remote HTTP configuration can be extracted.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.98
Protocol version : HTTP/1.0
SSL : no
Keep-Alive : no
Options allowed : (Not implemented)
Headers :
Content-type: text/html
Date: Tue, 11 Jan 2000 13:50:06 GMT
Connection: close
Last-Modified: Wed, 23 Aug 2006 17:22:41 GMT
Content-length: 888
192.168.1.95
Protocol version : HTTP/1.0
SSL : no
Keep-Alive : no
Options allowed : (Not implemented)
Headers :
Content-type: text/html
Date: Tue, 04 Jan 2000 22:07:58 GMT
Connection: close
Last-Modified: Wed, 23 Aug 2006 17:22:41 GMT
Content-length: 888
192.168.1.79
Protocol version : HTTP/1.1
SSL : no
Keep-Alive : no
Options allowed : (Not implemented)
Headers :
Cache-control: no-cache
Server: Ubicom/1.1
Content-Type: text/html
192.168.1.65
Protocol version : HTTP/1.0
SSL : no
Keep-Alive : no
Headers :
Server: Intoto Http Server v1.0
WWW-Authenticate: Basic realm="WRT54G"
Content-type: text/html
Pragma: no-cache
Connection: Close
192.168.1.26
Protocol version : HTTP/1.1
SSL : no
Keep-Alive : yes
Options allowed : (Not implemented)
Headers :
Date: Wed, 13 Apr 2011 16:58:44 GMT
Server: Apache/2.2.8 (Ubuntu) mod_fastcgi/2.4.6 PHP/5.2.4-2ubuntu5.9 with Suhosin-Patch mod_ssl/2.2.8 OpenSSL/0.9.8g
Location: http://192.168.1.26/my_blog
Content-Length: 375
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=iso-8859-1
192.168.1.1
Protocol version : HTTP/1.1
SSL : no
Keep-Alive : no
Options allowed : OPTIONS, GET, HEAD, POST
Headers :
Expires: 0
Last-Modified: Wed, 13 Apr 2011 17:01:47 GMT
Cache-Control: no-store, no-cache, must-revalidate
Cache-Control: post-check=0, pre-check=0
Pragma: no-cache
WWW-Authenticate: Basic realm="."
Content-type: text/html
Connection: close
Transfer-Encoding: chunked
Date: Wed, 13 Apr 2011 17:01:47 GMT
Server: lighttpd/1.4.23
Description
This test gives some information about the remote HTTP protocol - the
version used, whether HTTP Keep-Alive and HTTP pipelining are enabled,
etc...
This test is informational only and does not denote any security
problem.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/14
Port dlink_dccd (2003/udp)
Plugin ID: 47606
D-Link DCC Protocol Security Bypass
Synopsis
The remote network service is affected by a security bypass
vulnerability.
List of Hosts Plugin Output
192.168.1.79
192.168.1.79
Nessus was able to exploit the vulnerability to retrieve the remote
device's SSID :
enterprise-bridge
Description
The remote D-link Click 'n Connect Daemon does not implement any
authentication and therefore allows remote attackers to view
configuration and control server functions via the affected service.
Solution
Unknown at this time.
Risk Factor
High/ CVSS Base Score: 8.3
(CVSS2#AV:A/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.9(CVSS2#E:F/RL:U/RC:ND)
Bugtraq ID
41187
Plugin publication date: 2010/07/06
Plugin last modification date: 2011/03/11
Ease of exploitability: Exploits are available
Port www (3689/tcp)
Plugin ID: 20217
iTunes Music Sharing Enabled
Synopsis
The remote host contains an application that may not match your
corporate security policy.
List of Hosts
192.168.1.60
Description
The version of iTunes on the remote host is configured to stream music
between hosts.
Such song sharing may not be in accordance with your security policy.
Solution
Disable song sharing if desired or limit access to this port.
Risk Factor
None
Plugin last modification date: 2011/03/14
Port (8089/tcp)
Plugin ID: 51891
SSL Session Resume Supported
Synopsis
The remote host allows resuming SSL sessions.
List of Hosts Plugin Output
192.168.1.180
This port supports resuming SSLv3/TLSv1 sessions.
Description
This script detects whether a host allows resuming SSL sessions by
performing a full SSL handshake to receive a session ID, and then
reconnecting with the previously used session ID. If the server
accepts the session ID in the second connection, the server maintains
a cache of sessions that can be resumed.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/11
Port www (3000/tcp)
Plugin ID: 51891
SSL Session Resume Supported
Synopsis
The remote host allows resuming SSL sessions.
List of Hosts Plugin Output
192.168.1.26
This port supports resuming SSLv3/TLSv1 sessions.
Description
This script detects whether a host allows resuming SSL sessions by
performing a full SSL handshake to receive a session ID, and then
reconnecting with the previously used session ID. If the server
accepts the session ID in the second connection, the server maintains
a cache of sessions that can be resumed.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/11
Port www (443/tcp)
Plugin ID: 51891
SSL Session Resume Supported
Synopsis
The remote host allows resuming SSL sessions.
List of Hosts Plugin Output Plugin Output
192.168.1.26
This port supports resuming SSLv3/TLSv1 sessions.
192.168.1.11
This port supports resuming SSLv3/TLSv1 sessions.
Description
This script detects whether a host allows resuming SSL sessions by
performing a full SSL handshake to receive a session ID, and then
reconnecting with the previously used session ID. If the server
accepts the session ID in the second connection, the server maintains
a cache of sessions that can be resumed.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/11
Port (0/icmp)
Plugin ID: 10114
ICMP Timestamp Request Remote Date Disclosure
Synopsis
It is possible to determine the exact time set on the remote host.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.98
The difference between the local and remote clocks is 11222 seconds.
192.168.1.95
The difference between the local and remote clocks is -18784 seconds.
192.168.1.80
The difference between the local and remote clocks is 46944 seconds.
192.168.1.30
The difference between the local and remote clocks is -291 seconds.
192.168.1.26
The difference between the local and remote clocks is -201 seconds.
192.168.1.238
The difference between the local and remote clocks is -285 seconds.
192.168.1.237
The difference between the local and remote clocks is -292 seconds.
192.168.1.227
The difference between the local and remote clocks is -301 seconds.
192.168.1.203
This host returns non-standard timestamps (high bit is set)
192.168.1.19
The difference between the local and remote clocks is 17937 seconds.
192.168.1.180
The ICMP timestamps seem to be in little endian format (not in network format)
The difference between the local and remote clocks is -11242 seconds.
192.168.1.18
The difference between the local and remote clocks is 17939 seconds.
192.168.1.16
The ICMP timestamps seem to be in little endian format (not in network format)
The difference between the local and remote clocks is -824 seconds.
192.168.1.14
The difference between the local and remote clocks is -62 seconds.
192.168.1.11
The difference between the local and remote clocks is 1452 seconds.
192.168.1.10
The difference between the local and remote clocks is 4715 seconds.
192.168.1.1
The difference between the local and remote clocks is -291 seconds.
Description
The remote host answers to an ICMP timestamp request. This allows an
attacker to know the date which is set on your machine.
This may help him to defeat all your time based authentication
protocols.
Solution
Filter out the ICMP timestamp requests (13), and the outgoing ICMP
timestamp replies (14).
Risk Factor
None
CVE
CVE-1999-0524
Plugin publication date: 1999/08/01
Plugin last modification date: 2011/03/21
Port (0/tcp)
Plugin ID: 45433
Memory Information (via DMI)
Synopsis
Information about the remote system's memory devices can be read.
List of Hosts Plugin Output
192.168.1.13
Total memory : 2048 MB
Description
Using the SMBIOS (aka DMI) interface, it was possible to retrieve
information about the remote system's memory devices, such as the
total amount of installed memory.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (8834/tcp)
Plugin ID: 10107
HTTP Server Type and Version
Synopsis
A web server is running on the remote host.
List of Hosts Plugin Output
192.168.1.13
The remote web server type is :
NessusWWW
Description
This plugin attempts to determine the type and the version of the
remote web server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port (8060/tcp)
Plugin ID: 10107
HTTP Server Type and Version
Synopsis
A web server is running on the remote host.
List of Hosts Plugin Output Plugin Output
192.168.1.237
The remote web server type is :
Roku UPnP/1.0 MiniUPnPd/1.4
192.168.1.227
The remote web server type is :
Roku UPnP/1.0 MiniUPnPd/1.4
Description
This plugin attempts to determine the type and the version of the
remote web server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port (8000/tcp)
Plugin ID: 10107
HTTP Server Type and Version
Synopsis
A web server is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The remote web server type is :
CherryPy/3.1.2
Description
This plugin attempts to determine the type and the version of the
remote web server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port (5800/tcp)
Plugin ID: 10107
HTTP Server Type and Version
Synopsis
A web server is running on the remote host.
List of Hosts Plugin Output
192.168.1.66
The remote web server type is :
RealVNC-VNCApplication/E4.5.4 (r41964)
Description
This plugin attempts to determine the type and the version of the
remote web server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port (4444/tcp)
Plugin ID: 10107
HTTP Server Type and Version
Synopsis
A web server is running on the remote host.
List of Hosts Plugin Output
192.168.1.79
The remote web server type is :
ipOS/7.6 UPnP/1.0 ipUPnP/1.0
Description
This plugin attempts to determine the type and the version of the
remote web server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port (3689/tcp)
Plugin ID: 10107
HTTP Server Type and Version
Synopsis
A web server is running on the remote host.
List of Hosts Plugin Output
192.168.1.60
The remote web server type is :
iTunes/8.2.1 (Mac OS X)
Description
This plugin attempts to determine the type and the version of the
remote web server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port (631/tcp)
Plugin ID: 10107
HTTP Server Type and Version
Synopsis
A web server is running on the remote host.
List of Hosts Plugin Output
192.168.1.30
The remote web server type is :
CUPS/1.1
Description
This plugin attempts to determine the type and the version of the
remote web server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port (443/tcp)
Plugin ID: 10107
HTTP Server Type and Version
Synopsis
A web server is running on the remote host.
List of Hosts Plugin Output Plugin Output Plugin Output
192.168.1.79
The remote web server type is :
Ubicom/1.1
192.168.1.26
The remote web server type is :
Apache/2.2.8 (Ubuntu) mod_fastcgi/2.4.6 PHP/5.2.4-2ubuntu5.9 with Suhosin-Patch mod_ssl/2.2.8 OpenSSL/0.9.8g
You can set the directive 'ServerTokens Prod' to limit the information
emanating from the server in its response headers.
192.168.1.11
The remote web server type is :
Apache
and the 'ServerTokens' directive is ProductOnly
Apache does not offer a way to hide the server type.
Description
This plugin attempts to determine the type and the version of the
remote web server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port www (80/tcp)
Plugin ID: 10107
HTTP Server Type and Version
Synopsis
A web server is running on the remote host.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.80
The remote web server type is :
GoAhead-Webs
192.168.1.79
The remote web server type is :
Ubicom/1.1
192.168.1.65
The remote web server type is :
Intoto Http Server v1.0
192.168.1.26
The remote web server type is :
Apache/2.2.8 (Ubuntu) mod_fastcgi/2.4.6 PHP/5.2.4-2ubuntu5.9 with Suhosin-Patch mod_ssl/2.2.8 OpenSSL/0.9.8g
You can set the directive 'ServerTokens Prod' to limit the information
emanating from the server in its response headers.
192.168.1.1
The remote web server type is :
lighttpd/1.4.23
Description
This plugin attempts to determine the type and the version of the
remote web server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port www (443/tcp)
Plugin ID: 53360
PolarSSL Diffie-Hellman Key Exchange Security Bypass Vulnerability
Synopsis
The remote SSL/TLS server accepts a weak Diffie-Hellman public
value.
List of Hosts
192.168.1.11
Description
This script detects whether a SSL/TLS server accepts a weak
Diffie-Hellman (DH) public value by setting the DH value to 1 in the
Client Key Exchange handshake message.
Servers accepting this value allow an attacker to force the
calculation of a fully predictable Diffie-Hellman secret, which serves
as the pre master secret in SSL/TLS key computation. Successfully
exploiting this issue may allow attackers to perform man-in-the-middle
attacks or impersonate trusted servers, which will aid in further
attacks.
Note that only the following cipher suites are affected :
- SSL_EDH_RSA_DES_168_SHA
- SSL_EDH_RSA_AES_128_SHA
- SSL_EDH_RSA_AES_256_SHA
- SSL_EDH_RSA_CAMELLIA_128_SHA
- SSL_EDH_RSA_CAMELLIA_256_SHA
Solution
If using PolarSSL, upgrade to version 0.99-pre3 / 0.14.2 or
higher.
Risk Factor
Medium/ CVSS Base Score: 5.8
(CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:N)
Bugtraq ID
46670
Other references
OSVDB:70945
Patch publication date: 2011/02/25
Plugin publication date: 2011/04/11
Plugin last modification date: 2011/04/11
Port cifs (445/tcp)
Plugin ID: 42411
Microsoft Windows SMB Shares Unprivileged Access
Synopsis
It is possible to access a network share.
List of Hosts Plugin Output Plugin Output
192.168.1.30
The following shares can be accessed as dtwzdicm :
- backup - (readable,writable)
+ Content of this share :
..
Dictionaries.zip
VMWareImages
Videos
RainbowTables
- media - (readable,writable)
+ Content of this share :
..
Videos
Music
Pictures
192.168.1.215
The following shares can be accessed as unwnbojz :
- share - (readable)
+ Content of this share :
..
Backup-VM-09302006.zip
- iTunesMusic - (readable)
+ Content of this share :
..
Beastie Boys
Ben Harper
Biggie Smalls
Description
The remote has one or more Windows shares that can be accessed through
the network with the given credentials.
Depending on the share rights, it may allow an attacker to read/write
confidential data.
Solution
To restrict access under Windows, open Explorer, do a right click on
each share, go to the 'sharing' tab, and click on 'permissions'.
Risk Factor
High/ CVSS Base Score: 7.5
(CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P)
CVSS Temporal Score: 7.5(CVSS2#E:H/RL:U/RC:ND)
Bugtraq ID
8026
Other references
OSVDB:299
Plugin publication date: 2009/11/06
Plugin last modification date: 2011/03/27
Ease of exploitability: No exploit is required
Port (0/tcp)
Plugin ID: 13855
Microsoft Windows Installed Hotfixes
Synopsis
It is possible to enumerate installed hotfixes on the remote Windows
host.
List of Hosts Plugin Output
192.168.1.215
The SMB account used for this test does not have sufficient privileges to get
the list of the hotfixes installed on the remote host. As a result, Nessus was
not able to determine the missing hotfixes on the remote host and most SMB checks
have been disabled.
Solution : Configure the account you are using to get the ability to connect to ADMIN$
Description
Using the supplied credentials, Nessus was able to log into the the
remote Windows host, enumerate installed hotfixes, and store them in
its knowledge base for other plugins to use.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/04
Port (0/tcp)
Plugin ID: 50686
IP Forwarding Enabled
Synopsis
The remote has IP forwarding enabled.
List of Hosts
192.168.1.98
192.168.1.95
192.168.1.79
192.168.1.203
Description
The remote host has IP forwarding enabled. An attacker may use this
flaw to use the to route packets through this host and potentially
bypass some firewalls / routers / NAC filtering.
Unless the remote host is a router, it is recommended that you disable IP
forwarding.
Solution
On Linux, you can disable IP forwarding by doing :
echo 0 > /proc/sys/net/ipv4/ip_forward
On Windows, set the key 'IPEnableRouter' to 0 under
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameter
On Mac OS X, you can disable IP forwarding by executing the command :
sysctl -w net.inet.ip.forwarding=0
For other systems, check with your vendor.
Risk Factor
Low/ CVSS Base Score: 3.2
(CVSS2#AV:A/AC:H/Au:N/C:P/I:P/A:N)
CVE
CVE-1999-0511
Plugin last modification date: 2011/03/21
Port www (8834/tcp)
Plugin ID: 15588
Web Server SSL Port HTTP Traffic Detection
Synopsis
An SSL detection issue might impede the Nessus Scan.
List of Hosts
192.168.1.13
Description
Nessus has discovered that it is talking in plain HTTP on a SSL port.
Nessus has corrected this issue by enabling HTTPS for this port only.
However if other SSL ports are used on the remote host, they might be
skipped.
Solution
Enable SSL tests in the 'Services' preference setting, or increase the
timeouts if this option is already set and the plugin missed this
port.
Risk Factor
None
Plugin last modification date: 2011/04/01
Port (3000/tcp)
Plugin ID: 15588
Web Server SSL Port HTTP Traffic Detection
Synopsis
An SSL detection issue might impede the Nessus Scan.
List of Hosts
192.168.1.26
Description
Nessus has discovered that it is talking in plain HTTP on a SSL port.
Nessus has corrected this issue by enabling HTTPS for this port only.
However if other SSL ports are used on the remote host, they might be
skipped.
Solution
Enable SSL tests in the 'Services' preference setting, or increase the
timeouts if this option is already set and the plugin missed this
port.
Risk Factor
None
Plugin last modification date: 2011/04/01
Port (0/tcp)
Plugin ID: 22869
Software Enumeration (SSH)
Synopsis
It is possible to enumerate installed software on the remote host, via
SSH.
List of Hosts Plugin Output
192.168.1.13
Here is the list of packages installed on the remote CentOS Linux system :
GConf2-2.14.0-9.el5|(none)
MAKEDEV-3.23-1.2|(none)
Nessus-4.4.1-es5|(none)
NetworkManager-0.7.0-10.el5_5.2|1
NetworkManager-glib-0.7.0-10.el5_5.2|1
ORBit2-2.14.3-5.el5|(none)
SysVinit-2.86-15.el5|(none)
acl-2.2.39-6.el5|(none)
acpid-1.0.4-9.el5_4.2|(none)
afpfs-ng-0.8.1-2.el5.1|(none)
afpfs-ng-devel-0.8.1-2.el5.1|(none)
alsa-lib-1.0.17-1.el5|(none)
amtu-1.0.6-1.el5|(none)
anacron-2.3-45.el5.centos|(none)
apmd-3.2.2-5|1
apr-1.2.7-11.el5_5.3|(none)
apr-devel-1.2.7-11.el5_5.3|(none)
apr-util-1.2.7-11.el5_5.2|(none)
apr-util-devel-1.2.7-11.el5_5.2|(none)
aspell-0.60.3-7.1|12
aspell-en-6.0-2.1|50
at-3.1.8-84.el5|(none)
at-spi-1.7.11-3.el5|(none)
atk-1.12.2-1.fc6|(none)
attr-2.4.32-1.1|(none)
audiofile-0.2.6-5|1
audit-1.7.17-3.el5|(none)
audit-libs-1.7.17-3.el5|(none)
audit-libs-python-1.7.17-3.el5|(none)
authconfig-5.3.21-6.el5|(none)
autoconf-2.59-12|(none)
autofs-5.0.1-0.rc2.143.el5_5.6|1
automake-1.9.6-2.3.el5|(none)
automake14-1.4p6-13.el5.1|(none)
automake15-1.5-16.el5.2|(none)
automake16-1.6.3-8.el5.1|(none)
automake17-1.7.9-7.el5.2|(none)
avahi-0.6.16-9.el5_5|(none)
avahi-compat-libdns_sd-0.6.16-9.el5_5|(none)
avahi-glib-0.6.16-9.el5_5|(none)
basesystem-8.0-5.1.1.el5.centos|(none)
bash-3.2-24.el5|(none)
bc-1.06-21|(none)
bind-libs-9.3.6-4.P1.el5_5.3|30
bind-utils-9.3.6-4.P1.el5_5.3|30
binutils-2.17.50.0.6-14.el5|(none)
bison-2.3-2.1|(none)
bitstream-vera-fonts-1.10-7|(none)
bluez-gnome-0.5-5.fc6|(none)
bluez-libs-3.7-1.1|(none)
bluez-utils-3.7-2.2.el5.centos|(none)
byacc-1.9-29.2.2|(none)
bzip2-1.0.3-6.el5_5|(none)
bzip2-libs-1.0.3-6.el5_5|(none)
cairo-1.2.4-5.el5|(none)
ccid-1.3.8-1.el5|(none)
centos-release-5-5.el5.centos|10
centos-release-notes-5.5-0|(none)
checkpolicy-1.33.1-6.el5|(none)
chkconfig-1.3.30.2-2.el5|(none)
chkfontpath-1.10.1-1.1|(none)
conman-0.1.9.2-8.el5|(none)
coolkey-1.1.0-14.el5|(none)
coreutils-5.97-23.el5_4.2|(none)
cpio-2.6-23.el5_4.1|(none)
cpp-4.1.2-48.el5|(none)
cpuspeed-1.2.1-9.el5|1
cracklib-2.8.9-3.3|(none)
cracklib-dicts-2.8.9-3.3|(none)
crash-4.1.2-4.el5.centos.1|(none)
crontabs-1.10-8|(none)
cryptsetup-luks-1.0.3-5.el5|(none)
cscope-15.5-15.1.el5_3.1|(none)
ctags-5.6-1.1|(none)
cups-1.3.7-18.el5_5.8|1
cups-libs-1.3.7-18.el5_5.8|1
curl-7.15.5-9.el5|(none)
cvs-1.11.22-7.el5|(none)
cyrus-sasl-2.1.22-5.el5_4.3|(none)
cyrus-sasl-devel-2.1.22-5.el5_4.3|(none)
cyrus-sasl-lib-2.1.22-5.el5_4.3|(none)
cyrus-sasl-plain-2.1.22-5.el5_4.3|(none)
db4-4.3.29-10.el5_5.2|(none)
db4-devel-4.3.29-10.el5_5.2|(none)
dbus-1.1.2-14.el5|(none)
dbus-glib-0.73-10.el5_5|(none)
dbus-libs-1.1.2-14.el5|(none)
dbus-python-0.70-9.el5_4|(none)
desktop-file-utils-0.10-7|(none)
dev86-0.16.17-2.2|(none)
device-mapper-1.02.39-1.el5_5.2|(none)
device-mapper-event-1.02.39-1.el5_5.2|(none)
device-mapper-multipath-0.4.7-34.el5_5.6|(none)
dhclient-3.0.5-23.el5_5.2|12
dhcpv6-client-1.0.10-18.el5|(none)
diffstat-1.41-1.2.3.el5|(none)
diffutils-2.8.1-15.2.3.el5|(none)
dmidecode-2.10-3.el5|1
dmraid-1.0.0.rc13-63.el5|(none)
dmraid-events-1.0.0.rc13-63.el5|(none)
dnsmasq-2.45-1.1.el5_3|(none)
dogtail-0.6.1-3.el5|(none)
dos2unix-3.1-27.2.el5|(none)
dosfstools-2.11-9.el5|(none)
doxygen-1.4.7-1.1|1
dump-0.4b41-4.el5|(none)
e2fsprogs-1.39-23.el5_5.1|(none)
e2fsprogs-devel-1.39-23.el5_5.1|(none)
e2fsprogs-libs-1.39-23.el5_5.1|(none)
ecryptfs-utils-75-5.el5|(none)
ed-0.2-39.el5_2|(none)
eject-2.1.5-4.2.el5|(none)
elfutils-0.137-3.el5|(none)
elfutils-libelf-0.137-3.el5|(none)
elfutils-libs-0.137-3.el5|(none)
esound-0.2.36-3|1
ethtool-6-4.el5|(none)
expat-1.95.8-8.3.el5_5.3|(none)
expat-devel-1.95.8-8.3.el5_5.3|(none)
fbset-2.1-22|(none)
file-4.17-15.el5_3.1|(none)
filesystem-2.4.0-3.el5|(none)
findutils-4.2.27-6.el5|1
finger-0.17-32.2.1.1|(none)
fipscheck-1.2.0-1.el5|(none)
