List of PlugIn IDs
The following plugin IDs have problems associated with them. Select the ID to review more detail.
Plugin id#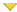 | # of issues | Plugin name | Severity |
|---|---|---|---|
| 52585 | 1 | MS11-017: Vulnerabilities in Remote Desktop Connection Could Allow Remote Code Execution (2508062) | High Severity problem(s) found |
| 51912 | 1 | MS11-012: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2479628) | High Severity problem(s) found |
| 51911 | 1 | MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) | High Severity problem(s) found |
| 51907 | 1 | MS11-007: Vulnerability in the OpenType Compact Font Format (CFF) Driver Could Allow Remote Code Execution (2485376) | High Severity problem(s) found |
| 51906 | 1 | MS11-006: Vulnerability in Windows Shell Graphics Processing Could Allow Remote Code Execution (2483185) | High Severity problem(s) found |
| 51903 | 1 | MS11-003: Cumulative Security Update for Internet Explorer (2482017) | High Severity problem(s) found |
| 51587 | 1 | MS KB2488013: Internet Explorer CSS Import Rule Processing Arbitrary Code Execution | High Severity problem(s) found |
| 51455 | 1 | MS11-002: Vulnerabilities in Microsoft Data Access Components Could Allow Remote Code Execution (2451910) | High Severity problem(s) found |
| 51352 | 1 | Microsoft .NET Framework Service Pack Out of Date | High Severity problem(s) found |
| 51172 | 1 | MS10-100: Vulnerability in Consent User Interface Could Allow Elevation of Privilege (2442962) | High Severity problem(s) found |
| 51170 | 1 | MS10-098: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2436673) | High Severity problem(s) found |
| 51168 | 1 | MS10-096: Vulnerability in Windows Address Book Could Allow Remote Code Execution (2423089) | High Severity problem(s) found |
| 51164 | 1 | MS10-092: Vulnerability in Task Scheduler Could Allow Elevation of Privilege (2305420) | High Severity problem(s) found |
| 51163 | 1 | MS10-091: Vulnerabilities in the OpenType Font (OTF) Driver Could Allow Remote Code Execution (2296199) | High Severity problem(s) found |
| 51162 | 1 | MS10-090: Cumulative Security Update for Internet Explorer (2416400) | High Severity problem(s) found |
| 49962 | 1 | MS10-085: Vulnerability in SChannel Could Allow Denial of Service (2207566) | High Severity problem(s) found |
| 49960 | 1 | MS10-083: Vulnerability in COM Validation in Windows Shell and WordPad Could Allow Remote Code Execution (2405882) | High Severity problem(s) found |
| 49958 | 1 | MS10-081: Vulnerability in Windows Common Control Library Could Allow Remote Code Execution (2296011) | High Severity problem(s) found |
| 49953 | 1 | MS10-076: Vulnerability in the Embedded OpenType Font Engine Could Allow Remote Code Execution (982132) | High Severity problem(s) found |
| 49951 | 1 | MS10-074: Vulnerability in Microsoft Foundation Classes Could Allow Remote Code Execution (2387149) | High Severity problem(s) found |
| 49950 | 1 | MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) | High Severity problem(s) found |
| 49948 | 1 | MS10-071: Cumulative Security Update for Internet Explorer (2360131) | High Severity problem(s) found |
| 49226 | 1 | MS10-068: Vulnerability in Local Security Authority Subsystem Service Could Allow Elevation of Privilege (983539) | High Severity problem(s) found |
| 49221 | 1 | MS10-063: Vulnerability in Unicode Scripts Processor Could Allow Remote Code Execution (2320113) | High Severity problem(s) found |
| 49219 | 1 | MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) | High Severity problem(s) found |
| 48405 | 1 | MS10-054: Vulnerabilities in SMB Server Could Allow Remote Code Execution (982214) (remote check) | High Severity problem(s) found |
| 48296 | 1 | MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) | High Severity problem(s) found |
| 48295 | 1 | MS10-058: Vulnerabilities in TCP/IP Could Allow Elevation of Privilege (978886) | High Severity problem(s) found |
| 48291 | 1 | MS10-054: Vulnerabilities in SMB Server Could Allow Remote Code Execution (982214) | High Severity problem(s) found |
| 48290 | 1 | MS10-053: Cumulative Security Update for Internet Explorer (2183461) | High Severity problem(s) found |
| 48288 | 1 | MS10-051: Vulnerability in Microsoft XML Core Services Could Allow Remote Code Execution (2079403) | High Severity problem(s) found |
| 48286 | 1 | MS10-049: Vulnerabilities in SChannel could allow Remote Code Execution (980436) | High Severity problem(s) found |
| 48285 | 1 | MS10-048: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2160329) | High Severity problem(s) found |
| 48284 | 1 | MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) | High Severity problem(s) found |
| 48216 | 1 | MS10-046: Vulnerability in Windows Shell Could Allow Remote Code Execution (2286198) | High Severity problem(s) found |
| 47750 | 1 | MS KB2286198: Windows Shell Shortcut Icon Parsing Arbitrary Code Execution | High Severity problem(s) found |
| 47556 | 1 | MS10-012: Vulnerabilities in SMB Could Allow Remote Code Execution (971468) (uncredentialed check) | High Severity problem(s) found |
| 46844 | 1 | MS10-037: Vulnerability in the OpenType Compact Font Format (CFF) Driver Could Allow Elevation of Privilege (980218) | High Severity problem(s) found |
| 46842 | 1 | MS10-035: Cumulative Security Update for Internet Explorer (982381) | High Severity problem(s) found |
| 46841 | 1 | MS10-034: Cumulative Security Update of ActiveX Kill Bits (980195) | High Severity problem(s) found |
| 46840 | 1 | MS10-033: Vulnerabilities in Media Decompression Could Allow Remote Code Execution (979902) | High Severity problem(s) found |
| 46839 | 1 | MS10-032: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (979559) | High Severity problem(s) found |
| 46312 | 1 | MS10-030: Vulnerability in Outlook Express and Windows Mail Could Allow Remote Code Execution (978542) | High Severity problem(s) found |
| 45509 | 1 | MS10-022: Vulnerability in VBScript Scripting Engine Could Allow Remote Code Execution (981169) | High Severity problem(s) found |
| 45507 | 1 | MS10-020: Vulnerabilities in SMB Client Could Allow Remote Code Execution (980232) | High Severity problem(s) found |
| 45506 | 1 | MS10-019: Vulnerabilities in Windows Could Allow Remote Code Execution (981210) | High Severity problem(s) found |
| 45378 | 1 | MS10-018: Cumulative Security Update for Internet Explorer (980182) | High Severity problem(s) found |
| 44423 | 1 | MS10-013: Vulnerability in Microsoft DirectShow Could Allow Remote Code Execution (977935) | High Severity problem(s) found |
| 44422 | 1 | MS10-012: Vulnerabilities in SMB Could Allow Remote Code Execution (971468) | High Severity problem(s) found |
| 44419 | 1 | MS10-009: Vulnerabilities in Windows TCP/IP Could Allow Remote Code Execution (974145) | High Severity problem(s) found |
| 44418 | 1 | MS10-008: Cumulative Security Update of ActiveX Kill Bits (978262) | High Severity problem(s) found |
| 44416 | 1 | MS10-006: Vulnerabilities in SMB Client Could Allow Remote Code Execution (978251) | High Severity problem(s) found |
| 44110 | 1 | MS10-002: Cumulative Security Update for Internet Explorer (978207) | High Severity problem(s) found |
| 43865 | 1 | MS10-001: Vulnerability in the Embedded OpenType Font Engine Could Allow Remote Code Execution (972270) | High Severity problem(s) found |
| 43064 | 1 | MS09-072: Cumulative Security Update for Internet Explorer (976325) | High Severity problem(s) found |
| 43063 | 1 | MS09-071: Vulnerabilities in Internet Authentication Service Could Allow Remote Code Execution (974318) | High Severity problem(s) found |
| 42440 | 1 | MS09-066: Vulnerability in Active Directory Could Allow Denial of Service (973309) | High Severity problem(s) found |
| 42439 | 1 | MS09-065: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (969947) | High Severity problem(s) found |
| 42437 | 1 | MS09-063: Vulnerability in Web Services on Devices API Could Allow Remote Code Execution (973565) | High Severity problem(s) found |
| 42118 | 1 | MS09-062: Vulnerabilities in GDI+ Could Allow Remote Code Execution (957488) | High Severity problem(s) found |
| 42115 | 1 | MS09-059: Vulnerability in Local Security Authority Subsystem Service Could Allow Denial of Service (975467) | High Severity problem(s) found |
| 42114 | 1 | MS09-058: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (971486) | High Severity problem(s) found |
| 42111 | 1 | MS09-055: Cumulative Security Update of ActiveX Kill Bits (973525) | High Severity problem(s) found |
| 42110 | 1 | MS09-054: Cumulative Security Update for Internet Explorer (974455) | High Severity problem(s) found |
| 42107 | 1 | MS09-051: Vulnerabilities in Windows Media Runtime Could Allow Remote Code Execution (975682) | High Severity problem(s) found |
| 42106 | 1 | MS09-050: Vulnerabilities in SMBv2 Could Allow Remote Code Execution (975517) | High Severity problem(s) found |
| 40891 | 1 | MS09-048: Vulnerabilities in Windows TCP/IP Could Allow Remote Code Execution (967723) | High Severity problem(s) found |
| 40888 | 1 | MS09-045: Vulnerability in JScript Scripting Engine Could Allow Remote Code Execution (971961) | High Severity problem(s) found |
| 40887 | 1 | MS09-050: Microsoft Windows SMB2 _Smb2ValidateProviderCallback() Vulnerability (975497) (uncredentialed check) | High Severity problem(s) found |
| 40565 | 1 | MS09-044: Vulnerabilities in Remote Desktop Connection Could Allow Remote Code Execution (970927) | High Severity problem(s) found |
| 40560 | 1 | MS09-041: Vulnerability in Workstation Service Could Allow Elevation of Privilege (971657) | High Severity problem(s) found |
| 40557 | 1 | MS09-038: Vulnerabilities in Windows Media File Processing Could Allow Remote Code Execution (971557) | High Severity problem(s) found |
| 40556 | 1 | MS09-037: Vulnerabilities in Microsoft Active Template Library (ATL) Could Allow Remote Code Execution (973908) | High Severity problem(s) found |
| 40407 | 1 | MS09-034: Cumulative Security Update for Internet Explorer (972260) | High Severity problem(s) found |
| 39792 | 1 | MS09-029: Vulnerabilities in the Embedded OpenType Font Engine Could Allow Remote Code Execution (961371) | High Severity problem(s) found |
| 39622 | 1 | MS09-032: Cumulative Security Update of ActiveX Kill Bits (973346) | High Severity problem(s) found |
| 39350 | 1 | MS KB969898: Cumulative Security Update of ActiveX Kill Bits | High Severity problem(s) found |
| 39348 | 1 | MS09-026: Vulnerability in RPC Could Allow Elevation of Privilege (970238) | High Severity problem(s) found |
| 39347 | 1 | MS09-025: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (968537) | High Severity problem(s) found |
| 39344 | 1 | MS09-022: Vulnerabilities in Windows Print Spooler Could Allow Remote Code Execution (961501) | High Severity problem(s) found |
| 39341 | 1 | MS09-019: Cumulative Security Update for Internet Explorer (969897) | High Severity problem(s) found |
| 36152 | 1 | MS09-014: Cumulative Security Update for Internet Explorer (963027) | High Severity problem(s) found |
| 36151 | 1 | MS09-013: Vulnerabilities in Windows HTTP Services Could Allow Remote Code Execution (960803) | High Severity problem(s) found |
| 36150 | 1 | MS09-012: Vulnerabilities in Windows Could Allow Elevation of Privilege (959454) | High Severity problem(s) found |
| 35822 | 1 | MS09-006: Vulnerabilities in Windows Kernel Could Allow Remote Code Execution (958690) | High Severity problem(s) found |
| 35634 | 1 | MS KB960715: Cumulative Security Update of ActiveX Kill Bits | High Severity problem(s) found |
| 35630 | 1 | MS09-002: Cumulative Security Update for Internet Explorer (961260) | High Severity problem(s) found |
| 35361 | 1 | MS09-001: Vulnerabilities in SMB Could Allow Remote Code Execution (958687) | High Severity problem(s) found |
| 35221 | 1 | MS08-078: Microsoft Internet Explorer Security Update (960714) | High Severity problem(s) found |
| 35072 | 1 | MS08-073: Microsoft Internet Explorer Multiple Vulnerabilities (958215) | High Severity problem(s) found |
| 35070 | 1 | MS08-071: Vulnerabilities in GDI+ Could Allow Remote Code Execution (956802) | High Severity problem(s) found |
| 34744 | 1 | MS08-069: Vulnerabilities in Microsoft XML Core Services Could Allow Remote Code Execution (955218) | High Severity problem(s) found |
| 34743 | 1 | MS08-068: Vulnerability in SMB Could Allow Remote Code Execution (957097) | High Severity problem(s) found |
| 34476 | 1 | MS08-067: Microsoft Windows Server Service Crafted RPC Request Handling Unspecified Remote Code Execution (958644) | High Severity problem(s) found |
| 34414 | 1 | MS KB956391: Cumulative Security Update of ActiveX Kill Bits | High Severity problem(s) found |
| 34409 | 1 | MS08-064: Microsoft Windows Virtual Address Descriptors (VAD) Local Privilege Escalation (956841) | High Severity problem(s) found |
| 34408 | 1 | MS08-063: Microsoft Windows SMB File Name Handling Remote Underflow (957095) | High Severity problem(s) found |
| 34406 | 1 | MS08-061: Microsoft Windows Kernel Multiple Privilege Elevation (954211) | High Severity problem(s) found |
| 34403 | 1 | MS08-058: Microsoft Internet Explorer Multiple Vulnerabilities (956390) | High Severity problem(s) found |
| 33881 | 1 | MS KB953839: Cumulative Security Update of ActiveX Kill Bits | High Severity problem(s) found |
| 33878 | 1 | MS08-049: Vulnerabilities in Event System Could Allow Remote Code Execution (950974) | High Severity problem(s) found |
| 33874 | 1 | MS08-045: Cumulative Security Update for Internet Explorer (953838) | High Severity problem(s) found |
| 33135 | 1 | MS08-033: Vulnerabilities in DirectX Could Allow Remote Code Execution (951698) | High Severity problem(s) found |
| 33134 | 1 | MS08-032: Cumulative Security Update of ActiveX Kill Bits (950760) | High Severity problem(s) found |
| 33133 | 1 | MS08-031: Cumulative Security Update for Internet Explorer (950759) | High Severity problem(s) found |
| 31798 | 1 | MS08-025: Vulnerability in Windows Kernel Could Allow Elevation of Privilege (941693) | High Severity problem(s) found |
| 31797 | 1 | MS08-024: Cumulative Security Update for Internet Explorer (947864) | High Severity problem(s) found |
| 31794 | 1 | MS08-021: Vulnerabilities in GDI Could Allow Remote Code Execution (948590) | High Severity problem(s) found |
| 52977 | 1 | MS KB2524375: Fraudulent Digital Certificates Could Allow Spoofing | Medium Severity problem(s) found |
| 51837 | 1 | MS KB2501696: Vulnerability in MHTML Could Allow Information Disclosure | Medium Severity problem(s) found |
| 51173 | 1 | MS10-101: Vulnerability in Windows Netlogon Service Could Allow Denial of Service (2207559) | Medium Severity problem(s) found |
| 49695 | 1 | MS10-070: Vulnerability in ASP.NET Could Allow Information Disclosure (2418042) | Medium Severity problem(s) found |
| 48761 | 1 | MS KB982316: Elevation of Privilege Using Windows Service Isolation Bypass | Medium Severity problem(s) found |
| 45516 | 1 | MS10-029: Vulnerability in Windows ISATAP Component Could Allow Spoofing (978338) | Medium Severity problem(s) found |
| 45508 | 1 | MS10-021: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (979683) | Medium Severity problem(s) found |
| 44425 | 1 | MS10-015: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (977165) | Medium Severity problem(s) found |
| 44424 | 1 | MS10-014: Vulnerability in Kerberos Could Allow Denial of Service (977290) | Medium Severity problem(s) found |
| 42112 | 1 | MS09-056: Vulnerabilities in Windows CryptoAPI Could Allow Spoofing (974571) | Medium Severity problem(s) found |
| 36153 | 1 | MS09-015: Blended Threat Vulnerability in SearchPath Could Allow Elevation of Privilege (959426) | Medium Severity problem(s) found |
| 35824 | 1 | MS09-008: Vulnerabilities in DNS and WINS Server Could Allow Spoofing (962238) | Medium Severity problem(s) found |
| 35823 | 1 | MS09-007: Vulnerability in SChannel Could Allow Spoofing (960225) | Medium Severity problem(s) found |
| 35074 | 1 | MS08-075: Vulnerabilities in Windows Search Could Allow Remote Code Execution (959349) | Medium Severity problem(s) found |
| 33877 | 1 | MS08-048: Security Update for Outlook Express and Windows Mail (951066) | Medium Severity problem(s) found |
| 33876 | 1 | MS08-047: Vulnerability in IPsec Policy Processing Could Allow Information Disclosure (953733) | Medium Severity problem(s) found |
| 33442 | 1 | MS08-038: Vulnerability in Windows Explorer Could Allow Remote Code Execution (950582) | Medium Severity problem(s) found |
| 33441 | 1 | MS08-037: Vulnerabilities in DNS Could Allow Spoofing (953230) | Medium Severity problem(s) found |
| 33138 | 1 | MS08-035: Vulnerability in Active Directory Could Allow Denial of Service (953235) | Medium Severity problem(s) found |
| 51351 | 1 | Microsoft .NET Framework Detection | Low Severity problem(s) found |
| 48942 | 1 | Microsoft Windows SMB Registry : OS Version and Processor Architecture | Low Severity problem(s) found |
| 48337 | 1 | Windows ComputerSystemProduct Enumeration (WMI) | Low Severity problem(s) found |
| 44871 | 1 | WMI Server Feature Enumeration | Low Severity problem(s) found |
| 44401 | 1 | Microsoft Windows SMB Service Config Enumeration | Low Severity problem(s) found |
| 38912 | 1 | Microsoft Windows SMB Registry : Vista / Server 2008 Service Pack Detection | Low Severity problem(s) found |
| 38153 | 1 | Microsoft Windows Summary of Missing Patches | Low Severity problem(s) found |
| 34252 | 34 | Microsoft Windows Remote Listeners Enumeration (WMI) | Low Severity problem(s) found |
| 34220 | 1 | Netstat Portscanner (WMI) | Low Severity problem(s) found |
| 34096 | 1 | BIOS Version (WMI) | Low Severity problem(s) found |
| 26920 | 1 | Microsoft Windows SMB NULL Session Authentication | Low Severity problem(s) found |
| 24272 | 1 | Network Interfaces Enumeration (WMI) | Low Severity problem(s) found |
| 24270 | 1 | Computer Manufacturer Information (WMI) | Low Severity problem(s) found |
| 24269 | 1 | Windows Management Instrumentation (WMI) Available | Low Severity problem(s) found |
| 20811 | 1 | Microsoft Windows Installed Software Enumeration (credentialed check) | Low Severity problem(s) found |
| 17651 | 1 | Microsoft Windows SMB : Obtains the Password Policy | Low Severity problem(s) found |
| 11457 | 1 | Microsoft Windows SMB Registry : Winlogon Cached Password Weakness | Low Severity problem(s) found |
| 11011 | 2 | Microsoft Windows SMB Service Detection | Low Severity problem(s) found |
| 10916 | 1 | Microsoft Windows - Local Users Information : Passwords never expire | Low Severity problem(s) found |
| 10915 | 1 | Microsoft Windows - Local Users Information : User has never logged on | Low Severity problem(s) found |
| 10913 | 1 | Microsoft Windows - Local Users Information : Disabled accounts | Low Severity problem(s) found |
| 10908 | 1 | Microsoft Windows 'Domain Administrators' Group User List | Low Severity problem(s) found |
| 10902 | 1 | Microsoft Windows 'Administrators' Group User List | Low Severity problem(s) found |
| 10900 | 1 | Microsoft Windows - Users Information : Passwords never expires | Low Severity problem(s) found |
| 10899 | 1 | Microsoft Windows - Users Information : User has never logged in | Low Severity problem(s) found |
| 10898 | 1 | Microsoft WIndows - Users Information : Never changed password | Low Severity problem(s) found |
| 10897 | 1 | Microsoft Windows - Users Information : disabled accounts | Low Severity problem(s) found |
| 10860 | 1 | SMB Use Host SID to Enumerate Local Users | Low Severity problem(s) found |
| 10859 | 1 | Microsoft Windows SMB LsaQueryInformationPolicy Function SID Enumeration | Low Severity problem(s) found |
| 10785 | 1 | Microsoft Windows SMB NativeLanManager Remote System Information Disclosure | Low Severity problem(s) found |
| 10761 | 1 | COM+ Internet Services (CIS) Server Detection | Low Severity problem(s) found |
| 10736 | 11 | DCE Services Enumeration | Low Severity problem(s) found |
| 10456 | 1 | Microsoft Windows SMB Service Enumeration | Low Severity problem(s) found |
| 10413 | 1 | Microsoft Windows SMB Registry : Remote PDC/BDC Detection | Low Severity problem(s) found |
| 10400 | 1 | Microsoft Windows SMB Registry Remotely Accessible | Low Severity problem(s) found |
| 10399 | 1 | SMB Use Domain SID to Enumerate Users | Low Severity problem(s) found |
| 10398 | 1 | Microsoft Windows SMB LsaQueryInformationPolicy Function NULL Session Domain SID Enumeration | Low Severity problem(s) found |
| 10396 | 1 | Microsoft Windows SMB Shares Access | Low Severity problem(s) found |
| 10395 | 1 | Microsoft Windows SMB Shares Enumeration | Low Severity problem(s) found |
| 10394 | 1 | Microsoft Windows SMB Log In Possible | Low Severity problem(s) found |
| 10150 | 1 | Windows NetBIOS / SMB Remote Host Information Disclosure | Low Severity problem(s) found |
Port (0/tcp)
Plugin ID: 10900
Microsoft Windows - Users Information : Passwords never expires
Synopsis
At least one user has a password that never expires.
List of Hosts Plugin Output
192.168.1.180
The following users have passwords that never expire :
- Guest
- WIN-8BPIQBRO0CX$
- EXCHANGE$
Note that, in addition to the Administrator, Guest, and Kerberos
accounts, Nessus has enumerated only those domain users with UIDs
between 1000 and 1200. To use a different range, edit the scan policy
and change the 'Start UID' and/or 'End UID' preferences for this
plugin, then re-run the scan.
Description
Using the supplied credentials, it is possible to list users whose
passwords never expire.
Solution
Allow / require users to change their passwords regularly.
Risk Factor
None
Plugin last modification date: 2011/03/21
Port cifs (445/tcp)
Plugin ID: 10395
Microsoft Windows SMB Shares Enumeration
Synopsis
It is possible to enumerate remote network shares.
List of Hosts Plugin Output
192.168.1.180
Here are the SMB shares available on the remote host when logged as administrator:
- ADMIN$
- C$
- IPC$
- NETLOGON
- SYSVOL
Description
By connecting to the remote host, Nessus was able to enumerate
the network share names.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 52977
MS KB2524375: Fraudulent Digital Certificates Could Allow Spoofing
Synopsis
The remote Windows host has an out-of-date SSL certificate blacklist.
List of Hosts Plugin Output
192.168.1.180
Nessus was unable to open the following registry key :
SOFTWARE\Microsoft\SystemCertificates\Disallowed\Certificates\1916A2AF346D399F50313C393200F14140456616
This indicates the update has not been applied.
Description
The remote host is missing KB2524375, which updates the system's SSL
certificate blacklist.
A certificate authority (CA) has revoked a number of fraudulent SSL
certificates for several prominent public websites. Without this
update, browsers will be unable to learn that the certificates have
been revoked if either Online Certificate Status Protocol (OCSP) is
disabled, or OCSP is enabled and fails.
If an attacker can trick someone into using the affected browser and
visiting a malicious site using one of the fraudulent certificates, he
may be able to fool that user into believing the site is a legitimate
one. In turn, the user could send credentials to the malicious site
or download and install applications.
Solution
Apply the relevant update provided by Microsoft.
See also
http://www.nessus.org/u?b8fdcaa8
http://www.comodo.com/Comodo-Fraud-Incident-2011-03-23.html
http://www.microsoft.com/technet/security/advisory/2524375.mspx
http://support.microsoft.com/kb/2524375
Risk Factor
Medium/ CVSS Base Score: 6.8
(CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P)
Patch publication date: 2011/03/23
Plugin publication date: 2011/03/25
Plugin last modification date: 2011/03/28
Port cifs (445/tcp)
Plugin ID: 35634
MS KB960715: Cumulative Security Update of ActiveX Kill Bits
Synopsis
The remote Windows host is missing a security update containing
ActiveX kill bits.
List of Hosts Plugin Output
192.168.1.180
The kill-bit has not been set for the following control :
{FFBB3F3B-0A5A-4106-BE53-DFE1E2340CB1}
Note that Nessus did not check whether there were other kill-bits
that have not been set because 'Thorough Tests' was not enabled
when this scan was run.
Description
The remote host is missing a list of kill bits for ActiveX controls
that are known to contain vulnerabilities.
If these ActiveX controls are ever installed on the remote host,
either now or in the future, they would expose it to various security
issues.
Solution
Microsoft has released an advisory about this :
http://www.microsoft.com/technet/security/advisory/960715.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2009-0305
Bugtraq ID
33663
Other references
OSVDB:51833
CWE:119
Plugin last modification date: 2011/03/16
Ease of exploitability: Exploits are available
Exploitable with: Canvas (D2ExploitPack)
Port (0/tcp)
Plugin ID: 10897
Microsoft Windows - Users Information : disabled accounts
Synopsis
At least one user account has been disabled.
List of Hosts Plugin Output
192.168.1.180
The following user accounts have been disabled :
- Guest
- krbtgt
- 249E6E5E-02B7-46F0-B
Note that, in addition to the Administrator, Guest, and Kerberos
accounts, Nessus has enumerated only those domain users with UIDs
between 1000 and 1200. To use a different range, edit the scan policy
and change the 'Start UID' and/or 'End UID' preferences for
'SMB use domain SID to enumerate users' setting, and then re-run the scan.
Description
Using the supplied credentials, it is possible to list user accounts
that have been disabled.
Solution
Delete accounts that are no longer needed.
Risk Factor
None
Plugin last modification date: 2011/03/21
Port cifs (445/tcp)
Plugin ID: 10785
Microsoft Windows SMB NativeLanManager Remote System Information Disclosure
Synopsis
It is possible to obtain information about the remote operating
system.
List of Hosts Plugin Output
192.168.1.180
The remote Operating System is : Windows Server (R) 2008 Standard 6001 Service Pack 1
The remote native lan manager is : Windows Server (R) 2008 Standard 6.0
The remote SMB Domain Name is : TX
Description
It is possible to get the remote operating system name and
version (Windows and/or Samba) by sending an authentication
request to port 139 or 445.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/17
Port cifs (445/tcp)
Plugin ID: 40557
MS09-038: Vulnerabilities in Windows Media File Processing Could Allow Remote Code Execution (971557)
Synopsis
Arbitrary code can be executed on the remote host through Windows
Media file processing.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\Avifil32.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18270
Description
The remote Windows host is affected by two vulnerabilities involving
the way in which AVI headers are processed and AVI data is validated
that could be abused to execute arbitrary code remotely.
If an attacker can trick a user on the affected system into opening
a specially crafted AVI file, he may be able to leverage these issues
to execute arbitrary code subject to the user's privileges.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-038.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.3(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:56908
OSVDB:56909
CWE:189
MSFT:MS09-038
Patch publication date: 2009/08/11
Plugin publication date: 2009/08/11
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 48405
MS10-054: Vulnerabilities in SMB Server Could Allow Remote Code Execution (982214) (remote check)
Synopsis
It is possible to execute arbitrary code on the remote Windows host
due to flaws in its SMB implementation.
List of Hosts
192.168.1.180
Description
The remote host is affected by several vulnerabilities in the SMB
server that may allow an attacker to execute arbitrary code or perform
a denial of service against the remote host. These vulnerabilities
depend on access to a shared drive, but do not necessarily require
credentials.
Solution
Microsoft has released a set of patches for Windows XP, Vista, 2008,
7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-054.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.8(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:66974
OSVDB:66975
OSVDB:66976
EDB-ID:14607
MSFT:MS10-054
Patch publication date: 2010/08/10
Plugin publication date: 2010/08/23
Plugin last modification date: 2011/03/14
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 39622
MS09-032: Cumulative Security Update of ActiveX Kill Bits (973346)
Synopsis
The remote Windows host is missing a security update containing
ActiveX kill bits.
