List of PlugIn IDs
The following plugin IDs have problems associated with them. Select the ID to review more detail.
Plugin id#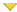 | # of issues | Plugin name | Severity |
|---|---|---|---|
| 40887 | 1 | MS09-050: Microsoft Windows SMB2 _Smb2ValidateProviderCallback() Vulnerability (975497) (uncredentialed check) | High Severity problem(s) found |
| 26194 | 1 | Web Server Uses Plain Text Authentication Forms | Medium Severity problem(s) found |
| 20007 | 1 | SSL Version 2 (v2) Protocol Detection | Medium Severity problem(s) found |
| 10723 | 1 | LDAP Server NULL Bind Connection Information Disclosure | Medium Severity problem(s) found |
| 10722 | 1 | LDAP NULL BASE Search Access | Medium Severity problem(s) found |
| 51891 | 1 | SSL Session Resume Supported | Low Severity problem(s) found |
| 50845 | 1 | OpenSSL Detection | Low Severity problem(s) found |
| 45590 | 1 | Common Platform Enumeration (CPE) | Low Severity problem(s) found |
| 43829 | 1 | Kerberos Information Disclosure | Low Severity problem(s) found |
| 39463 | 1 | HTTP Server Cookies Set | Low Severity problem(s) found |
| 35716 | 1 | Ethernet Card Manufacturer Detection | Low Severity problem(s) found |
| 33929 | 1 | PCI DSS compliance | Low Severity problem(s) found |
| 26920 | 1 | Microsoft Windows SMB NULL Session Authentication | Low Severity problem(s) found |
| 26917 | 1 | Microsoft Windows SMB Registry : Nessus Cannot Access the Windows Registry | Low Severity problem(s) found |
| 25701 | 1 | LDAP Crafted Search Request Server Information Disclosure | Low Severity problem(s) found |
| 25220 | 1 | TCP/IP Timestamps Supported | Low Severity problem(s) found |
| 22964 | 5 | Service Detection | Low Severity problem(s) found |
| 21643 | 1 | SSL Cipher Suites Supported | Low Severity problem(s) found |
| 20870 | 1 | LDAP Server Detection | Low Severity problem(s) found |
| 20094 | 1 | VMware Virtual Machine Detection | Low Severity problem(s) found |
| 19506 | 1 | Nessus Scan Information | Low Severity problem(s) found |
| 11936 | 1 | OS Identification | Low Severity problem(s) found |
| 11011 | 2 | Microsoft Windows SMB Service Detection | Low Severity problem(s) found |
| 11002 | 2 | DNS Server Detection | Low Severity problem(s) found |
| 10884 | 1 | Network Time Protocol (NTP) Server Detection | Low Severity problem(s) found |
| 10785 | 1 | Microsoft Windows SMB NativeLanManager Remote System Information Disclosure | Low Severity problem(s) found |
| 10761 | 1 | COM+ Internet Services (CIS) Server Detection | Low Severity problem(s) found |
| 10736 | 11 | DCE Services Enumeration | Low Severity problem(s) found |
| 10662 | 1 | Web mirroring | Low Severity problem(s) found |
| 10394 | 1 | Microsoft Windows SMB Log In Possible | Low Severity problem(s) found |
| 10287 | 1 | Traceroute Information | Low Severity problem(s) found |
| 10150 | 1 | Windows NetBIOS / SMB Remote Host Information Disclosure | Low Severity problem(s) found |
| 10114 | 1 | ICMP Timestamp Request Remote Date Disclosure | Low Severity problem(s) found |
| 10107 | 1 | HTTP Server Type and Version | Low Severity problem(s) found |
Port (0/tcp)
Plugin ID: 33929
PCI DSS compliance
Synopsis
Nessus has determined that this host is NOT COMPLIANT with the PCI
DSS requirements.
List of Hosts Plugin Output
192.168.1.180
+ Some services implement SSL 2.0.
+ 2 high risk flaws were found. See :
http://www.nessus.org/plugins/index.php?view=single&id=40887
http://www.nessus.org/plugins/index.php?view=single&id=49070
+ 5 medium risk flaws were found. See :
http://www.nessus.org/plugins/index.php?view=single&id=10723
http://www.nessus.org/plugins/index.php?view=single&id=10722
http://www.nessus.org/plugins/index.php?view=single&id=51192
http://www.nessus.org/plugins/index.php?view=single&id=20007
http://www.nessus.org/plugins/index.php?view=single&id=26194
Description
The remote web server is vulnerable to cross-site scripting (XSS)
attacks, implements old SSL2.0 cryptography, runs obsolete software,
or is affected by dangerous vulnerabilities (CVSS base score >= 4).
Solution
Risk Factor
None
Plugin last modification date: 2010/07/22
Port cifs (445/tcp)
Plugin ID: 26917
Microsoft Windows SMB Registry : Nessus Cannot Access the Windows Registry
Synopsis
Nessus is not able to access the remote Windows Registry.