fipscheck-lib-1.2.0-1.el5|(none)
firebird-devel-2.1.3.18185.0-2.el5|(none)
firebird-filesystem-2.1.3.18185.0-2.el5|(none)
firebird-libfbclient-2.1.3.18185.0-2.el5|(none)
firebird-libfbembed-2.1.3.18185.0-2.el5|(none)
firstboot-tui-1.4.27.8-1.el5.centos|(none)
flex-2.5.4a-41.fc6|(none)
fontconfig-2.4.1-7.el5|(none)
freetype-2.2.1-28.el5_5.1|(none)
ftp-0.17-35.el5|(none)
gail-1.9.2-3.el5_4|(none)
gamin-0.1.7-8.el5|(none)
gamin-python-0.1.7-8.el5|(none)
gawk-3.1.5-14.el5|(none)
gcc-4.1.2-48.el5|(none)
gcc-c++-4.1.2-48.el5|(none)
gcc-gfortran-4.1.2-48.el5|(none)
gdb-7.0.1-23.el5_5.2|(none)
gdbm-1.8.0-26.2.1|(none)
gettext-0.14.6-4.el5|(none)
glib2-2.12.3-4.el5_3.1|(none)
glibc-2.5-49.el5_5.7|(none)
glibc-common-2.5-49.el5_5.7|(none)
glibc-devel-2.5-49.el5_5.7|(none)
glibc-headers-2.5-49.el5_5.7|(none)
gmp-4.1.4-10.el5|(none)
gnome-keyring-0.6.0-1.fc6|(none)
gnome-mime-data-2.4.2-3.1|(none)
gnome-mount-0.5-3.el5|(none)
gnome-python2-2.16.0-1.fc6|(none)
gnome-python2-bonobo-2.16.0-1.fc6|(none)
gnome-python2-gconf-2.16.0-1.fc6|(none)
gnome-python2-gnomevfs-2.16.0-1.fc6|(none)
gnome-vfs2-2.16.2-6.el5_5.1|(none)
gnu-efi-3.0c-1.1|(none)
gnupg-1.4.5-14.el5_5.1|(none)
gnutls-1.4.1-3.el5_4.8|(none)
gpg-pubkey-e8562897-459f07a4|(none)
gpm-1.20.1-74.1|(none)
grep-2.5.1-55.el5|(none)
groff-1.18.1.1-11.1|(none)
grub-0.97-13.5|(none)
gtk2-2.10.4-21.el5_5.6|(none)
gzip-1.3.5-11.el5.centos.1|(none)
hal-0.5.8.1-59.el5|(none)
hdparm-6.6-2|(none)
hesiod-3.1.0-8|(none)
hicolor-icon-theme-0.9-2.1|(none)
hmaccalc-0.9.6-3.el5|(none)
htmlview-4.0.0-2.el5|(none)
hwdata-0.213.18-1.el5.1|(none)
ibmasm-3.0-9|(none)
ifd-egate-0.05-15|(none)
imake-1.0.2-3|(none)
indent-2.2.9-14.fc6|(none)
info-4.8-14.el5|(none)
initscripts-8.45.30-3.el5.centos|(none)
iproute-2.6.18-11.el5|(none)
ipsec-tools-0.6.5-14.el5_5.5|(none)
iptables-1.3.5-5.3.el5_4.1|(none)
iptables-ipv6-1.3.5-5.3.el5_4.1|(none)
iptstate-1.4-2.el5|(none)
iputils-20020927-46.el5|(none)
irda-utils-0.9.17-2.fc6|(none)
irqbalance-0.55-15.el5|2
jwhois-3.2.3-8.el5|(none)
kbd-1.12-21.el5|(none)
kernel-2.6.18-194.32.1.el5|(none)
kernel-2.6.18-194.el5|(none)
kernel-devel-2.6.18-194.32.1.el5|(none)
kernel-headers-2.6.18-194.32.1.el5|(none)
keyutils-1.2-1.el5|(none)
keyutils-libs-1.2-1.el5|(none)
keyutils-libs-devel-1.2-1.el5|(none)
kpartx-0.4.7-34.el5_5.6|(none)
krb5-devel-1.6.1-36.el5_5.6|(none)
krb5-libs-1.6.1-36.el5_5.6|(none)
krb5-workstation-1.6.1-36.el5_5.6|(none)
ksh-20100202-1.el5_5.1|(none)
kudzu-1.2.57.1.24-1.el5.centos|(none)
less-436-2.el5|(none)
lftp-3.7.11-4.el5_5.3|(none)
libFS-1.0.0-3.1|(none)
libICE-1.0.1-2.1|(none)
libIDL-0.8.7-1.fc6|(none)
libSM-1.0.1-3.1|(none)
libX11-1.0.3-11.el5|(none)
libXTrap-1.0.0-3.1|(none)
libXau-1.0.1-3.1|(none)
libXaw-1.0.2-8.1|(none)
libXcursor-1.1.7-1.1|(none)
libXdmcp-1.0.1-2.1|(none)
libXevie-1.0.1-3.1|(none)
libXext-1.0.1-2.1|(none)
libXfixes-4.0.1-2.1|(none)
libXfont-1.2.2-1.0.3.el5_1|(none)
libXfontcache-1.0.2-3.1|(none)
libXft-2.1.10-1.1|(none)
libXi-1.0.1-4.el5_4|(none)
libXinerama-1.0.1-2.1|(none)
libXmu-1.0.2-5|(none)
libXpm-3.5.5-3|(none)
libXrandr-1.1.1-3.3|(none)
libXrender-0.9.1-3.1|(none)
libXres-1.0.1-3.1|(none)
libXt-1.0.2-3.2.el5|(none)
libXtst-1.0.1-3.1|(none)
libXxf86misc-1.0.1-3.1|(none)
libXxf86vm-1.0.1-3.1|(none)
libacl-2.2.39-6.el5|(none)
libaio-0.3.106-5|(none)
libart_lgpl-2.3.17-4|(none)
libattr-2.4.32-1.1|(none)
libbonobo-2.16.0-1.1.el5_5.1|(none)
libbonoboui-2.16.0-1.fc6|(none)
libcap-1.10-26|(none)
libdaemon-0.10-5.el5|(none)
libdrm-2.0.2-1.1|(none)
libevent-1.4.13-1|(none)
libfontenc-1.0.2-2.2.el5|(none)
libgcc-4.1.2-48.el5|(none)
libgcrypt-1.4.4-5.el5|(none)
libgfortran-4.1.2-48.el5|(none)
libglade2-2.6.0-2|(none)
libgnome-2.16.0-6.el5|(none)
libgnomecanvas-2.14.0-4.1|(none)
libgnomeui-2.16.0-5.el5|(none)
libgomp-4.4.0-6.el5|(none)
libgpg-error-1.4-2|(none)
libgssapi-0.10-2|(none)
libhugetlbfs-1.3-7.el5|(none)
libicu-3.6-5.11.4|(none)
libidn-0.6.5-1.1|(none)
libjpeg-6b-37|(none)
libnotify-0.4.2-6.el5|(none)
libpcap-0.9.4-15.el5|14
libpcap-devel-0.9.4-15.el5|14
libpng-1.2.10-7.1.el5_5.3|2
libselinux-1.33.4-5.5.el5|(none)
libselinux-devel-1.33.4-5.5.el5|(none)
libselinux-python-1.33.4-5.5.el5|(none)
libselinux-utils-1.33.4-5.5.el5|(none)
libsemanage-1.9.1-4.4.el5|(none)
libsepol-1.15.2-3.el5|(none)
libsepol-devel-1.15.2-3.el5|(none)
libssh-0.4.6-1.el5.rf|(none)
libssh-devel-0.4.6-1.el5.rf|(none)
libssh2-1.2.7-1.el5.rf|(none)
libssh2-devel-1.2.7-1.el5.rf|(none)
libstdc++-4.1.2-48.el5|(none)
libstdc++-devel-4.1.2-48.el5|(none)
libsysfs-2.0.0-6|(none)
libtermcap-2.0.8-46.1|(none)
libtiff-3.8.2-7.el5_5.5|(none)
libtool-1.5.22-7.el5_4|(none)
libusb-0.1.12-5.1|(none)
libuser-0.54.7-2.1.el5_4.1|(none)
libutempter-1.1.4-4.el5|(none)
libvolume_id-095-14.21.el5_5.1|(none)
libwnck-2.16.0-4.fc6|(none)
libxml2-2.6.26-2.1.2.8.el5_5.1|(none)
libxml2-python-2.6.26-2.1.2.8.el5_5.1|(none)
libxslt-1.1.17-2.el5_2.2|(none)
logrotate-3.7.4-9.el5_5.2|(none)
logwatch-7.3-8.el5|(none)
lsof-4.78-3|(none)
ltrace-0.5-13.45svn.el5|(none)
lvm2-2.02.56-8.el5_5.6|(none)
m2crypto-0.16-6.el5.6|(none)
m4-1.4.5-3.el5.1|(none)
mailcap-2.1.23-1.fc6|(none)
mailx-8.1.1-44.2.2|(none)
make-3.81-3.el5|1
man-1.6d-1.1|(none)
man-pages-2.39-15.el5_4|(none)
mcstrans-0.2.11-3.el5|(none)
mdadm-2.6.9-3.el5|(none)
mesa-libGL-6.5.1-7.8.el5|(none)
mgetty-1.1.33-9.fc6|(none)
microcode_ctl-1.17-1.50.el5|1
mingetty-1.07-5.2.2|(none)
mkbootdisk-1.5.3-2.1|(none)
mkinitrd-5.1.19.6-61.el5_5.2|(none)
mktemp-1.5-23.2.2|3
mlocate-0.15-1.el5.2|(none)
module-init-tools-3.3-0.pre3.1.60.el5_5.1|(none)
mtools-3.9.10-2.fc6|(none)
mtr-0.71-3.1|2
mysql-5.0.77-4.el5_5.4|(none)
mysql-devel-5.0.77-4.el5_5.4|(none)
nano-1.3.12-1.1|(none)
nash-5.1.19.6-61.el5_5.2|(none)
nc-1.84-10.fc6|(none)
ncurses-5.5-24.20060715|(none)
neon-0.25.5-10.el5_4.1|(none)
net-tools-1.60-81.el5|(none)
newt-0.52.2-15.el5|(none)
nfs-utils-1.0.9-47.el5_5|1
nfs-utils-lib-1.0.8-7.6.el5|(none)
notification-daemon-0.3.5-9.el5|(none)
nscd-2.5-49.el5_5.7|(none)
nspr-4.8.6-1.el5_5|(none)
nss-3.12.8-1.el5.centos|(none)
nss-tools-3.12.8-1.el5.centos|(none)
nss_db-2.2-35.4.el5_5|(none)
nss_ldap-253-25.el5|(none)
ntsysv-1.3.30.2-2.el5|(none)
numactl-0.9.8-11.el5|(none)
oddjob-0.27-9.el5|(none)
oddjob-libs-0.27-9.el5|(none)
openldap-2.3.43-12.el5_5.3|(none)
openldap-devel-2.3.43-12.el5_5.3|(none)
openssh-4.3p2-41.el5_5.1|(none)
openssh-clients-4.3p2-41.el5_5.1|(none)
openssh-server-4.3p2-41.el5_5.1|(none)
openssl-0.9.8e-12.el5_5.7|(none)
openssl-devel-0.9.8e-12.el5_5.7|(none)
oprofile-0.9.4-15.el5|(none)
pam-0.99.6.2-6.el5_5.2|(none)
pam_ccreds-3-5|(none)
pam_krb5-2.2.14-15|(none)
pam_passwdqc-1.0.2-1.2.2|(none)
pam_pkcs11-0.5.3-23|(none)
pam_smb-1.1.7-7.2.1|(none)
pango-1.14.9-8.el5.centos|(none)
paps-0.6.6-19.el5|(none)
parted-1.8.1-27.el5|(none)
passwd-0.73-1|(none)
patch-2.5.4-29.2.3.el5|(none)
patchutils-0.2.31-2.2.2|(none)
pax-3.4-2.el5_4|(none)
pciutils-2.2.3-8.el5_4|(none)
pcmciautils-014-5|(none)
pcre-6.6-2.el5_1.7|(none)
pcre-devel-6.6-2.el5_1.7|(none)
pcsc-lite-1.4.4-4.el5_5|(none)
pcsc-lite-libs-1.4.4-4.el5_5|(none)
perl-5.8.8-32.el5_5.2|4
perl-DBI-1.52-2.el5|(none)
perl-String-CRC32-1.4-2.fc6|(none)
perl-URI-1.35-3|(none)
pinfo-0.6.9-1.fc6|(none)
pkgconfig-0.21-2.el5|1
pkinit-nss-0.7.6-1.el5|(none)
pm-utils-0.99.3-10.el5.centos|(none)
policycoreutils-1.33.12-14.8.el5|(none)
poppler-0.5.4-4.4.el5_5.14|(none)
poppler-utils-0.5.4-4.4.el5_5.14|(none)
popt-1.10.2.3-20.el5_5.1|(none)
portmap-4.0-65.2.2.1|(none)
postgresql-8.1.22-1.el5_5.1|(none)
postgresql-devel-8.1.22-1.el5_5.1|(none)
postgresql-libs-8.1.22-1.el5_5.1|(none)
ppp-2.4.4-2.el5|(none)
prelink-0.4.0-2.el5|(none)
procmail-3.22-17.1.el5.centos|(none)
procps-3.2.7-16.el5|(none)
psacct-6.3.2-44.el5|(none)
psmisc-22.2-7|(none)
pstack-1.2-7.2.2|(none)
pvs-3.2.1-1|(none)
pycairo-1.2.0-1.1|(none)
pygobject2-2.12.1-5.el5|(none)
pygtk2-2.10.1-12.el5|(none)
pyorbit-2.14.1-3.el5|(none)
pyspi-0.6.1-1.el5|(none)
python-2.4.3-27.el5_5.3|(none)
python-elementtree-1.2.6-5|(none)
python-iniparse-0.2.3-4.el5|(none)
python-ldap-2.2.0-2.1|0
python-numeric-23.7-2.2.2|(none)
python-sqlite-1.1.7-1.2.1|(none)
python-urlgrabber-3.1.0-5.el5|(none)
quota-3.13-1.2.5.el5|1
rcs-5.7-30.1|(none)
rdate-1.4-8.el5|(none)
rdist-6.1.5-44|1
readahead-1.3-8.el5|1
readline-5.1-3.el5|(none)
redhat-logos-4.9.99-11.el5.centos|(none)
redhat-lsb-3.1-12.3.EL.el5.centos|(none)
redhat-menus-6.7.8-3.el5|(none)
redhat-rpm-config-8.0.45-32.el5.centos|(none)
rhpl-0.194.1-1|(none)
rmt-0.4b41-4.el5|(none)
rng-utils-2.0-1.14.1.fc6|1
rootfiles-8.1-1.1.1|(none)
rp-pppoe-3.5-32.1|(none)
rpm-4.4.2.3-20.el5_5.1|(none)
rpm-build-4.4.2.3-20.el5_5.1|(none)
rpm-libs-4.4.2.3-20.el5_5.1|(none)
rpm-python-4.4.2.3-20.el5_5.1|(none)
rsh-0.17-40.el5|(none)
rsync-2.6.8-3.1|(none)
sed-4.1.5-5.fc6|(none)
selinux-policy-2.4.6-279.el5_5.2|(none)
selinux-policy-targeted-2.4.6-279.el5_5.2|(none)
sendmail-8.13.8-8.el5|(none)
setarch-2.0-1.1|(none)
setools-3.0-3.el5|(none)
setserial-2.17-19.2.2|(none)
setup-2.5.58-7.el5|(none)
setuptool-1.19.2-1.el5.centos|(none)
sgpio-1.2.0_10-2.el5|(none)
shadow-utils-4.0.17-15.el5|2
shared-mime-info-0.19-5.el5|(none)
slang-2.0.6-4.el5|(none)
smartmontools-5.38-2.el5|1
sos-1.7-9.49.el5|(none)
specspo-13-1.el5.centos|(none)
splint-3.1.1-16.el5|(none)
sqlite-3.3.6-5|(none)
squashfs-tools-3.0-4|(none)
startup-notification-0.8-4.1|(none)
strace-4.5.18-5.el5_5.5|(none)
stunnel-4.15-2.el5.1|(none)
subversion-1.4.2-4.el5_3.1|(none)
subversion-devel-1.4.2-4.el5_3.1|(none)
sudo-1.7.2p1-9.el5_5|(none)
swig-1.3.29-2.el5|(none)
symlinks-1.2-24.2.2|(none)
sysfsutils-2.0.0-6|(none)
sysklogd-1.4.1-46.el5|(none)
syslinux-3.11-4|(none)
system-config-network-tui-1.3.99.18-1.el5|(none)
system-config-securitylevel-tui-1.6.29.1-5.el5|(none)
systemtap-1.1-3.el5_5.3|(none)
systemtap-runtime-1.1-3.el5_5.3|(none)
talk-0.17-29.2.2|(none)
tar-1.15.1-30.el5|2
tcl-8.4.13-4.el5|(none)
tcp_wrappers-7.6-40.7.el5|(none)
tcpdump-3.9.4-15.el5|14
tcsh-6.14-17.el5_5.2|(none)
telnet-0.17-39.el5|1
termcap-5.5-1.20060701.1|1
texinfo-4.8-14.el5|(none)
time-1.7-27.2.2|(none)
tmpwatch-2.9.7-1.1.el5.2|(none)
traceroute-2.0.1-5.el5|3
tree-1.5.0-4|(none)
trousers-0.3.1-4.el5|(none)
ttmkfdir-3.0.9-23.el5|(none)
tzdata-2010l-1.el5|(none)
udev-095-14.21.el5_5.1|(none)
udftools-1.0.0b3-0.1.el5|(none)
unix2dos-2.2-26.2.3.el5|(none)
unzip-5.52-3.el5|(none)
usbutils-0.71-2.1|(none)
usermode-1.88-3.el5.2|(none)
util-linux-2.13-0.52.el5_4.1|(none)
valgrind-3.5.0-1.el5|1
vconfig-1.9-3|(none)
vim-minimal-7.0.109-6.el5|2
vixie-cron-4.1-77.el5_4.1|4
wget-1.11.4-2.el5_4.1|(none)
which-2.16-7|(none)
wireless-tools-28-2.el5|1
words-3.0-9.1|(none)
wpa_supplicant-0.5.10-9.el5|1
xorg-x11-filesystem-7.1-2.fc6|(none)
xorg-x11-font-utils-7.1-2|1
xorg-x11-fonts-base-7.1-2.1.el5|(none)
xorg-x11-server-Xvfb-1.1.1-48.76.el5_5.2|(none)
xorg-x11-server-utils-7.1-4.fc6|(none)
xorg-x11-xauth-1.0.1-2.1|1
xorg-x11-xfs-1.0.2-4|1
xorg-x11-xinit-1.0.2-15.el5|(none)
yp-tools-2.9-1.el5|(none)
ypbind-1.19-12.el5|3
yum-3.2.22-26.el5.centos|(none)
yum-fastestmirror-1.1.16-14.el5.centos.1|(none)
yum-metadata-parser-1.1.2-3.el5.centos|(none)
yum-updatesd-0.9-2.el5|1
zip-2.31-2.el5|(none)
zlib-1.2.3-3|(none)
zlib-devel-1.2.3-3|(none)
Description
This plugin lists the software installed on the remote host by calling
the appropriate command (rpm -qa on RPM-based Linux distributions,
qpkg, dpkg, etc...)
Solution
Remove any software that is not in compliance with your
organization's acceptable use and security policies.
Risk Factor
None
Plugin last modification date: 2011/03/07
Port (59695/udp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/usr/sbin/avahi-daemon' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (49755/udp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/opt/nessus/sbin/nessusd' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (42555/udp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/opt/nessus/sbin/nessusd' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (35295/udp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/usr/sbin/avahi-daemon' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port www (8834/tcp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/opt/nessus/sbin/nessusd' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (5353/udp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/usr/sbin/avahi-daemon' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port pvs_proxy (1243/tcp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/opt/pvs/bin/pvs-proxy' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port nessus (1241/tcp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/opt/nessus/sbin/nessusd' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port rpc-status (792/tcp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/sbin/rpc.statd' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port rpc-status (789/udp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/sbin/rpc.statd' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (786/udp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/sbin/rpc.statd' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (631/udp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/usr/sbin/cupsd' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port rpc-portmapper (111/udp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/sbin/portmap' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port ssh (22/tcp)
Plugin ID: 25221
Remote listeners enumeration
Synopsis
Using netstat, it is possible to identify daemons listening on the remote
port.
List of Hosts Plugin Output
192.168.1.13
The Linux process '/usr/sbin/sshd' is listening on this port.
Description
By logging into the remote host and using the Linux-specific 'netstat
-anp' command, it was possible to obtain the name of the processe
listening on the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port cifs (445/tcp)
Plugin ID: 10400
Microsoft Windows SMB Registry Remotely Accessible
Synopsis
Access the remote Windows Registry.
List of Hosts
192.168.1.215
Description
It was possible to access the remote Windows Registry using the login
/ password combination used for the Windows local checks (SMB tests).
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/04
Port (8834/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output Plugin Output
192.168.1.13
An HTTP proxy is running on this port.
192.168.1.13
A web server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (8089/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output Plugin Output
192.168.1.180
A web server is running on this port through SSLv2.
192.168.1.180
An SSLv2 server answered on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (8060/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output Plugin Output
192.168.1.237
A web server is running on this port.
192.168.1.227
A web server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (8000/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.180
A web server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (5902/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.14
A vnc server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (5901/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.14
A vnc server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (5900/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output Plugin Output Plugin Output
192.168.1.66
A vnc server is running on this port.
192.168.1.60
A vnc server is running on this port.
192.168.1.233
A vnc server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (5800/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.66
A web server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (4444/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.79
A web server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (3689/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output Plugin Output Plugin Output
192.168.1.66
A web server is running on this port.
192.168.1.60
A web server is running on this port.
192.168.1.234
A web server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (1243/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.13
A TLSv1 server answered on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (1241/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.13
A TLSv1 server answered on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (631/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.30
A web server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (593/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.180
An http-rpc-epmap is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port www (443/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.79
A web server is running on this port through TLSv1.
192.168.1.79
A TLSv1 server answered on this port.
192.168.1.26
A web server is running on this port through SSLv2.
192.168.1.26
An SSLv2 server answered on this port.
192.168.1.16
A web server is running on this port.
192.168.1.11
A web server is running on this port through TLSv1.
192.168.1.11
A TLSv1 server answered on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (88/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.233
A Kerberos ticket server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port www (80/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.98
A web server is running on this port.
192.168.1.95
A web server is running on this port.
192.168.1.80
A web server is running on this port.
192.168.1.79
A web server is running on this port.
192.168.1.65
A web server is running on this port.
192.168.1.26
A web server is running on this port.
192.168.1.16
A web server is running on this port.
192.168.1.1
A web server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (23/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output Plugin Output
192.168.1.98
A telnet server is running on this port.
192.168.1.95
A telnet server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port ssh (22/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.98
An SSH server is running on this port.
192.168.1.95
An SSH server is running on this port.
192.168.1.66
An SSH server is running on this port.
192.168.1.60
An SSH server is running on this port.
192.168.1.26
An SSH server is running on this port.
192.168.1.233
An SSH server is running on this port.
192.168.1.19
An SSH server is running on this port.
192.168.1.18
An SSH server is running on this port.
192.168.1.14
An SSH server is running on this port.
192.168.1.13
An SSH server is running on this port.
192.168.1.11
An SSH server is running on this port.
192.168.1.10
An SSH server is running on this port.
192.168.1.1
An SSH server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port ldap (389/tcp)
Plugin ID: 10723
LDAP Server NULL Bind Connection Information Disclosure
Synopsis
The remote LDAP server allows anonymous access.
List of Hosts
192.168.1.180
Description
The LDAP server on the remote host is currently configured such that a
user can connect to it without authentication - via a 'NULL BIND' -
and query it for information. Although the queries that are allowed
are likely to be fairly restricted, this may result in disclosure of
information that an attacker could find useful.
Note that version 3 of the LDAP protocol requires that a server allow
anonymous access -- a 'NULL BIND' -- to the root DSA-Specific Entry
(DSE) even though it may still require authentication to perform other
queries. As such, this finding may be a false-positive.
Solution
Unless the remote LDAP server supports LDAP v3, configure it to
disallow NULL BINDs.
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Other references
OSVDB:9723
Plugin publication date: 2001/08/13
Plugin last modification date: 2011/03/11
Port www (80/tcp)
Plugin ID: 11213
HTTP TRACE / TRACK Methods Allowed
Synopsis
Debugging functions are enabled on the remote web server.
List of Hosts Plugin Output
192.168.1.26
To disable these methods, add the following lines for each virtual
host in your configuration file :
RewriteEngine on
RewriteCond %{REQUEST_METHOD} ^(TRACE|TRACK)
RewriteRule .* - [F]
Alternatively, note that Apache versions 1.3.34, 2.0.55, and 2.2
support disabling the TRACE method natively via the 'TraceEnable'
directive.
Nessus sent the following TRACE request :
------------------------------ snip ------------------------------
TRACE /Nessus1771966430.html HTTP/1.1
Connection: Close
Host: 192.168.1.26
Pragma: no-cache
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0)
Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, image/png, */*
Accept-Language: en
Accept-Charset: iso-8859-1,*,utf-8
------------------------------ snip ------------------------------
and received the following response from the remote server :
------------------------------ snip ------------------------------
HTTP/1.1 200 OK
Date: Wed, 13 Apr 2011 16:58:42 GMT
Server: Apache/2.2.8 (Ubuntu) mod_fastcgi/2.4.6 PHP/5.2.4-2ubuntu5.9 with Suhosin-Patch mod_ssl/2.2.8 OpenSSL/0.9.8g
Keep-Alive: timeout=15, max=100
Connection: Keep-Alive
Transfer-Encoding: chunked
Content-Type: message/http
TRACE /Nessus1771966430.html HTTP/1.1
Connection: Keep-Alive
Host: 192.168.1.26
Pragma: no-cache
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0)
Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, image/png, */*
Accept-Language: en
Accept-Charset: iso-8859-1,*,utf-8
------------------------------ snip ------------------------------
Description
The remote webserver supports the TRACE and/or TRACK methods. TRACE
and TRACK are HTTP methods that are used to debug web server
connections.