List of Hosts Plugin Output
192.168.1.180
The kill-bit has not been set for the following control :
{011B3619-FE63-4814-8A84-15A194CE9CE3}
Note that Nessus did not check whether there were other kill-bits
that have not been set because 'Thorough Tests' was not enabled
when this scan was run.
Description
The remote host is missing a list of kill bits for ActiveX controls
that are known to contain vulnerabilities.
If these ActiveX controls are ever installed on the remote host,
either now or in the future, they would expose it to various security
issues.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-032.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2008-0015
Bugtraq ID
35558
Other references
CWE:119
OSVDB:55651
MSFT:MS09-032
Patch publication date: 2009/07/14
Plugin publication date: 2009/07/07
Plugin last modification date: 2011/03/16
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact, Metasploit (Microsoft DirectShow (msvidctl.dll) MPEG-2 Memory Corruption)
Port cifs (445/tcp)
Plugin ID: 36151
MS09-013: Vulnerabilities in Windows HTTP Services Could Allow Remote Code Execution (960803)
Synopsis
The remote host contains an API that is affected by multiple
vulnerabilities.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Winhttp.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18178
Description
The version of Windows HTTP Services installed on the remote host is
affected by several vulnerabilities :
- An integer underflow triggered by a specially crafted
response from a malicious web server (for example,
during device discovery of UPnP devices on a network)
may allow for arbitrary code execution. (CVE-2009-0086)
- Incomplete validation of the distinguished name in a
digital certificate may, in combination with other
attacks, allow an attacker to successfully spoof the
digital certificate of a third-party web site.
(CVE-2009-0089)
- A flaw in the way that Windows HTTP Services handles
NTLM credentials may allow an attacker to reflect back
a user's credentials and thereby gain access as that
user. (CVE-2009-0550)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-013.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:53619
OSVDB:53620
OSVDB:53621
CWE:20
MSFT:MS09-013
Plugin last modification date: 2011/03/11
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port (0/tcp)
Plugin ID: 10899
Microsoft Windows - Users Information : User has never logged in
Synopsis
At least one user has never logged in to his / her account.
List of Hosts Plugin Output
192.168.1.180
The following users have never logged in :
- Guest
- krbtgt
- 249E6E5E-02B7-46F0-B
- pcurrie
- dtouart
- sgieber
- fcrumb
- cvukelj
- aballs
- idepierre
- mmcleroy
- kmalavet
- tjank
- fdraxler
- cpaskell
- mcosgrave
- deichert
- lmicha
- kbarroso
- vroutte
- rschummer
- lfollett
- pcoladonato
- gdelreal
- lthroneberry
- lmccarn
- mlutjen
- vkonkel
- asponsler
- metzkorn
- tmcquirter
- fconcannon
- lyouker
- mamini
- lrosko
- dcolligan
- fprok
- vnickleberry
- afeurtado
- rgerczak
- hvanhekken
- cdoudna
- sbessent
- wlorimor
- hkarmazyn
- sdechambeau
- lsotelo
- aterris
- mkanta
- atopacio
- gkamphoefner
- abergmeier
- ksorrentino
- lgiacchino
- mmajorga
- fcosby
- lsimcic
- ltabor
- lschweickert
- dbrueckman
- scalverley
- tstansfield
- fpassarelli
- tkreinhagen
- dkoenigsberg
- asteltenpohl
- agoonen
- smockler
- npacheco
- ycambell
- schesher
- mwinegardner
- spoissant
- jlicerio
- murman
- cvrazel
- czoelle
- apaulshock
- gbartus
- edorrough
- jdifiora
- jteno
- tmichel
- bbegan
- aconelli
- ceuton
- sadelmann
- slook
- jhoffpavir
- nholsing
- mscouller
- jbroadwater
- ebrentlinger
- ablaske
- iguzon
- smceldowney
Note that, in addition to the Administrator, Guest, and Kerberos
accounts, Nessus has enumerated only those domain users with UIDs
between 1000 and 1200. To use a different range, edit the scan policy
and change the 'Start UID' and/or 'End UID' preferences for
'SMB use domain SID to enumerate users' setting, and then re-run the scan.
Description
Using the supplied credentials, it is possible to list users who have
never logged into their accounts.
Solution
Delete accounts that are not needed.
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (0/tcp)
Plugin ID: 10913
Microsoft Windows - Local Users Information : Disabled accounts
Synopsis
At least one local user account has been disabled.
List of Hosts Plugin Output
192.168.1.180
The following local user accounts have been disabled :
- Guest
- 249E6E5E-02B7-46F0-B
Note that, in addition to the Administrator and Guest accounts, Nessus
has only checked for local users with UIDs between 1000 and 1200.
To use a different range, edit the scan policy and change the 'Start
UID' and/or 'End UID' preferences for 'SMB use host SID to enumerate
local users' setting, and then re-run the scan.
Description
Using the supplied credentials, it is possible to list local user
accounts that have been disabled.
Solution
Delete accounts that are no longer needed.
Risk Factor
None
Other references
OSVDB:752
Plugin publication date: 2002/03/17
Plugin last modification date: 2011/03/21
Port cifs (445/tcp)
Plugin ID: 33134
MS08-032: Cumulative Security Update of ActiveX Kill Bits (950760)
Synopsis
The remote Windows host has an ActiveX control that is affected by
multiple memory corruption vulnerabilities.
List of Hosts Plugin Output
192.168.1.180
The kill-bit has not been set for the following control :
{40F23EB7-B397-4285-8F3C-AACE4FA40309}
Note that Nessus did not check whether there were other kill-bits
that have not been set because 'Thorough Tests' was not enabled
when this scan was run.
Description
The remote host contains the sapi.dll ActiveX control.
The version of this control installed on the remote host reportedly
contains multiple memory corruption flaws. If an attacker can trick a
user on the affected host into visiting a specially-crafted web page,
he may be able to leverage this issue to execute arbitrary code on the
host subject to the user's privileges.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms08-032.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
Bugtraq ID
29558
Other references
OSVDB:33627
OSVDB:46062
OSVDB:46076
OSVDB:46087
CWE:119
MSFT:MS08-032
Plugin publication date: 2008/06/10
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 49960
MS10-083: Vulnerability in COM Validation in Windows Shell and WordPad Could Allow Remote Code Execution (2405882)
Synopsis
The remote windows host is affected by a remote code execution
vulnerability.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Ole32.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18498
Description
The remote windows host contains a version of the Windows Shell or
the WordPad text editor that contains a vulnerability in the way it
handles shortcut files.
An attacker, exploiting this flaw, can execute arbitrary commands on
the remote host subject to the privileges of the user opening the
file.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-083.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2010-1263
Bugtraq ID
40574
Other references
OSVDB:65219
MSFT:MS10-083
Patch publication date: 2010/10/12
Plugin publication date: 2010/10/13
Plugin last modification date: 2011/03/22
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 36150
MS09-012: Vulnerabilities in Windows Could Allow Elevation of Privilege (959454)
Synopsis
A local user can elevate his privileges on the remote host.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\Ntoskrnl.exe has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18226
Description
The version of Windows running on the remote host is affected by
potentially four vulnerabilities involving its MSDTC transaction
facility and/or Windows Service Isolation that may allow a local user
to escalate his privileges and take complete control of the affected
system.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-012.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 5.6(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:44580
OSVDB:53666
OSVDB:53667
OSVDB:53668
CWE:264
MSFT:MS09-012
Plugin last modification date: 2011/03/14
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 51907
MS11-007: Vulnerability in the OpenType Compact Font Format (CFF) Driver Could Allow Remote Code Execution (2485376)
Synopsis
The remote Windows host contains a font driver that is affected by a
privilege escalation vulnerability.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Atmfd.dll has not been patched
Remote version : 5.1.2.226
Should be : 5.1.2.231
Description
The remote Windows host contains a version of the OpenType Compact
Font Format (CFF) Font Driver that fails to properly validate certain
data passed from user mode to kernel mode.
A remote attacker could exploit this by tricking a user into viewing
content rendered in a specially crafted CFF font (via vectors such as
web, instant message, or email), resulting in arbitrary code execution
in kernel mode.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2:
http://www.microsoft.com/technet/security/Bulletin/MS11-007.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVE
CVE-2011-0033
Bugtraq ID
46106
Other references
OSVDB:70821
MSFT:MS11-007
Patch publication date: 2011/02/08
Plugin publication date: 2011/02/08
Plugin last modification date: 2011/03/09
Port cifs (445/tcp)
Plugin ID: 10413
Microsoft Windows SMB Registry : Remote PDC/BDC Detection
Synopsis
The remote system is a Domain Controller.
List of Hosts
192.168.1.180
Description
The remote host seems to be a Primary Domain Controller or a Backup
Domain Controller.
This can be verified by the value of the registry key 'ProductType'
under 'HKLM\SYSTEM\CurrentControlSet\Control\ProductOptions'.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 42107
MS09-051: Vulnerabilities in Windows Media Runtime Could Allow Remote Code Execution (975682)
Synopsis
Arbitrary code can be executed on the remote host through opening a
Windows Media Format file.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\wmspdmod.dll has not been patched
Remote version : 11.0.6001.7000
Should be : 11.0.6001.7005
Description
The remote Windows host contains a version of the Windows Media
Runtime that is affected by multiple vulnerabilities :
- The ASF parser incorrectly parses files which make use
of the Window Media Speech codec. A remote attacker can
exploit this by tricking a user into opening a specially
crafted ASF file, which can lead to arbitrary code
execution. (CVE-2009-0555)
- The Audio Compression Manager does not properly initialize
certain functions in compressed audio files. A remote
attacker can exploit this by tricking a user into opening
a specially crafted media file, which can lead to
arbitrary code execution. (CVE-2009-2525)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/MS09-051.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
Other references
OSVDB:58844
OSVDB:58845
CWE:94
MSFT:MS09-051
Patch publication date: 2009/10/13
Plugin publication date: 2009/10/13
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact
Port cifs (445/tcp)
Plugin ID: 49958
MS10-081: Vulnerability in Windows Common Control Library Could Allow Remote Code Execution (2296011)
Synopsis
A library on the remote Windows host has a buffer overflow
vulnerability.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Comctl32.dll has not been patched
Remote version : 5.82.6001.18000
Should be : 5.82.6001.18523
Description
The remote host has a heap buffer overflow vulnerability in the
Windows common control library. This vulnerability can be exploited
when a user visits a specially crafted web page while using a third-
party scalable vector graphics (SVG) viewer.
A remote attacker could exploit this by tricking a user into visiting
a maliciously crafted web page.
Solution
Microsoft has released a set of patches for Windows 2003, XP, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/MS10-081.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.2(CVSS2#E:U/RL:OF/RC:UC)
CVE
CVE-2010-2746
Bugtraq ID
43717
Other references
OSVDB:68549
EDB-ID:15963
MSFT:MS10-081
Patch publication date: 2010/10/12
Plugin publication date: 2010/10/13
Plugin last modification date: 2011/03/22
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 39350
MS KB969898: Cumulative Security Update of ActiveX Kill Bits
Synopsis
The remote Windows host is missing a security update containing
ActiveX kill bits.
List of Hosts Plugin Output
192.168.1.180
The kill-bit has not been set for the following control :
{648A5600-2C6E-101B-82B6-000000000014}
Note that Nessus did not check whether there were other kill-bits
that have not been set because 'Thorough Tests' was not enabled
when this scan was run.
Description
The remote host is missing a list of kill bits for ActiveX controls
that are known to contain vulnerabilities.
If these ActiveX controls are ever installed on the remote host,
either now or in the future, they would expose it to various security
issues.
Solution
Microsoft has released an advisory about this :
http://www.microsoft.com/technet/security/advisory/969898.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:52830
OSVDB:54968
CWE:94
Plugin last modification date: 2011/03/16
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 35823
MS09-007: Vulnerability in SChannel Could Allow Spoofing (960225)
Synopsis
It may be possible to spoof user identities.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Schannel.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18175
Description
The Secure Channel (SChannel) authentication component included in the
remote version of Windows does not sufficiently validate certain
Transport Layer Security (TLS) handshake messages to ensure that a
client does in fact have access to the private key linked to a
certificate used for authentication. An attacker who has access to
the public key component of a user's certificate may be able to
leverage this issue to authenticate as that user against services such
as web servers that use certificate-based authentication or to
impersonate that user.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-007.mspx
Risk Factor
Medium/ CVSS Base Score: 6.8
(CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:P)
CVSS Temporal Score: 5.0(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2009-0085
Bugtraq ID
34015
Other references
OSVDB:52521
CWE:287
MSFT:MS09-007
Plugin last modification date: 2011/03/14
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 33877
MS08-048: Security Update for Outlook Express and Windows Mail (951066)
Synopsis
An information disclosure vulnerability is present on the remote host
due to an issue in Outlook Express / Microsoft Mail
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Inetcomm.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18049
Description
The remote host is running a version of Microsoft Outlook Express
which contains a flaw which might be used to cause an information
disclosure.
To exploit this flaw, an attacker would need to send a malformed email
to a victim on the remote host and have him open it.
Solution
Microsoft has released a set of patches for Outlook Express and
Windows Mail :
http://www.microsoft.com/technet/security/bulletin/ms08-048.mspx
Risk Factor
Medium/ CVSS Base Score: 5.4
(CVSS2#AV:N/AC:H/Au:N/C:C/I:N/A:N)
CVSS Temporal Score: 4.5(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2008-1448
Bugtraq ID
30585
Other references
OSVDB:47413
CWE:264
MSFT:MS08-048
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 11457
Microsoft Windows SMB Registry : Winlogon Cached Password Weakness
Synopsis
User credentials are stored in memory.
List of Hosts
192.168.1.180
Description
The registry key
HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\CachedLogonsCount
is non-null. It means that the remote host locally caches the passwords
of the users when they log in, in order to continue to allow the users
to log in in the case of the failure of the PDC.
Solution
use regedt32 and set the value of this key to 0
Risk Factor
Low/ CVSS Base Score: 2.6
(CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 44423
MS10-013: Vulnerability in Microsoft DirectShow Could Allow Remote Code Execution (977935)
Synopsis
It is possible to execute arbitrary code on the remote Windows host
using DirectShow.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\Quartz.dll has not been patched
Remote version : 6.6.6001.18000
Should be : 6.6.6001.18389
Description
The version of Microsoft DirectShow installed on the remote host is
affected by a heap buffer overflow that can be triggered when parsing
AVI media files.
If an attacker can trick a user on the affected host into opening a
specially crafted AVI file, he may be able to leverage this issue to
execute arbitrary code subject to the user's privileges.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-013.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2010-0250
Bugtraq ID
38112
Other references
OSVDB:62257
MSFT:MS10-013
CWE:119
Patch publication date: 2010/02/09
Plugin publication date: 2010/02/09
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 48288
MS10-051: Vulnerability in Microsoft XML Core Services Could Allow Remote Code Execution (2079403)
Synopsis
Arbitrary code can be executed on the remote host through its
Microsoft XML Core Services component.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Msxml3.dll has not been patched
Remote version : 8.100.1043.0
Should be : 8.100.4002.0
Description
The version of Microsoft XML Core Services (MSXML) 3.0 on the remote
Windows host is affected by a memory corruption vulnerability that can
be triggered when processing certain HTTP responses.
If an attacker can trick a user on the affected system into visiting a
malicious web site using Internet Explorer, he may be able to leverage
this issue to execute arbitrary code subject to the user's
privileges.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-051.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.3(CVSS2#E:POC/RL:OF/RC:C)
CVE
CVE-2010-2561
Bugtraq ID
42300
Other references
OSVDB:66973
MSFT:MS10-051
Patch publication date: 2010/08/10
Plugin publication date: 2010/08/11
Plugin last modification date: 2011/04/01
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 52585
MS11-017: Vulnerabilities in Remote Desktop Connection Could Allow Remote Code Execution (2508062)
Synopsis
It is possible to execute arbitrary code on the remote host through
the Remote Desktop client.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mstscax.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18564
Description
The remote host contains a version of the Remote Desktop client that
incorrectly restricts the path used for loading external libraries.
If an attacker can trick a user on the affected system into opening a
specially crafted .rdp file located in the same network directory as
a specially crafted dynamic link library (DLL) file, he may be able
to leverage this issue to execute arbitrary code subject to the user's
privileges.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
7, 2008, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms11-017.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVE
CVE-2011-0029
Bugtraq ID
46678
Other references
OSVDB:71014
MSFT:MS11-017
Patch publication date: 2011/03/08
Plugin publication date: 2011/03/08
Plugin last modification date: 2011/03/09
Port cifs (445/tcp)
Plugin ID: 44424
MS10-014: Vulnerability in Kerberos Could Allow Denial of Service (977290)
Synopsis
It is possible to crash the remote service.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Kdcsvc.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18374
Description
The remote host contains a version of the Kerberos server that
contains a security flaw that may allow an attacker to crash the
remote service via a NULL pointer dereference.
An attacker would need valid credentials to exploit this
vulnerability.
Solution
Microsoft has released a set of patches for Windows 2000, 2003 and
2008:
http://www.microsoft.com/technet/security/bulletin/ms10-014.mspx
Risk Factor
Medium/ CVSS Base Score: 4.0
(CVSS2#AV:N/AC:L/Au:S/C:N/I:N/A:P)
CVSS Temporal Score: 3.0(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2010-0035
Bugtraq ID
38110
Other references
OSVDB:62258
MSFT:MS10-014
Patch publication date: 2010/02/09
Plugin publication date: 2010/02/09
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port (0/tcp)
Plugin ID: 10916
Microsoft Windows - Local Users Information : Passwords never expire
Synopsis
At least one local user has a password that never expires.
List of Hosts Plugin Output
192.168.1.180
The following local users have passwords that never expire :
- Guest
- WIN-8BPIQBRO0CX$
- EXCHANGE$
Note that, in addition to the Administrator and Guest accounts, Nessus
has only checked for local users with UIDs between 1000 and 1200.
To use a different range, edit the scan policy and change the 'Start
UID' and/or 'End UID' preferences for this plugin, then re-run the
scan.
Description
Using the supplied credentials, it is possible to list local users
whose passwords never expire.
Solution
Allow / require users to change their passwords regularly.
Risk Factor
None
Other references
OSVDB:755
Plugin publication date: 2002/03/17
Plugin last modification date: 2011/03/21
Port (0/tcp)
Plugin ID: 44871
WMI Server Feature Enumeration
Synopsis
It is possible to enumerate Windows server features using WMI.
List of Hosts Plugin Output
192.168.1.180
Nessus enumerated the following server features :
- Active Directory Domain Controller
- Active Directory Domain Controller Tools
- Active Directory Domain Services
- Active Directory Domain Services Tools
- DNS Server
- DNS Server Tools
- Group Policy Management
- Remote Server Administration Tools
- Role Administration Tools
Description
Nessus was able to enumerate the server features of the remote host by
querying the 'Win32_ServerFeature' class of the '\Root\cimv2' WMI
namespace.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port cifs (445/tcp)
Plugin ID: 31794
MS08-021: Vulnerabilities in GDI Could Allow Remote Code Execution (948590)
Synopsis
Arbitrary code can be executed on the remote host by sending a malformed file
to a victim.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\gdi32.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18023
Description
The remote host contains a version of Microsoft Windows is missing a critical
security update which fixes several vulnerabilities in the Graphic Rendering
Engine, and in the way Windows handles Metafiles.
An attacker may exploit these flaws to execute arbitrary code on the remote
host. To exploit this flaw, an attacker would need to send a specially
crafted image to a user on the remote host, or lure him into visiting a rogue
website containing such a file.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003 and Vista :
http://www.microsoft.com/technet/security/bulletin/ms08-021.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:44213
OSVDB:44214
OSVDB:44215
CWE:119
MSFT:MS08-021
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 42115
MS09-059: Vulnerability in Local Security Authority Subsystem Service Could Allow Denial of Service (975467)
Synopsis
The remote Windows host is prone to a denial of service attack.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Msv1_0.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18330
Description
The version of LSASS running on the remote host has an integer overflow
vulnerability. A remote attacker could exploit this to cause a denial of
service.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 and 7 :
http://www.microsoft.com/technet/security/Bulletin/MS09-059.mspx
Risk Factor
High/ CVSS Base Score: 7.8
(CVSS2#AV:N/AC:L/Au:N/C:N/I:N/A:C)
CVSS Temporal Score: 6.4(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2009-2524
Bugtraq ID
36593
Other references
OSVDB:58862
CWE:189
MSFT:MS09-059
Patch publication date: 2009/10/13
Plugin publication date: 2009/10/13
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 48296
MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799)
Synopsis
The remote Windows host has multiple privilege escalation
vulnerabilities.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Rtutils.dll has not been patched
Remote version : 6.0.6000.16386
Should be : 6.0.6001.18495
Description
The version of Tracing Feature for Services on the remote host has the
following vulnerabilities :
- Windows places incorrect ACLs on registry keys, which
code allow an attacker to execute code with elevated
privileges. (CVE-2010-2554)
- Memory is allocated in an unspecified, unsafe manner
when processing specially crafted long strings. An
attacker could exploit this to execute code with elevated
privileges. (CVE-2010-2555)
Solution
Microsoft has released a set of patches for Windows Vista, 2008, 7,
and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-059.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.0(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:66977
OSVDB:66978
MSFT:MS10-059
Patch publication date: 2010/08/10
Plugin publication date: 2010/08/11
Plugin last modification date: 2011/04/01
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 34476
MS08-067: Microsoft Windows Server Service Crafted RPC Request Handling Unspecified Remote Code Execution (958644)
Synopsis
Arbitrary code can be executed on the remote host due to a flaw in the
'server' service.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Netapi32.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18157
Description
The remote host is vulnerable to a buffer overrun in the 'Server' service
which may allow an attacker to execute arbitrary code on the remote host
with the 'System' privileges.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003, Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms08-067.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 8.7(CVSS2#E:H/RL:OF/RC:C)
CVE
CVE-2008-4250
Bugtraq ID
31874
Other references
OSVDB:49243
CWE:94
MSFT:MS08-067
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact, Metasploit (Microsoft Server Service Relative Path Stack Corruption)
Port cifs (445/tcp)
Plugin ID: 44401
Microsoft Windows SMB Service Config Enumeration
Synopsis
It is possible to enumerate configuration parameters of remote
services.