List of Hosts Plugin Output
192.168.1.180
Could not connect to the registry because:
Could not connect to \winreg
Description
It was not possible to connect to PIPE\winreg on the remote host.
If you intend to use Nessus to perform registry-based checks, the
registry checks will not work because the 'Remote Registry Access'
service (winreg) has been disabled on the remote host or can not be
connected to with the supplied credentials.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/27
Port cifs (445/tcp)
Plugin ID: 26920
Microsoft Windows SMB NULL Session Authentication
Synopsis
It is possible to log into the remote Windows host with a NULL
session.
List of Hosts
192.168.1.180
Description
The remote host is running Microsoft Windows, and it was possible to
log into it using a NULL session (i.e., with no login or password). An
unauthenticated remote attacker can leverage this issue to get
information about the remote host.
Solution
n/a
Risk Factor
None
Bugtraq ID
494
Other references
OSVDB:299
Plugin publication date: 2007/10/04
Plugin last modification date: 2011/03/28
Ease of exploitability: No known exploits are available
Port cifs (445/tcp)
Plugin ID: 40887
MS09-050: Microsoft Windows SMB2 _Smb2ValidateProviderCallback() Vulnerability (975497) (uncredentialed check)
Synopsis
Arbitrary code may be executed on the remote host through the SMB port
List of Hosts
192.168.1.180
Description
The remote host is running a version of Microsoft Windows Vista or
Windows Server 2008 that contains a vulnerability in its SMBv2
implementation.
An attacker could exploit this flaw to disable the remote host or to
execute arbitrary code on it.
Solution
Microsoft has released a patch for Windows Vista and Windows Server
2008 :
http://www.microsoft.com/technet/security/Bulletin/MS09-050.mspx
Risk Factor
Critical/ CVSS Base Score: 10.0
(CVSS2#AV:N/AC:L/Au:N/C:C/I:C/A:C)
CVSS Temporal Score: 8.3(CVSS2#E:F/RL:OF/RC:C)
CVE
CVE-2009-3103
Bugtraq ID
36299
Other references
CWE:399
OSVDB:57799
MSFT:MS09-050
Patch publication date: 2009/10/13
Plugin publication date: 2009/09/08
Plugin last modification date: 2011/03/11
Ease of exploitability: Exploits are available
Exploitable with: Canvas (CANVAS), Core Impact, Metasploit (Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference)
Port (0/tcp)
Plugin ID: 19506
Nessus Scan Information
Synopsis
Information about the Nessus scan.
List of Hosts Plugin Output
192.168.1.180
Information about this scan :
Nessus version : 4.4.1
Plugin feed version : 201104050834
Type of plugin feed : ProfessionalFeed (Direct)
Scanner IP : 192.168.1.13
Port scanner(s) : nessus_syn_scanner
Port range : 1-65535
Thorough tests : no
Experimental tests : no
Paranoia level : 1
Report Verbosity : 1
Safe checks : yes
Optimize the test : yes
CGI scanning : enabled
Web application tests : disabled
Max hosts : 100
Max checks : 5
Recv timeout : 5
Backports : None
Scan Start Date : 2011/4/6 10:53
Scan duration : 191 sec
Description
This script displays, for each tested host, information about the scan itself:
- The version of the plugin set
- The type of plugin feed (HomeFeed or ProfessionalFeed)
- The version of the Nessus Engine
- The port scanner(s) used
- The port range scanned
- The date of the scan
- The duration of the scan
- The number of hosts scanned in parallel
- The number of checks done in parallel
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/19
Port (0/tcp)
Plugin ID: 25220
TCP/IP Timestamps Supported
Synopsis
The remote service implements TCP timestamps.
List of Hosts
192.168.1.180
Description
The remote host implements TCP timestamps, as defined by RFC1323. A
side effect of this feature is that the uptime of the remote host can
sometimes be computed.
Solution
n/a
See also
http://www.ietf.org/rfc/rfc1323.txt
Risk Factor
None
Plugin last modification date: 2011/03/20
Port ntp (123/udp)
Plugin ID: 10884
Network Time Protocol (NTP) Server Detection
Synopsis
An NTP server is listening on the remote host.
List of Hosts
192.168.1.180
Description
An NTP (Network Time Protocol) server is listening on this port. It
provides information about the current date and time of the remote
system and may provide system information.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port ldap (389/tcp)
Plugin ID: 10723
LDAP Server NULL Bind Connection Information Disclosure
Synopsis
The remote LDAP server allows anonymous access.
List of Hosts
192.168.1.180
Description
The LDAP server on the remote host is currently configured such that a
user can connect to it without authentication - via a 'NULL BIND' -
and query it for information. Although the queries that are allowed
are likely to be fairly restricted, this may result in disclosure of
information that an attacker could find useful.