Solution
Disable these methods. Refer to the plugin output for more information.
See also
http://www.cgisecurity.com/whitehat-mirror/WH-WhitePaper_XST_ebook.pdf
http://www.apacheweek.com/issues/03-01-24
http://www.kb.cert.org/vuls/id/288308
http://www.kb.cert.org/vuls/id/867593
http://sunsolve.sun.com/search/document.do?assetkey=1-66-200942-1
Risk Factor
Medium/ CVSS Base Score: 4.3
(CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N)
CVSS Temporal Score: 3.9(CVSS2#E:F/RL:W/RC:C)
Other references
OSVDB:877
OSVDB:3726
OSVDB:5648
OSVDB:50485
CWE:16
Plugin publication date: 2003/01/23
Plugin last modification date: 2011/03/17
Ease of exploitability: Exploits are available
Port ntp (123/udp)
Plugin ID: 43156
NTP ntpd Mode 7 Error Response Packet Loop Remote DoS
Synopsis
The remote network time service has a denial of service
vulnerability.
List of Hosts
192.168.1.234
Description
The version of ntpd running on the remote host has a denial of
service vulnerability. It responds to mode 7 error packets with its
own mode 7 error packets. A remote attacker could exploit this by
sending a mode 7 error response with a spoofed IP header, setting the
source and destination IP addresses to the IP address of the target.
This would cause ntpd to respond to itself endlessly, consuming
excessive amounts of CPU, resulting in a denial of service.
Solution
Upgrade to NTP 4.2.4p8 or later.
Risk Factor
Medium/ CVSS Base Score: 6.4
(CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:P)
CVSS Temporal Score: 5.3(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2009-3563
Bugtraq ID
37255
Other references
OSVDB:60847
CERT:568372
Secunia:37629
Patch publication date: 2009/12/08
Plugin publication date: 2009/12/14
Plugin last modification date: 2011/03/11
Ease of exploitability: Exploits are available
Port (3389/tcp)
Plugin ID: 30218
Terminal Services Encryption Level is not FIPS-140 Compliant
Synopsis
The remote host is not FIPS-140 compliant.
List of Hosts Plugin Output Plugin Output
192.168.1.215
The terminal services encryption level is set to :
2. Medium (Client Compatible)
192.168.1.16
The terminal services encryption level is set to :
2. Medium (Client Compatible)
Description
The encryption setting used by the remote Terminal Services service
is not FIPS-140 compliant.
Solution
Change RDP encryption level to :
4. FIPS Compliant
Risk Factor
Low/ CVSS Base Score: 2.6
(CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/04/04
Port nessus (1241/tcp)
Plugin ID: 10147
Nessus Server Detection
Synopsis
A Nessus daemon is listening on the remote port.
List of Hosts
192.168.1.13
Description
A Nessus daemon is listening on the remote port. It is not
recommended to let anyone connect to this port.
Also, make sure that the remote Nessus installation has been
authorized.
Solution
Filter incoming traffic to this port.
Risk Factor
None
Plugin last modification date: 2011/03/11
Port cifs (445/tcp)
Plugin ID: 17651
Microsoft Windows SMB : Obtains the Password Policy
Synopsis
It is possible to retrieve the remote host's password policy using the
supplied credentials.
List of Hosts Plugin Output
192.168.1.30
The following password policy is defined on the remote host:
Minimum password len: 5
Password history len: 0
Maximum password age (d): No limit
Password must meet complexity requirements: Disabled
Minimum password age (d): 0
Forced logoff time (s): Not set
Locked account time (s): 1800
Time between failed logon (s): 1800
Number of invalid logon before locked out (s): 0
Description
Using the supplied credentials it was possible to extract the
password policy for the remote Windows host. The password policy must
conform to the Informational System Policy.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/04
Port www (4444/tcp)
Plugin ID: 11140
Web Server UDDI Detection
Synopsis
The remote web server operates a business-oriented web services
registry.
List of Hosts
192.168.1.79
Description
The remote web server supports Universal Description, Discovery, and
Integration (UDDI) requests, which are a standard way for businesses
to publish service listings.
Solution
n/a
See also
http://en.wikipedia.org/wiki/UDDI
Risk Factor
None
Plugin last modification date: 2011/03/11
Port pvs_proxy (1243/tcp)
Plugin ID: 46212
PVS Proxy Detection
Synopsis
A proxy service is listening on this port.
List of Hosts
192.168.1.13
Description
The remote service appears to be a Tenable Network Security proxy for
either the Passive Vulnerability Scanner (PVS) or the Security Center
3 proxy.
PVS monitors network traffic in real-time, detecting server and client
vulnerabilities, and a PVS proxy is used by Tenable's SecurityCenter 4
to transfer report data between a PVS sensor and a SecurityCenter
console.
The Security Center 3 proxy is in place for legacy communication
requirements.
Solution
Limit incoming traffic to this port if desired.
See also
http://www.nessus.org/products/pvs/
Risk Factor
None
Plugin last modification date: 2011/03/11
Port ldap (389/tcp)
Plugin ID: 10722
LDAP NULL BASE Search Access
Synopsis
The remote LDAP server may disclose sensitive information.
List of Hosts
192.168.1.180
Description
The remote LDAP server supports search requests with a null, or empty,
base object. This allows information to be retrieved without any
prior knowledge of the directory structure. Coupled with a NULL BIND,
an anonymous user may be able to query your LDAP server using a tool
such as 'LdapMiner'.
Note that there are valid reasons to allow queries with a null base.
For example, it is required in version 3 of the LDAP protocol to
provide access to the root DSA-Specific Entry (DSE), with information
about the supported naming context, authentication types, and the
like. It also means that legitimate users can find information in the
directory without any a priori knowledge of its structure. As such,
this finding may be a false-positive.
Solution
If the remote LDAP server supports a version of the LDAP protocol
before v3, consider whether to disable NULL BASE queries on your LDAP
server.
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/11
Port rpc-status (938/tcp)
Plugin ID: 11111
RPC Services Enumeration
Synopsis
An ONC RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.18
The following RPC services are available on TCP port 938 :
- program: 100024 (status), version: 1
Description
By sending a DUMP request to the portmapper, it was possible to
enumerate the ONC RPC services running on the remote port. Using this
information, it is possible to connect and bind to each service by
sending an RPC request to the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port rpc-status (935/udp)
Plugin ID: 11111
RPC Services Enumeration
Synopsis
An ONC RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.18
The following RPC services are available on UDP port 935 :
- program: 100024 (status), version: 1
Description
By sending a DUMP request to the portmapper, it was possible to
enumerate the ONC RPC services running on the remote port. Using this
information, it is possible to connect and bind to each service by
sending an RPC request to the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port (792/tcp)
Plugin ID: 11111
RPC Services Enumeration
Synopsis
An ONC RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.13
The following RPC services are available on TCP port 792 :
- program: 100024 (status), version: 1
Description
By sending a DUMP request to the portmapper, it was possible to
enumerate the ONC RPC services running on the remote port. Using this
information, it is possible to connect and bind to each service by
sending an RPC request to the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port (789/udp)
Plugin ID: 11111
RPC Services Enumeration
Synopsis
An ONC RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.13
The following RPC services are available on UDP port 789 :
- program: 100024 (status), version: 1
Description
By sending a DUMP request to the portmapper, it was possible to
enumerate the ONC RPC services running on the remote port. Using this
information, it is possible to connect and bind to each service by
sending an RPC request to the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port rpc-portmapper (111/udp)
Plugin ID: 11111
RPC Services Enumeration
Synopsis
An ONC RPC service is running on the remote host.
List of Hosts Plugin Output Plugin Output Plugin Output
192.168.1.30
The following RPC services are available on UDP port 111 :
- program: 100000 (portmapper), version: 2
192.168.1.18
The following RPC services are available on UDP port 111 :
- program: 100000 (portmapper), version: 2
192.168.1.13
The following RPC services are available on UDP port 111 :
- program: 100000 (portmapper), version: 2
Description
By sending a DUMP request to the portmapper, it was possible to
enumerate the ONC RPC services running on the remote port. Using this
information, it is possible to connect and bind to each service by
sending an RPC request to the remote port.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port (0/tcp)
Plugin ID: 45432
Processor Information (via DMI)
Synopsis
Information about the remote system's processor can be read.
List of Hosts Plugin Output
192.168.1.13
Current Speed : 2666 MHz
Version : Intel(R) Celeron(R) D CPU 2.66GHz
Manufacturer : Intel
External Clock : 133 MHz
Family : Celeron
Type : Central Processor
Description
Using the SMBIOS (aka DMI) interface, it was possible to retrieve
information about the remote system's hardware, such as its processor
type.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (0/tcp)
Plugin ID: 46180
Additional DNS Hostnames
Synopsis
Potential virtual hosts have been detected.
List of Hosts Plugin Output
192.168.1.26
- movabletype
Description
Hostnames different from the current hostname have been collected by
miscellaneous plugins. Different web servers may be hosted on name-
based virtual hosts.
Solution
If you want to test them, re-scan using the special vhost syntax,
such as :
www.example.com[192.0.32.10]
Risk Factor
None
Plugin last modification date: 2011/03/26
Port (0/tcp)
Plugin ID: 46215
Inconsistent Hostname and IP Address
Synopsis
The remote host's hostname is not consistent with DNS information.
List of Hosts Plugin Output
192.168.1.80
The host name 'xbox-main-office' does not resolve to an IP address
Description
The name of this machine either does not resolve or resolves to a
different IP address.
This may come from a badly configured reverse DNS or from a host file
in use on the Nessus scanning host.
As a result, URLs in plugin output may not be directly usable in a web
browser and some web tests may be incomplete.
Solution
Fix the reverse DNS or host file.
Risk Factor
None
Plugin last modification date: 2011/03/26
Port pvs_proxy (1243/tcp)
Plugin ID: 35291
SSL Certificate Signed using Weak Hashing Algorithm
Synopsis
The SSL certificate has been signed using a weak hash algorithm.
List of Hosts Plugin Output
192.168.1.13
Here is the service's SSL certificate :
Subject Name:
Country: US
State/Province: none
Locality: Columbia
Organization: Tenable Users United
Organization Unit: Server certificate for gogo
Common Name: gogo
Email Address: pvsd@gogo
Issuer Name:
Country: US
State/Province: none
Locality: Columbia
Organization: Tenable Users United
Organization Unit: Certification Authority for gogo
Common Name: gogo
Email Address: ca@gogo
Serial Number: 01
Version: 3
Signature Algorithm: MD5 With RSA Encryption
Not Valid Before: Feb 21 19:03:25 2011 GMT
Not Valid After: Feb 21 19:03:25 2012 GMT
Public Key Info:
Algorithm: RSA Encryption
Public Key: 00 C6 33 F1 C2 18 C8 61 54 6F 19 04 0A 36 52 BE 31 38 74 86
D5 4C 8B 2F 39 2E E5 CD 32 97 C7 90 D0 20 80 82 A4 09 8A 10
FB 57 5A 82 D0 75 C4 E6 E9 C5 D1 DA 2C 15 40 DE 21 82 2C C1
D6 95 72 14 84 73 83 9A 8D 0E 13 75 7E CF 4A B5 BA 83 82 66
44 6F 98 70 D6 3F 9D 06 73 62 F1 A0 C6 A2 9F B6 58 8F 5E 62
D7 4E 02 80 55 7D 8A 04 17 8A 14 36 66 FD 63 A1 54 11 B9 C8
0D 70 8D 41 52 26 3D 7C 45
Exponent: 01 00 01
Signature: 00 88 44 24 00 19 DC 61 BC 77 29 8A 5A B0 5C C1 95 D1 DE 88
68 B0 17 5D 32 A2 B7 BE 99 CA 25 F1 21 F7 FF 2F BE 63 66 4D
B3 A0 F0 08 5D A5 1F E2 9A CB 7E 57 B5 20 64 EE 3C 98 45 39
8F 8C A6 53 EF EE 39 18 EC 6F C8 77 8C A8 3B 11 B6 92 3E 16
17 D7 1F 36 03 B8 54 3B 65 9C B7 45 AA 9F A7 E1 55 CD E6 76
0F 0D 4F F8 AB CD A1 8C 1B 51 BF 3E 09 DD 55 7B 56 EF 84 0B
A1 BC EE 19 01 C1 53 28 56
Extension: 2.16.840.1.113730.1.1
Critical: 0
Data: 03 02 06 40
Extension: Key Usage (2.5.29.15)
Critical: 0
Key Usage: Digital Signature, Non Repudiation, Key Encipherment
Extension: Comment (2.16.840.1.113730.1.13)
Critical: 0
Comment: OpenSSL Generated Certificate
Extension: Subject Key Identifier (2.5.29.14)
Critical: 0
Subject Key Identifier: 3C 84 F9 30 0E 83 DB 01 16 A1 1D 23 D5 D2 DF 79 18 D6 BD 5D
Extension: Authority Key Identifier (2.5.29.35)
Critical: 0
Extension: Subject Alternative Name (2.5.29.17)
Critical: 0
Extension: Issuer Alternative Name (2.5.29.18)
Critical: 0
Data: 30 00
Description
The remote service uses an SSL certificate that has been signed using
a cryptographically weak hashing algorithm - MD2, MD4, or MD5. These
signature algorithms are known to be vulnerable to collision attacks.
In theory, a determined attacker may be able to leverage this weakness
to generate another certificate with the same digital signature, which
could allow him to masquerade as the affected service.
Solution
Contact the Certificate Authority to have the certificate reissued.
See also
http://tools.ietf.org/html/rfc3279
http://www.phreedom.org/research/rogue-ca/
http://www.microsoft.com/technet/security/advisory/961509.mspx
http://www.kb.cert.org/vuls/id/836068
Risk Factor
Medium/ CVSS Base Score: 4.0
(CVSS2#AV:N/AC:H/Au:N/C:P/I:P/A:N)
CVSS Temporal Score: 3.3(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2004-2761
Other references
OSVDB:45106
OSVDB:45108
OSVDB:45127
CWE:310
Plugin last modification date: 2011/03/17
Ease of exploitability: Exploits are available
Port www (3689/tcp)
Plugin ID: 45391
iTunes < 9.1 Multiple Vulnerabilities (uncredentialed check)
Synopsis
The remote host contains an application that is affected by multiple
vulnerabilities.
List of Hosts Plugin Output
192.168.1.60
iTunes 8.2.1 appears to be running on the remote host based on the
following response header :
DAAP-Server: iTunes/8.2.1 (Mac OS X)
Description
The remote version of iTunes is older than 9.1. Such versions may be
affected by multiple vulnerabilities :
- A buffer underflow in ImageIO's handling of TIFF images
may lead to an application crash or arbitrary code
execution. (CVE-2009-2285)
- An integer overflow in the applications's handling of
images with an embedded color profile may lead to an
application crash or arbitrary code execution.
(CVE-2010-0040)
- An uninitialized memory access issue in ImageIO's
handling of BMP images may result in sending data from
Safari's memory to a website under an attacker's
control. (CVE-2010-0041)
- An uninitialized memory access issue in ImageIO's
handling of TIFF images may result in sending data from
Safari's memory to a website under an attacker's
control. (CVE-2010-0042)
- A memory corruption issue in the application's handling
of TIFF images may lead to an application crash or
arbitrary code execution. (CVE-2010-0043)
- An infinite loop in the application's handling of
imported MP4 podcast files may lead to an application
crash and prevent subsequent operation. (CVE-2010-0531)
- A race condition during the installation process may
allow a local user modify a file that is then executed
with SYSTEM privileges. (CVE-2010-0532)
- A path searching issue may allow code execution if an
attacker can place a specially crafted DLL in a
directory and have a user open another file using
iTunes in that directory. (CVE-2010-1795)
- Syncing a mobile device may allow a local user to gain
the privileges of the console user due to an insecure
file operation in the handling of log files.
(CVE-2010-1768)
Solution
Upgrade to iTunes 9.1 or later.
See also
http://support.apple.com/kb/HT4105
http://lists.apple.com/archives/security-announce/2010/mar/msg00003.html
http://www.securityfocus.com/advisories/19388
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2009-2285
CVE-2010-0040
CVE-2010-0041
CVE-2010-0042
CVE-2010-0043
CVE-2010-0531
CVE-2010-0532
CVE-2010-1768
CVE-2010-1795
Other references
OSVDB:55265
OSVDB:62933
OSVDB:62934
OSVDB:62935
OSVDB:62936
OSVDB:62949
OSVDB:62950
OSVDB:63449
OSVDB:63450
OSVDB:67329
OSVDB:67332
CWE:119
Patch publication date: 2010/03/30
Plugin publication date: 2010/03/31
Plugin last modification date: 2011/03/08
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 10428
Microsoft Windows SMB Fully Accessible Registry Detection
Synopsis
Nessus had insufficient access to the remote registry.
List of Hosts
192.168.1.215
Description
Nessus did not access the remote registry completely,
because this needs to be logged in as administrator.
If you want the permissions / values of all the sensitive
registry keys to be checked for, we recommend that you fill
the 'SMB Login' options in the 'Windows credentials' section
of the policy by the administrator login name and password.
Solution
Use an administrator level account for scanning.
Risk Factor
None
Plugin last modification date: 2011/03/04
Port vnc (5902/tcp)
Plugin ID: 10342
VNC Software Detection
Synopsis
The remote host is running a remote display software (VNC).
List of Hosts Plugin Output
192.168.1.14
The highest RFB protocol version supported by the server is :
3.8
Description
The remote host is running VNC (Virtual Network Computing), which uses
the RFB (Remote Framebuffer) protocol to provide remote access to
graphical user interfaces and thus permits a console on the remote
host to be displayed on another.
Solution
Make sure use of this software is done in accordance with your
organization's security policy and filter incoming traffic to this
port.
See also
http://en.wikipedia.org/wiki/Vnc
Risk Factor
None
Plugin last modification date: 2011/04/01
Port vnc (5901/tcp)
Plugin ID: 10342
VNC Software Detection
Synopsis
The remote host is running a remote display software (VNC).
List of Hosts Plugin Output
192.168.1.14
The highest RFB protocol version supported by the server is :
3.8
Description
The remote host is running VNC (Virtual Network Computing), which uses
the RFB (Remote Framebuffer) protocol to provide remote access to
graphical user interfaces and thus permits a console on the remote
host to be displayed on another.
Solution
Make sure use of this software is done in accordance with your
organization's security policy and filter incoming traffic to this
port.
See also
http://en.wikipedia.org/wiki/Vnc
Risk Factor
None
Plugin last modification date: 2011/04/01
Port (5900/tcp)
Plugin ID: 10342
VNC Software Detection
Synopsis
The remote host is running a remote display software (VNC).
List of Hosts Plugin Output Plugin Output Plugin Output
192.168.1.66
The highest RFB protocol version supported by the server is :
3.3
192.168.1.60
The highest RFB protocol version supported by the server is :
3.889
192.168.1.233
The highest RFB protocol version supported by the server is :
3.889
Description
The remote host is running VNC (Virtual Network Computing), which uses
the RFB (Remote Framebuffer) protocol to provide remote access to
graphical user interfaces and thus permits a console on the remote
host to be displayed on another.
Solution
Make sure use of this software is done in accordance with your
organization's security policy and filter incoming traffic to this
port.
See also
http://en.wikipedia.org/wiki/Vnc
Risk Factor
None
Plugin last modification date: 2011/04/01
Port www (3000/tcp)
Plugin ID: 42873
SSL Medium Strength Cipher Suites Supported
Synopsis
The remote service supports the use of medium strength SSL ciphers.
List of Hosts Plugin Output
192.168.1.26
Here are the medium strength SSL ciphers supported by the remote server :
Medium Strength Ciphers (>= 56-bit and < 112-bit key)
SSLv2
DES-CBC-MD5 Kx=RSA Au=RSA Enc=DES(56) Mac=MD5
SSLv3
EDH-RSA-DES-CBC-SHA Kx=DH Au=RSA Enc=DES(56) Mac=SHA1
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1
TLSv1
EDH-RSA-DES-CBC-SHA Kx=DH Au=RSA Enc=DES(56) Mac=SHA1
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Description
The remote host supports the use of SSL ciphers that offer medium
strength encryption, which we currently regard as those with key
lengths at least 56 bits and less than 112 bits.
Note: This is considerably easier to exploit if the attacker is on the
same physical network.
Solution
Reconfigure the affected application if possible to avoid use of
medium strength ciphers.
Risk Factor
Medium/ CVSS Base Score: 4.3
(CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/21
Port (1243/tcp)
Plugin ID: 42873
SSL Medium Strength Cipher Suites Supported
Synopsis
The remote service supports the use of medium strength SSL ciphers.
List of Hosts Plugin Output
192.168.1.13
Here is the only medium strength SSL cipher supported by the remote server :
Medium Strength Ciphers (>= 56-bit and < 112-bit key)
TLSv1
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Description
The remote host supports the use of SSL ciphers that offer medium
strength encryption, which we currently regard as those with key
lengths at least 56 bits and less than 112 bits.
Note: This is considerably easier to exploit if the attacker is on the
same physical network.
Solution
Reconfigure the affected application if possible to avoid use of
medium strength ciphers.
Risk Factor
Medium/ CVSS Base Score: 4.3
(CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/21
Port www (443/tcp)
Plugin ID: 42873
SSL Medium Strength Cipher Suites Supported
Synopsis
The remote service supports the use of medium strength SSL ciphers.
List of Hosts Plugin Output
192.168.1.26
Here are the medium strength SSL ciphers supported by the remote server :
Medium Strength Ciphers (>= 56-bit and < 112-bit key)
SSLv2
DES-CBC-MD5 Kx=RSA Au=RSA Enc=DES(56) Mac=MD5
SSLv3
EDH-RSA-DES-CBC-SHA Kx=DH Au=RSA Enc=DES(56) Mac=SHA1
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1
TLSv1
EDH-RSA-DES-CBC-SHA Kx=DH Au=RSA Enc=DES(56) Mac=SHA1
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Description
The remote host supports the use of SSL ciphers that offer medium
strength encryption, which we currently regard as those with key
lengths at least 56 bits and less than 112 bits.
Note: This is considerably easier to exploit if the attacker is on the
same physical network.
Solution
Reconfigure the affected application if possible to avoid use of
medium strength ciphers.
Risk Factor
Medium/ CVSS Base Score: 4.3
(CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/21
Port dns (53/tcp)
Plugin ID: 10595
DNS Server Zone Tranfer Information Disclosure (AXFR)
Synopsis
The remote name server allows zone transfers
List of Hosts
192.168.1.10
Description
The remote name server allows DNS zone transfers to be performed.
A zone transfer lets a remote attacker instantly populate a list of
potential targets. In addition, companies often use a naming
convention that can give hints as to a servers primary application
(for instance, proxy.example.com, payroll.example.com,
b2b.example.com, etc.).
As such, this information is of great use to an attacker, who may use
it to gain information about the topology of the network and spot new
targets.
Solution
Limit DNS zone transfers to only the servers that need the
information.
See also
http://en.wikipedia.org/wiki/AXFR
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
CVE
CVE-1999-0532
Other references
OSVDB:492
Plugin publication date: 2001/01/16
Plugin last modification date: 2011/03/11
Port ssh (22/tcp)
Plugin ID: 10882
SSH Protocol Version 1 Session Key Retrieval
Synopsis
The remote service offers an insecure cryptographic protocol.
List of Hosts
192.168.1.60
Description
The remote SSH daemon supports connections made using the version 1.33
and/or 1.5 of the SSH protocol.
These protocols are not completely cryptographically safe so they
should not be used.
Solution
Disable compatibility with version 1 of the protocol.
Risk Factor
Medium/ CVSS Base Score: 4.0
(CVSS2#AV:N/AC:H/Au:N/C:P/I:P/A:N)
CVSS Temporal Score: 3.0(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2001-0361
Bugtraq ID
2344
Other references
OSVDB:2116
CWE:310
Plugin publication date: 2002/03/06
Plugin last modification date: 2011/03/21
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 10860
SMB Use Host SID to Enumerate Local Users
Synopsis
It is possible to enumerate local users.
List of Hosts Plugin Output Plugin Output
192.168.1.30
- nobody (id 501, Guest account)
- admin (id 1196)
Note that, in addition to the Administrator and Guest accounts, Nessus
has enumerated only those local users with IDs between 1000 and 1200.