List of Hosts Plugin Output
192.168.1.180
The following services are set to start automatically :
AeLookupSvc startup parameters :
Display name : Application Experience
Service name : AeLookupSvc
Log on as : localSystem
Executable path : C:\Windows\system32\svchost.exe -k netsvcs
BFE startup parameters :
Display name : Base Filtering Engine
Service name : BFE
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalServiceNoNetwork
Dependencies : RpcSs/
BITS startup parameters :
Display name : Background Intelligent Transfer Service
Service name : BITS
Log on as : LocalSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
Dependencies : RpcSs/EventSystem/
CryptSvc startup parameters :
Display name : Cryptographic Services
Service name : CryptSvc
Log on as : NT Authority\NetworkService
Executable path : C:\Windows\system32\svchost.exe -k NetworkService
Dependencies : RpcSs/
DFSR startup parameters :
Display name : DFS Replication
Service name : DFSR
Log on as : LocalSystem
Executable path : C:\Windows\system32\DFSRs.exe
Dependencies : RpcSs/EventSystem/
DNS startup parameters :
Display name : DNS Server
Service name : DNS
Log on as : LocalSystem
Executable path : C:\Windows\system32\dns.exe
Dependencies : Tcpip/Afd/RpcSs/NTDS/
Dfs startup parameters :
Display name : DFS Namespace
Service name : Dfs
Log on as : LocalSystem
Executable path : C:\Windows\system32\dfssvc.exe
Dependencies : LanmanWorkstation/LanmanServer/DfsDriver/Mup/SamSS/RemoteRegistry/
Dhcp startup parameters :
Display name : DHCP Client
Service name : Dhcp
Log on as : NT Authority\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestricted
Dependencies : NSI/Tdx/Afd/
Dnscache startup parameters :
Display name : DNS Client
Service name : Dnscache
Log on as : NT AUTHORITY\NetworkService
Executable path : C:\Windows\system32\svchost.exe -k NetworkService
Dependencies : Tdx/
EventLog startup parameters :
Display name : Windows Event Log
Service name : EventLog
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted
EventSystem startup parameters :
Display name : COM+ Event System
Service name : EventSystem
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalService
Dependencies : rpcss/
IKEEXT startup parameters :
Display name : IKE and AuthIP IPsec Keying Modules
Service name : IKEEXT
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k netsvcs
Dependencies : BFE/
IsmServ startup parameters :
Display name : Intersite Messaging
Service name : IsmServ
Log on as : LocalSystem
Executable path : C:\Windows\System32\ismserv.exe
Dependencies : SamSS/NTDS/
KtmRm startup parameters :
Display name : KtmRm for Distributed Transaction Coordinator
Service name : KtmRm
Log on as : NT AUTHORITY\NetworkService
Executable path : C:\Windows\System32\svchost.exe -k NetworkService
Dependencies : RPCSS/SamSS/
LanmanServer startup parameters :
Display name : Server
Service name : LanmanServer
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k netsvcs
Dependencies : SamSS/Srv/
LanmanWorkstation startup parameters :
Display name : Workstation
Service name : LanmanWorkstation
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\System32\svchost.exe -k LocalService
Dependencies : Bowser/MRxSmb10/MRxSmb20/NSI/
MpsSvc startup parameters :
Display name : Windows Firewall
Service name : MpsSvc
Log on as : NT Authority\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalServiceNoNetwork
Dependencies : mpsdrv/bfe/
NTDS startup parameters :
Display name : Active Directory Domain Services
Service name : NTDS
Log on as : LocalSystem
Executable path : C:\Windows\System32\lsass.exe
Netlogon startup parameters :
Display name : Netlogon
Service name : Netlogon
Log on as : LocalSystem
Executable path : C:\Windows\system32\lsass.exe
Dependencies : LanmanWorkstation/LanmanServer/
NlaSvc startup parameters :
Display name : Network Location Awareness
Service name : NlaSvc
Log on as : NT AUTHORITY\NetworkService
Executable path : C:\Windows\System32\svchost.exe -k NetworkService
Dependencies : NSI/RpcSs/TcpIp/
NtFrs startup parameters :
Display name : File Replication Service
Service name : NtFrs
Log on as : LocalSystem
Executable path : C:\Windows\system32\ntfrs.exe
Dependencies : RpcSs/EventSystem/NTDS/
PlugPlay startup parameters :
Display name : Plug and Play
Service name : PlugPlay
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k DcomLaunch
PolicyAgent startup parameters :
Display name : IPsec Policy Agent
Service name : PolicyAgent
Log on as : NT Authority\NetworkService
Executable path : C:\Windows\system32\svchost.exe -k NetworkServiceNetworkRestricted
Dependencies : Tcpip/bfe/
ProfSvc startup parameters :
Display name : User Profile Service
Service name : ProfSvc
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k netsvcs
Dependencies : RpcSs/
RemoteRegistry startup parameters :
Display name : Remote Registry
Service name : RemoteRegistry
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k regsvc
Dependencies : RPCSS/
SENS startup parameters :
Display name : System Event Notification Service
Service name : SENS
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k netsvcs
Dependencies : EventSystem/
SamSs startup parameters :
Display name : Security Accounts Manager
Service name : SamSs
Log on as : LocalSystem
Executable path : C:\Windows\system32\lsass.exe
Dependencies : RPCSS/
ShellHWDetection startup parameters :
Display name : Shell Hardware Detection
Service name : ShellHWDetection
Log on as : LocalSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
Dependencies : RpcSs/
Splunkd startup parameters :
Display name : Splunkd
Service name : Splunkd
Log on as : LocalSystem
Executable path : C:\Program Files\Splunk\bin\splunkd.exe service
Splunkweb startup parameters :
Display name : Splunkweb
Service name : Splunkweb
Log on as : LocalSystem
Executable path : C:\Program Files\Splunk\bin\PythonService.exe
Spooler startup parameters :
Display name : Print Spooler
Service name : Spooler
Log on as : LocalSystem
Executable path : C:\Windows\System32\spoolsv.exe
Dependencies : RPCSS/http/
TBS startup parameters :
Display name : TPM Base Services
Service name : TBS
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\System32\svchost.exe -k LocalService
TermService startup parameters :
Display name : Terminal Services
Service name : TermService
Log on as : NT Authority\NetworkService
Executable path : C:\Windows\System32\svchost.exe -k NetworkService
Dependencies : RPCSS/TermDD/
UxSms startup parameters :
Display name : Desktop Window Manager Session Manager
Service name : UxSms
Log on as : localSystem
Executable path : C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted
W32Time startup parameters :
Display name : Windows Time
Service name : W32Time
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalService
WerSvc startup parameters :
Display name : Windows Error Reporting Service
Service name : WerSvc
Log on as : localSystem
Executable path : C:\Windows\System32\svchost.exe -k WerSvcGroup
WinRM startup parameters :
Display name : Windows Remote Management (WS-Management)
Service name : WinRM
Log on as : NT AUTHORITY\NetworkService
Executable path : C:\Windows\System32\svchost.exe -k NetworkService
Dependencies : RPCSS/HTTP/
Winmgmt startup parameters :
Display name : Windows Management Instrumentation
Service name : Winmgmt
Log on as : localSystem
Executable path : C:\Windows\system32\svchost.exe -k netsvcs
Dependencies : RPCSS/
iphlpsvc startup parameters :
Display name : IP Helper
Service name : iphlpsvc
Log on as : LocalSystem
Executable path : C:\Windows\System32\svchost.exe -k NetSvcs
Dependencies : RpcSS/Tdx/winmgmt/tcpip/nsi/
kdc startup parameters :
Display name : Kerberos Key Distribution Center
Service name : kdc
Log on as : LocalSystem
Executable path : C:\Windows\System32\lsass.exe
Dependencies : RpcSs/Afd/NTDS/
lmhosts startup parameters :
Display name : TCP/IP NetBIOS Helper
Service name : lmhosts
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestricted
Dependencies : NetBT/Afd/
netprofm startup parameters :
Display name : Network List Service
Service name : netprofm
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\System32\svchost.exe -k LocalService
Dependencies : RpcSs/nlasvc/
nsi startup parameters :
Display name : Network Store Interface Service
Service name : nsi
Log on as : NT Authority\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalService
Dependencies : nsiproxy/
seclogon startup parameters :
Display name : Secondary Logon
Service name : seclogon
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k netsvcs
slsvc startup parameters :
Display name : Software Licensing
Service name : slsvc
Log on as : NT AUTHORITY\NetworkService
Executable path : C:\Windows\system32\SLsvc.exe
Dependencies : RpcSs/
wuauserv startup parameters :
Display name : Windows Update
Service name : wuauserv
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k netsvcs
Dependencies : rpcss/
The following services must be started manually :
ALG startup parameters :
Display name : Application Layer Gateway Service
Service name : ALG
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\System32\alg.exe
AppMgmt startup parameters :
Display name : Application Management
Service name : AppMgmt
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k netsvcs
Appinfo startup parameters :
Display name : Application Information
Service name : Appinfo
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k netsvcs
Dependencies : RpcSs/ProfSvc/
AudioEndpointBuilder startup parameters :
Display name : Windows Audio Endpoint Builder
Service name : AudioEndpointBuilder
Log on as : LocalSystem
Executable path : C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted
Dependencies : PlugPlay/
Audiosrv startup parameters :
Display name : Windows Audio
Service name : Audiosrv
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted
Dependencies : AudioEndpointBuilder/RpcSs/MMCSS/
COMSysApp startup parameters :
Display name : COM+ System Application
Service name : COMSysApp
Log on as : LocalSystem
Executable path : C:\Windows\system32\dllhost.exe /Processid:{02D4B3F1-FD88-11D1-960D-00805FC79235}
Dependencies : RpcSs/EventSystem/SENS/
EapHost startup parameters :
Display name : Extensible Authentication Protocol
Service name : EapHost
Log on as : localSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
Dependencies : RPCSS/KeyIso/
FCRegSvc startup parameters :
Display name : Microsoft Fibre Channel Platform Registration Service
Service name : FCRegSvc
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestricted
FDResPub startup parameters :
Display name : Function Discovery Resource Publication
Service name : FDResPub
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalService
Dependencies : RpcSs/http/
KeyIso startup parameters :
Display name : CNG Key Isolation
Service name : KeyIso
Log on as : LocalSystem
Executable path : C:\Windows\system32\lsass.exe
Dependencies : RpcSs/
MMCSS startup parameters :
Display name : Multimedia Class Scheduler
Service name : MMCSS
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k netsvcs
MSiSCSI startup parameters :
Display name : Microsoft iSCSI Initiator Service
Service name : MSiSCSI
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k netsvcs
Netman startup parameters :
Display name : Network Connections
Service name : Netman
Log on as : LocalSystem
Executable path : C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted
Dependencies : RpcSs/nsi/
ProtectedStorage startup parameters :
Display name : Protected Storage
Service name : ProtectedStorage
Log on as : LocalSystem
Executable path : C:\Windows\system32\lsass.exe
Dependencies : RpcSs/
RSoPProv startup parameters :
Display name : Resultant Set of Policy Provider
Service name : RSoPProv
Log on as : LocalSystem
Executable path : C:\Windows\system32\RSoPProv.exe
Dependencies : RPCSS/
RasAuto startup parameters :
Display name : Remote Access Auto Connection Manager
Service name : RasAuto
Log on as : localSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
Dependencies : RasMan/TapiSrv/
RasMan startup parameters :
Display name : Remote Access Connection Manager
Service name : RasMan
Log on as : localSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
Dependencies : Tapisrv/SstpSvc/
RpcLocator startup parameters :
Display name : Remote Procedure Call (RPC) Locator
Service name : RpcLocator
Log on as : NT AUTHORITY\NetworkService
Executable path : C:\Windows\system32\locator.exe
SLUINotify startup parameters :
Display name : SL UI Notification Service
Service name : SLUINotify
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalService
Dependencies : SLSvc/netprofm/EventSystem/
SNMPTRAP startup parameters :
Display name : SNMP Trap
Service name : SNMPTRAP
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\System32\snmptrap.exe
SessionEnv startup parameters :
Display name : Terminal Services Configuration
Service name : SessionEnv
Log on as : localSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
Dependencies : RPCSS/LanmanWorkstation/
SstpSvc startup parameters :
Display name : Secure Socket Tunneling Protocol Service
Service name : SstpSvc
Log on as : NT Authority\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalService
THREADORDER startup parameters :
Display name : Thread Ordering Server
Service name : THREADORDER
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalService
TapiSrv startup parameters :
Display name : Telephony
Service name : TapiSrv
Log on as : NT AUTHORITY\NetworkService
Executable path : C:\Windows\System32\svchost.exe -k tapisrv
Dependencies : PlugPlay/RpcSs/
TrkWks startup parameters :
Display name : Distributed Link Tracking Client
Service name : TrkWks
Log on as : LocalSystem
Executable path : C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted
Dependencies : RpcSs/
UI0Detect startup parameters :
Display name : Interactive Services Detection
Service name : UI0Detect
Log on as : LocalSystem
Executable path : C:\Windows\system32\UI0Detect.exe
UmRdpService startup parameters :
Display name : Terminal Services UserMode Port Redirector
Service name : UmRdpService
Log on as : localSystem
Executable path : C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted
Dependencies : TermService/
VSS startup parameters :
Display name : Volume Shadow Copy
Service name : VSS
Log on as : LocalSystem
Executable path : C:\Windows\system32\vssvc.exe
Dependencies : RPCSS/
WPDBusEnum startup parameters :
Display name : Portable Device Enumerator Service
Service name : WPDBusEnum
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestricted
Dependencies : RpcSs/
WcsPlugInService startup parameters :
Display name : Windows Color System
Service name : WcsPlugInService
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k wcssvc
Dependencies : RpcSs/
Wecsvc startup parameters :
Display name : Windows Event Collector
Service name : Wecsvc
Log on as : NT AUTHORITY\NetworkService
Executable path : C:\Windows\system32\svchost.exe -k NetworkService
Dependencies : HTTP/Eventlog/mpssvc/
WinHttpAutoProxySvc startup parameters :
Display name : WinHTTP Web Proxy Auto-Discovery Service
Service name : WinHttpAutoProxySvc
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalService
Dependencies : Dhcp/
clr_optimization_v2.0.50727_32 startup parameters :
Display name : Microsoft .NET Framework NGEN v2.0.50727_X86
Service name : clr_optimization_v2.0.50727_32
Log on as : LocalSystem
Executable path : C:\Windows\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe
dot3svc startup parameters :
Display name : Wired AutoConfig
Service name : dot3svc
Log on as : localSystem
Executable path : C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestricted
Dependencies : RpcSs/Ndisuio/Eaphost/
fdPHost startup parameters :
Display name : Function Discovery Provider Host
Service name : fdPHost
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalService
Dependencies : RpcSs/http/
hidserv startup parameters :
Display name : Human Interface Device Access
Service name : hidserv
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestricted
hkmsvc startup parameters :
Display name : Health Key and Certificate Management
Service name : hkmsvc
Log on as : localSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
Dependencies : RpcSs/
lltdsvc startup parameters :
Display name : Link-Layer Topology Discovery Mapper
Service name : lltdsvc
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\System32\svchost.exe -k LocalService
Dependencies : rpcss/lltdio/
msiserver startup parameters :
Display name : Windows Installer
Service name : msiserver
Log on as : LocalSystem
Executable path : C:\Windows\system32\msiexec /V
Dependencies : rpcss/
napagent startup parameters :
Display name : Network Access Protection Agent
Service name : napagent
Log on as : NT AUTHORITY\NetworkService
Executable path : C:\Windows\System32\svchost.exe -k NetworkService
Dependencies : RpcSs/
pla startup parameters :
Display name : Performance Logs & Alerts
Service name : pla
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\System32\svchost.exe -k LocalServiceNoNetwork
Dependencies : RPCSS/
sacsvr startup parameters :
Display name : Special Administration Console Helper
Service name : sacsvr
Log on as : LocalSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
swprv startup parameters :
Display name : Microsoft Software Shadow Copy Provider
Service name : swprv
Log on as : LocalSystem
Executable path : C:\Windows\System32\svchost.exe -k swprv
Dependencies : RPCSS/
vds startup parameters :
Display name : Virtual Disk
Service name : vds
Log on as : LocalSystem
Executable path : C:\Windows\System32\vds.exe
Dependencies : RpcSs/PlugPlay/
wercplsupport startup parameters :
Display name : Problem Reports and Solutions Control Panel Support
Service name : wercplsupport
Log on as : localSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
wmiApSrv startup parameters :
Display name : WMI Performance Adapter
Service name : wmiApSrv
Log on as : localSystem
Executable path : C:\Windows\system32\wbem\WmiApSrv.exe
wudfsvc startup parameters :
Display name : Windows Driver Foundation - User-mode Driver Framework
Service name : wudfsvc
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestricted
Dependencies : PlugPlay/
The following services are disabled :
Browser startup parameters :
Display name : Computer Browser
Service name : Browser
Log on as : LocalSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
Dependencies : LanmanWorkstation/LanmanServer/
CscService startup parameters :
Display name : Offline Files
Service name : CscService
Log on as : LocalSystem
Executable path : C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted
Dependencies : RpcSs/
IPBusEnum startup parameters :
Display name : PnP-X IP Bus Enumerator
Service name : IPBusEnum
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestricted
Dependencies : RpcSs/fdPHost/
RemoteAccess startup parameters :
Display name : Routing and Remote Access
Service name : RemoteAccess
Log on as : localSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
Dependencies : RpcSS/Bfe/RasMan/Http/+NetBIOSGroup/
SSDPSRV startup parameters :
Display name : SSDP Discovery
Service name : SSDPSRV
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalService
Dependencies : HTTP/
SharedAccess startup parameters :
Display name : Internet Connection Sharing (ICS)
Service name : SharedAccess
Log on as : LocalSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
Dependencies : Netman/WinMgmt/RasMan/BFE/
SysMain startup parameters :
Display name : Superfetch
Service name : SysMain
Log on as : LocalSystem
Executable path : C:\Windows\system32\svchost.exe -k LocalSystemNetworkRestricted
Dependencies : rpcss/fileinfo/
Themes startup parameters :
Display name : Themes
Service name : Themes
Log on as : LocalSystem
Executable path : C:\Windows\System32\svchost.exe -k netsvcs
upnphost startup parameters :
Display name : UPnP Device Host
Service name : upnphost
Log on as : NT AUTHORITY\LocalService
Executable path : C:\Windows\system32\svchost.exe -k LocalService
Dependencies : SSDPSRV/HTTP/
Description
This plugin implements the QueryServiceConfig() calls to obtain,
using the SMB protocol, the launch parameters of each active service
on the remote host (executable path, log on type, etc).
Solution
Ensure that each service is configured properly.
Risk Factor
None
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 45506
MS10-019: Vulnerabilities in Windows Could Allow Remote Code Execution (981210)
Synopsis
The remote Windows host has multiple code execution vulnerabilities.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Wintrust.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18387
Description
The version of Windows running on the remote host has vulnerabilities
in the Windows Authenticode Signature mechanism. Modifying an
existing signed executable or cabinet file can result in arbitrary
code execution.
A remote attacker could exploit this by tricking a user into executing
or opening a maliciously crafted file, resulting in arbitrary code
execution.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-019.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:63745
OSVDB:63746
MSFT:MS10-019
Patch publication date: 2010/04/13
Plugin publication date: 2010/04/13
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 46841
MS10-034: Cumulative Security Update of ActiveX Kill Bits (980195)
Synopsis
The remote Windows host is missing an update that disables selected
ActiveX controls.
List of Hosts Plugin Output
192.168.1.180
The kill bit has not been set for the following control :
{14FD1463-1F3F-4357-9C03-2080B442F503}
Note that Nessus did not check whether there were other kill bits
that have not been set because "Thorough Tests" was not enabled
when this scan was run.
Description
The Microsoft Data Analyzer ActiveX control has a remote code
execution vulnerability. The system may also have one or more
vulnerable third-party ActiveX controls installed.
A remote attacker could exploit these issues by tricking a user into
requesting a maliciously crafted web page, resulting in arbitrary
code execution.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-034.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:62246
OSVDB:65218
OSVDB:65382
OSVDB:65468
OSVDB:65480
OSVDB:65481
CWE:94
MSFT:MS10-034
Patch publication date: 2010/06/08
Plugin publication date: 2010/06/09
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port (0/tcp)
Plugin ID: 48337
Windows ComputerSystemProduct Enumeration (WMI)
Synopsis
It is possible to obtain product information from the remote host
using WMI.
List of Hosts Plugin Output
192.168.1.180
+ Computer System Product
- IdentifyingNumber : VMware-56 4d b0 ad 12 c6 9b f3-49 9a 05 61 c8 9d a1 c6
- Description : Computer System Product
- Vendor : VMware, Inc.
- Name : VMware Virtual Platform
- UUID : ADB04D56-C612-F39B-499A-0561C89DA1C6
- Version : None
Description
By querying the WMI class 'Win32_ComputerSystemProduct', it is
possible to extract product information about the computer system such
as UUID, IdentifyingNumber, vendor, etc.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port cifs (445/tcp)
Plugin ID: 40407
MS09-034: Cumulative Security Update for Internet Explorer (972260)
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18294
Description
The remote host is missing IE Security Update 972260.
The remote version of IE is affected by several vulnerabilities that
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-034.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:56693
OSVDB:56694
OSVDB:56695
CWE:94
MSFT:MS09-034
Patch publication date: 2009/07/28
Plugin publication date: 2009/07/28
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 46842
MS10-035: Cumulative Security Update for Internet Explorer (982381)
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18470
Description
The remote host is missing IE Security Update 982381.
The remote version of IE is affected by several vulnerabilities that
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-035.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
Other references
OSVDB:62156
OSVDB:65211
OSVDB:65212
OSVDB:65213
OSVDB:65214
OSVDB:65215
CWE:264
MSFT:MS10-035
Patch publication date: 2010/06/08
Plugin publication date: 2010/06/09
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS)
Port cifs (445/tcp)
Plugin ID: 10398
Microsoft Windows SMB LsaQueryInformationPolicy Function NULL Session Domain SID Enumeration
Synopsis
It is possible to obtain the domain SID.
List of Hosts Plugin Output
192.168.1.180
The remote domain SID value is :
1-5-21-3840563293-1772093868-3818923108
Description
By emulating the call to LsaQueryInformationPolicy() it was
possible to obtain the domain SID (Security Identifier).
The domain SID can then be used to get the list of users
of the domain
Solution
n/a
Risk Factor
None
CVE
CVE-2000-1200
Bugtraq ID
959
Other references
OSVDB:715
Plugin publication date: 2000/05/09
Plugin last modification date: 2011/03/07
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 10400
Microsoft Windows SMB Registry Remotely Accessible
Synopsis
Access the remote Windows Registry.
List of Hosts
192.168.1.180
Description
It was possible to access the remote Windows Registry using the login
/ password combination used for the Windows local checks (SMB tests).
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 48761
MS KB982316: Elevation of Privilege Using Windows Service Isolation Bypass
Synopsis
The remote Windows host has a privilege escalation vulnerability.
List of Hosts Plugin Output
192.168.1.180
The Network Service group has Full Control rights to :
HKLM\Software\Microsoft\Windows\CurrentVersion\Telephony
Description
Windows Service Isolation can be bypassed on the remote host,
resulting in the elevation of privileges.
A local attacker could exploit this by leveraging the TAPI service to
execute code as SYSTEM.
A similar problem affects other Windows services that run as the
NetworkService user (e.g. IIS, SQL Server), though Nessus has
not checked for those issues.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/advisory/2264072.mspx
Although these patches mitigate this vulnerability, users should
be aware this is considered a non-security update by Microsoft.
Refer to the Microsoft advisory for more information.
See also
http://argeniss.com/research/TokenKidnappingRevengePaper.pdf
http://www.microsoft.com/technet/security/advisory/2264072.mspx
Risk Factor
Medium/ CVSS Base Score: 6.8
(CVSS2#AV:L/AC:L/Au:S/C:C/I:C/A:C)
CVSS Temporal Score: 5.6(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2010-1886
Bugtraq ID
42278
Other references
OSVDB:67083
Patch publication date: 2010/08/10
Plugin publication date: 2010/08/26
Plugin last modification date: 2011/03/09
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 33441
MS08-037: Vulnerabilities in DNS Could Allow Spoofing (953230)
Synopsis
The remote host is vulnerable to DNS spoofing attacks.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\dns.exe has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18081
Description
Flaws in the remote DNS library may let an attacker send malicious DNS
responses to DNS requests made by the remote host, thereby spoofing or
redirecting internet traffic from legitimate locations.
Solution
Microsoft has released patches for Windows 2000, XP, and 2003 Server :
http://www.microsoft.com/technet/security/Bulletin/MS08-037.mspx
Risk Factor
Medium/ CVSS Base Score: 5.8
(CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:N)
CVSS Temporal Score: 4.8(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:46777
OSVDB:46778
MSFT:MS08-037
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 46844
MS10-037: Vulnerability in the OpenType Compact Font Format (CFF) Driver Could Allow Elevation of Privilege (980218)
Synopsis
The remote Windows host contains a font driver that is affected by
a privilege escalation vulnerability.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\Atmfd.dll has not been patched
Remote version : 5.1.2.226
Should be : 5.1.2.228
Description
The remote Windows host contains a version of the OpenType Compact
Font Format (CFF) Font Driver that fails to properly validate certain
data passed from user mode to kernel mode.
By viewing content rendered in a specially crafted CFF font, a local
attacker may be able to exploit this vulnerability to execute
arbitrary code in kernel mode and take complete control of the
affected system.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-037.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2010-0819
Bugtraq ID
40572
Other references
OSVDB:65217
MSFT:MS10-037
Patch publication date: 2010/06/08
Plugin publication date: 2010/06/09
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port (0/tcp)
Plugin ID: 38153
Microsoft Windows Summary of Missing Patches
Synopsis
The remote host is missing several Microsoft Security Patches
List of Hosts Plugin Output
192.168.1.180
The patches for the following bulletins are missing on the remote host :
- MS08-021 ( http://www.microsoft.com/technet/security/bulletin/ms08-021.mspx )
- MS08-024 ( http://www.microsoft.com/technet/security/bulletin/ms08-024.mspx )
- MS08-025 ( http://www.microsoft.com/technet/security/bulletin/ms08-025.mspx )
- MS08-031 ( http://www.microsoft.com/technet/security/bulletin/ms08-031.mspx )
- MS08-032 ( http://www.microsoft.com/technet/security/bulletin/ms08-032.mspx )
- MS08-033 ( http://www.microsoft.com/technet/security/bulletin/ms08-033.mspx )
- MS08-035 ( http://www.microsoft.com/technet/security/bulletin/ms08-035.mspx )
- MS08-037 ( http://www.microsoft.com/technet/security/bulletin/ms08-037.mspx )
- MS08-038 ( http://www.microsoft.com/technet/security/bulletin/ms08-038.mspx )
- MS08-045 ( http://www.microsoft.com/technet/security/bulletin/ms08-045.mspx )
- MS08-047 ( http://www.microsoft.com/technet/security/bulletin/ms08-047.mspx )
- MS08-048 ( http://www.microsoft.com/technet/security/bulletin/ms08-048.mspx )
- MS08-049 ( http://www.microsoft.com/technet/security/bulletin/ms08-049.mspx )
- MS08-058 ( http://www.microsoft.com/technet/security/bulletin/ms08-058.mspx )
- MS08-061 ( http://www.microsoft.com/technet/security/bulletin/ms08-061.mspx )
- MS08-063 ( http://www.microsoft.com/technet/security/bulletin/ms08-063.mspx )
- MS08-064 ( http://www.microsoft.com/technet/security/bulletin/ms08-064.mspx )
- MS08-067 ( http://www.microsoft.com/technet/security/bulletin/ms08-067.mspx )
- MS08-068 ( http://www.microsoft.com/technet/security/bulletin/ms08-068.mspx )
- MS08-069 ( http://www.microsoft.com/technet/security/bulletin/ms08-069.mspx )
- MS08-071 ( http://www.microsoft.com/technet/security/bulletin/ms08-071.mspx )
- MS08-073 ( http://www.microsoft.com/technet/security/bulletin/ms08-073.mspx )
- MS08-075 ( http://www.microsoft.com/technet/security/bulletin/ms08-075.mspx )
- MS08-078 ( http://www.microsoft.com/technet/security/bulletin/ms08-078.mspx )
- MS09-002 ( http://www.microsoft.com/technet/security/bulletin/ms09-002.mspx )
- MS09-006 ( http://www.microsoft.com/technet/security/bulletin/ms09-006.mspx )
- MS09-007 ( http://www.microsoft.com/technet/security/bulletin/ms09-007.mspx )
- MS09-008 ( http://www.microsoft.com/technet/security/bulletin/ms09-008.mspx )
- MS09-012 ( http://www.microsoft.com/technet/security/bulletin/ms09-012.mspx )
- MS09-013 ( http://www.microsoft.com/technet/security/bulletin/ms09-013.mspx )
- MS09-014 ( http://www.microsoft.com/technet/security/bulletin/ms09-014.mspx )
- MS09-015 ( http://www.microsoft.com/technet/security/bulletin/ms09-015.mspx )
- MS09-019 ( http://www.microsoft.com/technet/security/bulletin/ms09-019.mspx )
- MS09-022 ( http://www.microsoft.com/technet/security/bulletin/ms09-022.mspx )
- MS09-025 ( http://www.microsoft.com/technet/security/bulletin/ms09-025.mspx )
- MS09-026 ( http://www.microsoft.com/technet/security/bulletin/ms09-026.mspx )
- MS09-029 ( http://www.microsoft.com/technet/security/bulletin/ms09-029.mspx )
- MS09-032 ( http://www.microsoft.com/technet/security/bulletin/ms09-032.mspx )
- MS09-034 ( http://www.microsoft.com/technet/security/bulletin/ms09-034.mspx )
- MS09-037 ( http://www.microsoft.com/technet/security/bulletin/ms09-037.mspx )
- MS09-038 ( http://www.microsoft.com/technet/security/bulletin/ms09-038.mspx )
- MS09-041 ( http://www.microsoft.com/technet/security/bulletin/ms09-041.mspx )
- MS09-044 ( http://www.microsoft.com/technet/security/bulletin/ms09-044.mspx )
- MS09-045 ( http://www.microsoft.com/technet/security/bulletin/ms09-045.mspx )
- MS09-048 ( http://www.microsoft.com/technet/security/bulletin/ms09-048.mspx )
- MS09-050 ( http://www.microsoft.com/technet/security/bulletin/ms09-050.mspx )
- MS09-051 ( http://www.microsoft.com/technet/security/bulletin/ms09-051.mspx )
- MS09-054 ( http://www.microsoft.com/technet/security/bulletin/ms09-054.mspx )
- MS09-055 ( http://www.microsoft.com/technet/security/bulletin/ms09-055.mspx )
- MS09-056 ( http://www.microsoft.com/technet/security/bulletin/ms09-056.mspx )
- MS09-058 ( http://www.microsoft.com/technet/security/bulletin/ms09-058.mspx )
- MS09-059 ( http://www.microsoft.com/technet/security/bulletin/ms09-059.mspx )
- MS09-062 ( http://www.microsoft.com/technet/security/bulletin/ms09-062.mspx )
- MS09-063 ( http://www.microsoft.com/technet/security/bulletin/ms09-063.mspx )
- MS09-065 ( http://www.microsoft.com/technet/security/bulletin/ms09-065.mspx )
- MS09-066 ( http://www.microsoft.com/technet/security/bulletin/ms09-066.mspx )
- MS09-071 ( http://www.microsoft.com/technet/security/bulletin/ms09-071.mspx )
- MS09-072 ( http://www.microsoft.com/technet/security/bulletin/ms09-072.mspx )
- MS10-001 ( http://www.microsoft.com/technet/security/bulletin/ms10-001.mspx )
- MS10-002 ( http://www.microsoft.com/technet/security/bulletin/ms10-002.mspx )
- MS10-006 ( http://www.microsoft.com/technet/security/bulletin/ms10-006.mspx )
- MS10-008 ( http://www.microsoft.com/technet/security/bulletin/ms10-008.mspx )
- MS10-009 ( http://www.microsoft.com/technet/security/bulletin/ms10-009.mspx )
- MS10-012 ( http://www.microsoft.com/technet/security/bulletin/ms10-012.mspx )
- MS10-013 ( http://www.microsoft.com/technet/security/bulletin/ms10-013.mspx )
- MS10-014 ( http://www.microsoft.com/technet/security/bulletin/ms10-014.mspx )
- MS10-015 ( http://www.microsoft.com/technet/security/bulletin/ms10-015.mspx )
- MS10-018 ( http://www.microsoft.com/technet/security/bulletin/ms10-018.mspx )
- MS10-019 ( http://www.microsoft.com/technet/security/bulletin/ms10-019.mspx )
- MS10-020 ( http://www.microsoft.com/technet/security/bulletin/ms10-020.mspx )
- MS10-021 ( http://www.microsoft.com/technet/security/bulletin/ms10-021.mspx )
- MS10-022 ( http://www.microsoft.com/technet/security/bulletin/ms10-022.mspx )
- MS10-029 ( http://www.microsoft.com/technet/security/bulletin/ms10-029.mspx )
- MS10-030 ( http://www.microsoft.com/technet/security/bulletin/ms10-030.mspx )
- MS10-032 ( http://www.microsoft.com/technet/security/bulletin/ms10-032.mspx )
- MS10-033 ( http://www.microsoft.com/technet/security/bulletin/ms10-033.mspx )
- MS10-034 ( http://www.microsoft.com/technet/security/bulletin/ms10-034.mspx )
- MS10-035 ( http://www.microsoft.com/technet/security/bulletin/ms10-035.mspx )
- MS10-037 ( http://www.microsoft.com/technet/security/bulletin/ms10-037.mspx )
- MS10-046 ( http://www.microsoft.com/technet/security/bulletin/ms10-046.mspx )
- MS10-047 ( http://www.microsoft.com/technet/security/bulletin/ms10-047.mspx )
- MS10-048 ( http://www.microsoft.com/technet/security/bulletin/ms10-048.mspx )
- MS10-049 ( http://www.microsoft.com/technet/security/bulletin/ms10-049.mspx )
- MS10-051 ( http://www.microsoft.com/technet/security/bulletin/ms10-051.mspx )
- MS10-053 ( http://www.microsoft.com/technet/security/bulletin/ms10-053.mspx )
- MS10-054 ( http://www.microsoft.com/technet/security/bulletin/ms10-054.mspx )
- MS10-058 ( http://www.microsoft.com/technet/security/bulletin/ms10-058.mspx )
- MS10-059 ( http://www.microsoft.com/technet/security/bulletin/ms10-059.mspx )
- MS10-061 ( http://www.microsoft.com/technet/security/bulletin/ms10-061.mspx )
- MS10-063 ( http://www.microsoft.com/technet/security/bulletin/ms10-063.mspx )
- MS10-068 ( http://www.microsoft.com/technet/security/bulletin/ms10-068.mspx )
- MS10-070 ( http://www.microsoft.com/technet/security/bulletin/ms10-070.mspx )
- MS10-071 ( http://www.microsoft.com/technet/security/bulletin/ms10-071.mspx )
- MS10-073 ( http://www.microsoft.com/technet/security/bulletin/ms10-073.mspx )
- MS10-074 ( http://www.microsoft.com/technet/security/bulletin/ms10-074.mspx )
- MS10-076 ( http://www.microsoft.com/technet/security/bulletin/ms10-076.mspx )
- MS10-081 ( http://www.microsoft.com/technet/security/bulletin/ms10-081.mspx )
- MS10-083 ( http://www.microsoft.com/technet/security/bulletin/ms10-083.mspx )
- MS10-085 ( http://www.microsoft.com/technet/security/bulletin/ms10-085.mspx )
- MS10-090 ( http://www.microsoft.com/technet/security/bulletin/ms10-090.mspx )
- MS10-091 ( http://www.microsoft.com/technet/security/bulletin/ms10-091.mspx )
- MS10-092 ( http://www.microsoft.com/technet/security/bulletin/ms10-092.mspx )
- MS10-096 ( http://www.microsoft.com/technet/security/bulletin/ms10-096.mspx )
- MS10-098 ( http://www.microsoft.com/technet/security/bulletin/ms10-098.mspx )
- MS10-100 ( http://www.microsoft.com/technet/security/bulletin/ms10-100.mspx )
- MS10-101 ( http://www.microsoft.com/technet/security/bulletin/ms10-101.mspx )
- MS11-002 ( http://www.microsoft.com/technet/security/bulletin/ms11-002.mspx )
- MS11-003 ( http://www.microsoft.com/technet/security/bulletin/ms11-003.mspx )
- MS11-006 ( http://www.microsoft.com/technet/security/bulletin/ms11-006.mspx )
- MS11-007 ( http://www.microsoft.com/technet/security/bulletin/ms11-007.mspx )
- MS11-011 ( http://www.microsoft.com/technet/security/bulletin/ms11-011.mspx )
- MS11-012 ( http://www.microsoft.com/technet/security/bulletin/ms11-012.mspx )
- MS11-017 ( http://www.microsoft.com/technet/security/bulletin/ms11-017.mspx )
Description
This plugin summarizes the list of Microsoft Security Patches which
have not been installed on the remote host.