Note that version 3 of the LDAP protocol requires that a server allow
anonymous access -- a 'NULL BIND' -- to the root DSA-Specific Entry
(DSE) even though it may still require authentication to perform other
queries. As such, this finding may be a false-positive.
Solution
Unless the remote LDAP server supports LDAP v3, configure it to
disallow NULL BINDs.
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Other references
OSVDB:9723
Plugin publication date: 2001/08/13
Plugin last modification date: 2011/03/11
Port (0/tcp)
Plugin ID: 20094
VMware Virtual Machine Detection
Synopsis
The remote host seems to be a VMware virtual machine.
List of Hosts
192.168.1.180
Description
According to the MAC address of its network adapter, the remote host
is a VMware virtual machine.
Since it is physically accessible through the network, ensure that its
configuration matches your organization's security policy.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/27
Port ldap (389/tcp)
Plugin ID: 10722
LDAP NULL BASE Search Access
Synopsis
The remote LDAP server may disclose sensitive information.
List of Hosts
192.168.1.180
Description
The remote LDAP server supports search requests with a null, or empty,
base object. This allows information to be retrieved without any
prior knowledge of the directory structure. Coupled with a NULL BIND,
an anonymous user may be able to query your LDAP server using a tool
such as 'LdapMiner'.
Note that there are valid reasons to allow queries with a null base.
For example, it is required in version 3 of the LDAP protocol to
provide access to the root DSA-Specific Entry (DSE), with information
about the supported naming context, authentication types, and the
like. It also means that legitimate users can find information in the
directory without any a priori knowledge of its structure. As such,
this finding may be a false-positive.
Solution
If the remote LDAP server supports a version of the LDAP protocol
before v3, consider whether to disable NULL BASE queries on your LDAP
server.
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/11
Port www (8000/tcp)
Plugin ID: 10107
HTTP Server Type and Version
Synopsis
A web server is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The remote web server type is :
CherryPy/3.1.2
Description
This plugin attempts to determine the type and the version of the
remote web server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/01
Port www (8089/tcp)
Plugin ID: 21643
SSL Cipher Suites Supported
Synopsis
The remote service encrypts communications using SSL.
List of Hosts Plugin Output
192.168.1.180
Here is the list of SSL ciphers supported by the remote server :
High Strength Ciphers (>= 112-bit key)
SSLv2
DES-CBC3-MD5 Kx=RSA Au=RSA Enc=3DES(168) Mac=MD5
RC2-CBC-MD5 Kx=RSA Au=RSA Enc=RC2(128) Mac=MD5
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
SSLv3
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
TLSv1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1
AES128-SHA Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
AES256-SHA Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1
The fields above are :
{OpenSSL ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric encryption method}
Mac={message authentication code}
{export flag}
Description
This script detects which SSL ciphers are supported by the remote
service for encrypting communications.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port www (8089/tcp)
Plugin ID: 20007
SSL Version 2 (v2) Protocol Detection
Synopsis
The remote service encrypts traffic using a protocol with known
weaknesses.
List of Hosts
192.168.1.180
Description
The remote service accepts connections encrypted using SSL 2.0, which
reportedly suffers from several cryptographic flaws and has been
deprecated for several years. An attacker may be able to exploit
these issues to conduct man-in-the-middle attacks or decrypt
communications between the affected service and clients.
Solution
Consult the application's documentation to disable SSL 2.0 and use SSL
3.0 or TLS 1.0 instead.
See also
http://www.schneier.com/paper-ssl.pdf
http://support.microsoft.com/kb/187498
http://www.linux4beginners.info/node/disable-sslv2
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/11
Port www (8089/tcp)
Plugin ID: 50845
OpenSSL Detection
Synopsis
The remote service appears to use OpenSSL to encrypt traffic.
List of Hosts
192.168.1.180
Description
Based on its behavior, it seems that the remote service is using the
OpenSSL library to encrypt traffic.
Note that this plugin can only detect OpenSSL implementations that
have enabled support for TLS extensions (RFC 4366).
Solution
n/a
See also
http://www.openssl.org
Risk Factor
None
Plugin last modification date: 2011/03/11
Port ldap (389/tcp)
Plugin ID: 20870
LDAP Server Detection
Synopsis
There is an LDAP server active on the remote host.
List of Hosts
192.168.1.180
Description
The remote host is running a Lightweight Directory Access Protocol, or
LDAP, server. LDAP is a protocol for providing access to directory
services over TCP/IP.
Solution
n/a
See also
http://en.wikipedia.org/wiki/LDAP
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (0/udp)
Plugin ID: 10287
Traceroute Information
Synopsis
It was possible to obtain traceroute information.