To use a different range, edit the scan policy and change the 'Start
UID' and/or 'End UID' preferences for this plugin, then re-run the
scan.
192.168.1.215
- Administrator (id 500, Administrator account)
- Guest (id 501, Guest account)
- HelpServicesGroup (id 1001)
- SUPPORT_388945a0 (id 1002)
- HelpAssistant (id 1004)
- kirk (id 1005)
- spock (id 1006)
- scotty (id 1007)
Note that, in addition to the Administrator and Guest accounts, Nessus
has enumerated only those local users with IDs between 1000 and 1200.
To use a different range, edit the scan policy and change the 'Start
UID' and/or 'End UID' preferences for this plugin, then re-run the
scan.
Description
Using the host security identifier (SID), it is possible to enumerate local users
on the remote Windows system.
Solution
n/a
Risk Factor
None
CVE
CVE-2000-1200
Bugtraq ID
959
Other references
OSVDB:714
Plugin publication date: 2002/02/13
Plugin last modification date: 2011/03/07
Ease of exploitability: Exploits are available
Port www (443/tcp)
Plugin ID: 19772
Skype Detection
Synopsis
A Voice Over IP service is running on the remote port.
List of Hosts
192.168.1.16
Description
The remote host is running Skype, a peer-to-peer Voice Over IP application.
Due to the peer-to-peer nature of Skype, any user connecting to the Skype
network may consume a large amount of bandwith.
Make sure the use of this program is done in accordance with your corporate
security policy.
Solution
If this service is not needed, disable it. Note that filtering this port will
not be sufficient, since this software can establish outgoing connections.
Risk Factor
None
Plugin last modification date: 2011/03/11
Port www (80/tcp)
Plugin ID: 19772
Skype Detection
Synopsis
A Voice Over IP service is running on the remote port.
List of Hosts
192.168.1.16
Description
The remote host is running Skype, a peer-to-peer Voice Over IP application.
Due to the peer-to-peer nature of Skype, any user connecting to the Skype
network may consume a large amount of bandwith.
Make sure the use of this program is done in accordance with your corporate
security policy.
Solution
If this service is not needed, disable it. Note that filtering this port will
not be sufficient, since this software can establish outgoing connections.
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (67/udp)
Plugin ID: 10663
DHCP Server Detection
Synopsis
The remote DHCP server may expose information about the associated
network.
List of Hosts Plugin Output
192.168.1.10
Nessus gathered the following information from the remote DHCP server :
Master DHCP server of this network : 192.168.1.10
IP address the DHCP server would attribute us : 192.168.1.226
DHCP server(s) identifier : 192.168.1.10
Netmask : 255.255.255.0
Router : 192.168.1.1
Domain name server(s) : 192.168.1.10
Domain name :
Broadcast address : 192.168.1.255
Description
This script contacts the remote DHCP server (if any) and attempts to
retrieve information about the network layout.
Some DHCP servers provide sensitive information such as the NIS domain
name, or network layout information such as the list of the network
web servers, and so on.
It does not demonstrate any vulnerability, but a local attacker may
use DHCP to become intimately familiar with the associated network.
Solution
Apply filtering to keep this information off the network and remove
any options that are not in use.
Risk Factor
Low/ CVSS Base Score: 3.3
(CVSS2#AV:A/AC:L/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/21
Port www (8099/tcp)
Plugin ID: 44319
D-Link Router Detection
Synopsis
The remote device is a D-Link router.
List of Hosts Plugin Output
192.168.1.79
Model : DIR-655 A4
Description : Xtreme N GIGABIT Router
Firmware : 1.33NA, 2010/01/19
Description
The remote device is a D-Link router. These devices route packets
and may provide port forwarding, DMZ configuration and other
networking services.
Solution
Disable this hardware if it violates your corporate policy.
See also
http://www.dlink.com/
Risk Factor
None
Plugin last modification date: 2011/02/26
Port (49177/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49177 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 367abb81-9844-35f1-ad32-98f038001003, version 2.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49177
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port (49176/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49176 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 50abc2a4-574d-40b3-9d66-ee4fd5fba076, version 5.0
Description : DNS Server
Windows process : dns.exe
Type : Remote RPC service
TCP Port : 49176
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port (49163/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49163 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 6b5bdd1e-528c-422c-af8c-a4079be4fe48, version 1.0
Description : Unknown RPC service
Annotation : Remote Fw APIs
Type : Remote RPC service
TCP Port : 49163
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-0123456789ab, version 1.0
Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe
Annotation : IPSec Policy agent endpoint
Type : Remote RPC service
TCP Port : 49163
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port (49161/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49161 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc59b4-4264-101a-8c59-08002b2f8426, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs Service
Type : Remote RPC service
TCP Port : 49161
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : d049b186-814f-11d1-9a3c-00c04fc9b232, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs API
Type : Remote RPC service
TCP Port : 49161
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a00c021c-2be2-11d2-b678-0000f87a8f8e, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : PERFMON SERVICE
Type : Remote RPC service
TCP Port : 49161
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49158/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49158 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49158
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49158
IP : 192.168.1.180
192.168.1.16
The following DCERPC services are available on TCP port 49158 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49158
IP : 192.168.1.16
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49156/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.16
The following DCERPC services are available on TCP port 49156 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 6b5bdd1e-528c-422c-af8c-a4079be4fe48, version 1.0
Description : Unknown RPC service
Annotation : Remote Fw APIs
Type : Remote RPC service
TCP Port : 49156
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-0123456789ab, version 1.0
Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe
Annotation : IPSec Policy agent endpoint
Type : Remote RPC service
TCP Port : 49156
IP : 192.168.1.16
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49155/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49155 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
192.168.1.16
The following DCERPC services are available on TCP port 49155 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 367abb81-9844-35f1-ad32-98f038001003, version 2.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.16
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49154/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49154 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.180
192.168.1.16
The following DCERPC services are available on TCP port 49154 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 552d076a-cb29-4e44-8b6a-d15e59e2c0af, version 1.0
Description : Unknown RPC service
Annotation : IP Transition Configuration endpoint
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 98716d03-89ac-44c7-bb8c-285824e51c4a, version 1.0
Description : Unknown RPC service
Annotation : XactSrv service
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.16
Object UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 58e604e8-9adb-4d2e-a464-3b0683fb1480, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.16
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49153/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49153 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service
Annotation : Event log TCPIP
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.180
192.168.1.16
The following DCERPC services are available on TCP port 49153 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service
Annotation : Event log TCPIP
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30adc50c-5cbc-46ce-9a0e-91914789e23c, version 1.0
Description : Unknown RPC service
Annotation : NRP server endpoint
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.16
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service
Annotation : Security Center
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.16
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49152/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49152 :
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49152
IP : 192.168.1.180
192.168.1.16
The following DCERPC services are available on TCP port 49152 :
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49152
IP : 192.168.1.16
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output Plugin Output
192.168.1.180
The following DCERPC services are available remotely :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service
Annotation : Unimodem LRPC Endpoint
Type : Remote RPC service
Named pipe : \pipe\tapsrv
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Remote RPC service
Named pipe : \PIPE\srvsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service
Annotation : Event log TCPIP
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\InitShutdown
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\InitShutdown
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
192.168.1.16
The following DCERPC services are available remotely :
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\InitShutdown
Netbios name : \\O-REN
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\InitShutdown
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : b58aa02e-2884-4e97-8176-4ee06d794184, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \pipe\trkwks
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0767a036-0d22-48aa-ba69-b619480f38cb, version 1.0
Description : Unknown RPC service
Annotation : PcaSvc
Type : Remote RPC service
Named pipe : \pipe\trkwks
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 552d076a-cb29-4e44-8b6a-d15e59e2c0af, version 1.0
Description : Unknown RPC service
Annotation : IP Transition Configuration endpoint
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 98716d03-89ac-44c7-bb8c-285824e51c4a, version 1.0
Description : Unknown RPC service
Annotation : XactSrv service
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\O-REN
Object UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\O-REN
Object UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Remote RPC service
Named pipe : \PIPE\srvsvc
Netbios name : \\O-REN
Object UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Remote RPC service
Named pipe : \PIPE\browser
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\srvsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\browser
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
Named pipe : \PIPE\srvsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
Named pipe : \PIPE\browser
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
Named pipe : \PIPE\srvsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
Named pipe : \PIPE\browser
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
Named pipe : \PIPE\srvsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
Named pipe : \PIPE\browser
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 58e604e8-9adb-4d2e-a464-3b0683fb1480, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 58e604e8-9adb-4d2e-a464-3b0683fb1480, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
Named pipe : \PIPE\srvsvc
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 58e604e8-9adb-4d2e-a464-3b0683fb1480, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Remote RPC service
Named pipe : \PIPE\browser
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service
Annotation : Event log TCPIP
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30adc50c-5cbc-46ce-9a0e-91914789e23c, version 1.0
Description : Unknown RPC service
Annotation : NRP server endpoint
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\O-REN
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service
Annotation : Security Center
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\O-REN
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port epmap (135/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output Plugin Output
192.168.1.180
The following DCERPC services are available locally :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : securityevent
Object UUID : 3bdb59a0-d736-4d44-9074-c1ee00000001
UUID : 24019106-a203-4642-b88d-82dae9158929, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : LRPC-0ff3c2fc1f213f02ce
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service
Annotation : Unimodem LRPC Endpoint
Type : Local RPC service
Named pipe : tapsrvlpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service
Annotation : Unimodem LRPC Endpoint
Type : Local RPC service
Named pipe : unimdmsvc
Object UUID : 58abe70e-dc51-4f6c-917d-e8cc4f13e1fd
UUID : 906b0ce0-c70b-1067-b317-00dd010662da, version 1.0
Description : Distributed Transaction Coordinator
Windows process : msdtc.exe
Type : Local RPC service
Named pipe : LRPC-3fbda57d0c4803ba9c
Object UUID : 6971a2ac-7f04-4ec5-8d8d-d1d88ee83c48
UUID : 906b0ce0-c70b-1067-b317-00dd010662da, version 1.0
Description : Distributed Transaction Coordinator
Windows process : msdtc.exe
Type : Local RPC service
Named pipe : LRPC-3fbda57d0c4803ba9c
Object UUID : a3b8b0c1-7f58-4ac6-a858-05237e74d876
UUID : 906b0ce0-c70b-1067-b317-00dd010662da, version 1.0
Description : Distributed Transaction Coordinator
Windows process : msdtc.exe
Type : Local RPC service
Named pipe : LRPC-3fbda57d0c4803ba9c
Object UUID : 71ebac49-c98f-40cf-b969-28879f258965
UUID : 906b0ce0-c70b-1067-b317-00dd010662da, version 1.0
Description : Distributed Transaction Coordinator
Windows process : msdtc.exe
Type : Local RPC service
Named pipe : LRPC-3fbda57d0c4803ba9c
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-0123456789ab, version 1.0
Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe
Annotation : IPSec Policy agent endpoint
Type : Local RPC service
Named pipe : LRPC-64636b2001baa70a54
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc59b4-4264-101a-8c59-08002b2f8426, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs Service
Type : Local RPC service
Named pipe : OLE4D00800FB7224E3BA74F6D7F4A40
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc59b4-4264-101a-8c59-08002b2f8426, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs Service
Type : Local RPC service
Named pipe : LRPC-32c9434230805de61a
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : d049b186-814f-11d1-9a3c-00c04fc9b232, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs API
Type : Local RPC service
Named pipe : OLE4D00800FB7224E3BA74F6D7F4A40
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : d049b186-814f-11d1-9a3c-00c04fc9b232, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs API
Type : Local RPC service
Named pipe : LRPC-32c9434230805de61a
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a00c021c-2be2-11d2-b678-0000f87a8f8e, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : PERFMON SERVICE
Type : Local RPC service
Named pipe : OLE4D00800FB7224E3BA74F6D7F4A40
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a00c021c-2be2-11d2-b678-0000f87a8f8e, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : PERFMON SERVICE
Type : Local RPC service
Named pipe : LRPC-32c9434230805de61a
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0b6edbfa-4a24-4fc6-8a23-942b1eca65d1, version 1.0
Description : Unknown RPC service
Annotation : Spooler function endpoint
Type : Local RPC service
Named pipe : spoolss
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : ae33069b-a2a8-46ee-a235-ddfd339be281, version 1.0
Description : Unknown RPC service
Annotation : Spooler base remote object endpoint
Type : Local RPC service
Named pipe : spoolss
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 4a452661-8290-4b36-8fbe-7f4093a94978, version 1.0
Description : Unknown RPC service
Annotation : Spooler function endpoint
Type : Local RPC service
Named pipe : spoolss
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : dd490425-5325-4565-b774-7e27d6c09c24, version 1.0
Description : Unknown RPC service
Annotation : Base Firewall Engine API
Type : Local RPC service
Named pipe : LRPC-eb9e1c5180d5c63bde
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 7f9d11bf-7fb9-436b-a812-b2d50c5d4c03, version 1.0
Description : Unknown RPC service
Annotation : Fw APIs
Type : Local RPC service
Named pipe : LRPC-eb9e1c5180d5c63bde
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2fb92682-6599-42dc-ae13-bd2ca89bd11c, version 1.0
Description : Unknown RPC service
Annotation : Fw APIs
Type : Local RPC service
Named pipe : LRPC-eb9e1c5180d5c63bde
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service
Annotation : NSI server endpoint
Type : Local RPC service
Named pipe : OLEC78F635656704CF5919BEF8848AE
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service
Annotation : NSI server endpoint
Type : Local RPC service
Named pipe : LRPC-ccb919c378b80e784b
Object UUID : 666f7270-6c69-7365-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 736e6573-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 736e6573-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 6c637067-6569-746e-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-3c4ccad02b6d68ae95
Object UUID : 24d1f7c7-76af-4f28-9ccd-7f6cb6468601
UUID : 2eb08e3e-639f-4fba-97b1-14f878961076, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : LRPC-3c4ccad02b6d68ae95
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service
Annotation : Event log TCPIP
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service
Named pipe : dhcpcsvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : dhcpcsvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : dhcpcsvc6
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000001
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc0C3841
Object UUID : 52ef130c-08fd-4388-86b3-6edf00000001
UUID : 12e65dd8-887f-41ef-91bf-8d816c42c2e7, version 1.0
Description : Unknown RPC service
Annotation : Secure Desktop LRPC interface
Type : Local RPC service
Named pipe : WMsgKRpc0C3841
Object UUID : 6d726574-7273-0076-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-e873bdd3ada3ba61b1
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc0C24C0
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WindowsShutdown
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc0C24C0
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WindowsShutdown
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : audit
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : audit
192.168.1.16
The following DCERPC services are available locally :
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WindowsShutdown
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc065EA0
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WindowsShutdown
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc065EA0
Object UUID : 6d726574-7273-0076-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-25042e60342afbce7a
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000001
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc0767A1
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service
Annotation : Security Center
Type : Local RPC service
Named pipe : dhcpcsvc
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000002
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc010E0842
Object UUID : 52ef130c-08fd-4388-86b3-6edf00000002
UUID : 12e65dd8-887f-41ef-91bf-8d816c42c2e7, version 1.0
Description : Unknown RPC service
Annotation : Secure Desktop LRPC interface
Type : Local RPC service
Named pipe : WMsgKRpc010E0842
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 4b112204-0e19-11d3-b42b-0000f81feb9f, version 1.0
Description : SSDP service
Windows process : unknow
Type : Local RPC service
Named pipe : LRPC-99502c96840901627b
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : c100beac-d33a-4a4b-bf23-bbef4663d017, version 1.0
Description : Unknown RPC service
Annotation : wcncsvc.transport
Type : Local RPC service
Named pipe : LRPC-99502c96840901627b
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : c100beac-d33a-4a4b-bf23-bbef4663d017, version 1.0
Description : Unknown RPC service
Annotation : wcncsvc.transport
Type : Local RPC service
Named pipe : OLE0CEFF472F2DF4DAAAA92696F1AC9
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : c100beac-d33a-4a4b-bf23-bbef4663d017, version 1.0
Description : Unknown RPC service
Annotation : wcncsvc.transport
Type : Local RPC service
Named pipe : wcncsvc.transport
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : c100beab-d33a-4a4b-bf23-bbef4663d017, version 1.0
Description : Unknown RPC service
Annotation : wcncsvc.wcnprpc
Type : Local RPC service
Named pipe : LRPC-99502c96840901627b
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : c100beab-d33a-4a4b-bf23-bbef4663d017, version 1.0
Description : Unknown RPC service
Annotation : wcncsvc.wcnprpc
Type : Local RPC service
Named pipe : OLE0CEFF472F2DF4DAAAA92696F1AC9
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : c100beab-d33a-4a4b-bf23-bbef4663d017, version 1.0
Description : Unknown RPC service
Annotation : wcncsvc.wcnprpc
Type : Local RPC service
Named pipe : wcncsvc.transport
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : c100beab-d33a-4a4b-bf23-bbef4663d017, version 1.0
Description : Unknown RPC service
Annotation : wcncsvc.wcnprpc
Type : Local RPC service
Named pipe : wcncsvc.wcnprpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : b58aa02e-2884-4e97-8176-4ee06d794184, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : OLE530C778654FC445A8DAE25FD2613
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : b58aa02e-2884-4e97-8176-4ee06d794184, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : trkwks
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : b58aa02e-2884-4e97-8176-4ee06d794184, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : RemoteDevicesLPC_API
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : b58aa02e-2884-4e97-8176-4ee06d794184, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : TSUMRPD_PRINT_DRV_LPC_API
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0767a036-0d22-48aa-ba69-b619480f38cb, version 1.0
Description : Unknown RPC service
Annotation : PcaSvc
Type : Local RPC service
Named pipe : OLE530C778654FC445A8DAE25FD2613
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0767a036-0d22-48aa-ba69-b619480f38cb, version 1.0
Description : Unknown RPC service
Annotation : PcaSvc
Type : Local RPC service
Named pipe : trkwks
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0767a036-0d22-48aa-ba69-b619480f38cb, version 1.0
Description : Unknown RPC service
Annotation : PcaSvc
Type : Local RPC service
Named pipe : RemoteDevicesLPC_API
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0767a036-0d22-48aa-ba69-b619480f38cb, version 1.0
Description : Unknown RPC service
Annotation : PcaSvc
Type : Local RPC service
Named pipe : TSUMRPD_PRINT_DRV_LPC_API
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : LRPC-ba90735c3065ceee2d
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : LSARPC_ENDPOINT
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : lsapolicylookup
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : lsasspirpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-0123456789ab, version 1.0
Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe
Annotation : IPSec Policy agent endpoint
Type : Local RPC service
Named pipe : LRPC-eb10bf819ed8fe6476
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : dd490425-5325-4565-b774-7e27d6c09c24, version 1.0
Description : Unknown RPC service
Annotation : Base Firewall Engine API
Type : Local RPC service
Named pipe : LRPC-54f8eaf2412c824c9f
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 7f9d11bf-7fb9-436b-a812-b2d50c5d4c03, version 1.0
Description : Unknown RPC service
Annotation : Fw APIs
Type : Local RPC service
Named pipe : LRPC-54f8eaf2412c824c9f
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2fb92682-6599-42dc-ae13-bd2ca89bd11c, version 1.0
Description : Unknown RPC service
Annotation : Fw APIs
Type : Local RPC service
Named pipe : LRPC-54f8eaf2412c824c9f
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0b6edbfa-4a24-4fc6-8a23-942b1eca65d1, version 1.0
Description : Unknown RPC service
Annotation : Spooler function endpoint
Type : Local RPC service
Named pipe : spoolss
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : ae33069b-a2a8-46ee-a235-ddfd339be281, version 1.0
Description : Unknown RPC service
Annotation : Spooler base remote object endpoint
Type : Local RPC service
Named pipe : spoolss
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 4a452661-8290-4b36-8fbe-7f4093a94978, version 1.0
Description : Unknown RPC service
Annotation : Spooler function endpoint
Type : Local RPC service
Named pipe : spoolss
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service
Annotation : NSI server endpoint
Type : Local RPC service
Named pipe : OLE7C33B012DBF341B89F289558999B
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service
Annotation : NSI server endpoint
Type : Local RPC service
Named pipe : LRPC-79905173d4370807b0
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3473dd4d-2e88-4006-9cba-22570909dd10, version 5.0
Description : Unknown RPC service
Annotation : WinHttp Auto-Proxy Service
Type : Local RPC service
Named pipe : OLE7C33B012DBF341B89F289558999B
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3473dd4d-2e88-4006-9cba-22570909dd10, version 5.0
Description : Unknown RPC service
Annotation : WinHttp Auto-Proxy Service
Type : Local RPC service
Named pipe : LRPC-79905173d4370807b0
Object UUID : 6c637067-6569-746e-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 24d1f7c7-76af-4f28-9ccd-7f6cb6468601
UUID : 2eb08e3e-639f-4fba-97b1-14f878961076, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 666f7270-6c69-7365-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 666f7270-6c69-7365-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 736e6573-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 736e6573-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 736e6573-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 736e6573-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 552d076a-cb29-4e44-8b6a-d15e59e2c0af, version 1.0
Description : Unknown RPC service
Annotation : IP Transition Configuration endpoint
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 552d076a-cb29-4e44-8b6a-d15e59e2c0af, version 1.0
Description : Unknown RPC service
Annotation : IP Transition Configuration endpoint
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 552d076a-cb29-4e44-8b6a-d15e59e2c0af, version 1.0
Description : Unknown RPC service
Annotation : IP Transition Configuration endpoint
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 552d076a-cb29-4e44-8b6a-d15e59e2c0af, version 1.0
Description : Unknown RPC service
Annotation : IP Transition Configuration endpoint
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 98716d03-89ac-44c7-bb8c-285824e51c4a, version 1.0
Description : Unknown RPC service
Annotation : XactSrv service
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 98716d03-89ac-44c7-bb8c-285824e51c4a, version 1.0
Description : Unknown RPC service
Annotation : XactSrv service
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 98716d03-89ac-44c7-bb8c-285824e51c4a, version 1.0
Description : Unknown RPC service
Annotation : XactSrv service
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 98716d03-89ac-44c7-bb8c-285824e51c4a, version 1.0
Description : Unknown RPC service
Annotation : XactSrv service
Type : Local RPC service
Named pipe : senssvc
Object UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 73736573-6f69-656e-6e76-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30b044a5-a225-43f0-b3a4-e060df91f9c1, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 201ef99a-7fa0-444c-9399-19ba84f12a1a, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 5f54ce7d-5b79-4175-8584-cb65313a0e98, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : fd7a0523-dc70-43dd-9b2e-9c5ed48225b1, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 58e604e8-9adb-4d2e-a464-3b0683fb1480, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : LRPC-9622088b7ac197c794
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 58e604e8-9adb-4d2e-a464-3b0683fb1480, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 58e604e8-9adb-4d2e-a464-3b0683fb1480, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : OLED5056FFEFB26419182DBC4006E3E
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 58e604e8-9adb-4d2e-a464-3b0683fb1480, version 1.0
Description : Unknown RPC service
Annotation : AppInfo
Type : Local RPC service
Named pipe : senssvc
Object UUID : 3bdb59a0-d736-4d44-9074-c1ee00000001
UUID : 24019106-a203-4642-b88d-82dae9158929, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : LRPC-a66b0a8f030ce5c3eb
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service
Annotation : Event log TCPIP
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30adc50c-5cbc-46ce-9a0e-91914789e23c, version 1.0
Description : Unknown RPC service
Annotation : NRP server endpoint
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30adc50c-5cbc-46ce-9a0e-91914789e23c, version 1.0
Description : Unknown RPC service
Annotation : NRP server endpoint
Type : Local RPC service
Named pipe : AudioClientRpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30adc50c-5cbc-46ce-9a0e-91914789e23c, version 1.0
Description : Unknown RPC service
Annotation : NRP server endpoint
Type : Local RPC service
Named pipe : Audiosrv
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 30adc50c-5cbc-46ce-9a0e-91914789e23c, version 1.0
Description : Unknown RPC service
Annotation : NRP server endpoint
Type : Local RPC service
Named pipe : OLE1D18335C524C4C6F826BDD522CEF
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : AudioClientRpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : Audiosrv
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : OLE1D18335C524C4C6F826BDD522CEF
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : dhcpcsvc6
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service
Named pipe : AudioClientRpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service
Named pipe : Audiosrv
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service
Named pipe : OLE1D18335C524C4C6F826BDD522CEF
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service
Named pipe : dhcpcsvc6
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service
Named pipe : dhcpcsvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service
Annotation : Security Center
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service
Annotation : Security Center
Type : Local RPC service
Named pipe : AudioClientRpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service
Annotation : Security Center
Type : Local RPC service
Named pipe : Audiosrv
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service
Annotation : Security Center
Type : Local RPC service
Named pipe : OLE1D18335C524C4C6F826BDD522CEF
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 06bba54a-be05-49f9-b0a0-30f790261023, version 1.0
Description : Unknown RPC service
Annotation : Security Center
Type : Local RPC service
Named pipe : dhcpcsvc6
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dlink_dccd (2003/udp)
Plugin ID: 47605
D-link Click 'n Connect Daemon Detection
Synopsis
A remote networking service is listening on the remote host.