You should review and apply them to be up-to-date.
Solution
Run Windows Update on the remote host, or use a patch management solution
Risk Factor
None
Plugin last modification date: 2011/03/17
Port cifs (445/tcp)
Plugin ID: 33138
MS08-035: Vulnerability in Active Directory Could Allow Denial of Service (953235)
Synopsis
It is possible to crash Active Directory on the remote host.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\ntdsai.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18072
Description
The remote version of Active Directory contains a denial of service
vulnerability when processing LDAP requests. An attacker may exploit
this flaw to crash the remote Active Directory server.
Solution
Microsoft has released a set of patches for Windows 2000, Windows XP,
Windows 2003 and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms08-035.mspx
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:N/I:N/A:P)
CVSS Temporal Score: 4.1(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2008-1445
Bugtraq ID
29584
Other references
OSVDB:46066
CWE:20
MSFT:MS08-035
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 48942
Microsoft Windows SMB Registry : OS Version and Processor Architecture
Synopsis
It is possible to determine the processor architecture and Windows OS
version installed on the remote system.
List of Hosts Plugin Output
192.168.1.180
Operating System Version = 6.0.6001
Architecture = x86
Description
By using the supplied credentials, it is possible to connect to the
remote registry and determine the processor architecture and the
Windows OS version installed on the remote system.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port cifs (445/tcp)
Plugin ID: 46840
MS10-033: Vulnerabilities in Media Decompression Could Allow Remote Code Execution (979902)
Synopsis
Opening a specially crafted media file can result in arbitrary code
execution.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Asycfilt.dll has not been patched
Remote version : 6.0.6000.16386
Should be : 6.0.6001.18454
- C:\Windows\System32\Quartz.dll has not been patched
Remote version : 6.6.6001.18000
Should be : 6.6.6001.18461
Description
The remote Windows host has multiple unspecified code execution
vulnerabilities related to media decompression. A remote attacker
could exploit this by tricking a user into opening a specially crafted
media file, resulting in arbitrary code execution.
Solution
Microsoft has released a set of patches for DirectX 9, Windows Media
Format Runtime, Windows Media Encoder, and Asycfilt.dll (COM
component) :
http://www.microsoft.com/technet/security/bulletin/MS10-033.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.3(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:65221
OSVDB:65222
MSFT:MS10-033
Patch publication date: 2010/06/08
Plugin publication date: 2010/06/09
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port (0/tcp)
Plugin ID: 10908
Microsoft Windows 'Domain Administrators' Group User List
Synopsis
There is at least one user in the 'Domain Administrators' group.
List of Hosts Plugin Output
192.168.1.180
The following user is a member of the 'Domain Administrators' group :
- Administrator
Description
Using the supplied credentials, it is possible to extract the member
list of the 'Domain Administrators' group. Members of this group have
complete access to the Windows Domain.
Solution
Verify that each member of the group should have this type of access.
Risk Factor
None
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 35824
MS09-008: Vulnerabilities in DNS and WINS Server Could Allow Spoofing (962238)
Synopsis
The remote host is vulnerable to DNS and/or WINS spoofing attacks.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Dns.exe has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18214
Description
The remote host has a Windows DNS server and/or a Windows WINS server
installed.
Multiple vulnerabilities in the way that Windows DNS servers cache and
validate queries as well as the way that Windows DNS servers and
Windows WINS servers handle WPAD and ISATAP registration may allow
remote attackers to redirect network traffic intended for systems on
the Internet to the attacker's own systems.
Solution
Microsoft has released a set of patches for Windows 2000, 2003 and
2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-008.mspx
Risk Factor
Medium/ CVSS Base Score: 5.8
(CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:N)
CVSS Temporal Score: 4.3(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:52517
OSVDB:52518
OSVDB:52519
OSVDB:52520
CWE:20
MSFT:MS09-008
Plugin last modification date: 2011/03/14
Ease of exploitability: No known exploits are available
Port (0/tcp)
Plugin ID: 24269
Windows Management Instrumentation (WMI) Available
Synopsis
WMI queries can be made against the remote host.
List of Hosts
192.168.1.180
Description
The supplied credentials can be used to make WMI (Windows Management
Instrumentation) requests against the remote host over DCOM.
These requests can be used to gather information about the remote host
such as its current state, network interface configuration, etc.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port cifs (445/tcp)
Plugin ID: 33874
MS08-045: Cumulative Security Update for Internet Explorer (953838)
Synopsis
Arbitrary code can be executed on the remote host through the web
client.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18099
Description
The remote host is missing the IE cumulative security update 953838.
The remote version of IE is vulnerable to several flaws which may
allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008:
http://www.microsoft.com/technet/security/Bulletin/MS08-045.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.3(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:47414
OSVDB:47415
OSVDB:47416
OSVDB:47417
OSVDB:47418
OSVDB:47419
CWE:399
MSFT:MS08-045
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 45378
MS10-018: Cumulative Security Update for Internet Explorer (980182)
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18444
Description
The remote host is missing IE Security Update 980182.
The remote version of IE is affected by several vulnerabilities that
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, and Windows 7 :
http://www.microsoft.com/technet/security/bulletin/ms10-018.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2010-0267
CVE-2010-0488
CVE-2010-0489
CVE-2010-0490
CVE-2010-0491
CVE-2010-0492
CVE-2010-0494
CVE-2010-0805
CVE-2010-0806
CVE-2010-0807
Other references
OSVDB:62810
OSVDB:63327
OSVDB:63328
OSVDB:63329
OSVDB:63330
OSVDB:63331
OSVDB:63332
OSVDB:63333
OSVDB:63334
OSVDB:63335
MSFT:MS10-018
Patch publication date: 2010/03/30
Plugin publication date: 2010/03/30
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact, Metasploit (Internet Explorer DHTML Behaviors Use After Free)
Port cifs (445/tcp)
Plugin ID: 42112
MS09-056: Vulnerabilities in Windows CryptoAPI Could Allow Spoofing (974571)
Synopsis
Certain identity validation methods may be bypassed allowing impersonation.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\msasn1.dll has not been patched
Remote version : 6.0.6000.16386
Should be : 6.0.6001.18326
Description
The remote Windows host contains a version of the Microsoft Windows CryptoAPI
that is affected by multiple vulnerabilities :
- A spoofing vulnerability exists in the Microsoft Windows
CryptoAPI component when parsing ASN.1 information from
X.509 certificates. An attacker who successfully
exploited this vulnerability could impersonate another
user or system. (CVE-2009-2510)
- A spoofing vulnerability exists in the Microsoft Windows
CryptoAPI component when parsing ASN.1 object
identifiers from X.509 certificates. An attacker who
successfully exploited this vulnerability could
impersonate another user or system. (CVE-2009-2511)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008 and Windows 7 :
http://www.microsoft.com/technet/security/bulletin/MS09-056.mspx
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
CVSS Temporal Score: 4.1(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:58855
OSVDB:58856
CWE:189
MSFT:MS09-056
Patch publication date: 2009/10/13
Plugin publication date: 2009/10/13
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 42440
MS09-066: Vulnerability in Active Directory Could Allow Denial of Service (973309)
Synopsis
The installed version of Active Directory is prone to a denial of
service attack.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Ntdsai.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18281
Description
The installed version of Microsoft Active Directory / Active
Directory Application Mode / Active Directory Lightweight Directory
Service has a buffer overflow vulnerability. By sending specially
crafted LDAP or LDAPS requests, a remote attacker may be able to
exhaust stack space and cause the affected host to stop responding
until it is restarted.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-066.mspx
Risk Factor
High/ CVSS Base Score: 7.8
(CVSS2#AV:N/AC:L/Au:N/C:N/I:N/A:C)
CVSS Temporal Score: 6.4(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2009-1928
Bugtraq ID
36918
Other references
OSVDB:59856
CWE:399
MSFT:MS09-066
Patch publication date: 2009/11/10
Plugin publication date: 2009/11/10
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 17651
Microsoft Windows SMB : Obtains the Password Policy
Synopsis
It is possible to retrieve the remote host's password policy using the
supplied credentials.
List of Hosts Plugin Output
192.168.1.180
The following password policy is defined on the remote host:
Minimum password len: 7
Password history len: 24
Maximum password age (d): 42
Password must meet complexity requirements: Enabled
Minimum password age (d): 1
Forced logoff time (s): Not set
Locked account time (s): 1800
Time between failed logon (s): 1800
Number of invalid logon before locked out (s): 0
Description
Using the supplied credentials it was possible to extract the
password policy for the remote Windows host. The password policy must
conform to the Informational System Policy.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 51912
MS11-012: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2479628)
Synopsis
The remote Windows kernel is affected by multiple vulnerabilities.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Win32k.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18573
Description
The remote host is running a version of the Windows kernel that is
affected by one or more of the following vulnerabilities :
- The Win32k.sys kernel-mode driver improperly validates
data supplied from user mode to kernel mode.
(CVE-2011-0086)
- The Win32k.sys kernel-mode driver insufficiently
validates data supplied from user mode to kernel mode.
(CVE-2011-0087)
- The Win32k.sys kernel-mode driver does not properly
validate data supplied from user mode to kernel mode,
resulting in a 'Window Class Pointer Confusion'
vulnerability. (CVE-2011-0088)
- The Win32k.sys kernel-mode driver does not properly
validate data supplied from user mode to kernel mode,
resulting in a 'Window Class Improper Pointer
Validation' vulnerability. (CVE-2011-0089)
- The Win32k.sys kernel-mode driver does not properly
validate data supplied from user mode to kernel mode,
resulting in a memory corruption vulnerability.
(CVE-2011-0090)
An attacker with local access to the affected system can exploit these
issues to execute arbitrary code in kernel mode and take complete
control of the affected system.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS11-012.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
Other references
OSVDB:70814
OSVDB:70816
OSVDB:70817
OSVDB:70818
OSVDB:70819
MSFT:MS11-012
Patch publication date: 2011/02/08
Plugin publication date: 2011/02/08
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 47750
MS KB2286198: Windows Shell Shortcut Icon Parsing Arbitrary Code Execution
Synopsis
It may be possible to execute arbitrary code on the remote Windows
host using a malicious shortcut file.
List of Hosts Plugin Output
192.168.1.180
According to the following registry entries, displaying shortcut
icons has not been disabled :
Key : HKEY_CLASS_ROOT\lnkfile\shellex\IconHandler
Value : {00021401-0000-0000-C000-000000000046}
Key : HKEY_CLASS_ROOT\piffile\shellex\IconHandler
Value : {00021401-0000-0000-C000-000000000046}
Description
Windows Shell does not properly validate the parameters of a shortcut
file when loading its icon. Attempting to parse the icon of a
specially crafted shortcut file can result in arbitrary code
execution.
A remote attacker could exploit this by tricking a user into viewing a
malicious shortcut file via Windows Explorer, or any other application
that parses the shortcut's icon. This can also be exploited by an
attacker who tricks a user into inserting removable media containing
a malicious shortcut (e.g. CD, USB drive), and AutoPlay is enabled.
Solution
Either apply MS10-046 or disable the displaying of shortcut icons
(refer to the Microsoft advisory).
See also
http://www.microsoft.com/technet/security/advisory/2286198.mspx
http://www.microsoft.com/technet/security/bulletin/MS10-046.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2010-2568
Bugtraq ID
41732
Other references
OSVDB:66387
CERT:940193
EDB-ID:14403
Secunia:40647
MSFT:MS10-046
Plugin publication date: 2010/07/18
Plugin last modification date: 2011/03/09
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact, Metasploit (Microsoft Windows Shell LNK Code Execution)
Port (0/tcp)
Plugin ID: 24272
Network Interfaces Enumeration (WMI)
Synopsis
It is possible to obtain the list of network interfaces on the remote
host.
List of Hosts Plugin Output
192.168.1.180
+ Network Interface Information :
- Network Interface = [00000006] Intel(R) PRO/1000 MT Network Connection
- MAC Address = 00:0C:29:9D:A1:C6
- IPAddress/IPSubnet = 192.168.1.180/255.255.255.0
- IPAddress/IPSubnet = fe80::70ba:cd7a:a6bc:7237/64
+ Routing Information :
Destination Netmask Gateway
----------- ------- -------
127.0.0.0 255.0.0.0 0.0.0.0
127.0.0.1 255.255.255.255 0.0.0.0
127.255.255.255 255.255.255.255 0.0.0.0
192.168.1.0 255.255.255.0 0.0.0.0
192.168.1.180 255.255.255.255 0.0.0.0
192.168.1.255 255.255.255.255 0.0.0.0
224.0.0.0 240.0.0.0 0.0.0.0
224.0.0.0 240.0.0.0 0.0.0.0
255.255.255.255 255.255.255.255 0.0.0.0
255.255.255.255 255.255.255.255 0.0.0.0
Description
It is possible to use WMI queries to extract the list of network
interfaces on the remote host and the IP attached to them.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port cifs (445/tcp)
Plugin ID: 34414
MS KB956391: Cumulative Security Update of ActiveX Kill Bits
Synopsis
The remote Windows host is missing a security update containing
ActiveX kill bits
List of Hosts Plugin Output
192.168.1.180
The kill-bit has not been set for the following control :
{AED98630-0251-4E83-917D-43A23D66D507}
Note that Nessus did not check whether there were other kill-bits
that have not been set because 'Thorough Tests' was not enabled
when this scan was run.
Description
The remote host is missing a list of kill bits for ActiveX controls
that are known to contain vulnerabilities.
If these ActiveX controls are ever installed on the remote host,
either now or in the future, they would expose it to various security
issues.
Solution
Microsoft has released an advisory about this :
http://www.microsoft.com/technet/security/advisory/956391.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
Plugin last modification date: 2011/03/16
Port cifs (445/tcp)
Plugin ID: 51164
MS10-092: Vulnerability in Task Scheduler Could Allow Elevation of Privilege (2305420)
Synopsis
A privilege escalation vulnerability exists in Windows Task
Scheduler.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Schedsvc.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18551
Description
The remote host is running a version of Windows that contains a flaw
in the task scheduler that may lead to a privilege escalation by
running a specially crafted application.
To exploit this vulnerability, an attacker must have valid logon
credentials and be able to log on locally.
Solution
Microsoft has releaseed a set of patches for Vista, 2008, 7, and 2008
R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-092.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVE
CVE-2010-3338
Bugtraq ID
44357
Other references
OSVDB:68518
MSFT:MS10-092
Patch publication date: 2010/12/14
Plugin publication date: 2010/12/15
Plugin last modification date: 2011/03/18
Port cifs (445/tcp)
Plugin ID: 40888
MS09-045: Vulnerability in JScript Scripting Engine Could Allow Remote Code Execution (971961)
Synopsis
Arbitrary code can be executed on the remote host through the web or
email client.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\Jscript.dll has not been patched
Remote version : 5.7.0.18000
Should be : 5.7.0.18266
Description
The remote host is running a version of Windows that contains a flaw
in its JScript scripting engine.
An attacker may be able to execute arbitrary code on the remote host
by constructing a malicious JScript and enticing a victim to visit a
web site or view a specially crafted email message.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-045.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2009-1920
Bugtraq ID
36224
Other references
OSVDB:57804
CWE:94
MSFT:MS09-045
Plugin publication date: 2009/09/08
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 48291
MS10-054: Vulnerabilities in SMB Server Could Allow Remote Code Execution (982214)
Synopsis
It is possible to execute arbitrary code on the remote Windows host
due to flaws in its SMB implementation.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\drivers\Srv.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18495
Description
The remote host is affected by several vulnerabilities in the SMB
server that may allow an attacker to execute arbitrary code or perform
a denial of service against the remote host.
Solution
Microsoft has released a set of patches for Windows XP, Vista, 2008,
7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-054.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.8(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:66974
OSVDB:66975
OSVDB:66976
EDB-ID:14607
MSFT:MS10-054
Patch publication date: 2010/08/10
Plugin publication date: 2010/08/11
Plugin last modification date: 2011/04/01
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 45507
MS10-020: Vulnerabilities in SMB Client Could Allow Remote Code Execution (980232)
Synopsis
Arbitrary code can be executed on the remote host through the
installed SMB client.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\drivers\Mrxsmb.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18431
Description
The version of the SMB client software installed on the remote
Windows host may be affected by one or more vulnerabilities,
including some that could allow arbitrary code execution :
- Incorrect handling of incomplete SMB responses could
be abused to cause the system to stop responding.
(CVE-2009-3676)
- A vulnerability in the way the SMB client allocates
memory when parsing specially crafted SMB responses
could be abused by an unauthenticated remote attacker
to execute arbitrary code with system-level privileges.
(CVE-2010-0269)
- Improper validation of fields in SMB responses could
lead to a memory corruption issue and in turn to
arbitrary code execution with system-level privileges.
(CVE-2010-0270)
- Improper parsing of SMB transaction responses could
lead to a memory corruption issue resulting in code
execution with system-level privileges. (CVE-2010-0476)
- Improper handling of SMB responses could cause the SMB
client to consume the entire response and indicate an
invalid value to the Winsock kernel, which in turn
could allow remote code execution and result in the
compromise of the affected system. (CVE-2010-0477)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-020.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.3(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:59957
OSVDB:64925
OSVDB:64926
OSVDB:64927
OSVDB:64928
MSFT:MS10-020
Patch publication date: 2010/04/13
Plugin publication date: 2010/04/13
Plugin last modification date: 2011/02/23
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 49219
MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290)
Synopsis
Arbitrary code can be executed on the remote host due to a flaw in the
Spooler service.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Spoolsv.exe has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18511
Description
The version of the Print Spooler service on the remote Windows host
is affected by the following vulnerability :
- A service impersonation vulnerability could allow a
remote, unauthenticated attacker to execute arbitrary
code on a Windows XP system to escalate privileges on
all other supported Windows systems. (CVE-2010-2729)
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2:
http://www.microsoft.com/technet/security/bulletin/ms10-061.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVE
CVE-2010-2729
Bugtraq ID
43073
Other references
OSVDB:67988
MSFT:MS10-061
Patch publication date: 2010/09/14
Plugin publication date: 2010/09/14
Plugin last modification date: 2011/03/31
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Metasploit (Microsoft Print Spooler Service Impersonation Vulnerability)
Port cifs (445/tcp)
Plugin ID: 51903
MS11-003: Cumulative Security Update for Internet Explorer (2482017)
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18565
Description
The remote host is missing Internet Explorer (IE) Security Update
2482017.
The remote version of IE is affected by several vulnerabilities that
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for XP, 2003, Vista, 2008, 7,
and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms11-003.mspx
See also
http://seclists.org/fulldisclosure/2010/Dec/110
http://www.breakingpointsystems.com/community/blog/ie-vulnerability/
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
Other references
OSVDB:69796
OSVDB:70831
OSVDB:70832
OSVDB:70833
CERT:634956
EDB-ID:15708
EDB-ID:15746
MSFT:MS11-003
Secunia:42510
Patch publication date: 2011/02/08
Plugin publication date: 2011/02/08
Plugin last modification date: 2011/03/09
Ease of exploitability: Exploits are available
Exploitable with: Metasploit (Internet Explorer CSS Recursive Import Use After Free)
Port cifs (445/tcp)
Plugin ID: 20811
Microsoft Windows Installed Software Enumeration (credentialed check)
Synopsis
It is possible to enumerate installed software.
List of Hosts Plugin Output
192.168.1.180
The following software are installed on the remote host :
Splunk [version 107.2.25896]
Description
This plugin lists software potentially installed on the remote host by
crawling the registry entries in :
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
Note that these entries do not necessarily mean the applications are
actually installed on the remote host - they may have been left behind
by uninstallers, or the associated files may have been manually
removed.
Solution
Remove any applications that are not compliant with your organization's
acceptable use and security policies.
Risk Factor
None
Plugin last modification date: 2011/03/16
Port cifs (445/tcp)
Plugin ID: 31798
MS08-025: Vulnerability in Windows Kernel Could Allow Elevation of Privilege (941693)
Synopsis
A local user can elevate his privileges on the remote host.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Win32k.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18027
Description
The remote host contains a version of the Windows kernel which is vulnerable
to a security flaw which may allow a local user to elevate his privileges
or to crash it (therefore causing a denial of service).
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003, Vista, 2008:
http://www.microsoft.com/technet/security/bulletin/ms08-025.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.0(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2008-1084
Bugtraq ID
28554
Other references
OSVDB:44206
CWE:94
MSFT:MS08-025
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact
Port cifs (445/tcp)
Plugin ID: 34406
MS08-061: Microsoft Windows Kernel Multiple Privilege Elevation (954211)
Synopsis
A local user can elevate his privileges on the remote host.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Win32k.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18141
Description
The remote host contains a version of the Windows kernel which is vulnerable
to a security flaw which may allow a local user to elevate his privileges
or to crash it (therefore causing a denial of service).
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003, Vista, 2008:
http://www.microsoft.com/technet/security/bulletin/ms08-061.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 5.3(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:49054
OSVDB:49055
OSVDB:49056
CWE:264
MSFT:MS08-061
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 48284
MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852)
Synopsis
The Windows kernel is affected by several vulnerabilities that could
allow escalation of privileges.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Ntoskrnl.exe has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18488
Description
The remote Windows host is running a version of the Windows kernel
that is affected by one or more of the following vulnerabilities :
- A race condition when creating certain types of kernel
threads may allow a local attacker to execute arbitrary
code in kernel mode and take complete control of the
affected system. (CVE-2010-1888)
- A double free vulnerability when the kernel initializes
objects while handling certain errors may allow a local
attacker to execute arbitrary code in kernel mode and
take complete control of the affected system.
(CVE-2010-1889)
- A failure to properly validate access control lists on
kernel objects may allow a local attacker to cause the
system to become unresponsive and automatically
restart. (CVE-2010-1890)
Solution
Microsoft has released a set of patches for Windows XP, Vista, 2008,
7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/MS10-047.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.0(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:66988
OSVDB:66989
OSVDB:66990
MSFT:MS10-047
Patch publication date: 2010/08/10
Plugin publication date: 2010/08/11
Plugin last modification date: 2011/04/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 35070
MS08-071: Vulnerabilities in GDI+ Could Allow Remote Code Execution (956802)
Synopsis
Arbitrary code can be executed on the remote host through the Microsoft
GDI rendering engine.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Gdi32.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18159
Description
The remote host is running a version of Windows that is affected by
multiple buffer oveflow vulnerabilities when viewing WMF files, which
may allow an attacker to execute arbitrary code on the remote host.
To exploit this flaw, an attacker would need to send a malformed WMF
file to a user on the remote host and wait for him to open it using an
affected Microsoft application.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms08-071.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:50561
OSVDB:50562
CWE:119
MSFT:MS08-071
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 35074
MS08-075: Vulnerabilities in Windows Search Could Allow Remote Code Execution (959349)
Synopsis
Vulnerabilities in the Windows Shell may allow an attacker to execute
privileged commands on the remote host.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\Explorer.exe has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18164
Description
The remote version of Windows contains a version of the Windows Shell
which contains a vulnerability in the way it handles saved seaches..
An attacker might use this flaw to trick an administrator to execute a saved
search and therefore execute arbitrary commands on his behalf.
Solution
Microsoft has released a set of patches for Windows Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms08-075.mspx
Risk Factor
Medium/ CVSS Base Score: 6.2
(CVSS2#AV:L/AC:H/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 4.6(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:50565
OSVDB:50566
CWE:399
MSFT:MS08-075
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 49962
MS10-085: Vulnerability in SChannel Could Allow Denial of Service (2207566)
Synopsis
The remote Windows host has a denial of service vulnerability.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Schannel.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18507
Description
The remote Windows host is running a version of the Secure Channel
(SChannel) security package that is affected by a denial of service
vulnerability. This flaw exists in the way that SChannel processes
client certificates.
A remote attacker could send a specially crafted network packet to the
host that would cause the LSASS service to stop responding and the
system to restart.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-085.mspx
Risk Factor
High/ CVSS Base Score: 7.8
(CVSS2#AV:N/AC:L/Au:N/C:N/I:N/A:C)
CVSS Temporal Score: 5.8(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2010-3229
Bugtraq ID
43780
Other references
OSVDB:68560
MSFT:MS10-085
Patch publication date: 2010/10/12
Plugin publication date: 2010/10/13
Plugin last modification date: 2011/03/22
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 34744
MS08-069: Vulnerabilities in Microsoft XML Core Services Could Allow Remote Code Execution (955218)
Synopsis
Arbitrary code can be executed on the remote host through the web or
email client.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Msxml3.dll has not been patched
Remote version : 8.100.1043.0
Should be : 8.100.1048.0
Description
The remote host is running a version of Windows which contains a flaw
in the Windows XML Core Services..
An attacker may be able to execute arbitrary code on the remote host
by constructing a malicious script and enticing a victim to visit a
web site or view a specially-crafted email message.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008:
http://www.microsoft.com/technet/security/Bulletin/MS08-069.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.3(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:32627
OSVDB:49926
OSVDB:50279
CWE:200
MSFT:MS08-069
Plugin publication date: 2008/11/12
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 44110
MS10-002: Cumulative Security Update for Internet Explorer (978207)
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18385
Description
The remote host is missing IE Security Update 978207.
The remote version of IE is affected by several vulnerabilities that
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, and Windows 7 :
http://www.microsoft.com/technet/security/Bulletin/MS10-002.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2009-4074
CVE-2010-0027
CVE-2010-0244
CVE-2010-0245
CVE-2010-0246
CVE-2010-0247
CVE-2010-0248
CVE-2010-0249
Other references
OSVDB:60660
OSVDB:61697
OSVDB:61909
OSVDB:61910
OSVDB:61911
OSVDB:61912
OSVDB:61913
OSVDB:61914
MSFT:MS10-002
Secunia:38209
Patch publication date: 2009/01/21
Plugin publication date: 2009/01/21
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Metasploit (Internet Explorer "Aurora" Memory Corruption)
Port cifs (445/tcp)
Plugin ID: 51837
MS KB2501696: Vulnerability in MHTML Could Allow Information Disclosure
Synopsis
The remote Windows host is affected by an information disclosure
vulnerability.
List of Hosts Plugin Output
192.168.1.180
Nessus determined the workaround was not applied because MHTML has not
been added as a restricted protocol.
Description
A flaw exists in the way MHTML interprets MIME-formatted requests for
content blocks within a document. An attacker, exploiting this flaw,
could cause a victim to run malicious scripts when visiting various
web sites, resulting in information disclosure.
Solution
Consider applying the workaround provided by Microsoft.
Note, though, that applying the workaround may lead to some websites
working incorrectly.