List of Hosts
192.168.1.79
Description
The remote service is the D-link Click 'n Connect Daemon (DCCD), a
remote networking service provided on some D-link networking devices
that allows a remote client to view and configure the D-link device.
Solution
Limit incoming traffic to this port if desired.
See also
http://www.dlink.com
Risk Factor
None
Plugin last modification date: 2011/03/11
Port cifs (445/tcp)
Plugin ID: 26919
Microsoft Windows SMB Guest Account Local User Access
Synopsis
It is possible to log into the remote host.
List of Hosts
192.168.1.30
192.168.1.215
Description
The remote host is running one of the Microsoft Windows operating
systems. It was possible to log into it as a guest user using a
random account.
Solution
In the group policy change the setting for
'Network access: Sharing and security model for local accounts' from
'Guest only - local users authenticate as Guest' to
'Classic - local users authenticate as themselves'.
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
CVE
CVE-1999-0505
Plugin last modification date: 2011/03/21
Port vnc (5902/tcp)
Plugin ID: 19288
VNC Server Security Type Detection
Synopsis
A VNC server is running on the remote host.
List of Hosts Plugin Output
192.168.1.14
The remote VNC server supports the following security types :
+ 2 (VNC authentication)
+ 16 (Tight)
Description
This script checks the remote VNC server protocol version and the
available 'security types'.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port vnc (5901/tcp)
Plugin ID: 19288
VNC Server Security Type Detection
Synopsis
A VNC server is running on the remote host.
List of Hosts Plugin Output
192.168.1.14
The remote VNC server supports the following security types :
+ 2 (VNC authentication)
+ 16 (Tight)
Description
This script checks the remote VNC server protocol version and the
available 'security types'.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (5900/tcp)
Plugin ID: 19288
VNC Server Security Type Detection
Synopsis
A VNC server is running on the remote host.
List of Hosts Plugin Output Plugin Output
192.168.1.60
The remote VNC server supports the following security types :
+ 30
+ 2 (VNC authentication)
192.168.1.233
The remote VNC server supports the following security types :
+ 30
+ 2 (VNC authentication)
+ 35
Description
This script checks the remote VNC server protocol version and the
available 'security types'.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port cifs (445/tcp)
Plugin ID: 25240
Samba Server Detection
Synopsis
An SMB server is running on the remote host.
List of Hosts
192.168.1.30
Description
The remote host is running Samba, a CIFS/SMB server for Unix.
Solution
n/a
See also
http://www.samba.org/
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dns (53/udp)
Plugin ID: 35373
DNS Server DNSSEC Aware Resolver
Synopsis
The remote DNS resolver is DNSSEC-aware.
List of Hosts
192.168.1.10
Description
The remote DNS resolver accepts DNSSEC options. This means that it
may verify the authenticity of DNSSEC protected zones if it is
configured to trust their keys.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port cifs (445/tcp)
Plugin ID: 10859
Microsoft Windows SMB LsaQueryInformationPolicy Function SID Enumeration
Synopsis
It is possible to obtain the host SID for the remote host.
List of Hosts Plugin Output Plugin Output
192.168.1.30
The remote host SID value is :
1-5-21-3581115777-3128578739-639081464
The value of 'RestrictAnonymous' setting is : unknown
192.168.1.215
The remote host SID value is :
1-5-21-585241108-4110551116-1300125788
The value of 'RestrictAnonymous' setting is : unknown
Description
By emulating the call to LsaQueryInformationPolicy(), it was possible
to obtain the host SID (Security Identifier).
The host SID can then be used to get the list of local users.
Solution
You can prevent anonymous lookups of the host SID by setting the
'RestrictAnonymous' registry setting to an appropriate value.
Refer to the 'See also' section for guidance.
Risk Factor
None
CVE
CVE-2000-1200
Bugtraq ID
959
Other references
OSVDB:715
Plugin publication date: 2002/02/13
Plugin last modification date: 2011/03/07
Ease of exploitability: Exploits are available
Port netbios-ns (137/udp)
Plugin ID: 10150
Windows NetBIOS / SMB Remote Host Information Disclosure
Synopsis
It is possible to obtain the network name of the remote host.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.30
The following 7 NetBIOS names have been gathered :
NAS-MAIN-OFFICE = Computer name
NAS-MAIN-OFFICE = Messenger Service
NAS-MAIN-OFFICE = File Server Service
__MSBROWSE__ = Master Browser
ENTERPRISE = Master Browser
ENTERPRISE = Browser Service Elections
ENTERPRISE = Workgroup / Domain name
This SMB server seems to be a SAMBA server (MAC address is NULL).
192.168.1.26
The following 7 NetBIOS names have been gathered :
MOVABLETYPE = Computer name
MOVABLETYPE = Messenger Service
MOVABLETYPE = File Server Service
__MSBROWSE__ = Master Browser
MSHOME = Master Browser
MSHOME = Browser Service Elections
MSHOME = Workgroup / Domain name
This SMB server seems to be a SAMBA server (MAC address is NULL).
192.168.1.215
The following 6 NetBIOS names have been gathered :
MEDIA1 = Computer name
WORKGROUP = Workgroup / Domain name
MEDIA1 = File Server Service
WORKGROUP = Browser Service Elections
WORKGROUP = Master Browser
__MSBROWSE__ = Master Browser
The remote host has the following MAC address on its adapter :
00:18:8b:0e:74:e6
192.168.1.180
The following 5 NetBIOS names have been gathered :
WIN-8BPIQBRO0CX = Computer name
TX = Workgroup / Domain name
TX = Domain Controllers
WIN-8BPIQBRO0CX = File Server Service
TX = Domain Master Browser
The remote host has the following MAC address on its adapter :
00:0c:29:9d:a1:c6
Description
The remote host listens on UDP port 137 or TCP port 445 and replies to
NetBIOS nbtscan or SMB requests.
Note that this plugin gathers information to be used in other plugins
but does not itself generate a report.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/27
Port (0/tcp)
Plugin ID: 11933
Do not scan printers
Synopsis
The remote host appears to be a printer and will not be scanned.
List of Hosts Plugin Output
192.168.1.245
HP printer-related web server on port 80.
Description
The remote host appears to be a network printer or multi-function
device. Such devices often react very poorly when scanned - some
crash, others print a number of pages. To avoid problems, Nessus has
marked the remote host as 'Dead' and will not scan it.
Solution
If you are not concerned about such behavior, enable the 'Scan Network
Printers' setting under the 'Do not scan fragile devices' advanced
settings block and re-run the scan.
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (0/tcp)
Plugin ID: 43067
Web Application Tests Disabled
Synopsis
Web application tests were not enabled during the scan.
List of Hosts
192.168.1.98
192.168.1.95
192.168.1.79
192.168.1.65
192.168.1.26
192.168.1.237
192.168.1.234
192.168.1.227
192.168.1.180
192.168.1.13
192.168.1.11
192.168.1.1
Description
One or several web servers were detected by Nessus, but neither the
CGI tests nor the Web Application Tests were enabled.
If you want to get a more complete report, you should enable one of
these features, or both.
Please note that the scan might take significantly longer with these
tests, which is why they are disabled by default.
Solution
To enable specific CGI tests, go to the 'Advanced' tab, select
'Global variable settings' and set 'Enable CGI scanning'.
To generic enable web application tests, go to the 'Advanced' tab,
select 'Web Application Tests Settings' and set 'Enable web
applications tests'.
You may configure other options, for example HTTP credentials in
'Login configurations', or form-based authentication in 'HTTP login
page'.
Risk Factor
None
Plugin last modification date: 2011/03/15
Port www (80/tcp)
Plugin ID: 11522
Linksys Router Default Password (admin)
Synopsis
It is possible to log on the remote device with a default password.
List of Hosts Plugin Output
192.168.1.65
It was possible to log with the following credentials :
username :
password : admin
Description
The remote Linksys device has its default password ('admin') set.
An attacker may connect to it and reconfigure it using this account.
Solution
Connect to this port with a web browser, and click on the 'Password'
section to set a strong password.
Risk Factor
High/ CVSS Base Score: 7.5
(CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P)
Other references
OSVDB:821
Plugin publication date: 2003/04/06
Plugin last modification date: 2011/03/14
Port ssh (22/tcp)
Plugin ID: 10267
SSH Server Type and Version Information
Synopsis
An SSH server is listening on this port.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.98
SSH version : SSH-2.0-dropbear_0.48
SSH supported authentication : publickey,password
192.168.1.95
SSH version : SSH-2.0-dropbear_0.48
SSH supported authentication : publickey,password
192.168.1.66
SSH version : SSH-2.0-OpenSSH_5.2
SSH supported authentication : publickey,password,keyboard-interactive
192.168.1.60
SSH version : SSH-1.99-OpenSSH_5.1
SSH supported authentication : publickey,gssapi-keyex,gssapi-with-mic,password,keyboard-interactive
192.168.1.26
SSH version : SSH-2.0-OpenSSH_4.7p1 Debian-8ubuntu1.2
SSH supported authentication : publickey,password
192.168.1.233
SSH version : SSH-2.0-OpenSSH_5.2
SSH supported authentication : publickey,keyboard-interactive
192.168.1.19
SSH version : SSH-2.0-OpenSSH_4.3
SSH supported authentication : publickey,gssapi-with-mic,password
192.168.1.18
SSH version : SSH-2.0-OpenSSH_4.3
SSH supported authentication : publickey,gssapi-with-mic,password
192.168.1.14
SSH version : SSH-2.0-OpenSSH_5.1p1 Debian-6ubuntu2
SSH supported authentication : publickey,password
192.168.1.13
SSH version : SSH-2.0-OpenSSH_4.3
SSH supported authentication : publickey,gssapi-with-mic,password
192.168.1.11
SSH version : SSH-2.0-OpenSSH_4.3
SSH supported authentication : publickey,gssapi-with-mic,password
192.168.1.10
SSH version : SSH-2.0-OpenSSH_5.1p1 Debian-5
SSH supported authentication : publickey,password
192.168.1.1
SSH version : SSH-2.0-OpenSSH_5.1p1 FreeBSD-20080901
SSH supported authentication : publickey,password,keyboard-interactive
Description
It is possible to obtain information about the remote SSH
server by sending an empty authentication request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/17 2010/01/22
Port www (443/tcp)
Plugin ID: 45410
SSL Certificate commonName Mismatch
Synopsis
The SSL certificate commonName does not match the host name.
List of Hosts Plugin Output
192.168.1.11
The host name known by Nessus is : hanzo
The CommonName of the certificate is : SecurityCenter.
Description
This service presents an SSL certificate for which the 'commonName'
(CN) does not match the host name on which the service listens.
Solution
If the machine has several names, make sure that users connect to the
service through the DNS host name that matches the common name in the
certificate.
Risk Factor
None
Plugin last modification date: 2011/03/21
Port www (443/tcp)
Plugin ID: 51892
OpenSSL SSL_OP_NETSCAPE_REUSE_CIPHER_CHANGE_BUG Ciphersuite Change Issue
Synopsis
The remote host allows resuming SSL sessions.
List of Hosts Plugin Output
192.168.1.11
Session ID : b521de7a9051287214531a9a9ae84ffa0db7f3ace25e91de4dbc022063c1f817
Initial Cipher : TLS1_CK_DHE_RSA_WITH_AES_256_CBC_SHA (0x0039)
Resumed Cipher : TLS1_CK_RSA_WITH_IDEA_CBC_SHA (0x0007)
Description
The version of OpenSSL on the remote host has been shown to allow
resuming session with a different cipher than was used when the
session was initiated. This means that an attacker that sees (e.g.
by sniffing) the start of an SSL connection can manipulate the OpenSSL
session cache to cause subsequent resumes of that session to use a
cipher chosen by the attacker.
Note that other SSL implementations may also be affected by this vulnerability.
Solution
Upgrade to OpenSSL 0.9.8q / 1.0.0.c or later, or contact your vendor for a patch.
Risk Factor
Medium/ CVSS Base Score: 4.3
(CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N)
CVE
CVE-2010-4180
Bugtraq ID
45164
Other references
OSVDB:69565
Patch publication date: 2010/12/02
Plugin publication date: 2011/02/07
Plugin last modification date: 2011/03/16
Port (0/tcp)
Plugin ID: 11936
OS Identification
Synopsis
It is possible to guess the remote operating system
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.80
Remote operating system : Linux Kernel 2.4
Linux Kernel 2.6
Confidence Level : 54
Method : SinFP
The remote host is running one of these operating systems :
Linux Kernel 2.4
Linux Kernel 2.6
192.168.1.79
Remote operating system : ipOS
Confidence Level : 95
Method : HTTP
The remote host is running ipOS
192.168.1.66
Remote operating system : Mac OS X 10.7
iOS 4
Confidence Level : 59
Method : SinFP
The remote host is running one of these operating systems :
Mac OS X 10.7
iOS 4
192.168.1.65
Remote operating system : 3Com SuperStack Switch
HP ProCurve Switch
VxWorks
Confidence Level : 59
Method : SinFP
The remote host is running one of these operating systems :
3Com SuperStack Switch
HP ProCurve Switch
VxWorks
192.168.1.60
Remote operating system : Mac OS X 10.4
Mac OS X 10.5
Confidence Level : 59
Method : SinFP
The remote host is running one of these operating systems :
Mac OS X 10.4
Mac OS X 10.5
192.168.1.30
Remote operating system : Linux Kernel 2.4
Linux Kernel 2.6
Confidence Level : 54
Method : SinFP
The remote host is running one of these operating systems :
Linux Kernel 2.4
Linux Kernel 2.6
192.168.1.26
Remote operating system : Linux Kernel 2.6 on Ubuntu Linux 8.04 (hardy)
Confidence Level : 95
Method : SSH
The remote host is running Linux Kernel 2.6 on Ubuntu Linux 8.04 (hardy)
192.168.1.238
Remote operating system : Linux Kernel
Confidence Level : 30
Method : mDNS
The remote host is running Linux Kernel
192.168.1.237
Remote operating system : Cyber Switching ePower PDU
Confidence Level : 70
Method : SinFP
The remote host is running Cyber Switching ePower PDU
192.168.1.234
Remote operating system : AppleTV/3.0
Confidence Level : 98
Method : NTP
The remote host is running AppleTV/3.0
192.168.1.233
Remote operating system : Mac OS X 10.5
Mac OS X 10.6
Mac OS X 10.7
Confidence Level : 59
Method : SinFP
The remote host is running one of these operating systems :
Mac OS X 10.5
Mac OS X 10.6
Mac OS X 10.7
192.168.1.227
Remote operating system : Cyber Switching ePower PDU
Confidence Level : 70
Method : SinFP
The remote host is running Cyber Switching ePower PDU
192.168.1.215
Remote operating system : Microsoft Windows XP Service Pack 2
Microsoft Windows XP Service Pack 3
Confidence Level : 99
Method : MSRPC
The remote host is running one of these operating systems :
Microsoft Windows XP Service Pack 2
Microsoft Windows XP Service Pack 3
192.168.1.19
Remote operating system : Linux Kernel 2.6
Confidence Level : 70
Method : SinFP
The remote host is running Linux Kernel 2.6
192.168.1.180
Remote operating system : Microsoft Windows Server 2008 Service Pack 1
Confidence Level : 99
Method : MSRPC
The remote host is running Microsoft Windows Server 2008 Service Pack 1
192.168.1.18
Remote operating system : Linux Kernel 2.6
Confidence Level : 70
Method : SinFP
The remote host is running Linux Kernel 2.6
192.168.1.16
Remote operating system : Windows 7 Ultimate
Confidence Level : 69
Method : MSRPC
The remote host is running Windows 7 Ultimate
192.168.1.14
Remote operating system : Linux Kernel 2.6 on Debian 5.0 (lenny)
Confidence Level : 95
Method : SSH
The remote host is running Linux Kernel 2.6 on Debian 5.0 (lenny)
192.168.1.13
Remote operating system : Linux Kernel 2.6.18-194.32.1.el5 on CentOS release 5.5 (Final)
Confidence Level : 100
Method : LinuxDistribution
The remote host is running Linux Kernel 2.6.18-194.32.1.el5 on CentOS release 5.5 (Final)
192.168.1.11
Remote operating system : Linux Kernel 2.6
Confidence Level : 65
Method : SinFP
The remote host is running Linux Kernel 2.6
192.168.1.10
Remote operating system : Linux Kernel 2.6 on Debian 5.0 (lenny)
Confidence Level : 95
Method : SSH
The remote host is running Linux Kernel 2.6 on Debian 5.0 (lenny)
192.168.1.1
Remote operating system : FreeBSD 7.3
FreeBSD 7.4
Confidence Level : 85
Method : SSH
The remote host is running one of these operating systems :
FreeBSD 7.3
FreeBSD 7.4
Description
Using a combination of remote probes (TCP/IP, SMB, HTTP, NTP, SNMP, etc...)
it is possible to guess the name of the remote operating system in use, and
sometimes its version
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/04/08
Port cifs (445/tcp)
Plugin ID: 11011
Microsoft Windows SMB Service Detection
Synopsis
A file / print sharing service is listening on the remote host.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.30
A CIFS server is running on this port.
192.168.1.215
A CIFS server is running on this port.
192.168.1.180
A CIFS server is running on this port.
192.168.1.16
A CIFS server is running on this port.
Description
The remote service understands the CIFS (Common Internet File System)
or Server Message Block (SMB) protocol, used to provide shared access
to files, printers, etc between nodes on a network.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (139/tcp)
Plugin ID: 11011
Microsoft Windows SMB Service Detection
Synopsis
A file / print sharing service is listening on the remote host.
List of Hosts Plugin Output Plugin Output Plugin Output
192.168.1.30
An SMB server is running on this port.
192.168.1.215
An SMB server is running on this port.
192.168.1.180
An SMB server is running on this port.
Description
The remote service understands the CIFS (Common Internet File System)
or Server Message Block (SMB) protocol, used to provide shared access
to files, printers, etc between nodes on a network.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (8834/tcp)
Plugin ID: 21643
SSL Cipher Suites Supported
Synopsis
The remote service encrypts communications using SSL.
List of Hosts Plugin Output
192.168.1.13
Here is the list of SSL ciphers supported by the remote server :
High Strength Ciphers (>= 112-bit key)
SSLv3
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
TLSv1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
AES128-SHA Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
AES256-SHA Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Description
This script detects which SSL ciphers are supported by the remote
service for encrypting communications.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (8089/tcp)
Plugin ID: 21643
SSL Cipher Suites Supported
Synopsis
The remote service encrypts communications using SSL.
List of Hosts Plugin Output
192.168.1.180
Here is the list of SSL ciphers supported by the remote server :
High Strength Ciphers (>= 112-bit key)
SSLv2
DES-CBC3-MD5 Kx=RSA Au=RSA Enc=3DES(168) Mac=MD5
RC2-CBC-MD5 Kx=RSA Au=RSA Enc=RC2(128) Mac=MD5
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
SSLv3
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
TLSv1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
AES128-SHA Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
AES256-SHA Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Description
This script detects which SSL ciphers are supported by the remote
service for encrypting communications.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port www (3000/tcp)
Plugin ID: 21643
SSL Cipher Suites Supported
Synopsis
The remote service encrypts communications using SSL.
List of Hosts Plugin Output
192.168.1.26
Here is the list of SSL ciphers supported by the remote server :
Low Strength Ciphers (< 56-bit key)
SSLv2
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
SSLv3
EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
TLSv1
EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
Medium Strength Ciphers (>= 56-bit and < 112-bit key)
SSLv2
DES-CBC-MD5 Kx=RSA Au=RSA Enc=DES(56) Mac=MD5
SSLv3
EDH-RSA-DES-CBC-SHA Kx=DH Au=RSA Enc=DES(56) Mac=SHA1
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1
TLSv1
EDH-RSA-DES-CBC-SHA Kx=DH Au=RSA Enc=DES(56) Mac=SHA1
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1
High Strength Ciphers (>= 112-bit key)
SSLv2
DES-CBC3-MD5 Kx=RSA Au=RSA Enc=3DES(168) Mac=MD5
RC2-CBC-MD5 Kx=RSA Au=RSA Enc=RC2(128) Mac=MD5
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
SSLv3
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES(168) Mac=SHA1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
TLSv1
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES(168) Mac=SHA1
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES(128) Mac=SHA1
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES(256) Mac=SHA1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
AES128-SHA Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
AES256-SHA Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Description
This script detects which SSL ciphers are supported by the remote
service for encrypting communications.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (1243/tcp)
Plugin ID: 21643
SSL Cipher Suites Supported
Synopsis
The remote service encrypts communications using SSL.
List of Hosts Plugin Output
192.168.1.13
Here is the list of SSL ciphers supported by the remote server :
Medium Strength Ciphers (>= 56-bit and < 112-bit key)
TLSv1
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1
High Strength Ciphers (>= 112-bit key)
TLSv1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
AES128-SHA Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
AES256-SHA Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Description
This script detects which SSL ciphers are supported by the remote
service for encrypting communications.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (1241/tcp)
Plugin ID: 21643
SSL Cipher Suites Supported
Synopsis
The remote service encrypts communications using SSL.
List of Hosts Plugin Output
192.168.1.13
Here is the list of SSL ciphers supported by the remote server :
High Strength Ciphers (>= 112-bit key)
TLSv1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
AES128-SHA Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
AES256-SHA Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Description
This script detects which SSL ciphers are supported by the remote
service for encrypting communications.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port www (443/tcp)
Plugin ID: 21643
SSL Cipher Suites Supported
Synopsis
The remote service encrypts communications using SSL.
List of Hosts Plugin Output Plugin Output Plugin Output
192.168.1.79
Here is the list of SSL ciphers supported by the remote server :
High Strength Ciphers (>= 112-bit key)
SSLv3
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
TLSv1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
AES128-SHA Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
AES256-SHA Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
192.168.1.26
Here is the list of SSL ciphers supported by the remote server :
Low Strength Ciphers (< 56-bit key)
SSLv2
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
SSLv3
EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
TLSv1
EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
Medium Strength Ciphers (>= 56-bit and < 112-bit key)
SSLv2
DES-CBC-MD5 Kx=RSA Au=RSA Enc=DES(56) Mac=MD5
SSLv3
EDH-RSA-DES-CBC-SHA Kx=DH Au=RSA Enc=DES(56) Mac=SHA1
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1
TLSv1
EDH-RSA-DES-CBC-SHA Kx=DH Au=RSA Enc=DES(56) Mac=SHA1
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES(56) Mac=SHA1
High Strength Ciphers (>= 112-bit key)
SSLv2
DES-CBC3-MD5 Kx=RSA Au=RSA Enc=3DES(168) Mac=MD5
RC2-CBC-MD5 Kx=RSA Au=RSA Enc=RC2(128) Mac=MD5
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
SSLv3
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES(168) Mac=SHA1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
TLSv1
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES(168) Mac=SHA1
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES(128) Mac=SHA1
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES(256) Mac=SHA1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
AES128-SHA Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
AES256-SHA Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
192.168.1.11
Here is the list of SSL ciphers supported by the remote server :
High Strength Ciphers (>= 112-bit key)
SSLv3
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES(168) Mac=SHA1
IDEA-CBC-SHA Kx=RSA Au=RSA Enc=IDEA(128) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
TLSv1
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES(168) Mac=SHA1
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES(128) Mac=SHA1
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES(256) Mac=SHA1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
AES128-SHA Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
AES256-SHA Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
IDEA-CBC-SHA Kx=RSA Au=RSA Enc=IDEA(128) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Description
This script detects which SSL ciphers are supported by the remote
service for encrypting communications.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port ntp (123/udp)
Plugin ID: 10884
Network Time Protocol (NTP) Server Detection
Synopsis
An NTP server is listening on the remote host.
List of Hosts Plugin Output
192.168.1.66
192.168.1.234
It was possible to gather the following information from the remote NTP host :
version='ntpd [email protected] Sat Oct 7 04:38:28 PDT 2006 (1)',
processor='i386', system='Darwin/8.8.2', leap=3, stratum=16,
precision=-20, rootdelay=0.000, rootdispersion=134715.540, peer=0,
refid=INIT, reftime=0x00000000.00000000, poll=4,
clock=0xd15053b2.48a393ee, state=0, offset=0.000, frequency=0.000,
jitter=0.001, stability=0.000
192.168.1.233
192.168.1.180
Description
An NTP (Network Time Protocol) server is listening on this port. It
provides information about the current date and time of the remote
system and may provide system information.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port telnet (23/tcp)
Plugin ID: 10281
Telnet Server Detection
Synopsis
A Telnet server is listening on the remote port.