Risk Factor
Medium/ CVSS Base Score: 4.3
(CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N)
CVE
CVE-2011-0096
Bugtraq ID
46055
Other references
OSVDB:70693
Secunia:43093
Plugin last modification date: 2011/03/09
Port cifs (445/tcp)
Plugin ID: 51587
MS KB2488013: Internet Explorer CSS Import Rule Processing Arbitrary Code Execution
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
Nessus determined the workaround was not applied based on the following
information :
- Fix it solution referenced in KB 2488013 is not applied.
- Microsoft Enhanced Mitigation Experience Toolkit (EMET) is not installed.
Description
The remote host is missing one of the workarounds referenced in KB
2488013.
The remote version of IE reportedly fails to correctly process certain
specially crafted Cascading Style Sheets (CSS), which could result in
arbitrary code execution on the remote system.
Solution
Apply Microsoft suggested workarounds.
See also
http://seclists.org/fulldisclosure/2010/Dec/110
http://www.breakingpointsystems.com/community/blog/ie-vulnerability/
http://support.microsoft.com/kb/2488013/en-us
http://www.microsoft.com/technet/security/advisory/2488013.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVE
CVE-2010-3971
Bugtraq ID
45246
Other references
OSVDB:69796
CERT:634956
EDB-ID:15708
EDB-ID:15746
Secunia:42510
Plugin publication date: 2011/01/20
Plugin last modification date: 2011/03/09
Ease of exploitability: Exploits are available
Exploitable with: Metasploit (Internet Explorer CSS Recursive Import Use After Free)
Port cifs (445/tcp)
Plugin ID: 48286
MS10-049: Vulnerabilities in SChannel could allow Remote Code Execution (980436)
Synopsis
It may be possible to execute arbitrary code on the remote Windows
host using the Secure Channel security package.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Schannel.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18490
Description
The remote Windows host is running a version of the Secure Channel
(SChannel) security package that is affected by one or more of the
following vulnerabilities :
- The SChannel authentication component allows a client to
renegotiate the connection after the initial handshake,
which could be abused to inject information into an encrypted
connection, effectively sending traffic spoofing an
authenticated client. (CVE-2009-3555)
- The way that SChannel validates a certificate request message
sent by a server could lead to a denial of service or even allow
execution of arbitrary code if an attacker can trick a user on
the affected system into connecting to malicious web server over
SSL or TLS. (CVE-2010-2566)
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-049.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:59968
OSVDB:66987
CWE:310
MSFT:MS10-049
Patch publication date: 2010/08/10
Plugin publication date: 2010/08/11
Plugin last modification date: 2011/04/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 33442
MS08-038: Vulnerability in Windows Explorer Could Allow Remote Code Execution (950582)
Synopsis
Vulnerabilities in the Windows Shell may allow an attacker to execute
privileged commands on the remote host.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\shell32.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18062
Description
The remote version of Windows contains a version of the Windows Shell
that contains a vulnerability in the way it handles saved searches.
An attacker might use this flaw to trick an administrator to execute a
saved search and therefore execute arbitrary commands on his behalf.
Solution
Microsoft has released a set of patches for Windows Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms08-038.mspx
Risk Factor
Medium/ CVSS Base Score: 6.2
(CVSS2#AV:L/AC:H/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 4.6(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2008-1435
Bugtraq ID
30109
Other references
OSVDB:46774
MSFT:MS08-038
CWE:94
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 46839
MS10-032: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (979559)
Synopsis
The Windows kernel is affected by several vulnerabilities that could
allow escalation of privileges.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Win32k.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18468
Description
The remote Windows host is running a version of the Windows kernel
that is affected by one or more of the following vulnerabilities :
- Improper validation of changes in certain kernel
objects may allow a local attacker to execute arbitrary
code in kernel mode and take complete control of the
affected system. (CVE-2010-0484)
- Improper validation of parameters when creating a new
window may allow a local attacker to execute arbitrary
code in kernel mode and take complete control of the
affected system. (CVE-2010-0485)
- A vulnerability that arises in the way Windows provides
glyph outline information to applications may allow a
local attacker to execute arbitrary code in kernel mode
and take complete control of the affected system.
(CVE-2010-1255)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-032.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.0(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:65223
OSVDB:65224
OSVDB:65225
MSFT:MS10-032
Patch publication date: 2010/06/08
Plugin publication date: 2010/06/09
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact
Port cifs (445/tcp)
Plugin ID: 44419
MS10-009: Vulnerabilities in Windows TCP/IP Could Allow Remote Code Execution (974145)
Synopsis
The remote host has multiple vulnerabilities in its TCP/IP
implementation.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\drivers\Tcpip.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18377
Description
The remote Windows host has the following vulnerabilities in its
TCP/IP implementation :
- Hosts with IPv6 enabled perform insufficient bounds
checking when processing specially crafted ICMPv6 Router
Advertisement packets. A remote attacker could exploit
this to execute arbitrary code. (CVE-2010-0239)
- Specially crafted Encapsulating Security Payloads (ESP)
are not processed properly. A remote attacker could
exploit this to execute arbitrary code. (CVE-2010-0240)
- Hosts with IPv6 enabled perform insufficient bounds
checking when processing specially crafted ICMPv6 Route
Information packets. A remote attacker could exploit
this to execute arbitrary code. (CVE-2010-0241)
- Specially crafted TCP packets with a malformed
selective acknowledgment (SACK) value can cause the
system to stop responding and automatically restart. A
remote attacker could exploit this to cause a denial of
service. (CVE-2009-0242)
Solution
Microsoft has released a set of patches for Windows Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS10-009.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.8(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:62247
OSVDB:62248
OSVDB:62249
OSVDB:62250
MSFT:MS10-009
CWE:399
Patch publication date: 2010/02/09
Plugin publication date: 2010/02/09
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 51162
MS10-090: Cumulative Security Update for Internet Explorer (2416400)
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18542
Description
The remote host is missing Internet Explorer (IE) Security Update
2416400.
The remote version of IE is affected by several vulnerabilities that
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for XP, 2003, Vista, 2008, 7,
and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-090.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVE
CVE-2010-3340
CVE-2010-3342
CVE-2010-3343
CVE-2010-3345
CVE-2010-3346
CVE-2010-3348
CVE-2010-3962
Other references
OSVDB:68987
OSVDB:69160
OSVDB:69825
OSVDB:69826
OSVDB:69827
OSVDB:69828
OSVDB:69829
OSVDB:69830
MSFT:MS10-090
Patch publication date: 2010/12/14
Plugin publication date: 2010/12/15
Plugin last modification date: 2011/03/18
Ease of exploitability: Exploits are available
Exploitable with: Metasploit (Internet Explorer CSS SetUserClip Memory Corruption)
Port cifs (445/tcp)
Plugin ID: 51911
MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802)
Synopsis
The Windows kernel is affected by several vulnerabilities that could
allow escalation of privileges.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Ntoskrnl.exe has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18538
Description
The remote Windows host is running a version of the Windows kernel
that is affected by one or more of the following vulnerabilities :
- A buffer overflow in the 'GreEnableEUDC()' function can
be triggered using specially crafted end-user-defined
characters (EUDC) registry key values. (CVE-2010-4398)
- An integer truncation vulnerability exists due to the
failure of the Windows kernel to validate user-supplied
data before allocating memory. (CVE-2011-0045)
An attacker with local access to the affected system can exploit these
issues to execute arbitrary code in kernel mode and take complete
control of the affected system.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS11-011.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
Other references
OSVDB:69501
OSVDB:70823
CERT:529673
EDB-ID:15609
EDB-ID:16262
MSFT:MS11-011
Patch publication date: 2011/02/08
Plugin publication date: 2011/02/08
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 51170
MS10-098: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2436673)
Synopsis
A privilege escalation vulnerability exists in the Windows Kernel.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Win32k.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18539
Description
The remote host is running a version of Windows which contains a flaw
in the kernel which may lead to a privilege escalation by running a
specially crafted application.
To exploit this vulnerability an attacker must have valid logon
credentials and be able to log on locally.
Solution
Microsoft has released a set of patches for XP, 2003, Vista, 2008,
7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-098.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.1(CVSS2#E:U/RL:U/RC:C)
Other references
OSVDB:69797
OSVDB:69798
OSVDB:69799
OSVDB:69800
OSVDB:69801
OSVDB:69802
MSFT:MS10-098
Patch publication date: 2010/12/14
Plugin publication date: 2010/12/15
Plugin last modification date: 2011/03/18
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 10860
SMB Use Host SID to Enumerate Local Users
Synopsis
It is possible to enumerate local users.
List of Hosts Plugin Output
192.168.1.180
- Administrator (id 500, Administrator account)
- Guest (id 501, Guest account)
- WIN-8BPIQBRO0CX$ (id 1000)
- DnsAdmins (id 1101)
- DnsUpdateProxy (id 1102)
- EXCHANGE$ (id 1103)
- Exchange Domain Servers (id 1104)
- Exchange Enterprise Servers (id 1105)
- 249E6E5E-02B7-46F0-B (id 1106)
- scorebot (id 1107)
- pcurrie (id 1108)
- dtouart (id 1109)
- sgieber (id 1110)
- fcrumb (id 1111)
- cvukelj (id 1112)
- aballs (id 1113)
- idepierre (id 1114)
- mmcleroy (id 1115)
- kmalavet (id 1116)
- tjank (id 1117)
- fdraxler (id 1118)
- cpaskell (id 1119)
- mcosgrave (id 1120)
- deichert (id 1121)
- lmicha (id 1122)
- kbarroso (id 1123)
- vroutte (id 1124)
- rschummer (id 1125)
- lfollett (id 1126)
- pcoladonato (id 1127)
- gdelreal (id 1128)
- lthroneberry (id 1129)
- lmccarn (id 1130)
- mlutjen (id 1131)
- vkonkel (id 1132)
- asponsler (id 1133)
- metzkorn (id 1134)
- tmcquirter (id 1135)
- fconcannon (id 1136)
- lyouker (id 1137)
- mamini (id 1138)
- lrosko (id 1139)
- dcolligan (id 1140)
- fprok (id 1141)
- vnickleberry (id 1142)
- afeurtado (id 1143)
- rgerczak (id 1144)
- hvanhekken (id 1145)
- cdoudna (id 1146)
- sbessent (id 1147)
- wlorimor (id 1148)
- hkarmazyn (id 1149)
- sdechambeau (id 1150)
- lsotelo (id 1151)
- aterris (id 1152)
- mkanta (id 1153)
- atopacio (id 1154)
- gkamphoefner (id 1155)
- abergmeier (id 1156)
- ksorrentino (id 1157)
- lgiacchino (id 1158)
- mmajorga (id 1159)
- fcosby (id 1160)
- lsimcic (id 1161)
- ltabor (id 1162)
- lschweickert (id 1163)
- dbrueckman (id 1164)
- scalverley (id 1165)
- tstansfield (id 1166)
- fpassarelli (id 1167)
- tkreinhagen (id 1168)
- dkoenigsberg (id 1169)
- asteltenpohl (id 1170)
- agoonen (id 1171)
- smockler (id 1172)
- npacheco (id 1173)
- ycambell (id 1174)
- schesher (id 1175)
- mwinegardner (id 1176)
- spoissant (id 1177)
- jlicerio (id 1178)
- murman (id 1179)
- cvrazel (id 1180)
- czoelle (id 1181)
- apaulshock (id 1182)
- gbartus (id 1183)
- edorrough (id 1184)
- jdifiora (id 1185)
- jteno (id 1186)
- tmichel (id 1187)
- bbegan (id 1188)
- aconelli (id 1189)
- ceuton (id 1190)
- sadelmann (id 1191)
- slook (id 1192)
- jhoffpavir (id 1193)
- nholsing (id 1194)
- mscouller (id 1195)
- jbroadwater (id 1196)
- ebrentlinger (id 1197)
- ablaske (id 1198)
- iguzon (id 1199)
- smceldowney (id 1200)
Note that, in addition to the Administrator and Guest accounts, Nessus
has enumerated only those local users with IDs between 1000 and 1200.
To use a different range, edit the scan policy and change the 'Start
UID' and/or 'End UID' preferences for this plugin, then re-run the
scan.
Description
Using the host security identifier (SID), it is possible to enumerate local users
on the remote Windows system.
Solution
n/a
Risk Factor
None
CVE
CVE-2000-1200
Bugtraq ID
959
Other references
OSVDB:714
Plugin publication date: 2002/02/13
Plugin last modification date: 2011/03/07
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 34409
MS08-064: Microsoft Windows Virtual Address Descriptors (VAD) Local Privilege Escalation (956841)
Synopsis
A local user can elevate his privileges on the remote host.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\Ntoskrnl.exe has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18145
Description
The remote host contains a version of the Windows kernel which is vulnerable
to a security flaw which may allow a local user to elevate his privileges
or to crash it (therefore causing a denial of service).
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms08-064.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 5.3(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2008-4036
Bugtraq ID
31675
Other references
OSVDB:49053
CWE:189
MSFT:MS08-064
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 43063
MS09-071: Vulnerabilities in Internet Authentication Service Could Allow Remote Code Execution (974318)
Synopsis
The remote Windows host has multiple vulnerabilities in an
authentication service.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Rastls.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18336
Description
The remote Windows host has the following vulnerabilities in the
Internet Authentication Service :
- There is a memory corruption vulnerability in the PEAP
authentication implementation. A remote unauthenticated
attacker could exploit this to execute arbitrary code as
SYSTEM. (CVE-2009-2505)
- Sending a specially crafted MS-CHAP v2 authentication
request could allow a remote attacker to obtain the
privileges of a specific, authorized user. (CVE-2009-3677)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, and 2008 :
http://www.microsoft.com/technet/security/bulletin/MS09-071.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.4(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:60832
OSVDB:60833
CWE:255
CWE:94
MSFT:MS09-071
Patch publication date: 2009/12/08
Plugin publication date: 2009/12/08
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 36152
MS09-014: Cumulative Security Update for Internet Explorer (963027)
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18226
Description
The remote host is missing IE Security Update 963027.
The remote version of IE is affected by several vulnerabilities that
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-014.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
Other references
OSVDB:53619
OSVDB:53623
OSVDB:53624
OSVDB:53625
OSVDB:53626
OSVDB:53627
CWE:399
MSFT:MS09-014
Plugin last modification date: 2011/03/11
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 42111
MS09-055: Cumulative Security Update of ActiveX Kill Bits (973525)
Synopsis
The remote Windows host has multiple ActiveX controls that are
affected by multiple code execution vulnerabilities.
List of Hosts Plugin Output
192.168.1.180
The kill bit has not been set for the following control :
{0002E531-0000-0000-C000-000000000046}
Note that Nessus did not check whether there were other kill bits
that have not been set because 'Thorough Tests' was not enabled
when this scan was run.
Description
Microsoft ActiveX controls that were compiled using the vulnerable
Active Template Library described in Microsoft Security Bulletin
MS09-035 have remote code execution vulnerabilities. A remote attacker
could exploit this to execute arbitrary code by tricking a user into
requesting a maliciously crafted web page.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-055.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2009-2493
Bugtraq ID
35828
Other references
OSVDB:56698
CWE:264
MSFT:MS09-035
MSFT:MS09-055
Patch publication date: 2009/10/13
Plugin publication date: 2009/10/13
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port dce-rpc (49177/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49177 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 367abb81-9844-35f1-ad32-98f038001003, version 2.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49177
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49176/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49176 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 50abc2a4-574d-40b3-9d66-ee4fd5fba076, version 5.0
Description : DNS Server
Windows process : dns.exe
Type : Remote RPC service
TCP Port : 49176
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49163/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49163 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 6b5bdd1e-528c-422c-af8c-a4079be4fe48, version 1.0
Description : Unknown RPC service
Annotation : Remote Fw APIs
Type : Remote RPC service
TCP Port : 49163
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-0123456789ab, version 1.0
Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe
Annotation : IPSec Policy agent endpoint
Type : Remote RPC service
TCP Port : 49163
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49161/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49161 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc59b4-4264-101a-8c59-08002b2f8426, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs Service
Type : Remote RPC service
TCP Port : 49161
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : d049b186-814f-11d1-9a3c-00c04fc9b232, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs API
Type : Remote RPC service
TCP Port : 49161
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a00c021c-2be2-11d2-b678-0000f87a8f8e, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : PERFMON SERVICE
Type : Remote RPC service
TCP Port : 49161
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49158/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49158 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49158
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49158
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49155/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49155 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49154/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49154 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49153/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49153 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service
Annotation : Event log TCPIP
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49152/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49152 :
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49152
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available remotely :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service
Annotation : Unimodem LRPC Endpoint
Type : Remote RPC service
Named pipe : \pipe\tapsrv
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Remote RPC service
Named pipe : \PIPE\srvsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service
Annotation : Event log TCPIP
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\InitShutdown
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\InitShutdown
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port epmap (135/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available locally :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : securityevent
Object UUID : 3bdb59a0-d736-4d44-9074-c1ee00000001
UUID : 24019106-a203-4642-b88d-82dae9158929, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : LRPC-b5293a2288d578326a
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service
Annotation : Unimodem LRPC Endpoint
Type : Local RPC service
Named pipe : tapsrvlpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service
Annotation : Unimodem LRPC Endpoint
Type : Local RPC service
Named pipe : unimdmsvc
Object UUID : 58abe70e-dc51-4f6c-917d-e8cc4f13e1fd
UUID : 906b0ce0-c70b-1067-b317-00dd010662da, version 1.0
Description : Distributed Transaction Coordinator
Windows process : msdtc.exe
Type : Local RPC service
Named pipe : LRPC-3fbda57d0c4803ba9c
Object UUID : 6971a2ac-7f04-4ec5-8d8d-d1d88ee83c48
UUID : 906b0ce0-c70b-1067-b317-00dd010662da, version 1.0
Description : Distributed Transaction Coordinator
Windows process : msdtc.exe
Type : Local RPC service
Named pipe : LRPC-3fbda57d0c4803ba9c
Object UUID : a3b8b0c1-7f58-4ac6-a858-05237e74d876
UUID : 906b0ce0-c70b-1067-b317-00dd010662da, version 1.0
Description : Distributed Transaction Coordinator
Windows process : msdtc.exe
Type : Local RPC service
Named pipe : LRPC-3fbda57d0c4803ba9c
Object UUID : 71ebac49-c98f-40cf-b969-28879f258965
UUID : 906b0ce0-c70b-1067-b317-00dd010662da, version 1.0
Description : Distributed Transaction Coordinator
Windows process : msdtc.exe
Type : Local RPC service
Named pipe : LRPC-3fbda57d0c4803ba9c
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-0123456789ab, version 1.0
Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe
Annotation : IPSec Policy agent endpoint
Type : Local RPC service
Named pipe : LRPC-64636b2001baa70a54
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc59b4-4264-101a-8c59-08002b2f8426, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs Service
Type : Local RPC service
Named pipe : OLE4D00800FB7224E3BA74F6D7F4A40
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc59b4-4264-101a-8c59-08002b2f8426, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs Service
Type : Local RPC service
Named pipe : LRPC-32c9434230805de61a
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : d049b186-814f-11d1-9a3c-00c04fc9b232, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs API
Type : Local RPC service
Named pipe : OLE4D00800FB7224E3BA74F6D7F4A40
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : d049b186-814f-11d1-9a3c-00c04fc9b232, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs API
Type : Local RPC service
Named pipe : LRPC-32c9434230805de61a
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a00c021c-2be2-11d2-b678-0000f87a8f8e, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : PERFMON SERVICE
Type : Local RPC service
Named pipe : OLE4D00800FB7224E3BA74F6D7F4A40
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a00c021c-2be2-11d2-b678-0000f87a8f8e, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : PERFMON SERVICE
Type : Local RPC service
Named pipe : LRPC-32c9434230805de61a
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0b6edbfa-4a24-4fc6-8a23-942b1eca65d1, version 1.0
Description : Unknown RPC service
Annotation : Spooler function endpoint
Type : Local RPC service
Named pipe : spoolss
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : ae33069b-a2a8-46ee-a235-ddfd339be281, version 1.0
Description : Unknown RPC service
Annotation : Spooler base remote object endpoint
Type : Local RPC service
Named pipe : spoolss
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 4a452661-8290-4b36-8fbe-7f4093a94978, version 1.0
Description : Unknown RPC service
Annotation : Spooler function endpoint
Type : Local RPC service
Named pipe : spoolss
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : dd490425-5325-4565-b774-7e27d6c09c24, version 1.0
Description : Unknown RPC service
Annotation : Base Firewall Engine API
Type : Local RPC service
Named pipe : LRPC-eb9e1c5180d5c63bde
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 7f9d11bf-7fb9-436b-a812-b2d50c5d4c03, version 1.0
Description : Unknown RPC service
Annotation : Fw APIs
Type : Local RPC service
Named pipe : LRPC-eb9e1c5180d5c63bde
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2fb92682-6599-42dc-ae13-bd2ca89bd11c, version 1.0
Description : Unknown RPC service
Annotation : Fw APIs
Type : Local RPC service
Named pipe : LRPC-eb9e1c5180d5c63bde
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service
Annotation : NSI server endpoint
Type : Local RPC service
Named pipe : OLEC78F635656704CF5919BEF8848AE
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service
Annotation : NSI server endpoint
Type : Local RPC service
Named pipe : LRPC-ccb919c378b80e784b
Object UUID : 666f7270-6c69-7365-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 736e6573-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 736e6573-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 6c637067-6569-746e-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-3c4ccad02b6d68ae95
Object UUID : 24d1f7c7-76af-4f28-9ccd-7f6cb6468601
UUID : 2eb08e3e-639f-4fba-97b1-14f878961076, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : LRPC-3c4ccad02b6d68ae95
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service
Annotation : Event log TCPIP
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service
Named pipe : dhcpcsvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : dhcpcsvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : dhcpcsvc6
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000001
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc0C3841
Object UUID : 52ef130c-08fd-4388-86b3-6edf00000001
UUID : 12e65dd8-887f-41ef-91bf-8d816c42c2e7, version 1.0
Description : Unknown RPC service
Annotation : Secure Desktop LRPC interface
Type : Local RPC service
Named pipe : WMsgKRpc0C3841
Object UUID : 6d726574-7273-0076-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-e873bdd3ada3ba61b1
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc0C24C0
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WindowsShutdown
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc0C24C0
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WindowsShutdown
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : audit
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : audit
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 35221
MS08-078: Microsoft Internet Explorer Security Update (960714)
Synopsis
Arbitrary code can be executed on the remote host through the web
client.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18183
Description
The remote host is missing the IE security update 960714.
The remote version of IE is vulnerable to a memory corruption which
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008:
http://www.microsoft.com/technet/security/Bulletin/MS08-078.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2008-4844
Bugtraq ID
32721
Other references
OSVDB:50622
CWE:399
MSFT:MS08-078
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact, Metasploit (Internet Explorer Data Binding Memory Corruption)
Port cifs (445/tcp)
Plugin ID: 36153
MS09-015: Blended Threat Vulnerability in SearchPath Could Allow Elevation of Privilege (959426)
Synopsis
The remote host may allow remote code execution.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Secur32.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18215
Description
A vulnerability in the way the Windows SearchPath function locates and
opens files on the remote host could allow an attacker to execute
arbitrary remote code if he can trick a user into downloading a
specially crafted file into a specific location, such as the Windows
Desktop.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-015.mspx
Risk Factor
Medium/ CVSS Base Score: 5.8
(CVSS2#AV:N/AC:M/Au:N/C:P/I:P/A:N)
CVSS Temporal Score: 4.8(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2008-2540
Bugtraq ID
29445
Other references
OSVDB:53623
CWE:264
MSFT:MS09-015
Plugin last modification date: 2011/03/11
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 34403
MS08-058: Microsoft Internet Explorer Multiple Vulnerabilities (956390)
Synopsis
Arbitrary code can be executed on the remote host through the web client.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18137
Description
The remote host is missing the IE cumulative security update 956390.
The remote version of IE is vulnerable to several flaws which may allow an
attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003, Vista and 2008:
http://www.microsoft.com/technet/security/Bulletin/MS08-058.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:46630
OSVDB:49113
OSVDB:49114
OSVDB:49115
OSVDB:49116
OSVDB:49117
OSVDB:49118
CWE:399
MSFT:MS08-058
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port netbios-ns (137/udp)
Plugin ID: 10150
Windows NetBIOS / SMB Remote Host Information Disclosure
Synopsis
It is possible to obtain the network name of the remote host.
List of Hosts Plugin Output
192.168.1.180
The following 5 NetBIOS names have been gathered :
WIN-8BPIQBRO0CX = Computer name
TX = Workgroup / Domain name
TX = Domain Controllers
WIN-8BPIQBRO0CX = File Server Service
TX = Domain Master Browser
The remote host has the following MAC address on its adapter :
00:0c:29:9d:a1:c6
Description
The remote host listens on UDP port 137 or TCP port 445 and replies to
NetBIOS nbtscan or SMB requests.
Note that this plugin gathers information to be used in other plugins
but does not itself generate a report.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/27
Port cifs (445/tcp)
Plugin ID: 10859
Microsoft Windows SMB LsaQueryInformationPolicy Function SID Enumeration
Synopsis
It is possible to obtain the host SID for the remote host.
List of Hosts Plugin Output
192.168.1.180
The remote host SID value is :
1-5-21-3840563293-1772093868-3818923108
The value of 'RestrictAnonymous' setting is : 0
Description
By emulating the call to LsaQueryInformationPolicy(), it was possible
to obtain the host SID (Security Identifier).
The host SID can then be used to get the list of local users.
Solution
You can prevent anonymous lookups of the host SID by setting the
'RestrictAnonymous' registry setting to an appropriate value.
Refer to the 'See also' section for guidance.
Risk Factor
None
CVE
CVE-2000-1200
Bugtraq ID
959
Other references
OSVDB:715
Plugin publication date: 2002/02/13
Plugin last modification date: 2011/03/07
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 33881
MS KB953839: Cumulative Security Update of ActiveX Kill Bits
Synopsis
The remote Windows host is missing a security update containing
ActiveX kill bits.
List of Hosts Plugin Output
192.168.1.180
The kill-bit has not been set for the following control :
{B60770C2-0390-41A8-A8DE-61889888D840}
Note that Nessus did not check whether there were other kill-bits
that have not been set because 'Thorough Tests' was not enabled
when this scan was run.
Description
The remote host is missing a list of kill bits for ActiveX controls
that are known to contain vulnerabilities.
If these ActiveX controls are ever installed on the remote host,
either now or in the future, they would expose it to various security
issues.
Solution
Microsoft has released an advisory about this :
http://www.microsoft.com/technet/security/advisory/953839.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:40889
OSVDB:46232
OSVDB:46233
Plugin last modification date: 2011/03/16
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 40556
MS09-037: Vulnerabilities in Microsoft Active Template Library (ATL) Could Allow Remote Code Execution (973908)
Synopsis
Arbitrary code can be executed on the remote host through Microsoft
Active Template Library.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\Atl.dll has not been patched
Remote version : 3.5.2284.0
Should be : 3.5.2284.2
Description
The remote Windows host contains a version of the Microsoft Active
Template Library (ATL), included as part of Visual Studio or Visual
C++, that is affected by multiple vulnerabilities :
- A remote code execution issue affects the Microsoft
Video ActiveX Control due to the a flaw in the function
'CComVariant::ReadFromStream' used in the ATL header,
which fails to properly restrict untrusted data read
from a stream. (CVE-2008-0015)
- A remote code execution issue exists in the Microsoft
Active Template Library due to an error in the 'Load'
method of the 'IPersistStreamInit' interface, which
could allow calls to 'memcpy' with untrusted data.
(CVE-2008-0020)
- An issue in the ATL headers could allow an attacker to
force VariantClear to be called on a VARIANT that has
not been correctly initialized and, by supplying a
corrupt stream, to execute arbitrary code.
(CVE-2009-0901)
- Unsafe usage of 'OleLoadFromStream' could allow
instantiation of arbitrary objects which can bypass
related security policy, such as kill bits within
Internet Explorer. (CVE-2009-2493)
- A bug in the ATL header could allow reading a variant
from a stream and leaving the variant type read with
an invalid variant, which could be leveraged by an
attacker to execute arbitrary code remotely.
(CVE-2009-2494)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-037.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:55651
OSVDB:56272
OSVDB:56696
OSVDB:56698
OSVDB:56910
CWE:94
MSFT:MS09-037
Patch publication date: 2009/08/11
Plugin publication date: 2009/08/11
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact, Metasploit (Microsoft DirectShow (msvidctl.dll) MPEG-2 Memory Corruption)
Port cifs (445/tcp)
Plugin ID: 42106
MS09-050: Vulnerabilities in SMBv2 Could Allow Remote Code Execution (975517)
Synopsis
The remote SMB server can be abused to execute code remotely.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\drivers\srv2.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18331
Description
The remote Windows host contains a vulnerable SMBv2 implementation
with the following issues :
- A specially crafted SMBv2 packet can cause an
infinite loop in the Server service. A remote,
unauthenticated attacker can exploit this to cause
a denial of service. (CVE-2009-2526)
- Sending a specially crafted SMBv2 packet to the Server
service can result in code execution. A remote,
unauthenticated attacker can exploit this to take
complete control of the system. (CVE-2009-2532,
CVE-2009-3103)
Solution
Microsoft has released a set of patches for Windows Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/MS09-050.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 8.3(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:57799
OSVDB:58875
OSVDB:58876
CWE:399
MSFT:MS09-050
Patch publication date: 2009/10/13
Plugin publication date: 2009/10/13
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact, Metasploit (Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference)
Port cifs (445/tcp)
Plugin ID: 51173
MS10-101: Vulnerability in Windows Netlogon Service Could Allow Denial of Service (2207559)
Synopsis
The remote Windows host is affected by a denial of service
vulnerability in the Netlogon RPC Service.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Netlogon.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18529
Description
The remote Windows host contains a version of the NetLogon RPC
service that is affected by a denial of service vulnerability.
An attacker with administrative privileges on a machine that is joined
to the same domain as the affected domain controller could cause a
denial of service by sending a specially crafted Netlogon RPC
service.
Solution
Microsoft has released a set of patches for Windows 2003, 2008, and
2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-101.mspx
Risk Factor
Medium/ CVSS Base Score: 6.1
(CVSS2#AV:A/AC:L/Au:N/C:N/I:N/A:C)
CVE
CVE-2010-2742
Bugtraq ID
45271
Other references
OSVDB:69819
MSFT:MS10-101
Patch publication date: 2010/12/14
Plugin publication date: 2010/12/15
Plugin last modification date: 2011/03/16
Port cifs (445/tcp)
Plugin ID: 44425
MS10-015: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (977165)
Synopsis
The Windows kernel is affected by two vulnerabilities allowing a
local attacker to execute code with SYSTEM privileges.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\ntoskrnl.exe has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18377
Description
The remote Windows host is running a version of the Windows kernel
that is affected by two vulnerabilities :
- An elevation of privilege vulnerability exists in the
kernel due to the way it handles certain exceptions. An
attacker who successfully exploited this vulnerability
could run arbitrary code in kernel mode. An attacker
could then install programs, view / change / delete
data, or create new accounts with full user rights.
(CVE-2010-0232)
- An elevation of privilege vulnerability exists in the
Windows kernel due to a double free condition. An
attacker who successfully exploited this vulnerability
could run arbitrary code in kernel mode. An attacker
could then install programs, view / change / delete
data, or create new accounts with full user rights.
(CVE-2010-0233)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008 and 7
http://www.microsoft.com/technet/security/bulletin/MS10-015.mspx
Risk Factor
Medium/ CVSS Base Score: 6.2
(CVSS2#AV:L/AC:H/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 5.1(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:61854
OSVDB:62259
MSFT:MS10-015
CWE:20
Patch publication date: 2010/02/09
Plugin publication date: 2010/02/09
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact
Port (0/tcp)
Description
Solution
Risk Factor
Port cifs (445/tcp)
Plugin ID: 11011
Microsoft Windows SMB Service Detection
Synopsis
A file / print sharing service is listening on the remote host.
List of Hosts Plugin Output
192.168.1.180
A CIFS server is running on this port.
Description
The remote service understands the CIFS (Common Internet File System)
or Server Message Block (SMB) protocol, used to provide shared access
to files, printers, etc between nodes on a network.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port smb (139/tcp)
Plugin ID: 11011
Microsoft Windows SMB Service Detection
Synopsis
A file / print sharing service is listening on the remote host.
List of Hosts Plugin Output
192.168.1.180
An SMB server is running on this port.
Description
The remote service understands the CIFS (Common Internet File System)
or Server Message Block (SMB) protocol, used to provide shared access
to files, printers, etc between nodes on a network.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port cifs (445/tcp)
Plugin ID: 45516
MS10-029: Vulnerability in Windows ISATAP Component Could Allow Spoofing (978338)
Synopsis
The remote host is vulnerable to network spoofing attacks.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\drivers\Tcpip.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18427
Description
A spoofing vulnerability exists in the Microsoft Windows IPv6 stack
due to the way Windows checks the inner packet's IPv6 source address
in a tunneled ISATAP packet.
A remote attacker could exploit this by spoofing a trusted IP address,
which could be used to bypass security restrictions based on source
IP. This could also be exploited to disclose information if a
targeted host replies to the message using the spoofed IPv6 address.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS10-029.mspx
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
CVSS Temporal Score: 4.1(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2010-0812
Bugtraq ID
39352
Other references
OSVDB:63747
MSFT:MS10-029
Patch publication date: 2010/04/13
Plugin publication date: 2010/04/13
Plugin last modification date: 2011/02/23
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 33876
MS08-047: Vulnerability in IPsec Policy Processing Could Allow Information Disclosure (953733)
Synopsis
The remote host IPsec policy processing could lead to information
disclosure.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\IPsecsvc.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18094
Description
The remote version of Windows contains a bug in its IPsec
implementation which might lead to information disclosure.
Specifically, when importing a Windows Server 2003 IPsec policy into a
Windows Server 2008 domain, the system could ignore the IPsec policies
and transmit the traffic in clear text.
Solution
Microsoft has released a set of patches for Windows Vista and Server
2008 :
http://www.microsoft.com/technet/security/Bulletin/MS08-047.mspx
Risk Factor
Medium/ CVSS Base Score: 5.4
(CVSS2#AV:N/AC:H/Au:N/C:C/I:N/A:N)
CVSS Temporal Score: 4.5(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2008-2246
Bugtraq ID
30634
Other references
OSVDB:47396
CWE:200
MSFT:MS08-047
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 10456
Microsoft Windows SMB Service Enumeration
Synopsis
It is possible to enumerate remote services.
List of Hosts Plugin Output
192.168.1.180
Active Services :
Application Experience [ AeLookupSvc ]
Base Filtering Engine [ BFE ]
Background Intelligent Transfer Service [ BITS ]
Cryptographic Services [ CryptSvc ]
DCOM Server Process Launcher [ DcomLaunch ]
DFS Namespace [ Dfs ]
DFS Replication [ DFSR ]
DHCP Client [ Dhcp ]
DNS Server [ DNS ]
DNS Client [ Dnscache ]
Diagnostic Policy Service [ DPS ]
Windows Event Log [ EventLog ]
COM+ Event System [ EventSystem ]
Group Policy Client [ gpsvc ]
IKE and AuthIP IPsec Keying Modules [ IKEEXT ]
IP Helper [ iphlpsvc ]
Intersite Messaging [ IsmServ ]
Kerberos Key Distribution Center [ kdc ]
KtmRm for Distributed Transaction Coordinator [ KtmRm ]
Server [ LanmanServer ]
Workstation [ LanmanWorkstation ]
TCP/IP NetBIOS Helper [ lmhosts ]
Windows Firewall [ MpsSvc ]
Distributed Transaction Coordinator [ MSDTC ]
Netlogon [ Netlogon ]
Network Connections [ Netman ]
Network List Service [ netprofm ]
Network Location Awareness [ NlaSvc ]
Network Store Interface Service [ nsi ]
Active Directory Domain Services [ NTDS ]
File Replication Service [ NtFrs ]
Plug and Play [ PlugPlay ]
IPsec Policy Agent [ PolicyAgent ]
User Profile Service [ ProfSvc ]
Remote Access Connection Manager [ RasMan ]
Remote Registry [ RemoteRegistry ]
Remote Procedure Call (RPC) [ RpcSs ]
Security Accounts Manager [ SamSs ]
Task Scheduler [ Schedule ]
Secondary Logon [ seclogon ]
System Event Notification Service [ SENS ]
Shell Hardware Detection [ ShellHWDetection ]
Software Licensing [ slsvc ]
SL UI Notification Service [ SLUINotify ]
Splunkd [ Splunkd ]
Splunkweb [ Splunkweb ]
Print Spooler [ Spooler ]
Secure Socket Tunneling Protocol Service [ SstpSvc ]
Telephony [ TapiSrv ]
Terminal Services [ TermService ]
Windows Modules Installer [ TrustedInstaller ]
Desktop Window Manager Session Manager [ UxSms ]
Windows Time [ W32Time ]
Diagnostic System Host [ WdiSystemHost ]
Windows Error Reporting Service [ WerSvc ]
Windows Management Instrumentation [ Winmgmt ]
Windows Remote Management (WS-Management) [ WinRM ]
Windows Update [ wuauserv ]
Inactive Services :
Application Layer Gateway Service [ ALG ]
Application Information [ Appinfo ]
Application Management [ AppMgmt ]
Windows Audio Endpoint Builder [ AudioEndpointBuilder ]
Windows Audio [ Audiosrv ]
Computer Browser [ Browser ]
Certificate Propagation [ CertPropSvc ]
Microsoft .NET Framework NGEN v2.0.50727_X86 [ clr_optimization_v2.0.50727_32 ]
COM+ System Application [ COMSysApp ]
Offline Files [ CscService ]
Wired AutoConfig [ dot3svc ]
Extensible Authentication Protocol [ EapHost ]
Microsoft Fibre Channel Platform Registration Service [ FCRegSvc ]
Function Discovery Provider Host [ fdPHost ]
Function Discovery Resource Publication [ FDResPub ]
Human Interface Device Access [ hidserv ]
Health Key and Certificate Management [ hkmsvc ]
PnP-X IP Bus Enumerator [ IPBusEnum ]
CNG Key Isolation [ KeyIso ]
Link-Layer Topology Discovery Mapper [ lltdsvc ]
Multimedia Class Scheduler [ MMCSS ]
Microsoft iSCSI Initiator Service [ MSiSCSI ]
Windows Installer [ msiserver ]
Network Access Protection Agent [ napagent ]
Performance Logs & Alerts [ pla ]
Protected Storage [ ProtectedStorage ]
Remote Access Auto Connection Manager [ RasAuto ]
Routing and Remote Access [ RemoteAccess ]
Remote Procedure Call (RPC) Locator [ RpcLocator ]
Resultant Set of Policy Provider [ RSoPProv ]
Special Administration Console Helper [ sacsvr ]
Smart Card [ SCardSvr ]
Smart Card Removal Policy [ SCPolicySvc ]
Terminal Services Configuration [ SessionEnv ]
Internet Connection Sharing (ICS) [ SharedAccess ]
SNMP Trap [ SNMPTRAP ]
SSDP Discovery [ SSDPSRV ]
Microsoft Software Shadow Copy Provider [ swprv ]
Superfetch [ SysMain ]
TPM Base Services [ TBS ]
Themes [ Themes ]
Thread Ordering Server [ THREADORDER ]
Distributed Link Tracking Client [ TrkWks ]
Interactive Services Detection [ UI0Detect ]
Terminal Services UserMode Port Redirector [ UmRdpService ]
UPnP Device Host [ upnphost ]
Virtual Disk [ vds ]
Volume Shadow Copy [ VSS ]
Windows Color System [ WcsPlugInService ]
Diagnostic Service Host [ WdiServiceHost ]
Windows Event Collector [ Wecsvc ]
Problem Reports and Solutions Control Panel Support [ wercplsupport ]
WinHTTP Web Proxy Auto-Discovery Service [ WinHttpAutoProxySvc ]
WMI Performance Adapter [ wmiApSrv ]
Portable Device Enumerator Service [ WPDBusEnum ]
Windows Driver Foundation - User-mode Driver Framework [ wudfsvc ]
Description
This plugin implements the SvcOpenSCManager() and SvcEnumServices()
calls to obtain, using the SMB protocol, the list of active and
inactive services of the remote host.
An attacker may use this feature to gain better knowledge of the remote
host.
Solution
To prevent the listing of the services for being obtained, you should
either have tight login restrictions, so that only trusted users can
access your host, and/or you should filter incoming traffic to this port.
Risk Factor
Low/ CVSS Base Score: 2.6
(CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 40565
MS09-044: Vulnerabilities in Remote Desktop Connection Could Allow Remote Code Execution (970927)
Synopsis
It is possible to execute arbitrary code on the remote host.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mstscax.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18266
Description
The remote host contains a version of the Remote Desktop client with
several vulnerabilities that may allow an attacker to execute
arbirtary code on the remote host.
To exploit these vulnerabilities, an attacker would need to lure a
user of the remote host to connect to a rogue RDP server.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and Server 2008 :
http://www.microsoft.com/technet/security/bulletin/ms09-044.mspx
Risk Factor
High/ CVSS Base Score: 9.0
(CVSS2#AV:N/AC:L/Au:S/C:C/I:C/A:C)
CVSS Temporal Score: 6.7(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:56911
OSVDB:56912
MSFT:MS09-044
CWE:119
Patch publication date: 2009/08/11
Plugin publication date: 2009/08/11
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 10399
SMB Use Domain SID to Enumerate Users
Synopsis
It is possible to enumerate domain users.
List of Hosts Plugin Output
192.168.1.180
- Administrator (id 500, Administrator account)
- Guest (id 501, Guest account)
- krbtgt (id 502, Kerberos account)
- WIN-8BPIQBRO0CX$ (id 1000)
- DnsAdmins (id 1101)
- DnsUpdateProxy (id 1102)
- EXCHANGE$ (id 1103)
- Exchange Domain Servers (id 1104)
- Exchange Enterprise Servers (id 1105)
- 249E6E5E-02B7-46F0-B (id 1106)
- scorebot (id 1107)
- pcurrie (id 1108)
- dtouart (id 1109)
- sgieber (id 1110)
- fcrumb (id 1111)
- cvukelj (id 1112)
- aballs (id 1113)
- idepierre (id 1114)
- mmcleroy (id 1115)
- kmalavet (id 1116)
- tjank (id 1117)
- fdraxler (id 1118)
- cpaskell (id 1119)
- mcosgrave (id 1120)
- deichert (id 1121)
- lmicha (id 1122)
- kbarroso (id 1123)
- vroutte (id 1124)
- rschummer (id 1125)
- lfollett (id 1126)
- pcoladonato (id 1127)
- gdelreal (id 1128)
- lthroneberry (id 1129)
- lmccarn (id 1130)
- mlutjen (id 1131)
- vkonkel (id 1132)
- asponsler (id 1133)
- metzkorn (id 1134)
- tmcquirter (id 1135)
- fconcannon (id 1136)
- lyouker (id 1137)
- mamini (id 1138)
- lrosko (id 1139)
- dcolligan (id 1140)
- fprok (id 1141)
- vnickleberry (id 1142)
- afeurtado (id 1143)
- rgerczak (id 1144)
- hvanhekken (id 1145)
- cdoudna (id 1146)
- sbessent (id 1147)
- wlorimor (id 1148)
- hkarmazyn (id 1149)
- sdechambeau (id 1150)
- lsotelo (id 1151)
- aterris (id 1152)
- mkanta (id 1153)
- atopacio (id 1154)
- gkamphoefner (id 1155)
- abergmeier (id 1156)
- ksorrentino (id 1157)
- lgiacchino (id 1158)
- mmajorga (id 1159)
- fcosby (id 1160)
- lsimcic (id 1161)
- ltabor (id 1162)
- lschweickert (id 1163)
- dbrueckman (id 1164)
- scalverley (id 1165)
- tstansfield (id 1166)
- fpassarelli (id 1167)
- tkreinhagen (id 1168)
- dkoenigsberg (id 1169)
- asteltenpohl (id 1170)
- agoonen (id 1171)
- smockler (id 1172)
- npacheco (id 1173)
- ycambell (id 1174)
- schesher (id 1175)
- mwinegardner (id 1176)
- spoissant (id 1177)
- jlicerio (id 1178)
- murman (id 1179)
- cvrazel (id 1180)
- czoelle (id 1181)
- apaulshock (id 1182)
- gbartus (id 1183)
- edorrough (id 1184)
- jdifiora (id 1185)
- jteno (id 1186)
- tmichel (id 1187)
- bbegan (id 1188)
- aconelli (id 1189)
- ceuton (id 1190)
- sadelmann (id 1191)
- slook (id 1192)
- jhoffpavir (id 1193)
- nholsing (id 1194)
- mscouller (id 1195)
- jbroadwater (id 1196)
- ebrentlinger (id 1197)
- ablaske (id 1198)
- iguzon (id 1199)
- smceldowney (id 1200)
Note that, in addition to the Administrator, Guest, and Kerberos
accounts, Nessus has enumerated only those domain users with IDs
between 1000 and 1200. To use a different range, edit the scan policy
and change the 'Start UID' and/or 'End UID' preferences for this
plugin, then re-run the scan.
Description
Using the host SID, it is possible to enumerate the domain
users on the remote Windows system.
Solution
n/a
Risk Factor
None
CVE
CVE-2000-1200
Bugtraq ID
959
Other references
OSVDB:714
Plugin publication date: 2000/05/09
Plugin last modification date: 2011/03/07
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 51172
MS10-100: Vulnerability in Consent User Interface Could Allow Elevation of Privilege (2442962)
Synopsis
A Windows component on the remote host is affected by a vulnerability
that could allow escalation of privileges.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\Consent.exe has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18539
Description
The Consent User Interface (UI) component of the remote Windows host
does not properly process a registry key that has been set to a
specific value.
An attacker who can log on locally to the affected system and has the
'Impersonate a client after authentication' user right
(SeImpersonatePrivilege) can exploit this to run arbitrary code with
LocalSystem privileges.
Solution
Microsoft has released a set of patches for Windows Vista, 2008, 7,
and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-100.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVE
CVE-2010-3961
Bugtraq ID
45318
Other references
OSVDB:69824
MSFT:MS10-100
Patch publication date: 2010/12/14
Plugin publication date: 2010/12/15
Plugin last modification date: 2011/03/16
Port cifs (445/tcp)
Plugin ID: 43064
MS09-072: Cumulative Security Update for Internet Explorer (976325)
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18349
Description
The remote host is missing IE Security Update 976325.
The remote version of IE is affected by several vulnerabilities that
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, and Windows 7 :
http://www.microsoft.com/technet/security/Bulletin/MS09-072.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
Other references
OSVDB:56698
OSVDB:60490
OSVDB:60837
OSVDB:60838
OSVDB:60839
CWE:399
MSFT:MS09-072
Patch publication date: 2009/12/08
Plugin publication date: 2009/12/08
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact, Metasploit (Internet Explorer Style getElementsByTagName Memory Corruption)
Port (64559/udp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'dns.exe' is listening on this port (pid 1676).
This process 'dns.exe' (pid 1676) is hosting the following Windows services :
DNS (@%systemroot%\system32\dns.exe,-49157)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port dce-rpc (49177/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'services.exe' is listening on this port (pid 560).
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port dce-rpc (49176/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'dns.exe' is listening on this port (pid 1676).
This process 'dns.exe' (pid 1676) is hosting the following Windows services :
DNS (@%systemroot%\system32\dns.exe,-49157)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port dce-rpc (49163/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'svchost.exe' is listening on this port (pid 1848).
This process 'svchost.exe' (pid 1848) is hosting the following Windows services :
PolicyAgent (@%SystemRoot%\System32\polstore.dll,-5010)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port dce-rpc (49161/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'ntfrs.exe' is listening on this port (pid 1764).
This process 'ntfrs.exe' (pid 1764) is hosting the following Windows services :
NtFrs (File Replication Service)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port dce-rpc (49158/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'lsass.exe' is listening on this port (pid 572).
This process 'lsass.exe' (pid 572) is hosting the following Windows services :
kdc (@%SystemRoot%\System32\kdcsvc.dll,-1)
Netlogon (@%SystemRoot%\System32\netlogon.dll,-102)
NTDS (@%SystemRoot%\System32\ntdsmsg.dll,-1)
SamSs (@%SystemRoot%\system32\samsrv.dll,-1)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port ncacn_http (49157/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'lsass.exe' is listening on this port (pid 572).
This process 'lsass.exe' (pid 572) is hosting the following Windows services :
kdc (@%SystemRoot%\System32\kdcsvc.dll,-1)
Netlogon (@%SystemRoot%\System32\netlogon.dll,-102)
NTDS (@%SystemRoot%\System32\ntdsmsg.dll,-1)
SamSs (@%SystemRoot%\system32\samsrv.dll,-1)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port dce-rpc (49155/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'lsass.exe' is listening on this port (pid 572).
This process 'lsass.exe' (pid 572) is hosting the following Windows services :
kdc (@%SystemRoot%\System32\kdcsvc.dll,-1)
Netlogon (@%SystemRoot%\System32\netlogon.dll,-102)
NTDS (@%SystemRoot%\System32\ntdsmsg.dll,-1)
SamSs (@%SystemRoot%\system32\samsrv.dll,-1)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port dce-rpc (49154/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'svchost.exe' is listening on this port (pid 1032).
This process 'svchost.exe' (pid 1032) is hosting the following Windows services :
AeLookupSvc (@%SystemRoot%\system32\aelupsvc.dll,-1)
BITS (@%SystemRoot%\system32\qmgr.dll,-1000)
IKEEXT (@%SystemRoot%\system32\ikeext.dll,-501)
iphlpsvc (@%SystemRoot%\system32\iphlpsvc.dll,-200)
LanmanServer (@%systemroot%\system32\srvsvc.dll,-100)
ProfSvc (@%systemroot%\system32\profsvc.dll,-300)
RasMan (@%Systemroot%\system32\rasmans.dll,-200)
Schedule (@%SystemRoot%\system32\schedsvc.dll,-100)
seclogon (@%SystemRoot%\system32\seclogon.dll,-7001)
SENS (@%SystemRoot%\system32\Sens.dll,-200)
ShellHWDetection (@%SystemRoot%\System32\shsvcs.dll,-12288)
Winmgmt (@%Systemroot%\system32\wbem\wmisvc.dll,-205)
wuauserv (@%systemroot%\system32\wuaueng.dll,-105)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port dce-rpc (49153/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'svchost.exe' is listening on this port (pid 904).
This process 'svchost.exe' (pid 904) is hosting the following Windows services :
Dhcp (@%SystemRoot%\system32\dhcpcsvc.dll,-100)
EventLog (@%SystemRoot%\system32\wevtsvc.dll,-200)
lmhosts (@%SystemRoot%\system32\lmhsvc.dll,-101)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port dce-rpc (49152/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'wininit.exe' is listening on this port (pid 476).
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port www (8089/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'splunkd.exe' is listening on this port (pid 1956).
This process 'splunkd.exe' (pid 1956) is hosting the following Windows services :
Splunkd (Splunkd)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port www (8000/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'PythonService.exe' is listening on this port (pid 2044).
This process 'PythonService.exe' (pid 2044) is hosting the following Windows services :
Splunkweb (Splunkweb)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (5355/udp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'svchost.exe' is listening on this port (pid 1204).
This process 'svchost.exe' (pid 1204) is hosting the following Windows services :
CryptSvc (@%SystemRoot%\system32\cryptsvc.dll,-1001)
Dnscache (@%SystemRoot%\System32\dnsapi.dll,-101)
KtmRm (@comres.dll,-2946)
NlaSvc (@%SystemRoot%\System32\nlasvc.dll,-1)
TermService (@%SystemRoot%\System32\termsrv.dll,-268)
WinRM (@%Systemroot%\system32\wsmsvc.dll,-101)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (4500/udp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'svchost.exe' is listening on this port (pid 1032).
This process 'svchost.exe' (pid 1032) is hosting the following Windows services :
AeLookupSvc (@%SystemRoot%\system32\aelupsvc.dll,-1)
BITS (@%SystemRoot%\system32\qmgr.dll,-1000)
IKEEXT (@%SystemRoot%\system32\ikeext.dll,-501)
iphlpsvc (@%SystemRoot%\system32\iphlpsvc.dll,-200)
LanmanServer (@%systemroot%\system32\srvsvc.dll,-100)
ProfSvc (@%systemroot%\system32\profsvc.dll,-300)
RasMan (@%Systemroot%\system32\rasmans.dll,-200)
Schedule (@%SystemRoot%\system32\schedsvc.dll,-100)
seclogon (@%SystemRoot%\system32\seclogon.dll,-7001)
SENS (@%SystemRoot%\system32\Sens.dll,-200)
ShellHWDetection (@%SystemRoot%\System32\shsvcs.dll,-12288)
Winmgmt (@%Systemroot%\system32\wbem\wmisvc.dll,-205)
wuauserv (@%systemroot%\system32\wuaueng.dll,-105)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (3269/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'lsass.exe' is listening on this port (pid 572).
This process 'lsass.exe' (pid 572) is hosting the following Windows services :
kdc (@%SystemRoot%\System32\kdcsvc.dll,-1)
Netlogon (@%SystemRoot%\System32\netlogon.dll,-102)
NTDS (@%SystemRoot%\System32\ntdsmsg.dll,-1)
SamSs (@%SystemRoot%\system32\samsrv.dll,-1)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (3268/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'lsass.exe' is listening on this port (pid 572).
This process 'lsass.exe' (pid 572) is hosting the following Windows services :
kdc (@%SystemRoot%\System32\kdcsvc.dll,-1)
Netlogon (@%SystemRoot%\System32\netlogon.dll,-102)
NTDS (@%SystemRoot%\System32\ntdsmsg.dll,-1)
SamSs (@%SystemRoot%\system32\samsrv.dll,-1)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (636/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'lsass.exe' is listening on this port (pid 572).
This process 'lsass.exe' (pid 572) is hosting the following Windows services :
kdc (@%SystemRoot%\System32\kdcsvc.dll,-1)
Netlogon (@%SystemRoot%\System32\netlogon.dll,-102)
NTDS (@%SystemRoot%\System32\ntdsmsg.dll,-1)
SamSs (@%SystemRoot%\system32\samsrv.dll,-1)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port http-rpc-epmap (593/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'svchost.exe' is listening on this port (pid 868).
This process 'svchost.exe' (pid 868) is hosting the following Windows services :
RpcSs (@oleres.dll,-5010)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (500/udp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'svchost.exe' is listening on this port (pid 1032).
This process 'svchost.exe' (pid 1032) is hosting the following Windows services :
AeLookupSvc (@%SystemRoot%\system32\aelupsvc.dll,-1)
BITS (@%SystemRoot%\system32\qmgr.dll,-1000)
IKEEXT (@%SystemRoot%\system32\ikeext.dll,-501)
iphlpsvc (@%SystemRoot%\system32\iphlpsvc.dll,-200)
LanmanServer (@%systemroot%\system32\srvsvc.dll,-100)
ProfSvc (@%systemroot%\system32\profsvc.dll,-300)
RasMan (@%Systemroot%\system32\rasmans.dll,-200)
Schedule (@%SystemRoot%\system32\schedsvc.dll,-100)
seclogon (@%SystemRoot%\system32\seclogon.dll,-7001)
SENS (@%SystemRoot%\system32\Sens.dll,-200)
ShellHWDetection (@%SystemRoot%\System32\shsvcs.dll,-12288)
Winmgmt (@%Systemroot%\system32\wbem\wmisvc.dll,-205)
wuauserv (@%systemroot%\system32\wuaueng.dll,-105)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (464/udp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'lsass.exe' is listening on this port (pid 572).
This process 'lsass.exe' (pid 572) is hosting the following Windows services :
kdc (@%SystemRoot%\System32\kdcsvc.dll,-1)
Netlogon (@%SystemRoot%\System32\netlogon.dll,-102)
NTDS (@%SystemRoot%\System32\ntdsmsg.dll,-1)
SamSs (@%SystemRoot%\system32\samsrv.dll,-1)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port cifs (445/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'System' is listening on this port (pid 4).
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port ldap (389/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'lsass.exe' is listening on this port (pid 572).
This process 'lsass.exe' (pid 572) is hosting the following Windows services :
kdc (@%SystemRoot%\System32\kdcsvc.dll,-1)
Netlogon (@%SystemRoot%\System32\netlogon.dll,-102)
NTDS (@%SystemRoot%\System32\ntdsmsg.dll,-1)
SamSs (@%SystemRoot%\system32\samsrv.dll,-1)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port smb (139/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'System' is listening on this port (pid 4).
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (138/udp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'System' is listening on this port (pid 4).
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port netbios-ns (137/udp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'System' is listening on this port (pid 4).
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port epmap (135/tcp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'svchost.exe' is listening on this port (pid 868).
This process 'svchost.exe' (pid 868) is hosting the following Windows services :
RpcSs (@oleres.dll,-5010)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port ntp (123/udp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'svchost.exe' is listening on this port (pid 1088).
This process 'svchost.exe' (pid 1088) is hosting the following Windows services :
EventSystem (@comres.dll,-2450)
LanmanWorkstation (@%systemroot%\system32\wkssvc.dll,-100)
netprofm (@%SystemRoot%\system32\netprof.dll,-246)
nsi (@%SystemRoot%\system32\nsisvc.dll,-200)
SLUINotify (@%SystemRoot%\system32\SLUINotify.dll,-103)
SstpSvc (@%SystemRoot%\system32\sstpsvc.dll,-200)
W32Time (@%SystemRoot%\system32\w32time.dll,-200)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (88/udp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'lsass.exe' is listening on this port (pid 572).