List of Hosts Plugin Output Plugin Output
192.168.1.98
Here is the banner from the remote Telnet server :
------------------------------ snip ------------------------------
Login failed.
------------------------------ snip ------------------------------
192.168.1.95
Here is the banner from the remote Telnet server :
------------------------------ snip ------------------------------
Login failed.
------------------------------ snip ------------------------------
Description
The remote host is running a Telnet server, a remote terminal server.
Solution
Disable this service if you do not use it.
Risk Factor
None
Plugin last modification date: 2011/03/17
Port (0/tcp)
Plugin ID: 25203
Enumerate IPv4 Interfaces via SSH
Synopsis
This plugin enumerates IPv4 interfaces on a remote host.
List of Hosts Plugin Output
192.168.1.13
The following IPv4 addresses are set on the remote host :
- 192.168.1.13 (on interface eth0)
- 127.0.0.1 (on interface lo)
Description
By connecting to the remote host via SSH with the supplied
credentials, this plugin enumerates network interfaces configured with
IPv4 addresses.
Solution
Disable any unused IPv4 interfaces.
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (0/tcp)
Plugin ID: 35716
Ethernet Card Manufacturer Detection
Synopsis
The manufacturer can be deduced from the Ethernet OUI.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.98
The following card manufacturers were identified :
00:18:f8:d8:09:20 : Cisco-Linksys LLC
192.168.1.95
The following card manufacturers were identified :
00:18:f8:d8:08:90 : Cisco-Linksys LLC
192.168.1.80
The following card manufacturers were identified :
00:25:9c:8f:80:dd : Cisco-Linksys, LLC
192.168.1.79
The following card manufacturers were identified :
00:26:5a:fd:19:74 : D-Link Corporation
192.168.1.66
The following card manufacturers were identified :
00:1f:f3:d0:b6:29 : Apple, Inc
192.168.1.65
The following card manufacturers were identified :
00:1a:70:75:b5:fb : Cisco-Linksys, LLC
192.168.1.60
The following card manufacturers were identified :
00:17:f2:c8:da:c8 : Apple Computer
192.168.1.30
The following card manufacturers were identified :
00:0d:a2:01:83:fb : Infrant Technologies, Inc.
192.168.1.26
The following card manufacturers were identified :
00:0c:29:17:b2:6f : VMware, Inc.
192.168.1.238
The following card manufacturers were identified :
00:18:de:c1:de:8a : Intel Corporation
192.168.1.237
The following card manufacturers were identified :
00:0d:4b:63:c8:ef : Roku, LLC
192.168.1.234
The following card manufacturers were identified :
00:1b:63:f0:78:d1 : Apple Computer Inc.
192.168.1.227
The following card manufacturers were identified :
00:0d:4b:4c:29:5f : Roku, LLC
192.168.1.215
The following card manufacturers were identified :
00:18:8b:0e:74:e6 : Dell
192.168.1.203
The following card manufacturers were identified :
00:26:99:48:4d:4a : Cisco Systems
192.168.1.19
The following card manufacturers were identified :
00:0c:29:63:6f:24 : VMware, Inc.
192.168.1.180
The following card manufacturers were identified :
00:0c:29:9d:a1:c6 : VMware, Inc.
192.168.1.18
The following card manufacturers were identified :
00:0c:29:15:fd:8c : VMware, Inc.
192.168.1.16
The following card manufacturers were identified :
00:24:1d:52:d4:fb : GIGA-BYTE TECHNOLOGY CO.,LTD.
192.168.1.14
The following card manufacturers were identified :
00:22:19:dc:a7:a9 : Dell Inc
192.168.1.13
The following card manufacturers were identified :
00:a0:cc:3d:b3:ba : LITE-ON COMMUNICATIONS, INC.
00:17:31:03:14:1f : ASUSTek COMPUTER INC.
192.168.1.11
The following card manufacturers were identified :
00:17:31:08:74:82 : ASUSTek COMPUTER INC.
192.168.1.10
The following card manufacturers were identified :
00:00:24:c9:55:21 : CONNECT AS
192.168.1.1
The following card manufacturers were identified :
00:0d:b9:1c:0e:35 : PC Engines GmbH
Description
Each ethernet MAC address starts with a 24-bit 'Organizationally
Unique Identifier'.
These OUI are registered by IEEE.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/27
Port www (3689/tcp)
Plugin ID: 47763
iTunes < 9.2.1 'itpc:' Buffer Overflow Vulnerability (uncredentialed check)
Synopsis
The remote host contains an application that is affected by a buffer
overflow vulnerability.
List of Hosts Plugin Output
192.168.1.60
iTunes 8.2.1 appears to be running on the remote host based on the
following response header :
DAAP-Server: iTunes/8.2.1 (Mac OS X)
Description
The remote version of iTunes is older than 9.2.1. Such versions may
be affected by a buffer overflow vulnerability in the handling of
'itpc:' URLs which may allow an attacker to execute arbitrary code on
the remote host.
To exploit this vulnerability, an attacker would need to send a
malformed itpc: link to user on the remote host and wait for him to
click on it.
Solution
Upgrade to iTunes 9.2.1 or later.
See also
http://support.apple.com/kb/HT4263
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2010-1777
Bugtraq ID
41789
Other references
OSVDB:66456
Patch publication date: 2010/07/19
Plugin publication date: 2010/07/20
Plugin last modification date: 2011/03/08
Ease of exploitability: No known exploits are available
Port telnet (23/tcp)
Plugin ID: 42263
Unencrypted Telnet Server
Synopsis
The remote Telnet server transmits traffic in cleartext.
List of Hosts Plugin Output Plugin Output
192.168.1.98
Nessus collected the following banner from the remote Telnet server :
------------------------------ snip ------------------------------
Login failed.
------------------------------ snip ------------------------------
192.168.1.95
Nessus collected the following banner from the remote Telnet server :
------------------------------ snip ------------------------------
Login failed.
------------------------------ snip ------------------------------
Description
The remote host is running a Telnet server over an unencrypted
channel.
Using Telnet over an unencrypted channel is not recommended as logins,
passwords and commands are transferred in cleartext. An attacker may
eavesdrop on a Telnet session and obtain credentials or other
sensitive information.
Use of SSH is prefered nowadays as it protects credentials from
eavesdropping and can tunnel additional data streams such as the X11
session.
Solution
Disable this service and use SSH instead.
Risk Factor
Low/ CVSS Base Score: 2.6
(CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/17
Port (0/tcp)
Plugin ID: 35351
System Information Enumeration (via DMI)
Synopsis
Information about the remote system's hardware can be read.
List of Hosts Plugin Output
192.168.1.13
Serial Number : System Serial Number
Product Name : System Product Name
Description
Using the SMBIOS (aka DMI) interface, it was possible to retrieve
information about the remote system's hardware, such as its product
name and serial number.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port portmapper (111/tcp)
Plugin ID: 53335
RPC portmapper (TCP)
Synopsis
An ONC RPC portmapper is running on the remote host.
List of Hosts
192.168.1.30
192.168.1.18
192.168.1.13
Description
The RPC portmapper is running on this port.
The portmapper allows someone to get the port number of each RPC
service running on the remote host by sending either multiple lookup
requests or a DUMP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port (8089/tcp)
Plugin ID: 20007
SSL Version 2 (v2) Protocol Detection
Synopsis
The remote service encrypts traffic using a protocol with known
weaknesses.
List of Hosts
192.168.1.180
Description
The remote service accepts connections encrypted using SSL 2.0, which
reportedly suffers from several cryptographic flaws and has been
deprecated for several years. An attacker may be able to exploit
these issues to conduct man-in-the-middle attacks or decrypt
communications between the affected service and clients.
Solution
Consult the application's documentation to disable SSL 2.0 and use SSL
3.0 or TLS 1.0 instead.
See also
http://www.schneier.com/paper-ssl.pdf
http://support.microsoft.com/kb/187498
http://www.linux4beginners.info/node/disable-sslv2
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/11
Port www (443/tcp)
Plugin ID: 20007
SSL Version 2 (v2) Protocol Detection
Synopsis
The remote service encrypts traffic using a protocol with known
weaknesses.
List of Hosts
192.168.1.26
Description
The remote service accepts connections encrypted using SSL 2.0, which
reportedly suffers from several cryptographic flaws and has been
deprecated for several years. An attacker may be able to exploit
these issues to conduct man-in-the-middle attacks or decrypt
communications between the affected service and clients.
Solution
Consult the application's documentation to disable SSL 2.0 and use SSL
3.0 or TLS 1.0 instead.
See also
http://www.schneier.com/paper-ssl.pdf
http://support.microsoft.com/kb/187498
http://www.linux4beginners.info/node/disable-sslv2
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/11
Port www (8834/tcp)
Plugin ID: 20108
Web Server / Application favicon.ico Vendor Fingerprinting
Synopsis
The remote web server contains a graphic image that is prone to
information disclosure.
List of Hosts Plugin Output
192.168.1.13
The 'favico.ico' fingerprints this webserver as Nessus 4.x Web Client.
Description
The 'favicon.ico' file found on the remote web server belongs to a
popular webserver. This may be used to fingerprint the web server.
Solution
Remove the 'favicon.ico' file or create a custom one for your site.
Risk Factor
None
Other references
OSVDB:39272
Plugin last modification date: 2011/04/08
Port www (5800/tcp)
Plugin ID: 10758
VNC HTTP Server Detection
Synopsis
The remote host is running a remote display software (VNC).
List of Hosts
192.168.1.66
Description
The remote host is running VNC (Virtual Network Computing), which uses
the RFB (Remote Framebuffer) protocol to provide remote access to
graphical user interfaces and thus permits a console on the remote
host to be displayed on another.
Solution
Make sure use of this software is done in accordance with your
organization's security policy and filter incoming traffic to this
port.
See also
http://en.wikipedia.org/wiki/Vnc
Risk Factor
None
Plugin last modification date: 2011/03/17
Port www (443/tcp)
Plugin ID: 45411
SSL Certificate with Wrong Hostname
Synopsis
The SSL certificate for this service is for a different host.
List of Hosts Plugin Output
192.168.1.11
The following hostnames were checked :
SecurityCenter
Description
The commonName (CN) of the SSL certificate presented on this port is
for a different machine.
Solution
Purchase or generate a proper certificate for this service.
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N)
Plugin last modification date: 2011/03/26
Port (0/tcp)
Plugin ID: 42825
Apple TV Detection
Synopsis
The remote host is a digital media receiver.
List of Hosts
192.168.1.234
Description
The remote host is an Apple TV, a digital media receiver.
Solution
Make sure that use of such devices is in line with your
organization's acceptable use and security policies.
See also
http://www.apple.com/appletv/
Risk Factor
None
Plugin last modification date: 2011/03/17
Port (8834/tcp)
Plugin ID: 51192
SSL Certificate signed with an unknown Certificate Authority
Synopsis
The SSL certificate for this service is signed by an unknown
certificate authority.
List of Hosts Plugin Output
192.168.1.13
*** ERROR: Unknown root CA in the chain:
Organization: Nessus Users United
Organization Unit: Nessus Certification Authority
Locality: New York
Country: US
State/Province: NY
Common Name: Nessus Certification Authority
Certificate chain:
|-Organization: Nessus Users United
|-Organization Unit: Nessus Certification Authority
|-Locality: New York
|-Country: US
|-State/Province: NY
|-Common Name: Nessus Certification Authority
|
|--Organization: Nessus Users United
|--Organization Unit: Nessus Server
|--Locality: New York
|--Country: US
|--State/Province: NY
|--Common Name: gogo
|
Description
The X.509 certificate of the remote host is not signed by a known
public certificate authority. If the remote host is a public host in
production, this nullifies the use of SSL as anyone could establish a
man in the middle attack against the remote host.
Solution
Purchase or generate a proper certificate for this service.
Risk Factor
Medium/ CVSS Base Score: 6.4
(CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N)
Plugin last modification date: 2011/03/21
Port www (3000/tcp)
Plugin ID: 51192
SSL Certificate signed with an unknown Certificate Authority
Synopsis
The SSL certificate for this service is signed by an unknown
certificate authority.
List of Hosts Plugin Output
192.168.1.26
*** ERROR: Unknown root CA in the chain:
Country: US
State/Province: AZ
Locality: Tempe
Organization: JumpBox
Organization Unit: None
Common Name: jumpbox
Email Address: [email protected]
Certificate chain:
|-Country: US
|-State/Province: AZ
|-Locality: Tempe
|-Organization: JumpBox
|-Organization Unit: None
|-Common Name: jumpbox
|-Email Address: [email protected]
|
Description
The X.509 certificate of the remote host is not signed by a known
public certificate authority. If the remote host is a public host in
production, this nullifies the use of SSL as anyone could establish a
man in the middle attack against the remote host.
Solution
Purchase or generate a proper certificate for this service.
Risk Factor
Medium/ CVSS Base Score: 6.4
(CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N)
Plugin last modification date: 2011/03/21
Port (1243/tcp)
Plugin ID: 51192
SSL Certificate signed with an unknown Certificate Authority
Synopsis
The SSL certificate for this service is signed by an unknown
certificate authority.
List of Hosts Plugin Output
192.168.1.13
*** ERROR: Unknown root CA in the chain:
Country: US
State/Province: none
Locality: Columbia
Organization: Tenable Users United
Organization Unit: Certification Authority for gogo
Common Name: gogo
Email Address: ca@gogo
Certificate chain:
|-Country: US
|-State/Province: none
|-Locality: Columbia
|-Organization: Tenable Users United
|-Organization Unit: Certification Authority for gogo
|-Common Name: gogo
|-Email Address: ca@gogo
|
|--Country: US
|--State/Province: none
|--Locality: Columbia
|--Organization: Tenable Users United
|--Organization Unit: Server certificate for gogo
|--Common Name: gogo
|--Email Address: pvsd@gogo
|
Description
The X.509 certificate of the remote host is not signed by a known
public certificate authority. If the remote host is a public host in
production, this nullifies the use of SSL as anyone could establish a
man in the middle attack against the remote host.
Solution
Purchase or generate a proper certificate for this service.
Risk Factor
Medium/ CVSS Base Score: 6.4
(CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N)
Plugin last modification date: 2011/03/21
Port (1241/tcp)
Plugin ID: 51192
SSL Certificate signed with an unknown Certificate Authority
Synopsis
The SSL certificate for this service is signed by an unknown
certificate authority.
List of Hosts Plugin Output
192.168.1.13
*** ERROR: Unknown root CA in the chain:
Organization: Nessus Users United
Organization Unit: Nessus Certification Authority
Locality: New York
Country: US
State/Province: NY
Common Name: Nessus Certification Authority
Certificate chain:
|-Organization: Nessus Users United
|-Organization Unit: Nessus Certification Authority
|-Locality: New York
|-Country: US
|-State/Province: NY
|-Common Name: Nessus Certification Authority
|
|--Organization: Nessus Users United
|--Organization Unit: Nessus Server
|--Locality: New York
|--Country: US
|--State/Province: NY
|--Common Name: gogo
|
Description
The X.509 certificate of the remote host is not signed by a known
public certificate authority. If the remote host is a public host in
production, this nullifies the use of SSL as anyone could establish a
man in the middle attack against the remote host.
Solution
Purchase or generate a proper certificate for this service.
Risk Factor
Medium/ CVSS Base Score: 6.4
(CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N)
Plugin last modification date: 2011/03/21
Port www (443/tcp)
Plugin ID: 51192
SSL Certificate signed with an unknown Certificate Authority
Synopsis
The SSL certificate for this service is signed by an unknown
certificate authority.
List of Hosts Plugin Output Plugin Output Plugin Output
192.168.1.79
*** ERROR: Unknown root CA in the chain:
Country: TW
State/Province: Taiwan
Locality: Taipei
Organization: D-Link Corp.
Organization Unit: Wireless and Router Div.
Common Name: dlinkrouter
Certificate chain:
|-Country: TW
|-State/Province: Taiwan
|-Locality: Taipei
|-Organization: D-Link Corp.
|-Organization Unit: Wireless and Router Div.
|-Common Name: dlinkrouter
|
192.168.1.26
*** ERROR: Unknown root CA in the chain:
Country: US
State/Province: AZ
Locality: Tempe
Organization: JumpBox
Organization Unit: None
Common Name: jumpbox
Email Address: [email protected]
Certificate chain:
|-Country: US
|-State/Province: AZ
|-Locality: Tempe
|-Organization: JumpBox
|-Organization Unit: None
|-Common Name: jumpbox
|-Email Address: [email protected]
|
192.168.1.11
*** ERROR: Unknown root CA in the chain:
Country: US
State/Province: Maryland
Locality: Columbia
Organization: Tenable Network Security, Inc.
Organization Unit: Certification Authority for SecurityCenter
Common Name: SecurityCenter
Email Address: SecurityCenter@SecurityCenter
Certificate chain:
|-Country: US
|-State/Province: Maryland
|-Locality: Columbia
|-Organization: Tenable Network Security, Inc.
|-Organization Unit: Certification Authority for SecurityCenter
|-Common Name: SecurityCenter
|-Email Address: SecurityCenter@SecurityCenter
|
Description
The X.509 certificate of the remote host is not signed by a known
public certificate authority. If the remote host is a public host in
production, this nullifies the use of SSL as anyone could establish a
man in the middle attack against the remote host.
Solution
Purchase or generate a proper certificate for this service.
Risk Factor
Medium/ CVSS Base Score: 6.4
(CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N)
Plugin last modification date: 2011/03/21
Port cifs (445/tcp)
Plugin ID: 26920
Microsoft Windows SMB NULL Session Authentication
Synopsis
It is possible to log into the remote Windows host with a NULL
session.
List of Hosts
192.168.1.30
192.168.1.215
192.168.1.180
192.168.1.16
Description
The remote host is running Microsoft Windows, and it was possible to
log into it using a NULL session (i.e., with no login or password). An
unauthenticated remote attacker can leverage this issue to get
information about the remote host.
Solution
n/a
Risk Factor
None
Bugtraq ID
494
Other references
OSVDB:299
Plugin publication date: 2007/10/04
Plugin last modification date: 2011/03/28
Ease of exploitability: No known exploits are available
Port ssh (22/tcp)
Plugin ID: 10881
SSH Protocol Versions Supported
Synopsis
A SSH server is running on the remote host.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.66
The remote SSH daemon supports the following versions of the
SSH protocol :
- 1.99
- 2.0
SSHv2 host key fingerprint : d1:1a:57:f8:2a:69:fa:22:47:d4:d4:6d:62:91:64:aa
192.168.1.60
The remote SSH daemon supports the following versions of the
SSH protocol :
- 1.33
- 1.5
- 1.99
- 2.0
SSHv1 host key fingerprint : a1:45:ec:c0:97:1c:f5:0b:0e:da:1e:d0:ee:24:14:ab
SSHv2 host key fingerprint : 0c:e2:ce:d9:95:58:d9:e5:d6:7f:e3:3e:a4:0f:cf:6a
192.168.1.26
The remote SSH daemon supports the following versions of the
SSH protocol :
- 1.99
- 2.0
SSHv2 host key fingerprint : 31:5f:50:5c:b2:3d:de:a4:18:eb:c5:28:19:c1:ef:44
192.168.1.233
The remote SSH daemon supports the following versions of the
SSH protocol :
- 1.99
- 2.0
SSHv2 host key fingerprint : fb:6a:eb:ee:7c:40:7e:62:a0:86:e9:25:ef:fe:ab:29
192.168.1.19
The remote SSH daemon supports the following versions of the
SSH protocol :
- 1.99
- 2.0
SSHv2 host key fingerprint : 96:b5:97:e9:66:7b:ef:58:67:ec:49:83:c9:f4:b5:48
192.168.1.18
The remote SSH daemon supports the following versions of the
SSH protocol :
- 1.99
- 2.0
SSHv2 host key fingerprint : 96:b5:97:e9:66:7b:ef:58:67:ec:49:83:c9:f4:b5:48
192.168.1.14
The remote SSH daemon supports the following versions of the
SSH protocol :
- 1.99
- 2.0
SSHv2 host key fingerprint : 4b:96:e2:57:58:da:44:bc:bc:0f:23:7d:4b:49:42:a5
192.168.1.13
The remote SSH daemon supports the following versions of the
SSH protocol :
- 1.99
- 2.0
192.168.1.11
The remote SSH daemon supports the following versions of the
SSH protocol :
- 1.99
- 2.0
SSHv2 host key fingerprint : 4b:9e:e1:6b:8e:43:f4:a0:6a:d7:35:33:11:f4:32:03
192.168.1.10
The remote SSH daemon supports the following versions of the
SSH protocol :
- 1.99
- 2.0
SSHv2 host key fingerprint : 65:b6:df:e2:a2:2d:8f:7f:c2:f1:83:f6:6f:08:9a:6c
192.168.1.1
The remote SSH daemon supports the following versions of the
SSH protocol :
- 1.99
- 2.0
SSHv2 host key fingerprint : 35:c2:29:c3:67:04:c2:6f:24:64:a0:6a:d8:3c:f2:ab
Description
This plugin determines the versions of the SSH protocol supported by
the remote SSH daemon.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/30
Port www (631/tcp)
Plugin ID: 43111
HTTP Methods Allowed (per directory)
Synopsis
This plugin determines which HTTP methods are allowed on various CGI
directories.
List of Hosts Plugin Output
192.168.1.30
Based on the response to an OPTIONS request :
- HTTP methods HEAD OPTIONS POST PUT GET are allowed on :
/
Description
By calling the OPTIONS method, it is possible to determine which HTTP
methods are allowed on each directory.
As this list may be incomplete, the plugin also tests - if 'Thorough
tests' are enabled or 'Enable web applications tests' is set to 'yes'
in the scan policy - various known HTTP methods on each directory and
considers them as unsupported if it receives a response code of 400,
403, 405, or 501.
Note that the plugin output is only informational and does not
necessarily indicate the presence of any security vulnerabilities.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/14
Port www (8060/tcp)
Plugin ID: 35712
Web Server UPnP Detection
Synopsis
The remote web server provides UPnP information.
List of Hosts Plugin Output Plugin Output
192.168.1.237
Here is a summary of http://192.168.1.237:8060/ :
deviceType:urn:schemas-upnp-org:device:MediaRenderer:1
friendlyName:Roku Streaming Player
manufacturer:Roku
manufacturerURL:http://www.roku.com/
modelDescription:Roku Streaming Player Network Media
modelName:Roku Streaming Player 2050X
modelNumber:2050X
modelURL:http://www.roku.com/
serialNumber:J0A097028488
192.168.1.227
Here is a summary of http://192.168.1.227:8060/ :
deviceType:urn:schemas-upnp-org:device:MediaRenderer:1
friendlyName:Roku Streaming Player
manufacturer:Roku
manufacturerURL:http://www.roku.com/
modelDescription:Roku Streaming Player Network Media
modelName:Roku Streaming Player N1101
modelNumber:N1101
modelURL:http://www.roku.com/
serialNumber:D0C9DP009064
Description
It was possible to extract some information about the UPnP-enabled
device by querying this web server.
Services may also be reachable through SOAP requests.
Solution
Filter incoming traffic to this port if desired.
Risk Factor
None
Plugin last modification date: 2011/03/14
Port dns (53/udp)
Plugin ID: 35371
DNS Server hostname.bind Map Hostname Disclosure
Synopsis
The DNS server discloses the remote host name.
List of Hosts Plugin Output
192.168.1.10
The remote host name is :
madmonk
Description
It is possible to learn the remote host name by querying the remote
DNS server for 'hostname.bind' in the CHAOS domain.
Solution
It may be possible to disable this feature. Consult the vendor's
documentation for more information.
Risk Factor
None
Plugin last modification date: 2011/03/11
Port www (443/tcp)
Plugin ID: 10863
SSL Certificate Information
Synopsis
This plugin displays the SSL certificate.
List of Hosts Plugin Output Plugin Output Plugin Output
192.168.1.79
Subject Name:
Country: TW
State/Province: Taiwan
Locality: Taipei
Organization: D-Link Corp.
Organization Unit: Wireless and Router Div.
Common Name: dlinkrouter
Issuer Name:
Country: TW
State/Province: Taiwan
Locality: Taipei
Organization: D-Link Corp.
Organization Unit: Wireless and Router Div.