This process 'lsass.exe' (pid 572) is hosting the following Windows services :
kdc (@%SystemRoot%\System32\kdcsvc.dll,-1)
Netlogon (@%SystemRoot%\System32\netlogon.dll,-102)
NTDS (@%SystemRoot%\System32\ntdsmsg.dll,-1)
SamSs (@%SystemRoot%\system32\samsrv.dll,-1)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (53/udp)
Plugin ID: 34252
Microsoft Windows Remote Listeners Enumeration (WMI)
Synopsis
It is possible to obtain the names of processes listening on the
remote UDP and TCP ports.
List of Hosts Plugin Output
192.168.1.180
The Win32 process 'dns.exe' is listening on this port (pid 1676).
This process 'dns.exe' (pid 1676) is hosting the following Windows services :
DNS (@%systemroot%\system32\dns.exe,-49157)
Description
This script uses WMI to list the processes running on the remote host
and listening on TCP / UDP ports.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port (0/tcp)
Plugin ID: 34096
BIOS Version (WMI)
Synopsis
The BIOS version could be read.
List of Hosts Plugin Output
192.168.1.180
Vendor : Phoenix Technologies LTD
Version : 6.00
Release date : 20091231000000.000000+000
Description
It is possible to get information about the BIOS vendor and its
version via the host's WMI interface.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port cifs (445/tcp)
Plugin ID: 46312
MS10-030: Vulnerability in Outlook Express and Windows Mail Could Allow Remote Code Execution (978542)
Synopsis
An integer overflow vulnerability is present on the remote host due
to an issue in Outlook Express / Windows Mail.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Inetcomm.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18416
Description
The remote host is running a version of Microsoft Outlook Express /
Windows Mail that contains a flaw which might be used to cause an
integer overflow, resulting in remote code execution.
To exploit this flaw, an attacker would need a victim to connect to a
mail server under their control and send malicious responses to the
victim's email client.
Solution
Microsoft has released a set of patches for Outlook Express and
Windows Mail :
http://www.microsoft.com/technet/security/bulletin/ms10-030.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.3(CVSS2#E:POC/RL:OF/RC:C)
CVE
CVE-2010-0816
Bugtraq ID
39927
Other references
OSVDB:64530
MSFT:MS10-030
Patch publication date: 2010/05/11
Plugin publication date: 2010/05/11
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 42118
MS09-062: Vulnerabilities in GDI+ Could Allow Remote Code Execution (957488)
Synopsis
Arbitrary code can be executed on the remote host through the
Microsoft GDI rendering engine.
List of Hosts Plugin Output
192.168.1.180
None of the versions of 'gdiplus.dll' under C:\Windows\WinSxS
have been patched.
Description
The remote host is running a version of Windows that is affected by
multiple buffer overflow vulnerabilities when viewing TIFF, PNG, BMP,
and Office files, which may allow an attacker to execute arbitrary
code on the remote host. Additionally, there is a GDI+ .NET API
vulnerability that allows a malicious .NET application to gain
unmanaged code execution privileges.
To exploit these flaws, an attacker would need to send a malformed
image file to a user on the remote host and wait for them to open it
using an affected Microsoft application.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, IE, .NET Framework, Office, SQL Server, Developer Tools, and
Forefront :
http://www.microsoft.com/technet/security/Bulletin/MS09-062.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2009-2500
CVE-2009-2501
CVE-2009-2502
CVE-2009-2503
CVE-2009-2504
CVE-2009-2518
CVE-2009-2528
CVE-2009-3126
Other references
OSVDB:58863
OSVDB:58864
OSVDB:58865
OSVDB:58866
OSVDB:58867
OSVDB:58868
OSVDB:58869
OSVDB:58870
CWE:189
MSFT:MS09-062
Patch publication date: 2009/10/13
Plugin publication date: 2009/10/15
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 51168
MS10-096: Vulnerability in Windows Address Book Could Allow Remote Code Execution (2423089)
Synopsis
Arbitrary code can be executed on the remote host through
Windows Address Book.
List of Hosts Plugin Output
192.168.1.180
- C:\Program Files\Windows Mail\Wab.exe has not been patched
Remote version : 6.0.6000.16386
Should be : 6.0.6001.18535
Description
The remote Windows host contains a version of Windows Address Book
that incorrectly restricts the path used for loading external
libraries.
If an attacker can trick a user on the affected system into opening a
specially crafted Windows Address Book file located in the same
network directory as a specially crafted dynamic link library (DLL)
file, he may be able to leverage this issue to execute arbitrary code
subject to the user's privileges.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-096.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 8.4(CVSS2#E:F/RL:W/RC:ND)
CVE
CVE-2010-3147
Bugtraq ID
42648
Other references
OSVDB:67553
MSFT:MS10-096
Patch publication date: 2010/12/14
Plugin publication date: 2010/12/15
Plugin last modification date: 2011/03/18
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 35822
MS09-006: Vulnerabilities in Windows Kernel Could Allow Remote Code Execution (958690)
Synopsis
It is possible to execute arbitrary code on the remote host.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Win32k.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18211
Description
The remote host contains a version of the Windows kernel that is
affected by vulnerabilities :
- A remote code execution vulnerability exists due to
improper validation of input passed from user mode
through the kernel component of GDI. Successful
exploitation requires that a user on the affected host
view a specially crafted EMF or WMF image file, perhaps
by being tricked into visiting a malicious web site,
and could lead to a complete system compromise.
(CVE-2009-0081)
- A local privilege escalation vulnerability exists due to
the way the kernel validates handles. (CVE-2009-0082)
- A local privilege escalation vulnerability exists due to
improper handling of a specially crafted invalid pointer.
(CVE-2009-0083)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-006.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:52522
OSVDB:52523
OSVDB:52524
CWE:20
MSFT:MS09-006
Plugin last modification date: 2011/03/15
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port (0/tcp)
Plugin ID: 24270
Computer Manufacturer Information (WMI)
Synopsis
It is possible to obtain the name of the remote computer manufacturer.
List of Hosts Plugin Output
192.168.1.180
Computer Manufacturer : VMware, Inc.
Computer Model : VMware Virtual Platform
Computer SerialNumber : VMware-56 4d b0 ad 12 c6 9b f3-49 9a 05 61 c8 9d a1 c6
Computer Type : Other
Computer Memory : 1026 MB
Description
By making certain WMI queries, it is possible to obtain the model of
the remote computer as well as the name of its manufacturer and its
serial number.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port cifs (445/tcp)
Plugin ID: 26920
Microsoft Windows SMB NULL Session Authentication
Synopsis
It is possible to log into the remote Windows host with a NULL
session.
List of Hosts
192.168.1.180
Description
The remote host is running Microsoft Windows, and it was possible to
log into it using a NULL session (i.e., with no login or password). An
unauthenticated remote attacker can leverage this issue to get
information about the remote host.
Solution
n/a
Risk Factor
None
Bugtraq ID
494
Other references
OSVDB:299
Plugin publication date: 2007/10/04
Plugin last modification date: 2011/03/28
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 34408
MS08-063: Microsoft Windows SMB File Name Handling Remote Underflow (957095)
Synopsis
It is possible to crash the remote host due to a flaw in the 'server'
service.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\drivers\Srv.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18130
Description
The remote host contains a memory corruption vulnerability in the
'Server' service that may allow an attacker to perform a denial of
service against the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms08-063.mspx
Risk Factor
High/ CVSS Base Score: 7.5
(CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P)
CVSS Temporal Score: 6.2(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2008-4038
Bugtraq ID
31647
Other references
OSVDB:49057
CWE:119
MSFT:MS08-063
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 39344
MS09-022: Vulnerabilities in Windows Print Spooler Could Allow Remote Code Execution (961501)
Synopsis
Arbitrary code can be executed on the remote host due to a flaw in the
Spooler service.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Localspl.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18247
Description
The version of the Print Spooler service on the remote Windows host is
affected by one or more of the following vulnerabilities :
- A buffer overflow vulnerability could allow an
unauthenticated remote attacker to execute arbitrary
code with SYSTEM privileges. (CVE-2009-0228)
- Using a specially crafted separator page, a local user
can read or print any file on the affected system.
(CVE-2009-0229)
- Using a specially crafted RPC message, a user who has
the 'Manage Printer' privilege can have the spooler
load an arbitrary DLL and thereby execute arbitrary
code with elevated privileges. (CVE-2009-0230)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-022.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 8.3(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:54932
OSVDB:54933
OSVDB:54934
CWE:264
MSFT:MS09-022
Plugin last modification date: 2011/02/25
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact
Port cifs (445/tcp)
Plugin ID: 43865
MS10-001: Vulnerability in the Embedded OpenType Font Engine Could Allow Remote Code Execution (972270)
Synopsis
It is possible to execute arbitrary code on the remote Windows host
using the Embedded OpenType Font Engine.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\T2embed.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18344
Description
The remote Windows host contains a version of the Embedded OpenType
(EOT) Font Engine that is affected by an integer overflow
vulnerability in the 'LZCOMP' decompressor when decompressing a
specially crafted font.
If an attacker can trick a user on the affected system into viewing
content rendered in a specially crafted EOT font, he may be able to
leverage this issue to execute arbitrary code subject to the user's
privileges.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, and Windows 7 :
http://www.microsoft.com/technet/security/Bulletin/MS10-001.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.3(CVSS2#E:POC/RL:OF/RC:C)
CVE
CVE-2010-0018
Bugtraq ID
37671
Other references
OSVDB:61651
MSFT:MS10-001
CWE:189
Patch publication date: 2010/01/12
Plugin publication date: 2010/01/12
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 10396
Microsoft Windows SMB Shares Access
Synopsis
It is possible to access a network share.
List of Hosts Plugin Output
192.168.1.180
The following shares can be accessed as administrator :
- ADMIN$ - (readable,writable)
+ Content of this share :
..
AppPatch
assembly
bfsvc.exe
Boot
bootstat.dat
Branding
Cursors
Debug
DigitalLocker
Downloaded Program Files
DtcInstall.log
en-US
explorer.exe
Fonts
fveupdate.exe
Globalization
Help
HelpPane.exe
hh.exe
IME
inf
Installer
L2Schemas
LiveKernelReports
Logs
Media
mib.bin
Microsoft.NET
ModemLogs
MSAgent
msdfmap.ini
nap
NETLOGON.CHG
NTDS
ntfrs
Offline Web Pages
Panther
PLA
PolicyDefinitions
Provisioning
regedit.exe
Registration
RemotePackages
rescache
Resources
SchCache
schemas
security
ServerStandard.xml
ServiceProfiles
servicing
Setup
setupact.log
SETUPAPI.LOG
setuperr.log
SoftwareDistribution
Speech
SysMsiCache
system
system.ini
System32
SYSVOL
tapi
Tasks
Temp
tracing
TSSysprep.log
Users
Web
win.ini
WindowsMobile
WindowsShell.Manifest
WindowsUpdate.log
winhelp.exe
winhlp32.exe
winsxs
_default.pif
- C$ - (readable,writable)
+ Content of this share :
.rnd
autoexec.bat
Boot
bootmgr
BOOTSECT.BAK
config.sys
Documents and Settings
hiberfil.sys
pagefile.sys
PerfLogs
Program Files
ProgramData
System Volume Information
Users
Windows
- NETLOGON - (readable,writable)
+ Content of this share :
..
- SYSVOL - (readable,writable)
+ Content of this share :
..
tx.hec.net
Description
The remote has one or more Windows shares that can be accessed through
the network with the given credentials.
Depending on the share rights, it may allow an attacker to read /
write confidential data.
Solution
To restrict access under Windows, open Explorer, do a right click
on each share, go to the 'sharing' tab, and click on 'permissions'.
Risk Factor
None
Plugin last modification date: 2011/03/27
Port cifs (445/tcp)
Plugin ID: 48285
MS10-048: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2160329)
Synopsis
The Windows kernel is affected by several vulnerabilities that could
allow escalation of privileges.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Win32k.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18496
Description
The remote Windows host is running a version of the Windows kernel
that is affected by one or more of the following vulnerabilities :
- Improper valiation of an argument passed to a system
call can result in a denial of service. (CVE-2010-1887)
- Certain unspecified exceptions are not properly
handled which could result in arbitrary code execution
in the kernel. (CVE-2010-1894)
- Memory is not properly allocated when making a copy
from user mode, which could result in an elevation of
privileges. (CVE-2010-1895)
- Unspecified input from user mode is not properly
validated, which could result in arbitrary code
execution in the kernel. (CVE-2010-1896)
- Unspecified parameters are not properly validated
when creating a new window, which could result
in arbitrary code execution in the kernel.
(CVE-2010-1897)
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-048.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.0(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:66979
OSVDB:66980
OSVDB:66981
OSVDB:66982
OSVDB:66983
MSFT:MS10-048
Patch publication date: 2010/08/10
Plugin publication date: 2010/08/11
Plugin last modification date: 2011/04/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact
Port cifs (445/tcp)
Plugin ID: 44422
MS10-012: Vulnerabilities in SMB Could Allow Remote Code Execution (971468)
Synopsis
It is possible to execute arbitrary code on the remote Windows host
due to flaws in its SMB implementation.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\drivers\Srv.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18381
Description
The remote host is affected by several vulnerabilities in the SMB
server that may allow an attacker to execute arbitrary code or perform
a denial of service against the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-012.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.8(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:62253
OSVDB:62254
OSVDB:62255
OSVDB:62256
MSFT:MS10-012
CWE:310
CWE:264
Patch publication date: 2010/02/09
Plugin publication date: 2010/02/09
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port (0/tcp)
Plugin ID: 10902
Microsoft Windows 'Administrators' Group User List
Synopsis
There is at least one user in the 'Administrators' group.
List of Hosts Plugin Output
192.168.1.180
The following users are members of the 'Administrators' group :
- TX\Administrator (User)
- TX\Enterprise Admins (Group)
- TX\Domain Admins (Group)
Description
Using the supplied credentials, it is possible to extract the member
list of the 'Administrators' group. Members of this group have
complete access to the remote system.
Solution
Verify that each member of the group should have this type of access.
Risk Factor
None
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 47556
MS10-012: Vulnerabilities in SMB Could Allow Remote Code Execution (971468) (uncredentialed check)
Synopsis
It is possible to execute arbitrary code on the remote Windows host
due to flaws in its SMB implementation.
List of Hosts
192.168.1.180
Description
The remote host is affected by several vulnerabilities in the SMB
server that may allow an attacker to execute arbitrary code or perform
a denial of service against the remote host.
These vulnerabilities depend on access to a shared drive, but do not
necessarily require credentials.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-012.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.8(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:62253
OSVDB:62254
OSVDB:62255
OSVDB:62256
CWE:310
CWE:264
MSFT:MS10-012
Patch publication date: 2010/02/09
Plugin publication date: 2010/09/13
Plugin last modification date: 2011/03/21
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 39792
MS09-029: Vulnerabilities in the Embedded OpenType Font Engine Could Allow Remote Code Execution (961371)
Synopsis
It is possible to execute arbitrary code on the remote Windows host
using the Embedded OpenType Font Engine.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\T2embed.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18272
Description
The remote Windows host contains a version of the Embedded OpenType
(EOT) Font Engine that is affected by multiple buffer overflow
vulnerabilities due to the way the EOT font technology parses name
tables in specially crafted embedded fonts.
If an attacker can trick a user on the affected system into viewing
content rendered in a specially crafted EOT font, he may be able to
leverage these issues to execute arbitrary code subject to the user's
privileges.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-029.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:55842
OSVDB:55843
CWE:189
MSFT:MS09-029
Patch publication date: 2009/07/14
Plugin publication date: 2009/07/14
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 35072
MS08-073: Microsoft Internet Explorer Multiple Vulnerabilities (958215)
Synopsis
Arbitrary code can be executed on the remote host through the web client.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18157
Description
The remote host is missing the IE cumulative security update 958215.
The remote version of IE is vulnerable to several flaws which may allow an
attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003, Vista and 2008:
http://www.microsoft.com/technet/security/Bulletin/MS08-073.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.3(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:50610
OSVDB:50611
OSVDB:50612
OSVDB:50613
CWE:399
MSFT:MS08-073
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 49953
MS10-076: Vulnerability in the Embedded OpenType Font Engine Could Allow Remote Code Execution (982132)
Synopsis
It is possible to execute arbitrary code on the remote Windows host
using the Embedded OpenType Font Engine.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\T2embed.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18520
Description
The remote Windows host contains a version of the Embedded OpenType
(EOT) Font Engine that is affected by an integer overflow
vulnerability when parsing certain tables within specially crafted
files and content containing embedded fonts.
If an attacker can trick a user on the affected system into viewing
content rendered in a specially crafted EOT font, he may be able to
leverage this issue to execute arbitrary code subject to the user's
privileges.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-076.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2010-1883
Bugtraq ID
43775
Other references
OSVDB:68553
MSFT:MS10-076
Patch publication date: 2010/10/12
Plugin publication date: 2010/10/13
Plugin last modification date: 2011/03/24
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 33133
MS08-031: Cumulative Security Update for Internet Explorer (950759)
Synopsis
Arbitrary code can be executed on the remote host through the web
client.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18063
Description
The remote host is missing the IE cumulative security update 950759.
The remote version of IE is vulnerable to several flaws which may
allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS08-031.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:43606
OSVDB:46083
OSVDB:46084
CWE:20
MSFT:MS08-031
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 44418
MS10-008: Cumulative Security Update of ActiveX Kill Bits (978262)
Synopsis
The remote Windows host is missing an update that disables selected
ActiveX controls.
List of Hosts Plugin Output
192.168.1.180
{E0ECA9C3-D669-4EF4-8231-00724ED9288F}
Description
The Microsoft Data Analyzer ActiveX control has a remote code
execution vulnerability. The system may also have one or more
vulnerable third-party ActiveX controls installed.
A remote attacker could exploit these issues by tricking a user into
requesting a maliciously crafted web page, resulting in arbitrary code
execution.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, and 7 :
http://www.microsoft.com/technet/security/Bulletin/MS10-008.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 8.1(CVSS2#E:H/RL:OF/RC:C)
Other references
OSVDB:54137
OSVDB:62246
OSVDB:62267
OSVDB:62372
OSVDB:62438
MSFT:MS10-008
CWE:94
Patch publication date: 2010/02/09
Plugin publication date: 2010/02/09
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 49695
MS10-070: Vulnerability in ASP.NET Could Allow Information Disclosure (2418042)
Synopsis
The version of the .NET framework installed on the remote host has an
information disclosure vulnerability.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\Microsoft.NET\Framework\v2.0.50727\System.web.dll has not been patched
Remote version : 2.0.50727.1434
Should be : 2.0.50727.1887
Description
There is an information disclosure vulnerability in ASP.NET, part of
the .NET framework. Information can be leaked due to improper error
handling during encryption padding.
A remote attacker could exploit this to decrypt and modify an ASP.NET
application's server-encrypted data. In .NET Framework 3.5 SP1 and
above, an attacker could exploit this to download any file within the
ASP.NET application, including web.config.
Solution
Microsoft has released a set of patches for the .NET Framework on
Windows XP, 2003, Vista, 2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-070.mspx
Risk Factor
Medium/ CVSS Base Score: 6.4
(CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N)
CVSS Temporal Score: 5.3(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2010-3332
Bugtraq ID
43316
Other references
OSVDB:68127
MSFT:MS10-070
Patch publication date: 2010/09/28
Plugin publication date: 2010/09/28
Plugin last modification date: 2011/03/31
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 40560
MS09-041: Vulnerability in Workstation Service Could Allow Elevation of Privilege (971657)
Synopsis
Users can elevate their privileges on the remote host.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\wkssvc.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18270
Description
The remote host contains a version of the 'Workstation' service that
contains a memory corruption vulnerability that might allow an
attacker with valid credentials to execute arbitrary code on the
remote host.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista and
Server 2008 :
http://www.microsoft.com/technet/security/bulletin/ms09-041.mspx
Risk Factor
High/ CVSS Base Score: 9.0
(CVSS2#AV:N/AC:L/Au:S/C:C/I:C/A:C)
CVSS Temporal Score: 7.4(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2009-1544
Bugtraq ID
35972
Other references
OSVDB:56902
CWE:399
MSFT:MS09-041
Plugin publication date: 2009/08/11
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 42437
MS09-063: Vulnerability in Web Services on Devices API Could Allow Remote Code Execution (973565)
Synopsis
Arbitrary code can be executed on the remote host through the Web
Services for Devices API (WSDAPI).
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\wsdapi.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18306
Description
The remote Windows host is running a vulnerable version of WSDAPI.
Sending the affected service a packet with a specially crafted header
can result in arbitrary code execution. An attacker on the same
subnet could exploit this to take complete control of the system.
Solution
Microsoft has released a set of patches for Windows Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms09-063.mspx
Risk Factor
High/ CVSS Base Score: 8.3
(CVSS2#AV:A/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.5(CVSS2#E:POC/RL:OF/RC:C)
CVE
CVE-2009-2512
Bugtraq ID
36919
Other references
OSVDB:59865
CWE:94
MSFT:MS09-063
Patch publication date: 2009/11/10
Plugin publication date: 2009/11/10
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 51351
Microsoft .NET Framework Detection
Synopsis
A software framework is installed on the remote host.
List of Hosts Plugin Output
192.168.1.180
The remote host has following version(s) of Microsoft .NET Framework
installed :
+ Version : 2.0.50727
- Full Version : 2.0.50727.1434
- SP : 1
Description
Microsoft .NET Framework, a software framework for Microsoft Windows
operating systems is installed on the remote host.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 33135
MS08-033: Vulnerabilities in DirectX Could Allow Remote Code Execution (951698)
Synopsis
A vulnerability in DirectX could allow remote code execution.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\quartz.dll has not been patched
Remote version : 6.6.6001.18000
Should be : 6.6.6001.18063
Description
The remote host contains a version of DirectX that is affected by a
remote code execution vulnerability.
To exploit this flaw, an attacker would need to send a specially
malformed MPEG or SAMI file to a user on the remote host and have him
open it.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms08-033.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:46064
OSVDB:46065
CWE:119
MSFT:MS08-033
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 48216
MS10-046: Vulnerability in Windows Shell Could Allow Remote Code Execution (2286198)
Synopsis
The remote windows host is affected by a remote code execution
vulnerability.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Shell32.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18505
Description
The remote windows host contains a version of the Windows Shell that
contains a vulnerability in the way it handles shortcut icons.
An attacker, exploiting this flaw, can execute arbitrary commands on
the remote host subject to the privileges of the user opening the
shortcut.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/MS10-046.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2010-2568
Bugtraq ID
41732
Other references
OSVDB:66387
Secunia:40647
MSFT:MS10-046
Patch publication date: 2010/08/02
Plugin publication date: 2010/08/02
Plugin last modification date: 2011/04/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact, Metasploit (Microsoft Windows Shell LNK Code Execution)
Port cifs (445/tcp)
Plugin ID: 44416
MS10-006: Vulnerabilities in SMB Client Could Allow Remote Code Execution (978251)
Synopsis
Arbitrary code can be executed on the remote host through its SMB
client.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\drivers\Mrxsmb.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18375
Description
The version of the SMB client software installed on the remote
Windows host is affected by two vulnerabilities that could allow
arbitrary code execution :
- Improper validation of fields in SMB responses can lead
to a pool corruption issue and in turn to arbitrary
code execution with SYSTEM level privileges.
(CVE-2010-0016)
- Improper handling of a race condition involving SMB
'Negotiate' responses may allow a remote attacker to
execute arbitrary code, cause a denial of service, or
escalate his privileges. (CVE-2010-0017)
Note that successful exploitation of either issue requires an
attacker to trick a user on the affected host into initiating an SMB
connection to a malicious SMB server.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-006.mspx
Risk Factor
High/ CVSS Base Score: 7.6
(CVSS2#AV:N/AC:H/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.0(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:62243
OSVDB:62244
MSFT:MS10-006
CWE:362
Patch publication date: 2010/02/09
Plugin publication date: 2010/02/09
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 35361
MS09-001: Vulnerabilities in SMB Could Allow Remote Code Execution (958687)
Synopsis
It may be possible to execute arbitrary code on the remote host due
to a flaw in SMB.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\drivers\Srv.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18185
Description
The remote host is affected by a memory corruption vulnerability in
SMB that may allow an attacker to execute arbitrary code or perform a
denial of service against the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms09-001.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.8(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:48153
OSVDB:52691
OSVDB:52692
MSFT:MS09-001
CWE:399
Plugin last modification date: 2011/03/15
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 45509
MS10-022: Vulnerability in VBScript Scripting Engine Could Allow Remote Code Execution (981169)
Synopsis
Arbitrary code can be executed on the remote host through the
installed VBScript Scripting Engine.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\Vbscript.dll has not been patched
Remote version : 5.7.0.18000
Should be : 5.7.0.18440
Description
The installed version of the VBScript Scripting Engine allows an
attacker to specify a Help file location when displaying a dialog box
on a web page. If a user can be tricked into pressing the F1 key
while such a dialog box is being displayed, an attacker can leverage
this to cause the Windows Help System to load a specially crafted Help
file, resulting in execution of arbitrary code subject to the user's
privileges.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-022.mspx
Risk Factor
High/ CVSS Base Score: 7.6
(CVSS2#AV:N/AC:H/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.3(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2010-0483
Bugtraq ID
38463
Other references
OSVDB:62632
MSFT:MS10-022
CWE:94
Patch publication date: 2010/04/13
Plugin publication date: 2010/04/13
Plugin last modification date: 2011/02/23
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Metasploit (Internet Explorer Winhlp32.exe MsgBox Code Execution)
Port cifs (445/tcp)
Plugin ID: 49948
MS10-071: Cumulative Security Update for Internet Explorer (2360131)
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18522
Description
The remote host is missing IE Security Update 2360131.
The remote version of IE is affected by several vulnerabilities that
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for XP, 2003, Vista, 2008, 7,
and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-071.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 8.8(CVSS2#E:F/RL:U/RC:ND)
CVE
CVE-2010-0808
CVE-2010-3243
CVE-2010-3324
CVE-2010-3325
CVE-2010-3326
CVE-2010-3327
CVE-2010-3328
CVE-2010-3329
CVE-2010-3330
CVE-2010-3331
Other references
OSVDB:68123
OSVDB:68540
OSVDB:68541
OSVDB:68542
OSVDB:68543
OSVDB:68544
OSVDB:68545
OSVDB:68546
OSVDB:68547
OSVDB:68548
MSFT:MS10-071
Patch publication date: 2010/10/12
Plugin publication date: 2010/10/13
Plugin last modification date: 2011/03/31
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 51455
MS11-002: Vulnerabilities in Microsoft Data Access Components Could Allow Remote Code Execution (2451910)
Synopsis
Arbitrary code can be executed on the remote host through Microsoft
Data Access Components.
List of Hosts Plugin Output
192.168.1.180
- C:\Program Files\Common Files\system\ado\Msado15.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18570
Description
The version of Microsoft Data Access Components (MDAC) installed on
the remote Windows host is affected by two vulnerabilities, which could
allow arbitrary code execution if a user views a specially crafted
web page
- A buffer overflow in the Open Database Connectivity
(ODBC) API used by third-party applications can be
triggered by an overly long Data Source Name (DSN)
argument. (CVE-2011-0026)
- A failure of MDAC to correctly allocate memory when
handling internal data structures in ActiveX Data
Objects (ADO) records can be abused to execute
arbitrary code. (CVE-2011-0027)
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS11-002.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
Other references
OSVDB:70443
OSVDB:70444
EDB-ID:15984
MSFT:MS11-002
Patch publication date: 2011/01/11
Plugin publication date: 2011/01/11
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 49221
MS10-063: Vulnerability in Unicode Scripts Processor Could Allow Remote Code Execution (2320113)
Synopsis
It is possible to execute arbitrary code on the remote Windows host
using the Unicode Scripts Processor.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Usp10.dll has not been patched
Remote version : 1.626.6001.18000
Should be : 1.626.6001.18461
Description
The version of Microsoft Windows or Microsoft Office on the remote
host includes a version of the Unicode Script Processor (Usp10.dll),
also known as Uniscribe, which incorrectly validates a table in
OpenType fonts.