Common Name: dlinkrouter
Serial Number: 00 DB BA 88 FC D9 44 CA 07
Version: 1
Signature Algorithm: SHA-1 With RSA Encryption
Not Valid Before: Jan 11 13:00:37 2009 GMT
Not Valid After: Jan 09 13:00:37 2019 GMT
Public Key Info:
Algorithm: RSA Encryption
Public Key: 00 B6 90 84 ED E9 EE 5E C1 6A 19 62 12 D0 F8 7F 70 4D CF 3B
5A D6 E8 80 71 57 5F 3C FF 1E 09 09 86 11 4C F8 36 FB 96 D7
CD F8 E8 EB 31 82 98 11 D9 B9 95 77 56 26 EA F0 3A 9E 40 93
C2 A4 B1 C1 62 D7 61 23 6D E8 55 BD 2A 54 B9 A5 72 83 79 68
7A 8A 00 F9 43 C9 71 3E B9 DD 12 35 9E AE 8B 99 5B 55 E5 51
F1 F7 FE B2 52 DD 9D 0B C0 38 98 29 85 20 8F FD C2 D1 48 4A
B8 05 16 E4 9B 1D AE 88 DF
Exponent: 01 00 01
Signature: 00 3F 4E 24 FD 11 94 7E D9 A2 96 75 31 C2 FB B5 42 A1 32 E0
02 DD D0 E4 80 CB 16 E5 2C 14 BF 41 EF F9 56 CE E5 45 3C 44
FD A8 06 73 2F 3B 65 E6 5B 45 90 8A C5 BB 3C 3D 9B 5E FD 14
FB E6 D4 EE 27 86 6B DB 4E 06 A1 25 8B 0F CA B0 AB B6 B9 48
F6 B4 B1 E7 66 54 67 B4 EC 52 90 5C C7 1C 9E F0 C1 24 97 CC
A8 4A 81 43 D0 D8 32 73 EB C7 7F E6 C7 00 2A AB 4D 82 99 33
01 B2 77 DE 26 B1 11 DA 7F
192.168.1.26
Subject Name:
Country: US
State/Province: AZ
Locality: Tempe
Organization: JumpBox
Organization Unit: None
Common Name: jumpbox
Email Address: [email protected]
Issuer Name:
Country: US
State/Province: AZ
Locality: Tempe
Organization: JumpBox
Organization Unit: None
Common Name: jumpbox
Email Address: [email protected]
Serial Number: 00 A3 E7 C7 CA 2B 6B 3C ED
Version: 1
Signature Algorithm: SHA-1 With RSA Encryption
Not Valid Before: Nov 17 16:46:05 2009 GMT
Not Valid After: Nov 15 16:46:05 2019 GMT
Public Key Info:
Algorithm: RSA Encryption
Public Key: 00 C4 69 93 8E AA F2 B1 1A C0 0C 61 FB 80 EE 7A 19 8F A1 69
B5 2B 9B C9 CC FE F1 4E 10 E2 0B 0B 81 BF 13 7D 9D 83 71 F9
C2 AB 64 69 22 9D 2E C9 31 A0 7B F9 54 6E FC 00 EC BB 43 E3
D0 73 7C 17 C7 23 D0 51 D5 60 CE FA D9 7D 1D B3 0F 5B 96 1D
B6 A7 22 B7 78 A7 50 AC D4 7B ED 16 E7 7E 77 CB BA A9 85 0A
0A BC 69 96 3E B2 6A BD F3 47 1B 15 4A AE B1 32 C0 C4 D8 B0
C5 2F 81 1D 02 FD 52 F7 85
Exponent: 01 00 01
Signature: 00 2D 8D DD 0F 43 C7 16 BF DA 27 8A DF 10 32 1B F7 56 A0 97
04 0E 08 8A DE 8C 00 46 DE 18 99 84 58 F7 1B 46 8F 5B 0C 12
B7 1B 34 13 37 2D 2E DD 33 D2 C8 63 1E 76 AF D2 35 50 9B DE
A6 82 D5 90 1A 18 39 DF 0F 21 48 32 10 D2 8E F5 84 3D 5E 87
C8 C7 D2 B1 42 45 B5 13 CF 46 1B 64 DE BE 78 D7 E5 BD F3 38
06 99 89 A2 35 62 27 B7 91 4F 6C E0 87 52 68 5A 45 87 CC D5
F4 D7 38 26 00 E8 C6 D1 69
192.168.1.11
Subject Name:
Country: US
State/Province: Maryland
Locality: Columbia
Organization: Tenable Network Security, Inc.
Organization Unit: Certification Authority for SecurityCenter
Common Name: SecurityCenter
Email Address: SecurityCenter@SecurityCenter
Issuer Name:
Country: US
State/Province: Maryland
Locality: Columbia
Organization: Tenable Network Security, Inc.
Organization Unit: Certification Authority for SecurityCenter
Common Name: SecurityCenter
Email Address: SecurityCenter@SecurityCenter
Serial Number: 00 94 3A B2 53 56 B5 B9 13
Version: 3
Signature Algorithm: SHA-1 With RSA Encryption
Not Valid Before: Oct 27 13:49:56 2010 GMT
Not Valid After: Oct 26 13:49:56 2012 GMT
Public Key Info:
Algorithm: RSA Encryption
Public Key: 00 CF 1A A3 11 E0 4B 7F 7E E7 A9 87 67 32 7D D8 3C 09 6A F0
65 B4 C1 00 E9 59 28 BF 02 3D 50 77 1D 9C F5 FB E8 CF 57 34
C9 1D E3 80 60 BD 70 C9 88 00 95 08 78 6D 1F 9C 5B 90 D2 2C
93 36 20 6C 07 5C AF 11 7C B3 44 B1 9D DF EB F3 7E 83 3D 8E
F8 76 1D B9 1A C4 05 70 FE AE 45 D8 34 57 39 DD A8 6F 0A 65
18 9F 14 CC 75 04 79 9C 46 0F E4 35 3F EF 0B 0D C2 71 5A 69
7F 13 96 01 3D 46 EF EF 49
Exponent: 01 00 01
Signature: 00 38 D0 45 DF D9 D6 AF 7A D7 C9 B1 A9 74 69 B0 EF 86 F2 EA
84 A8 71 6C 7E 15 0E 4D 7A DA 6F 32 0F 5B C4 42 0F 12 8F FE
F2 78 1C 57 8B 67 EF 30 C5 EF C0 64 FB 7C F1 D4 D2 E4 09 64
80 FD 91 3C 20 A1 FA A2 91 16 3A 15 31 AE 19 2D 7C EC 97 51
DF 2C 90 1E 01 7A D5 01 1B FE 66 13 39 EB F8 17 71 2F 2B 0E
BA 8C F7 AE 8B 23 E5 61 D5 C5 59 2E 81 EA 94 E0 7F 92 F3 58
82 97 C2 AE AE 70 ED 70 BD
Extension: Subject Key Identifier (2.5.29.14)
Critical: 0
Subject Key Identifier: BC 54 88 2E 34 E3 65 81 DD C4 22 DE 07 DE 50 BE A4 6F 99 A7
Extension: Authority Key Identifier (2.5.29.35)
Critical: 0
Extension: Basic Constraints (2.5.29.19)
Critical: 1
Data: 30 00
Extension: Key Usage (2.5.29.15)
Critical: 0
Key Usage: Key Cert Signature, CRL Signature
Description
This plugin connects to every SSL-related port and attempts to
extract and dump the X.509 certificate.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/17
Port (0/tcp)
Plugin ID: 25202
Enumerate IPv6 Interfaces via SSH
Synopsis
This plugin enumerates IPv6 interfaces on a remote host.
List of Hosts Plugin Output
192.168.1.13
The following IPv6 interfaces are set on the remote host :
- fe80::2a0:ccff:fe3d:b3ba (on interface eth0)
- ::1 (on interface lo)
Description
By connecting to the remote host via SSH with the supplied
credentials, this plugin enumerates network interfaces configured with
IPv6 addresses.
Solution
Disable IPv6 if you do not actually using it. Otherwise, disable any
unused IPv6 interfaces.
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (0/tcp)
Plugin ID: 34098
BIOS version (SSH)
Synopsis
The BIOS version could be read.
List of Hosts Plugin Output
192.168.1.13
Version : 1002
Vendor : American Megatrends Inc.
Release Date : 04/11/2006
Description
Using the SMBIOS (aka DMI) interface, it was possible to get the BIOS
vendor and version.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/20
Port rpc-portmapper (111/udp)
Plugin ID: 10223
RPC portmapper Service Detection
Synopsis
An ONC RPC portmapper is running on the remote host.
List of Hosts
192.168.1.30
192.168.1.18
192.168.1.13
Description
The RPC portmapper is running on this port.
The portmapper allows someone to get the port number of each RPC
service running on the remote host by sending either multiple lookup
requests or a DUMP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/17
Port (0/tcp)
Plugin ID: 45590
Common Platform Enumeration (CPE)
Synopsis
It is possible to enumerate CPE names that matched on the remote
system.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.80
The remote operating system matched the following CPE's :
cpe:/o:linux:linux_kernel:2.4
cpe:/o:linux:linux_kernel:2.6
192.168.1.66
The remote operating system matched the following CPE :
cpe:/o:apple:mac_os_x:10.7
Following application CPE matched on the remote system :
cpe:/a:openbsd:openssh:5.2
192.168.1.60
The remote operating system matched the following CPE's :
cpe:/o:apple:mac_os_x:10.4 -> Apple Mac OS X 10.4
cpe:/o:apple:mac_os_x:10.5 -> Apple Mac OS X 10.5
192.168.1.30
The remote operating system matched the following CPE's :
cpe:/o:linux:linux_kernel:2.4
cpe:/o:linux:linux_kernel:2.6
Following application CPE matched on the remote system :
cpe:/a:samba:samba:3.0.34
192.168.1.26
The remote operating system matched the following CPE :
cpe:/o:ubuntu:ubuntu_linux:8.04 (Inferred CPE)
Following application CPE's matched on the remote system :
cpe:/a:php:php:5.2.4-2ubuntu5.9
cpe:/a:modssl:mod_ssl:2.2.8
cpe:/a:openbsd:openssh:4.7
cpe:/a:openssl:openssl:0.9.8g
cpe:/a:apache:http_server:2.2.8
192.168.1.233
The remote operating system matched the following CPE's :
cpe:/o:apple:mac_os_x:10.5 -> Apple Mac OS X 10.5
cpe:/o:apple:mac_os_x:10.6
cpe:/o:apple:mac_os_x:10.7
Following application CPE matched on the remote system :
cpe:/a:openbsd:openssh:5.2
192.168.1.215
The remote operating system matched the following CPE's :
cpe:/o:microsoft:windows_xp::sp2 -> Microsoft Windows XP Service Pack 2
cpe:/o:microsoft:windows_xp::sp3 -> Microsoft Windows XP Service Pack 3
192.168.1.19
The remote operating system matched the following CPE :
cpe:/o:linux:linux_kernel:2.6
Following application CPE matched on the remote system :
cpe:/a:openbsd:openssh:4.3 -> OpenBSD OpenSSH 4.3
192.168.1.180
The remote operating system matched the following CPE :
cpe:/o:microsoft:windows_server_2008::sp1
192.168.1.18
The remote operating system matched the following CPE :
cpe:/o:linux:linux_kernel:2.6
Following application CPE matched on the remote system :
cpe:/a:openbsd:openssh:4.3 -> OpenBSD OpenSSH 4.3
192.168.1.16
The remote operating system matched the following CPE :
cpe:/o:microsoft:windows_7:::ultimate
Following application CPE matched on the remote system :
cpe:/a:skype:skype:5.0.0.152
192.168.1.14
The remote operating system matched the following CPE :
cpe:/o:debian:debian_linux:5.0 -> Debian GNU/Linux 5.0
Following application CPE matched on the remote system :
cpe:/a:openbsd:openssh:5.1
192.168.1.13
The remote operating system matched the following CPE :
cpe:/o:centos:centos:5:update5
Following application CPE matched on the remote system :
cpe:/a:openbsd:openssh:4.3 -> OpenBSD OpenSSH 4.3
192.168.1.11
The remote operating system matched the following CPE :
cpe:/o:linux:linux_kernel:2.6
Following application CPE matched on the remote system :
cpe:/a:openbsd:openssh:4.3 -> OpenBSD OpenSSH 4.3
192.168.1.10
The remote operating system matched the following CPE :
cpe:/o:debian:debian_linux:5.0 -> Debian GNU/Linux 5.0
Following application CPE's matched on the remote system :
cpe:/a:openbsd:openssh:5.1
cpe:/a:isc:bind:Hack
192.168.1.1
The remote operating system matched the following CPE's :
cpe:/o:freebsd:freebsd:7.3
cpe:/o:freebsd:freebsd:7.4
Following application CPE matched on the remote system :
cpe:/a:openbsd:openssh:5.1
Description
By using information obtained from a Nessus scan, this plugin reports
CPE (Common Platform Enumeration) matches for various hardware and
software products found on a host.
Note that if an official CPE is not available for the product, this
plugin computes the best possible CPE based on the information
available from the scan.
Solution
n/a
See also
http://cpe.mitre.org/
Risk Factor
None
Plugin last modification date: 2011/03/08
Port www (3689/tcp)
Plugin ID: 41061
iTunes < 9.0.1 PLS File Buffer Overflow (uncredentialed check)
Synopsis
The remote host contains an application that is affected by a buffer
overflow vulnerability.
List of Hosts Plugin Output
192.168.1.60
iTunes 8.2.1 appears to be running on the remote host based on the
following response header :
DAAP-Server: iTunes/8.2.1 (Mac OS X)
Description
The remote version of iTunes is older than 9.0.1. Such versions are
affected by a buffer overflow involving the handling of PLS files. If
an attacker can trick a user on the affected host into opening a
malicious PLS file, he can leverage this issue to crash the affected
application or to execute arbitrary code on the affected system
subject to the user's privileges.
Solution
Upgrade to iTunes 9.0.1 or later.
See also
http://support.apple.com/kb/HT3884
http://lists.apple.com/archives/security-announce/2009/sep/msg00006.html
http://www.securityfocus.com/advisories/17952
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2009-2817
Bugtraq ID
36478
Other references
OSVDB:58271
CWE:119
Plugin publication date: 2009/09/23
Plugin last modification date: 2011/03/08
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port www (80/tcp)
Plugin ID: 44391
Linksys Router Detection
Synopsis
The remote device is a Linksys router.
List of Hosts Plugin Output
192.168.1.80
Model : WET610N
Description : Dual-Band Wireless-N Gaming and Video Adapter
Firmware : 1.0.03 build 351
Description
The remote device is a Linksys router. These devices route packets
and may provide port forwarding, DMZ configuration and other
networking services.
Solution
Ensure that use of this device agrees with your organization's
acceptable use and security policies.
See also
http://www.linksysbycisco.com/
Risk Factor
None
Plugin last modification date: 2011/02/26
Port dns (53/udp)
Plugin ID: 12217
DNS Server Cache Snooping Remote Information Disclosure
Synopsis
The remote DNS server is vulnerable to cache snooping attacks.
List of Hosts Plugin Output
192.168.1.10
Nessus sent a non-recursive query for example.com
and received 1 answer :
192.0.32.10
Description
The remote DNS server responds to queries for third-party domains
that do not have the recursion bit set.
This may allow a remote attacker to determine which domains have
recently been resolved via this name server, and therefore which hosts
have been recently visited.
For instance, if an attacker was interested in whether your company
utilizes the online services of a particular financial institution,
they would be able to use this attack to build a statistical model
regarding company usage of that financial institution. Of course, the
attack can also be used to find B2B partners, web-surfing patterns,
external mail servers, and more.
Note: If this is an internal DNS server not accessable to outside
networks, attacks would be limited to the internal network. This
may include employees, consultants and potentially users on
a guest network or WiFi connection if supported.
Solution
Contact the vendor of the DNS software for a fix.
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/30
Port (0/tcp)
Plugin ID: 44340
CentOS Update Set
Synopsis
The remote CentOS operating system is out-of-date.
List of Hosts Plugin Output
192.168.1.13
Installed version : 5.5
Latest version : 5.6
Description
The remote host is running a release of CentOS that is not at the
latest Update Set. Since updating CentOS brings a host up to the most
recent Update Set, this means that it has not been updated recently
and likely to be affected by multiple vulnerabilities.
Solution
Apply the latest Update Set.
See also
http://www.redhat.com/security/notes/
http://centos.org/modules/newbb/viewtopic.php?topic_id=24220&forum=37
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
Plugin last modification date: 2011/04/11
Port tftp (69/udp)
Plugin ID: 11819
TFTP Daemon Detection
Synopsis
A TFTP server is listening on the remote port.
List of Hosts
192.168.1.79
192.168.1.60
Description
The remote host is running a TFTP (Trivial File Transfer Protocol)
daemon. TFTP is often used by routers and diskless hosts to retrieve
their configuration. It is also used by worms to propagate.
Solution
Disable this service if you do not use it.
Risk Factor
None
Plugin last modification date: 2011/03/17
Port ssh (22/tcp)
Plugin ID: 39520
Backported Security Patch Detection (SSH)
Synopsis
Security patches are backported.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.66
Give Nessus credentials to perform local checks.
192.168.1.26
Give Nessus credentials to perform local checks.
192.168.1.233
Give Nessus credentials to perform local checks.
192.168.1.19
Give Nessus credentials to perform local checks.
192.168.1.18
Give Nessus credentials to perform local checks.
192.168.1.14
Give Nessus credentials to perform local checks.
192.168.1.13
192.168.1.11
Give Nessus credentials to perform local checks.
192.168.1.10
Give Nessus credentials to perform local checks.
192.168.1.1
Give Nessus credentials to perform local checks.
Description
Security patches may have been 'back ported' to the remote SSH server
without changing its version number.
Banner-based checks have been disabled to avoid false positives.
Note that this test is informational only and does not denote any
security problem.
Solution
N/A
See also
http://www.nessus.org/u?d636c8c7
Risk Factor
None
Plugin last modification date: 2011/03/16
Port www (443/tcp)
Plugin ID: 39521
Backported Security Patch Detection (WWW)
Synopsis
Security patches are backported.
List of Hosts Plugin Output
192.168.1.26
Give Nessus credentials to perform local checks.
Description
Security patches may have been 'back ported' to the remote HTTP server
without changing its version number.
Banner-based checks have been disabled to avoid false positives.
Note that this test is informational only and does not denote any
security problem.
Solution
N/A
See also
http://www.nessus.org/u?d636c8c7
Risk Factor
None
Plugin last modification date: 2011/03/18
Port www (80/tcp)
Plugin ID: 39521
Backported Security Patch Detection (WWW)
Synopsis
Security patches are backported.
List of Hosts Plugin Output
192.168.1.26
Give Nessus credentials to perform local checks.
Description
Security patches may have been 'back ported' to the remote HTTP server
without changing its version number.
Banner-based checks have been disabled to avoid false positives.
Note that this test is informational only and does not denote any
security problem.
Solution
N/A
See also
http://www.nessus.org/u?d636c8c7
Risk Factor
None
Plugin last modification date: 2011/03/18
Port www (2869/tcp)
Plugin ID: 11153
Service Detection (HELP Request)
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.16
A web server seems to be running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an 'HELP' request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/08
Port (0/udp)
Plugin ID: 10287
Traceroute Information
Synopsis
It was possible to obtain traceroute information.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.98
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.98 :
192.168.1.13
?
192.168.1.98
192.168.1.95
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.95 :
192.168.1.13
?
192.168.1.95
192.168.1.80
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.80 :
192.168.1.13
192.168.1.80
192.168.1.79
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.79 :
192.168.1.13
192.168.1.79
192.168.1.66
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.66 :
192.168.1.13
192.168.1.66
192.168.1.65
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.65 :
192.168.1.13
192.168.1.65
192.168.1.60
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.60 :
192.168.1.13
192.168.1.60
192.168.1.30
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.30 :
192.168.1.13
192.168.1.30
192.168.1.26
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.26 :
192.168.1.13
192.168.1.26
192.168.1.249
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.249 :
192.168.1.13
192.168.1.249
192.168.1.238
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.238 :
192.168.1.13
192.168.1.238
192.168.1.237
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.237 :
192.168.1.13
192.168.1.237
192.168.1.234
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.234 :
192.168.1.13
?
192.168.1.234
192.168.1.233
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.233 :
192.168.1.13
192.168.1.233
192.168.1.227
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.227 :
192.168.1.13
192.168.1.227
192.168.1.215
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.215 :
192.168.1.13
192.168.1.215
192.168.1.203
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.203 :
192.168.1.13
192.168.1.203
192.168.1.19
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.19 :
192.168.1.13
192.168.1.19
192.168.1.180
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.180 :
192.168.1.13
192.168.1.180
192.168.1.18
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.18 :
192.168.1.13
192.168.1.18
192.168.1.16
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.16 :
192.168.1.13
192.168.1.16
192.168.1.14
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.14 :
192.168.1.13
192.168.1.14
192.168.1.11
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.11 :
192.168.1.13
192.168.1.11
192.168.1.10
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.10 :
192.168.1.13
192.168.1.10
192.168.1.1
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.1 :
192.168.1.13
192.168.1.1
Description
Makes a traceroute to the remote host.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (0/tcp)
Plugin ID: 20094
VMware Virtual Machine Detection
Synopsis
The remote host seems to be a VMware virtual machine.
List of Hosts
192.168.1.26
192.168.1.19
192.168.1.180
192.168.1.18
Description
According to the MAC address of its network adapter, the remote host
is a VMware virtual machine.
Since it is physically accessible through the network, ensure that its
configuration matches your organization's security policy.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/27
Port (0/tcp)
Plugin ID: 12634
Authenticated Check: OS Name and Installed Package Enumeration
Synopsis
This plugin gathers information about the remote host via an
authenticated session.
List of Hosts Plugin Output
192.168.1.13
Nessus can run commands on localhost to check if patches are applied
The output of "uname -a" is :
Linux gogo 2.6.18-194.32.1.el5 #1 SMP Wed Jan 5 17:53:09 EST 2011 i686 i686 i386 GNU/Linux
Local security checks have been enabled for this host.
Description
This plugin logs into the remote host using SSH, RSH, RLOGIN, Telnet
or local commands and extracts the list of installed packages.
If using SSH, you should configure the scan with a valid SSH public
key and possibly an SSH passphrase (if the SSH public key is protected
by a passphrase).
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/01
Port (8099/tcp)
Plugin ID: 44318
HNAP Detection
Synopsis
The remote device has HNAP enabled.
List of Hosts
192.168.1.79
Description
The remote service supports the Home Network Administration Protocol
(HNAP), a SOAP-based protocol that provides a common interface for
administrative control of networked devices.
Solution
Limit incoming traffic to this port if desired.
See also
http://www.hnap.org/
http://www.cisco.com/web/partners/downloads/guest/hnap_protocol_whitepaper.pdf
Risk Factor
None
Plugin last modification date: 2011/02/26
Port www (80/tcp)
Plugin ID: 44318
HNAP Detection
Synopsis
The remote device has HNAP enabled.
List of Hosts
192.168.1.80
Description
The remote service supports the Home Network Administration Protocol
(HNAP), a SOAP-based protocol that provides a common interface for
administrative control of networked devices.
Solution
Limit incoming traffic to this port if desired.
See also
http://www.hnap.org/
http://www.cisco.com/web/partners/downloads/guest/hnap_protocol_whitepaper.pdf
Risk Factor
None
Plugin last modification date: 2011/02/26
Port mdns (5353/udp)
Plugin ID: 12218
mDNS Detection
Synopsis
It is possible to obtain information about the remote host.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.66
Nessus was able to extract the following information :
- mDNS hostname : johnnymo.local.
- Advertised services :
o Service name : johnnymo._ssh._tcp.local.
Port number : 22
o Service name : johnnymo._sftp-ssh._tcp.local.
Port number : 22
o Service name : A33E0296264E888D.227A9249F1997569._appletv-itunes._tcp.local.
Port number : 3689
192.168.1.60
Nessus was able to extract the following information :
- mDNS hostname : pdc-6.local.
- Advertised services :
o Service name : pdc (61) [00:17:f2:c8:da:c8]._workstation._tcp.local.
Port number : 9
o Service name : pdc (61)._net-assistant._udp.local.
Port number : 3283
o Service name : pdc (61)._rfb._tcp.local.
Port number : 5900
o Service name : pdc (61)._sftp-ssh._tcp.local.
Port number : 22
o Service name : pdc (61)._ssh._tcp.local.
Port number : 22
o Service name : Paul Asadoorian s Library_PW._daap._tcp.local.
Port number : 3689
192.168.1.30
Nessus was able to extract the following information :
- mDNS hostname : NAS-MAIN-OFFICE.local.
- Advertised services :
o Service name : NAS-MAIN-OFFICE [00:0d:a2:01:83:fb]._workstation._tcp.local.
Port number : 9
o Service name : ReadyNAS Discovery [NAS-MAIN-OFFICE]._readynas._tcp.local.
Port number : 9
- CPU type : PADRE
- OS : LINUX
192.168.1.26
Nessus was able to extract the following information :
- mDNS hostname : movabletype.local.
- Advertised services :
o Service name : movabletype [00:0c:29:17:b2:6f]._workstation._tcp.local.
Port number : 9
o Service name : movabletype on movabletype._http._tcp.local.
Port number : 80
o Service name : movabletype on movabletype._jumpbox-app._tcp.local.
Port number : 80
o Service name : movabletype administration on movabletype._https._tcp.local.
Port number : 3000
- CPU type : I686
- OS : LINUX
192.168.1.249
Nessus was able to extract the following information :
- mDNS hostname : Paul-Asadoorians-iPad.local.
192.168.1.238
Nessus was able to extract the following information :
- mDNS hostname : braydens-laptop.local.
- Advertised services :
o Service name : braydens-laptop [00:18:de:c1:de:8a]._workstation._tcp.local.
Port number : 9
- CPU type : I686
- OS : LINUX
192.168.1.234
Nessus was able to extract the following information :
- mDNS hostname : AppleTV.local.
- Advertised services :
o Service name : 70-35-10-73 AppleTV._sleep-proxy._udp.local.
Port number : 60456
o Service name : 76A17F1F1E099ACB._appletv._tcp.local.
Port number : 3689
o Service name : 76A17F1F1E099ACB._touch-able._tcp.local.
Port number : 3689
o Service name : iTunes_Ctrl_8EFC296D77A471B5._dacp._tcp.local.
Port number : 3689
192.168.1.233
Nessus was able to extract the following information :
- mDNS hostname : apollo-4.local.
- Advertised services :
o Service name : apollo._ssh._tcp.local.
Port number : 22
o Service name : apollo._sftp-ssh._tcp.local.
Port number : 22
o Service name : apollo._rfb._tcp.local.
Port number : 5900
o Service name : paulda@apollo._teleport._tcp.local.
Port number : 44176
192.168.1.215
Nessus was able to extract the following information :
- mDNS hostname : MEDIA1.local.
192.168.1.18
Nessus was able to extract the following information :
- mDNS hostname : lolce.local.
- Advertised services :
o Service name : lolce [00:0c:29:15:fd:8c]._workstation._tcp.local.
Port number : 9
- CPU type : I686
- OS : LINUX
192.168.1.14
Nessus was able to extract the following information :
- mDNS hostname : wpad.local.
- Advertised services :
o Service name : wpad [00:22:19:dc:a7:a9]._workstation._tcp.local.
Port number : 9
- CPU type : X86_64
- OS : LINUX
Description
The remote service understands the Bonjour (also known as ZeroConf or
mDNS) protocol, which allows anyone to uncover information from the
remote host such as its operating system type and exact version, its
hostname, and the list of services it is running.
Solution
Filter incoming traffic to UDP port 5353 if desired.
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/11
Port cifs (445/tcp)
Plugin ID: 40887
MS09-050: Microsoft Windows SMB2 _Smb2ValidateProviderCallback() Vulnerability (975497) (uncredentialed check)
Synopsis
Arbitrary code may be executed on the remote host through the SMB port
List of Hosts
192.168.1.180
Description
The remote host is running a version of Microsoft Windows Vista or
Windows Server 2008 that contains a vulnerability in its SMBv2
implementation.
An attacker could exploit this flaw to disable the remote host or to
execute arbitrary code on it.
Solution
Microsoft has released a patch for Windows Vista and Windows Server
2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-050.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 8.3(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2009-3103
Bugtraq ID
36299
Other references
CWE:399
OSVDB:57799
MSFT:MS09-050
Patch publication date: 2009/10/13
Plugin publication date: 2009/09/08
Plugin last modification date: 2011/03/11
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact, Metasploit (Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference)
Port (0/icmp)
Plugin ID: 11197
Multiple Ethernet Driver Frame Padding Information Disclosure (Etherleak)
Synopsis
The remote host appears to leak memory in network packets.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.98
Padding observed in one frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 E3 6F 2F ..............o/
0x10: 93 .
Padding observed in another frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 E0 F0 AF ................
0x10: 57 W
192.168.1.95
Padding observed in one frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 3A CF AD .............:..
0x10: 1F .
Padding observed in another frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 2B EB E5 .............+..
0x10: 9D .
192.168.1.65
Padding observed in one frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 7A B7 C7 .............z..
0x10: 94 .
Padding observed in another frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 C5 70 F8 ..............p.
0x10: 06 .
192.168.1.249
Padding observed in one frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 73 31 5C .............s1\
0x10: 8A .
Padding observed in another frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 69 80 1E .............i..
0x10: B4 .
192.168.1.238
Padding observed in one frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 9F 96 E9 ................
0x10: 91 .
Padding observed in another frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 76 E0 5B .............v.[
0x10: 8B .
192.168.1.237
Padding observed in one frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 C2 4B 85 ..............K.
0x10: BD .
Padding observed in another frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 C6 4F 83 ..............O.
0x10: 6B k
192.168.1.227
Padding observed in one frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 8D 05 A0 ................
0x10: A5 .
Padding observed in another frame :
0x00: 00 00 00 00 00 00 00 00 00 00 00 00 00 76 F0 6C .............v.l
0x10: F0 .
Description
The remote host uses a network device driver that pads ethernet
frames with data which vary from one packet to another, likely taken
from kernel memory, system memory allocated to the device driver, or a
hardware buffer on its network interface card.
Known as 'Etherleak', this information disclosure vulnerability may
allow an attacker to collect sensitive information from the affected
host provided he is on the same physical subnet as that host.
Solution
Contact the network device driver's vendor for a fix.
See also
http://www.nessus.org/u?719c90b4
Risk Factor
Low/ CVSS Base Score: 3.3
(CVSS2#AV:A/AC:L/Au:N/C:P/I:N/A:N)
CVSS Temporal Score: 2.4(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2003-0001
Bugtraq ID
6535
Other references
OSVDB:3873
Plugin publication date: 2003/01/14
Plugin last modification date: 2011/03/21
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 42410
Microsoft Windows NTLMSSP Authentication Request Remote Network Name Disclosure
Synopsis
It is possible to obtain the network name of the remote host.
List of Hosts Plugin Output
192.168.1.16
The following 2 NetBIOS names have been gathered :
O-REN = Computer name
O-REN = Workgroup / Domain name
Description
The remote host listens on tcp port 445 and replies to SMB requests.
By sending an NTLMSSP authentication request it is possible to obtain
the name of the remote system and the name of its domain.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/27
Port www (443/tcp)
Plugin ID: 51893
OpenSSL SSL_OP_NETSCAPE_REUSE_CIPHER_CHANGE_BUG Ciphersuite Disabled Cipher Issue
Synopsis
The remote host allows resuming SSL sessions.
List of Hosts Plugin Output
192.168.1.11
Session ID : 325bb8ad9e4e4afb76a0dd7b501fde839e7c55839bf32e4c83ecb3716c3718ce
Initial Cipher : TLS1_CK_DHE_RSA_WITH_AES_256_CBC_SHA (0x0039)
Resumed Cipher : TLS1_CK_DHE_DSS_WITH_3DES_EDE_CBC_SHA (0x0013)
Description
The version of OpenSSL on the remote host has been shown to allow the
use of disabled ciphers when resuming a session. This means that an
attacker that sees (e.g. by sniffing) the start of an SSL connection
can manipulate the OpenSSL session cache to cause subsequent resumes
of that session to use a disabled cipher chosen by the attacker.
Solution
Upgrade to OpenSSL 0.9.8j or later.
Risk Factor
Medium/ CVSS Base Score: 4.3
(CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N)
CVE
CVE-2008-7270
Bugtraq ID
45254
Other references
OSVDB:69655
Patch publication date: 2008/09/22
Plugin publication date: 2011/02/07
Plugin last modification date: 2011/03/30
Port (0/tcp)
Plugin ID: 11026
Wireless Access Point Detection
Synopsis
The remote host is a wireless access point.
List of Hosts Plugin Output
192.168.1.65
Nessus has determined that this device is an access point based on a
phrase found on the server's default web page. That is, Nessus
maintains a list of commonly-used technical phrases which can be
associated with wireless technologies. When Nessus encounters these
phrases during a scan, a determination is made regarding the nature of
the device. The exact phrase which Nessus flagged on is :
realm="WRT54
Description
Nessus has determined that the remote host is a wireless access point
(AP).
Ensure that proper physical and logical controls are in place for its
use. A misconfigured access point may allow an attacker to gain
access to an internal network without being physically present on the
premises. If the access point is using an 'off-the-shelf'
configuration (such as 40 or 104 bit WEP encryption), the data being
passed through the access point may be vulnerable to hijacking or
sniffing.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (8089/tcp)
Plugin ID: 50845
OpenSSL Detection
Synopsis
The remote service appears to use OpenSSL to encrypt traffic.
List of Hosts
192.168.1.180
Description
Based on its behavior, it seems that the remote service is using the
OpenSSL library to encrypt traffic.
Note that this plugin can only detect OpenSSL implementations that
have enabled support for TLS extensions (RFC 4366).
Solution
n/a
See also
http://www.openssl.org
Risk Factor
None
Plugin last modification date: 2011/03/11
Port www (443/tcp)
Plugin ID: 50845
OpenSSL Detection
Synopsis
The remote service appears to use OpenSSL to encrypt traffic.
List of Hosts
192.168.1.11
Description
Based on its behavior, it seems that the remote service is using the
OpenSSL library to encrypt traffic.
Note that this plugin can only detect OpenSSL implementations that
have enabled support for TLS extensions (RFC 4366).
Solution
n/a
See also
http://www.openssl.org
Risk Factor
None
Plugin last modification date: 2011/03/11
Port dns (53/udp)
Plugin ID: 10028
DNS Server BIND version Directive Remote Version Disclosure
Synopsis
It is possible to obtain the version number of the remote DNS server.
List of Hosts Plugin Output
192.168.1.10
The version of the remote DNS server is :
Hack Naked
Description
The remote host is running BIND or another DNS server that reports its
version number when it receives a special request, for the text
'version.bind' in the domain 'chaos'.
This version is not necessarily accurate and could even be forged, as
some DNS servers send the information based on a configuration file.
Solution
It is possible to hide the version number of bind by using the
'version' directive in the 'options' section in named.conf
Risk Factor
None
Other references
OSVDB:23
Plugin publication date: 1999/10/12
Plugin last modification date: 2011/03/11
Port (0/tcp)
Plugin ID: 21745
Authentication Failure - Local Checks Not Run
Synopsis
The local security checks are disabled.
List of Hosts Plugin Output
192.168.1.215
The local checks failed because :
the account used does not have sufficient privileges to read all the required registry entries
Description
The credentials provided for the scan did not allow us to log into the
remote host, or the remote operating system is not supported.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (88/tcp)
Plugin ID: 43829
Kerberos Information Disclosure
Synopsis
The remote Kerberos server is leaking information.
List of Hosts Plugin Output Plugin Output
192.168.1.233
Nessus gathered the following information :
Server time : 2011-04-13 17:01:55 UTC
192.168.1.180
Nessus gathered the following information :
Server time : 2011-04-13 19:59:15 UTC
Realm : TX.EC.NET
Description
Nessus was able to retrieve the realm name and/or server time of the
remote Kerberos server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port cifs (445/tcp)
Plugin ID: 10394
Microsoft Windows SMB Log In Possible
Synopsis
It is possible to log into the remote host.
List of Hosts Plugin Output Plugin Output Plugin Output Plugin Output
192.168.1.30
- NULL sessions are enabled on the remote host
- Remote users are authenticated as 'Guest'
192.168.1.215
- NULL sessions are enabled on the remote host
- Remote users are authenticated as 'Guest'
192.168.1.180
- NULL sessions are enabled on the remote host
192.168.1.16
- NULL sessions are enabled on the remote host
Description
The remote host is running Microsoft Windows operating
system or Samba, a CIFS/SMB server for Unix. It was
possible to log into it using one of the following
account :
- NULL session
- Guest account
- Given Credentials
Solution
n/a
See also
http://support.microsoft.com/support/kb/articles/Q143/4/74.ASP
http://support.microsoft.com/support/kb/articles/Q246/2/61.ASP
Risk Factor
None
Other references
OSVDB:297
OSVDB:3106
OSVDB:8230
OSVDB:10050
Plugin publication date: 2000/05/09
Plugin last modification date: 2011/03/21
Ease of exploitability: Exploits are available
Exploitable with: Metasploit (Microsoft Windows Authenticated User Code Execution)
Port www (443/tcp)
Plugin ID: 21208
Skype Stack Version Detection
Synopsis
It was possible to obtain the stack version and timestamp of the
remote Skype node.
List of Hosts Plugin Output
192.168.1.16
Stack version : 49
Stack timestamp : 2010/10/8 12:13
Skype version : Skype for Windows Version 5.0.0.152
Description
The remote host is running Skype, a peer-to-peer Voice over Internet
Protocol (VoIP) application.
By connecting to the remote port, it is possible to query the remote
service to obtain the stack version and its timestamp.
Solution
If this service is not needed, disable it. Note that filtering this
port will not be sufficient, since this software can establish
outgoing connections.
Risk Factor
None
Plugin last modification date: 2011/04/07
Port www (80/tcp)
Plugin ID: 21208
Skype Stack Version Detection
Synopsis
It was possible to obtain the stack version and timestamp of the
remote Skype node.
List of Hosts Plugin Output
192.168.1.16
Stack version : 49
Stack timestamp : 2010/10/8 12:13
Skype version : Skype for Windows Version 5.0.0.152
Description
The remote host is running Skype, a peer-to-peer Voice over Internet
Protocol (VoIP) application.
By connecting to the remote port, it is possible to query the remote
service to obtain the stack version and its timestamp.
Solution
If this service is not needed, disable it. Note that filtering this
port will not be sufficient, since this software can establish
outgoing connections.
Risk Factor
None
Plugin last modification date: 2011/04/07
Port cifs (445/tcp)
Plugin ID: 10397
Microsoft Windows SMB LanMan Pipe Server Listing Disclosure
Synopsis
It is possible to obtain network information.
List of Hosts Plugin Output
192.168.1.30
Here is the browse list of the remote host :
NAS-MAIN-OFFICE ( os : 0.0 )
Description
It was possible to obtain the browse list of the remote Windows system
by send a request to the LANMAN pipe. The browse list is the list of
the nearest Windows systems of the remote host.
Solution
n/a
Risk Factor
None
Other references
OSVDB:300
Plugin publication date: 2000/05/09
Plugin last modification date: 2011/03/04
Port www (3000/tcp)
Plugin ID: 26928
SSL Weak Cipher Suites Supported
Synopsis
The remote service supports the use of weak SSL ciphers.
List of Hosts Plugin Output
192.168.1.26
Here is the list of weak SSL ciphers supported by the remote server :
Low Strength Ciphers (< 56-bit key)
SSLv2
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
SSLv3
EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
TLSv1
EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Description
The remote host supports the use of SSL ciphers that offer either weak
encryption or no encryption at all.
Note: This is considerably easier to exploit if the attacker is on the
same physical network.
Solution
Reconfigure the affected application if possible to avoid use of weak
ciphers.
Risk Factor
Medium/ CVSS Base Score: 4.3
(CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/21
Port www (443/tcp)
Plugin ID: 26928
SSL Weak Cipher Suites Supported
Synopsis
The remote service supports the use of weak SSL ciphers.
List of Hosts Plugin Output
192.168.1.26
Here is the list of weak SSL ciphers supported by the remote server :
Low Strength Ciphers (< 56-bit key)
SSLv2
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
SSLv3
EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
TLSv1
EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Description
The remote host supports the use of SSL ciphers that offer either weak
encryption or no encryption at all.
Note: This is considerably easier to exploit if the attacker is on the
same physical network.
Solution
Reconfigure the affected application if possible to avoid use of weak
ciphers.
Risk Factor
Medium/ CVSS Base Score: 4.3
(CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/21
| 192.168.1.98 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:19 2011 |
| End time: | Wed Apr 13 12:58:03 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 0 |
| Low | 14 |
| Remote Host Information | |
| MAC address: | 00:18:f8:d8:09:20 |
| 192.168.1.95 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:19 2011 |
| End time: | Wed Apr 13 12:55:54 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 0 |
| Low | 14 |
| Remote Host Information | |
| MAC address: | 00:18:f8:d8:08:90 |
| 192.168.1.80 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:11 2011 |
| End time: | Wed Apr 13 12:54:40 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 0 |
| Low | 13 |
| Remote Host Information | |
| Operating System: | Linux Kernel 2.4 Linux Kernel 2.6 |
| DNS name: | xbox-main-office |
| IP address: | 192.168.1.80 |
| MAC address: | 00:25:9c:8f:80:dd |
| 192.168.1.79 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:11 2011 |
| End time: | Wed Apr 13 12:58:39 2011 |
| Number of vulnerabilities | |
| High | 2 |
| Medium | 1 |
| Low | 25 |
| Remote Host Information | |
| Operating System: | ipOS |
| MAC address: | 00:26:5a:fd:19:74 |
| 192.168.1.66 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:11 2011 |
| End time: | Wed Apr 13 12:55:05 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 1 |
| Low | 19 |
| Remote Host Information | |
| Operating System: | Mac OS X 10.7 iOS 4 |
| DNS name: | johnnymo |
| IP address: | 192.168.1.66 |
| MAC address: | 00:1f:f3:d0:b6:29 |
| 192.168.1.65 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:11 2011 |
| End time: | Wed Apr 13 12:57:46 2011 |
| Number of vulnerabilities | |
| High | 1 |
| Medium | 0 |
| Low | 11 |
| Remote Host Information | |
| Operating System: | 3Com SuperStack Switch HP ProCurve Switch VxWorks |
| MAC address: | 00:1a:70:75:b5:fb |
| 192.168.1.60 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:11 2011 |
| End time: | Wed Apr 13 12:54:52 2011 |
| Number of vulnerabilities | |
| High | 3 |
| Medium | 2 |
| Low | 17 |
| Remote Host Information | |
| Operating System: | Mac OS X 10.4 Mac OS X 10.5 |
| DNS name: | paimei |
| IP address: | 192.168.1.60 |
| MAC address: | 00:17:f2:c8:da:c8 |
| 192.168.1.30 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:10 2011 |
| End time: | Wed Apr 13 12:56:38 2011 |
| Number of vulnerabilities | |
| High | 1 |
| Medium | 2 |
| Low | 27 |
| Remote Host Information | |
| Operating System: | Linux Kernel 2.4 Linux Kernel 2.6 |
| NetBIOS name: | NAS-MAIN-OFFICE |
| MAC address: | 00:0d:a2:01:83:fb |
| 192.168.1.26 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:10 2011 |
| End time: | Wed Apr 13 12:55:45 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 9 |
| Low | 32 |
| Remote Host Information | |
| Operating System: | Linux Kernel 2.6 on Ubuntu Linux 8.04 (hardy) |
| NetBIOS name: | MOVABLETYPE |
| MAC address: | 00:0c:29:17:b2:6f |
| 192.168.1.249 | |
|---|---|
| Scan Time | |
| Start time: | |
| End time: | Wed Apr 13 13:06:09 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 1 |
| Low | 3 |
| Remote Host Information | |
| MAC address: | 7c:6d:62:cf:0a:33 |
| 192.168.1.245 | |
|---|---|
| Scan Time | |
| Start time: | |
| End time: | Wed Apr 13 12:57:12 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 0 |
| Low | 2 |
| Remote Host Information | |
| 192.168.1.238 | |
|---|---|
| Scan Time | |
| Start time: | |
| End time: | Wed Apr 13 12:57:47 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 1 |
| Low | 6 |
| Remote Host Information | |
| Operating System: | Linux Kernel |
| MAC address: | 00:18:de:c1:de:8a |
| 192.168.1.237 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:56:33 2011 |
| End time: | Wed Apr 13 12:58:42 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 0 |
| Low | 13 |
| Remote Host Information | |
| Operating System: | Cyber Switching ePower PDU |
| MAC address: | 00:0d:4b:63:c8:ef |
| 192.168.1.234 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:56:25 2011 |
| End time: | Wed Apr 13 12:58:46 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 2 |
| Low | 10 |
| Remote Host Information | |
| Operating System: | AppleTV/3.0 |
| MAC address: | 00:1b:63:f0:78:d1 |
| 192.168.1.233 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:56:25 2011 |
| End time: | Wed Apr 13 12:57:26 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 1 |
| Low | 15 |
| Remote Host Information | |
| Operating System: | Mac OS X 10.5 Mac OS X 10.6 Mac OS X 10.7 |
| MAC address: | c4:2c:03:08:6a:5f |
| 192.168.1.227 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:56:14 2011 |
| End time: | Wed Apr 13 12:58:36 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 0 |
| Low | 13 |
| Remote Host Information | |
| Operating System: | Cyber Switching ePower PDU |
| MAC address: | 00:0d:4b:4c:29:5f |
| 192.168.1.215 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:55:47 2011 |
| End time: | Wed Apr 13 13:00:17 2011 |
| Number of vulnerabilities | |
| High | 1 |
| Medium | 2 |
| Low | 22 |
| Remote Host Information | |
| Operating System: | Microsoft Windows XP Service Pack 2 Microsoft Windows XP Service Pack 3 |
| NetBIOS name: | MEDIA1 |
| MAC address: | 00:18:8b:0e:74:e6 |
| 192.168.1.203 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:55:16 2011 |
| End time: | Wed Apr 13 12:57:03 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 0 |
| Low | 5 |
| Remote Host Information | |
| MAC address: | 00:26:99:48:4d:4a |
| 192.168.1.19 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:10 2011 |
| End time: | Wed Apr 13 12:56:06 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 0 |
| Low | 12 |
| Remote Host Information | |
| Operating System: | Linux Kernel 2.6 |
| MAC address: | 00:0c:29:63:6f:24 |
| 192.168.1.180 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:38 2011 |
| End time: | Wed Apr 13 12:57:12 2011 |
| Number of vulnerabilities | |
| High | 1 |
| Medium | 4 |
| Low | 44 |
| Remote Host Information | |
| Operating System: | Microsoft Windows Server 2008 Service Pack 1 |
| NetBIOS name: | WIN-8BPIQBRO0CX |
| MAC address: | 00:0c:29:9d:a1:c6 |
| 192.168.1.18 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:10 2011 |
| End time: | Wed Apr 13 12:54:17 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 1 |
| Low | 18 |
| Remote Host Information | |
| Operating System: | Linux Kernel 2.6 |
| MAC address: | 00:0c:29:15:fd:8c |
| 192.168.1.16 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:10 2011 |
| End time: | Wed Apr 13 12:56:22 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 0 |
| Low | 32 |
| Remote Host Information | |
| Operating System: | Windows 7 Ultimate |
| NetBIOS name: | O-REN |
| MAC address: | 00:24:1d:52:d4:fb |
| 192.168.1.14 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:10 2011 |
| End time: | Wed Apr 13 12:54:28 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 1 |
| Low | 19 |
| Remote Host Information | |
| Operating System: | Linux Kernel 2.6 on Debian 5.0 (lenny) |
| MAC address: | 00:22:19:dc:a7:a9 |
| 192.168.1.13 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:09 2011 |
| End time: | Wed Apr 13 12:59:30 2011 |
| Number of vulnerabilities | |
| High | 1 |
| Medium | 5 |
| Low | 54 |
| Remote Host Information | |
| Operating System: | Linux Kernel 2.6.18-194.32.1.el5 on CentOS release 5.5 (Final) |
| DNS name: | gogo |
| IP address: | 192.168.1.13 |
| MAC address: | 00:a0:cc:3d:b3:ba 00:17:31:03:14:1f |
| 192.168.1.11 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:10 2011 |
| End time: | Wed Apr 13 12:57:23 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 5 |
| Low | 22 |
| Remote Host Information | |
| Operating System: | Linux Kernel 2.6 |
| DNS name: | hanzo |
| IP address: | 192.168.1.11 |
| MAC address: | 00:17:31:08:74:82 |
| 192.168.1.10 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:09 2011 |
| End time: | Wed Apr 13 12:54:23 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 2 |
| Low | 18 |
| Remote Host Information | |
| Operating System: | Linux Kernel 2.6 on Debian 5.0 (lenny) |
| DNS name: | madmonk |
| IP address: | 192.168.1.10 |
| MAC address: | 00:00:24:c9:55:21 |
| 192.168.1.1 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 13 12:53:09 2011 |
| End time: | Wed Apr 13 12:58:21 2011 |
| Number of vulnerabilities | |
| High | 0 |
| Medium | 0 |
| Low | 16 |
| Remote Host Information | |
| Operating System: | FreeBSD 7.3 FreeBSD 7.4 |
| DNS name: | linky |
| IP address: | 192.168.1.1 |
| MAC address: | 00:0d:b9:1c:0e:35 |