If an attacker can trick a user on the affected system into visiting a
malicious web site or opening a specially crafted document with an
application that supports embedded OpenType fonts, such as Microsoft
Office, he may be able to leverage this issue to execute arbitrary
code subject to the user's privileges.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
and 2008 as well as Microsoft Office XP, 2003, and 2007 :
http://www.microsoft.com/technet/security/Bulletin/MS10-063.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2010-2738
Bugtraq ID
43068
Other references
OSVDB:67984
MSFT:MS10-063
Patch publication date: 2010/09/14
Plugin publication date: 2010/09/14
Plugin last modification date: 2011/03/31
Ease of exploitability: Exploits are available
Port (0/tcp)
Plugin ID: 10915
Microsoft Windows - Local Users Information : User has never logged on
Synopsis
At least one local user has never logged in to his / her account.
List of Hosts Plugin Output
192.168.1.180
The following local users have never logged in :
- Guest
- 249E6E5E-02B7-46F0-B
- pcurrie
- dtouart
- sgieber
- fcrumb
- cvukelj
- aballs
- idepierre
- mmcleroy
- kmalavet
- tjank
- fdraxler
- cpaskell
- mcosgrave
- deichert
- lmicha
- kbarroso
- vroutte
- rschummer
- lfollett
- pcoladonato
- gdelreal
- lthroneberry
- lmccarn
- mlutjen
- vkonkel
- asponsler
- metzkorn
- tmcquirter
- fconcannon
- lyouker
- mamini
- lrosko
- dcolligan
- fprok
- vnickleberry
- afeurtado
- rgerczak
- hvanhekken
- cdoudna
- sbessent
- wlorimor
- hkarmazyn
- sdechambeau
- lsotelo
- aterris
- mkanta
- atopacio
- gkamphoefner
- abergmeier
- ksorrentino
- lgiacchino
- mmajorga
- fcosby
- lsimcic
- ltabor
- lschweickert
- dbrueckman
- scalverley
- tstansfield
- fpassarelli
- tkreinhagen
- dkoenigsberg
- asteltenpohl
- agoonen
- smockler
- npacheco
- ycambell
- schesher
- mwinegardner
- spoissant
- jlicerio
- murman
- cvrazel
- czoelle
- apaulshock
- gbartus
- edorrough
- jdifiora
- jteno
- tmichel
- bbegan
- aconelli
- ceuton
- sadelmann
- slook
- jhoffpavir
- nholsing
- mscouller
- jbroadwater
- ebrentlinger
- ablaske
- iguzon
- smceldowney
Note that, in addition to the Administrator and Guest accounts, Nessus
has only checked for local users with UIDs between 1000 and 1200.
To use a different range, edit the scan policy and change the 'Start
UID' and/or 'End UID' preferences for 'SMB use host SID to enumerate
local users' setting, and then re-run the scan.
Description
Using the supplied credentials, it is possible to list local users who
have never logged into their accounts.
Solution
Delete accounts that are not needed.
Risk Factor
None
Other references
OSVDB:754
Plugin publication date: 2002/03/17
Plugin last modification date: 2011/03/21
Port cifs (445/tcp)
Plugin ID: 51352
Microsoft .NET Framework Service Pack Out of Date
Synopsis
The remote system has a software framework installed that is out of
date.
List of Hosts Plugin Output
192.168.1.180
The following Microsoft .NET Framework version(s) do not have latest
service pack installed :
Installed version : Microsoft .NET Framework v2.0.50727 SP 1
Should be : Microsoft .NET Framework v2.0.50727 SP 2
Description
The remote system has Microsoft .NET Framework installed. The
installed version either has no service pack installed or the
installed service pack version is out of date.
Solution
Install the latest Microsoft .NET Framework service pack.
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
Plugin last modification date: 2011/03/07
Port cifs (445/tcp)
Plugin ID: 42114
MS09-058: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (971486)
Synopsis
The Windows kernel is vulnerable to multiple buffer overflow attacks.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\ntoskrnl.exe has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18304
Description
The remote Windows host is running a version of the Windows kernel
that is affected by multiple vulnerabilities :
- An elevation of privilege vulnerability exists in the
Windows kernel due to the incorrect truncation of a 64-
bit value to a 32-bit value. An attacker who
successfully exploited this vulnerability could run
arbitrary code in kernel mode. An attacker could then
install programs, view / change / delete data, or
create new accounts with full user rights.
(CVE-2009-2515)
- An elevation of privilege vulnerability exists in the
Windows kernel due to the incorrect truncation of a 64-
bit value to a 32-bit value. An attacker who
successfully exploited this vulnerability could run
arbitrary code in kernel mode. An attacker could then
install programs, view / change / delete data, or
create new accounts with full user rights.
(CVE-2009-2516)
- A denial of service vulnerability exists in the Windows
kernel because of the way the kernel handles certain
exceptions. An attacker could exploit the
vulnerability by running a specially crafted
application causing the system to restart.
(CVE-2009-2517)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/MS09-058.mspx
Risk Factor
High/ CVSS Base Score: 7.6
(CVSS2#AV:N/AC:H/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.0(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:58859
OSVDB:58860
OSVDB:58861
CWE:264
MSFT:MS09-058
Patch publication date: 2009/10/13
Plugin publication date: 2009/10/13
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port ncacn_http (49157/tcp)
Plugin ID: 10761
COM+ Internet Services (CIS) Server Detection
Synopsis
A COM+ Internet Services (CIS) server is listening on this port.
List of Hosts Plugin Output
192.168.1.180
Server banner :
ncacn_http/1.0
Description
COM+ Internet Services are RPC over HTTP tunneling and require IIS to
operate. CIS ports shouldn't be visible on internet but only behind a
firewall.
Solution
If you do not use this service, disable it with DCOMCNFG.
Otherwise, limit access to this port.
See also
http://msdn.microsoft.com/library/en-us/dndcom/html/cis.asp
http://support.microsoft.com/support/kb/articles/Q282/2/61.ASP
Risk Factor
None
Plugin last modification date: 2011/03/21
Port cifs (445/tcp)
Plugin ID: 40887
MS09-050: Microsoft Windows SMB2 _Smb2ValidateProviderCallback() Vulnerability (975497) (uncredentialed check)
Synopsis
Arbitrary code may be executed on the remote host through the SMB port
List of Hosts
192.168.1.180
Description
The remote host is running a version of Microsoft Windows Vista or
Windows Server 2008 that contains a vulnerability in its SMBv2
implementation.
An attacker could exploit this flaw to disable the remote host or to
execute arbitrary code on it.
Solution
Microsoft has released a patch for Windows Vista and Windows Server
2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-050.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 8.3(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2009-3103
Bugtraq ID
36299
Other references
CWE:399
OSVDB:57799
MSFT:MS09-050
Patch publication date: 2009/10/13
Plugin publication date: 2009/09/08
Plugin last modification date: 2011/03/11
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact, Metasploit (Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference)
Port cifs (445/tcp)
Plugin ID: 42439
MS09-065: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (969947)
Synopsis
The remote Windows kernel is affected by remote privilege escalation
vulnerabilities.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Win32k.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18311
Description
The remote host contains a version of the Windows kernel that is
affected by multiple vulnerabilities :
- A NULL pointer dereferencing vulnerability allowing a
local user to elevate his privileges (CVE-2009-1127)
- Insufficient validation of certain input passed to GDI
from user mode allows a local user to run arbitrary
code in kernel mode. (CVE-2009-2513)
- A parsing vulnerability when decoding a specially
crafted Embedded OpenType (EOT) font may allow a remote
user to execute arbitrary code on the remote host by
luring a user of the remote host into viewing a web
page containing such a malformed font. (CVE-2009-2514)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-065.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.3(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:59867
OSVDB:59868
OSVDB:59869
CWE:94
MSFT:MS09-065
Patch publication date: 2009/11/10
Plugin publication date: 2009/11/10
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 39341
MS09-019: Cumulative Security Update for Internet Explorer (969897)
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18248
Description
he remote host is missing IE Security Update 969897.
The remote version of IE is affected by several vulnerabilities that
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-019.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2007-3091
CVE-2009-1140
CVE-2009-1141
CVE-2009-1528
CVE-2009-1529
CVE-2009-1530
CVE-2009-1531
CVE-2009-1532
Other references
OSVDB:38497
OSVDB:54944
OSVDB:54945
OSVDB:54946
OSVDB:54947
OSVDB:54948
OSVDB:54949
OSVDB:54950
OSVDB:54951
CWE:362
MSFT:MS09-019
Plugin publication date: 2009/06/10
Plugin last modification date: 2011/02/25
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 31797
MS08-024: Cumulative Security Update for Internet Explorer (947864)
Synopsis
Arbitrary code can be executed on the remote host through the web client.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18023
Description
The remote host is missing the IE cumulative security update 947864.
The remote version of IE is vulnerable to several flaws which may allow an
attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003, Vista and 2008:
http://www.microsoft.com/technet/security/Bulletin/MS08-024.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.9(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2008-1085
Bugtraq ID
28552
Other references
OSVDB:44205
CWE:94
MSFT:MS08-024
Plugin last modification date: 2011/03/04
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 51163
MS10-091: Vulnerabilities in the OpenType Font (OTF) Driver Could Allow Remote Code Execution (2296199)
Synopsis
The remote Windows host contains a font driver that allows arbitrary
code execution.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\Atmfd.dll has not been patched
Remote version : 5.1.2.226
Should be : 5.1.2.230
Description
The remote Windows host contains a version of the OpenType Font (OTF)
Format Driver that is affected by two vulnerabilities :
- The driver does not properly index an array when
parsing OpenType fonts, which could allow a remote
attacker to run arbitrary code in kernel mode.
(CVE-2010-3956)
- The driver does not properly reset a pointer when
freeing memory, resulting in a 'double free' condition,
which could allow a remote attacker to run arbitrary
code in kernel mode. (CVE-2010-3957)
- The driver does not properly parse the CMAP table when
rendering a specially crafted OpenType font, which
could allow a local attacker to run arbitrary code in
kernel mode. (CVE-2010-3959)
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-091.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
Other references
OSVDB:69820
OSVDB:69821
OSVDB:69822
MSFT:MS10-091
Patch publication date: 2010/12/14
Plugin publication date: 2010/12/15
Plugin last modification date: 2011/03/18
Port cifs (445/tcp)
Plugin ID: 39348
MS09-026: Vulnerability in RPC Could Allow Elevation of Privilege (970238)
Synopsis
Arbitrary code can be executed on the remote host through its RPC
facility.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Rpcrt4.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18247
Description
The RPC Marshalling Engine installed on the remote Windows host does
not update its internal state appropriately, which could lead to a
pointer being read from an incorrect location. A remote attacker may
be able to leverage this issue to execute arbitrary code on the
affected host and take complete control of it.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-026.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 5.3(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2009-0568
Bugtraq ID
35219
Other references
OSVDB:54936
CWE:264
MSFT:MS09-026
Plugin last modification date: 2011/02/25
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 49951
MS10-074: Vulnerability in Microsoft Foundation Classes Could Allow Remote Code Execution (2387149)
Synopsis
It is possible to execute arbitrary code on the remote Windows host
through the Microsoft Foundation Class (MFC) Library component.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mfc40u.dll has not been patched
Remote version : 4.1.0.6140
Should be : 4.1.0.6151
Description
The Microsoft Foundation Class (MFC) library component installed on
the remote host is affected by a stack-based buffer overflow in the
'UpdateFrameTitleForDocument()' function of the 'CFrameWnd' class.
If there is an application on the affected host built with the
affected MFC library and that uses user-supplied data to set the
window title, it may be possible for an attacker to execute arbitrary
code on the remote host subject to the privileges of the user running
that application.
Note that an exploit involving PowerZip has been published.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-074.mspx
Risk Factor
High/ CVSS Base Score: 7.6
(CVSS2#AV:N/AC:H/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.8(CVSS2#E:POC/RL:U/RC:ND)
CVE
CVE-2010-3227
Bugtraq ID
41333
Other references
OSVDB:68585
MSFT:MS10-074
Patch publication date: 2010/10/12
Plugin publication date: 2010/10/13
Plugin last modification date: 2011/03/24
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 10394
Microsoft Windows SMB Log In Possible
Synopsis
It is possible to log into the remote host.
List of Hosts Plugin Output
192.168.1.180
- NULL sessions are enabled on the remote host
- The SMB tests will be done as 'administrator'/'******'
Description
The remote host is running Microsoft Windows operating
system or Samba, a CIFS/SMB server for Unix. It was
possible to log into it using one of the following
account :
- NULL session
- Guest account
- Given Credentials
Solution
n/a
See also
http://support.microsoft.com/support/kb/articles/Q143/4/74.ASP
http://support.microsoft.com/support/kb/articles/Q246/2/61.ASP
Risk Factor
None
Other references
OSVDB:297
OSVDB:3106
OSVDB:8230
OSVDB:10050
Plugin publication date: 2000/05/09
Plugin last modification date: 2011/03/21
Ease of exploitability: Exploits are available
Exploitable with: Metasploit (Microsoft Windows Authenticated User Code Execution)
Port cifs (445/tcp)
Plugin ID: 33878
MS08-049: Vulnerabilities in Event System Could Allow Remote Code Execution (950974)
Synopsis
Arbitrary code can be executed on the remote host through the
Microsoft Event System.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\es.dll has not been patched
Remote version : 2001.12.6931.18000
Should be : 2001.12.6931.18057
Description
The remote version of Windows contains a vulnerability in the Event
System that might allow an attacker to execute arbitrary code on the
remote host.
To exploit this vulnerability, an attacker with valid logon
credentials would need to send a malformed subscription request to the
remote Event System.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms08-049.mspx
Risk Factor
High/ CVSS Base Score: 8.5
(CVSS2#AV:N/AC:M/Au:S/C:C/I:C/A:C)
Other references
OSVDB:47411
OSVDB:47412
MSFT:MS08-049
CWE:20
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS)
Port cifs (445/tcp)
Plugin ID: 51906
MS11-006: Vulnerability in Windows Shell Graphics Processing Could Allow Remote Code Execution (2483185)
Synopsis
It may be possible to execute arbitrary code on the remote host using
the graphics rendering engine.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Shell32.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18588
Description
If a remote attacker can trick a user on the affected host into
opening a specially crafted bitmap file, he may be able to leverage a
vulnerability in the graphics rendering engine that arises due to its
failure to validate the 'biClrUsed' parameter and thereby execute
arbitrary code on the host subject to the user's privileges.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008 :
http://www.microsoft.com/technet/security/Bulletin/MS11-006.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVE
CVE-2010-3970
Bugtraq ID
45662
Other references
OSVDB:70263
MSFT:MS11-006
Patch publication date: 2011/02/08
Plugin publication date: 2011/02/08
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Metasploit (Microsoft Windows CreateSizedDIBSECTION Stack Buffer Overflow)
Port cifs (445/tcp)
Plugin ID: 38912
Microsoft Windows SMB Registry : Vista / Server 2008 Service Pack Detection
Synopsis
It was possible to determine the service pack installed on
the remote system.
List of Hosts Plugin Output
192.168.1.180
The remote Windows Vista / Server 2008 system has Service Pack 1 applied.
Description
It is possible to determine the Service Pack version of the Windows
Vista / Server 2008 system by reading the registry key
'HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\CSDVersion'.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/02
Port cifs (445/tcp)
Plugin ID: 45508
MS10-021: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (979683)
Synopsis
The Windows kernel is affected by eight vulnerabilities, including
some that allow a local attacker to execute code with SYSTEM
privileges.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\ntoskrnl.exe has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18427
Description
The remote Windows host is running a version of the Windows kernel
that is affected by eight vulnerabilities :
- A denial of service vulnerability exists in the Windows
kernel due to the insufficient validation of registry
keys passed to a Windows kernel system call.
(CVE-2010-0234)
- A denial of service vulnerability exists in the Windows
kernel due to the manner in which the kernel processes
the values of symbolic links. (CVE-2010-0235)
- An elevation of privilege vulnerability exists in the
Windows kernel due to the manner in which memory is
allocated when extracting a symbolic link from a registry
key. An attacker who successfully exploited this
vulnerability could run arbitrary code in kernel mode.
(CVE-2010-0236)
- An elevation of privilege vulnerability exists when the
Windows kernel does not properly restrict symbolic link
creation between untrusted and trusted registry hives. An
attacker who successfully exploited this vulnerability
could run arbitrary code in kernel mode. (CVE-2010-0237)
- A denial of service vulnerability exists in the way
that the Windows kernel validates registry keys.
(CVE-2010-0238)
- A denial of service vulnerability exists in the Windows
kernel due to the way that the kernel resolves the real
path for a registry key from its virtual path.
(CVE-2010-0481)
- A denial of service vulnerability exists in the Windows
kernel due to the improper validation of specially
crafted image files. (CVE-2010-0482)
- A denial of service vulnerability exists in the Windows
kernel due to the way that the kernel handles certain
exceptions. (CVE-2010-0810)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista, 2008 and 7 :
http://www.microsoft.com/technet/security/bulletin/ms10-021.mspx
Risk Factor
Medium/ CVSS Base Score: 6.2
(CVSS2#AV:L/AC:H/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 4.9(CVSS2#E:POC/RL:OF/RC:C)
CVE
CVE-2010-0234
CVE-2010-0235
CVE-2010-0236
CVE-2010-0237
CVE-2010-0238
CVE-2010-0481
CVE-2010-0482
CVE-2010-0810
Other references
OSVDB:63728
OSVDB:63729
OSVDB:63730
OSVDB:63731
OSVDB:63732
OSVDB:63733
OSVDB:63735
OSVDB:63736
MSFT:MS10-021
Patch publication date: 2010/04/13
Plugin publication date: 2010/04/13
Plugin last modification date: 2011/02/23
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 39347
MS09-025: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (968537)
Synopsis
The remote Windows kernel is affected by local privilege escalation
vulnerabilities.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Win32k.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18246
Description
The remote host contains a version of the Windows kernel that is
affected by multiple vulnerabilities :
- A failure of the Windows kernel to properly validate
changes in certain kernel objects allows a local user
to run arbitrary code in kernel mode. (CVE-2009-1123)
- Insufficient validation of certain pointers passed from
user mode allows a local user to run arbitrary code in
kernel mode. (CVE-2009-1124)
- A failure to properly validate an argument passed to a
Windows kernel system call allows a local user to run
arbitrary code in kernel mode. (CVE-2009-1125)
- Improper validation of input passed from user mode to
the kernel when editing a specific desktop parameter
allows a local user to run arbitrary code in kernel
mode. (CVE-2009-1126)
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-025.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.0(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:54940
OSVDB:54941
OSVDB:54942
OSVDB:54943
CWE:20
MSFT:MS09-025
Plugin last modification date: 2011/02/25
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 49226
MS10-068: Vulnerability in Local Security Authority Subsystem Service Could Allow Elevation of Privilege (983539)
Synopsis
The version of Active Directory on the remote Windows host can be
used to execute arbitrary code.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Ntdsai.dll has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18461
Description
The version of the Local Security Authority Subsystem Service (LSASS)
installed on the remote Windows host does not properly handle
malformed packets in LDAP messages when used in conjunction with
Microsoft Active Directory / Active Directory Application Mode /
Active Directory Lightweight Directory Service.
By sending a specially crafted LDAP message to a listening LSASS
server, an authenticated attacker with a member account within the
target Windows domain may be able to overflow a buffer and execute
arbitrary code, thereby gaining complete control of the affected
system.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-068.mspx
Risk Factor
High/ CVSS Base Score: 9.0
(CVSS2#AV:N/AC:L/Au:S/C:C/I:C/A:C)
CVSS Temporal Score: 6.7(CVSS2#E:U/RL:OF/RC:C)
CVE
CVE-2010-0820
Bugtraq ID
43037
Other references
OSVDB:67987
MSFT:MS10-068
Patch publication date: 2010/09/14
Plugin publication date: 2010/09/14
Plugin last modification date: 2011/03/31
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 42110
MS09-054: Cumulative Security Update for Internet Explorer (974455)
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18319
Description
The remote host is missing IE Security Update 974455.
The remote version of IE is affected by several vulnerabilities that
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-054.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.3(CVSS2#E:POC/RL:OF/RC:C)
Other references
OSVDB:58871
OSVDB:58872
OSVDB:58873
OSVDB:58874
CWE:94
MSFT:MS09-054
Patch publication date: 2009/10/13
Plugin publication date: 2009/10/13
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 48295
MS10-058: Vulnerabilities in TCP/IP Could Allow Elevation of Privilege (978886)
Synopsis
The remote host has multiple vulnerabilities in its TCP/IP
implementation.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\drivers\Tcpip.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18493
Description
The TCP/IP stack installed on the remote Windows host is affected by
one or more of the following vulnerabilities :
- An error exists in the Windows TCP/IP stack when
processing specially crafted IPv6 packets with a
malformed extension header which could cause the
affected system to stop responding if IPv6 features are
enabled, which is true by default in Windows Vista and
2008. (CVE-2010-1892)
- The Windows TCP/IP stack fails to properly handle data
copied from user mode, which could result in an integer
overflow and allow a local attacker to run arbitrary
code with system-level privileges. (CVE-2010-1892)
Solution
Microsoft has released a set of patches for Windows Vista, 2008, 7,
and 2008 R2 :
http://www.microsoft.com/technet/security/Bulletin/MS10-058.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 5.3(CVSS2#E:U/RL:OF/RC:C)
Other references
OSVDB:67004
OSVDB:67005
MSFT:MS10-058
Patch publication date: 2010/08/10
Plugin publication date: 2010/08/11
Plugin last modification date: 2011/04/01
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 48290
MS10-053: Cumulative Security Update for Internet Explorer (2183461)
Synopsis
Arbitrary code can be executed on the remote host through a web
browser.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18498
Description
The remote host is missing IE Security Update 2183461.
The remote version of IE is affected by several vulnerabilities that
may allow an attacker to execute arbitrary code on the remote host.
Solution
Microsoft has released a set of patches for XP, 2003, Vista, 2008, 7,
and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-053.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 7.7(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:66998
OSVDB:66999
OSVDB:67000
OSVDB:67001
OSVDB:67002
OSVDB:67003
MSFT:MS10-053
Patch publication date: 2010/08/10
Plugin publication date: 2010/08/11
Plugin last modification date: 2011/04/01
Ease of exploitability: Exploits are available
Port cifs (445/tcp)
Plugin ID: 34743
MS08-068: Vulnerability in SMB Could Allow Remote Code Execution (957097)
Synopsis
It is possible to execute code on the remote host.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\drivers\Mrxsmb10.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18130
Description
The remote version of Windows contains a version of SMB (Server
Message Block) protocol which is vulnerable to a credentials
reflection attack.
An attacker may exploit this flaw to elevate his privileges and gain
control of the remote host.
Solution
Microsoft has released a set of patches for Windows 2000, XP, 2003,
Vista and 2008 :
http://www.microsoft.com/technet/security/bulletin/ms08-068.mspx
Risk Factor
High/ CVSS Base Score: 7.6
(CVSS2#AV:N/AC:H/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.3(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2008-4037
Bugtraq ID
7385
Other references
OSVDB:49736
CWE:287
MSFT:MS08-068
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact, Metasploit (Microsoft Windows SMB Relay Code Execution)
Port cifs (445/tcp)
Plugin ID: 35630
MS09-002: Cumulative Security Update for Internet Explorer (961260)
Synopsis
Arbitrary code can be executed on the remote host through the web
client.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Mshtml.dll has not been patched
Remote version : 7.0.6001.18000
Should be : 7.0.6001.18203
Description
The remote host is missing IE Security Update 961260.
The remote version of IE is affected by two memory corruption
vulnerabilities that may allow an attacker to execute arbitrary code
on the remote host.
Solution
Microsoft has released a set of patches for Windows XP, 2003, Vista
and 2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-002.mspx
Risk Factor
High/ CVSS Base Score: 9.3
(CVSS2#AV:N/AC:M/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 8.1(CVSS2#E:H/RL:OF/RC:C)
Other references
OSVDB:51839
OSVDB:51840
CWE:399
MSFT:MS09-002
Plugin last modification date: 2011/03/15
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact, Metasploit (Internet Explorer 7 CFunctionPointer Uninitialized Memory Corruption)
Port (0/tcp)
Plugin ID: 10898
Microsoft WIndows - Users Information : Never changed password
Synopsis
At least one user has never changed his / her password.
List of Hosts Plugin Output
192.168.1.180
The following user has never changed his / her password :
- Administrator
Note that, in addition to the Administrator, Guest, and Kerberos
accounts, Nessus has enumerated only those domain users with UIDs
between 1000 and 1200. To use a different range, edit the scan policy
and change the 'Start UID' and/or 'End UID' preferences for
'SMB use domain SID to enumerate users' setting, and then re-run the scan.
Description
Using the supplied credentials, it is possible to list users who
have never changed their passwords.
Solution
Allow / require users to change their passwords regularly.
Risk Factor
None
Plugin last modification date: 2011/03/21
Port cifs (445/tcp)
Plugin ID: 40891
MS09-048: Vulnerabilities in Windows TCP/IP Could Allow Remote Code Execution (967723)
Synopsis
Multiple vulnerabilities in the Windows TCP/IP implementation could
lead to denial of service or remote code execution.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\System32\drivers\tcpip.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18311
Description
The TCP/IP implementation on the remote host has multiple flaws that
could allow remote code execution if an attacker sent specially
crafted TCP/IP packets over the network to a computer with a listening
service.
- A denial of service vulnerability exists in TCP/IP
processing in Microsoft Windows due to the way that
Windows handles an excessive number of established TCP
connections. The affect of this vulnerability can be
amplified by the requirement to process specially
crafted packets with a TCP receive window size set to a
very small value or zero. An attacker could exploit the
vulnerability by flooding a system with specially
crafted packets causing the affected system to stop
responding to new requests or automatically restart.
(CVE-2008-4609)
- A remote code execution vulnerability exists in the
Windows TCP/IP stack due to the TCP/IP stack not
cleaning up state information correctly. This causes the
TCP/IP stack to reference a field as a function pointer
when it actually contains other information. n anonymous
attacker could exploit the vulnerability by sending
specially crafted TCP/IP packets to a computer that has
a service listening over the network. An attacker who
successfully exploited this vulnerability could take
complete control of an affected system. (CVE-2009-1925)
- A denial of service vulnerability exists in TCP/IP
processing in Microsoft Windows due to an error in the
processing of specially crafted packets with a small or
zero TCP receive window size. If an application closes a
TCP connection with pending data to be sent and an
attacker has set a small or zero TCP receive window
size, the affected server will not be able to
completely close the TCP connection. An attacker could
exploit the vulnerability by flooding a system with
specially crafted packets causing the affected system
to stop responding to new requests. The system would
remain non-responsive even after the attacker stops
sending malicious packets. (CVE-2009-1926)
Solution
Microsoft has released a set of patches for Windows 2003, Vista and
2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-048.mspx
Risk Factor
High/ CVSS Base Score: 7.6
(CVSS2#AV:N/AC:H/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.3(CVSS2#E:F/RL:OF/RC:C)
Other references
OSVDB:57795
OSVDB:57796
OSVDB:57797
CWE:94
MSFT:MS09-048
Plugin publication date: 2009/09/08
Plugin last modification date: 2011/03/04
Ease of exploitability: Exploits are available
Exploitable with: Core Impact
Port cifs (445/tcp)
Plugin ID: 49950
MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957)
Synopsis
The Windows kernel is affected by multiple vulnerabilities that could
allow escalation of privileges.
List of Hosts Plugin Output
192.168.1.180
- C:\Windows\system32\Win32k.sys has not been patched
Remote version : 6.0.6001.18000
Should be : 6.0.6001.18523
Description
The remote Windows host is running a version of the Windows kernel
that is affected by the following vulnerabilities :
- A reference count leak, which could result
in arbitrary code execution in the kernel.
(CVE-2010-2549)
- Kernel-mode drivers load unspecified keyboard
layers improperly, which could result in arbitrary
code execution in the kernel. (CVE-2010-2743)
- Kernel-mode drivers do not properly validate
unspecified window class data, which could
result in arbitrary code execution in the kernel.
(CVE-2010-2744)
Solution
Microsoft has released a set of patches for Windows 2003, XP, Vista,
2008, 7, and 2008 R2 :
http://www.microsoft.com/technet/security/bulletin/ms10-073.mspx
Risk Factor
High/ CVSS Base Score: 7.2
(CVSS2#AV:L/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 6.5(CVSS2#E:POC/RL:U/RC:ND)
Other references
OSVDB:66003
OSVDB:68551
OSVDB:68552
EDB-ID:15985
MSFT:MS10-073
Patch publication date: 2010/10/12
Plugin publication date: 2010/10/13
Plugin last modification date: 2011/03/24
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS)
| 192.168.1.180 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 6 11:55:42 2011 |
| End time: | Wed Apr 6 11:58:03 2011 |
| Number of vulnerabilities | |
| High | 109 |
| Medium | 19 |
| Low | 85 |
| Remote Host Information | |
| Operating System: | Microsoft Windows Server 2008 Service Pack 1 |
| NetBIOS name: | WIN-8BPIQBRO0CX |