List of Hosts Plugin Output
192.168.1.180
For your information, here is the traceroute from 192.168.1.13 to 192.168.1.180 :
192.168.1.13
192.168.1.180
Description
Makes a traceroute to the remote host.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/21
Port netbios-ns (137/udp)
Plugin ID: 10150
Windows NetBIOS / SMB Remote Host Information Disclosure
Synopsis
It is possible to obtain the network name of the remote host.
List of Hosts Plugin Output
192.168.1.180
The following 5 NetBIOS names have been gathered :
WIN-8BPIQBRO0CX = Computer name
TX = Workgroup / Domain name
TX = Domain Controllers
WIN-8BPIQBRO0CX = File Server Service
TX = Domain Master Browser
The remote host has the following MAC address on its adapter :
00:0c:29:9d:a1:c6
Description
The remote host listens on UDP port 137 or TCP port 445 and replies to
NetBIOS nbtscan or SMB requests.
Note that this plugin gathers information to be used in other plugins
but does not itself generate a report.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/27
Port cifs (445/tcp)
Plugin ID: 10394
Microsoft Windows SMB Log In Possible
Synopsis
It is possible to log into the remote host.
List of Hosts Plugin Output
192.168.1.180
- NULL sessions are enabled on the remote host
Description
The remote host is running Microsoft Windows operating
system or Samba, a CIFS/SMB server for Unix. It was
possible to log into it using one of the following
account :
- NULL session
- Guest account
- Given Credentials
Solution
n/a
See also
http://support.microsoft.com/support/kb/articles/Q143/4/74.ASP
http://support.microsoft.com/support/kb/articles/Q246/2/61.ASP
Risk Factor
None
Other references
OSVDB:297
OSVDB:3106
OSVDB:8230
OSVDB:10050
Plugin publication date: 2000/05/09
Plugin last modification date: 2011/03/21
Ease of exploitability: Exploits are available
Exploitable with: Metasploit (Microsoft Windows Authenticated User Code Execution)
Port ncacn_http (49157/tcp)
Plugin ID: 10761
COM+ Internet Services (CIS) Server Detection
Synopsis
A COM+ Internet Services (CIS) server is listening on this port.
List of Hosts Plugin Output
192.168.1.180
Server banner :
ncacn_http/1.0
Description
COM+ Internet Services are RPC over HTTP tunneling and require IIS to
operate. CIS ports shouldn't be visible on internet but only behind a
firewall.
Solution
If you do not use this service, disable it with DCOMCNFG.
Otherwise, limit access to this port.
See also
http://msdn.microsoft.com/library/en-us/dndcom/html/cis.asp
http://support.microsoft.com/support/kb/articles/Q282/2/61.ASP
Risk Factor
None
Plugin last modification date: 2011/03/21
Port (0/tcp)
Plugin ID: 11936
OS Identification
Synopsis
It is possible to guess the remote operating system
List of Hosts Plugin Output
192.168.1.180
Remote operating system : Microsoft Windows Server 2008 Service Pack 1
Confidence Level : 99
Method : MSRPC
The remote host is running Microsoft Windows Server 2008 Service Pack 1
Description
Using a combination of remote probes (TCP/IP, SMB, HTTP, NTP, SNMP, etc...)
it is possible to guess the name of the remote operating system in use, and
sometimes its version
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/17
Port (0/tcp)
Plugin ID: 35716
Ethernet Card Manufacturer Detection
Synopsis
The manufacturer can be deduced from the Ethernet OUI.
List of Hosts Plugin Output
192.168.1.180
The following card manufacturers were identified :
00:0c:29:9d:a1:c6 : VMware, Inc.
Description
Each ethernet MAC address starts with a 24-bit 'Organizationally
Unique Identifier'.
These OUI are registered by IEEE.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/27
Port ncacn_http (49157/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.180
An ncacn_http server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port www (8089/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output Plugin Output
192.168.1.180
A web server is running on this port through SSLv2.
192.168.1.180
An SSLv2 server answered on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port www (8000/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.180
A web server is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port http-rpc-epmap (593/tcp)
Plugin ID: 22964
Service Detection
Synopsis
The remote service could be identified.
List of Hosts Plugin Output
192.168.1.180
An http-rpc-epmap is running on this port.
Description
It was possible to identify the remote service by its banner or by looking
at the error message it sends when it receives an HTTP request.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/04/04
Port dns (53/tcp)
Plugin ID: 11002
DNS Server Detection
Synopsis
A DNS server is listening on the remote host.
List of Hosts
192.168.1.180
Description
The remote service is a Domain Name System (DNS) server, which
provides a mapping between hostnames and IP addresses.
Solution
Disable this service if it is not needed or restrict access to
internal hosts only if the service is available externally.
Risk Factor
None
Plugin last modification date: 2011/03/11
Port dce-rpc (49177/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49177 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 367abb81-9844-35f1-ad32-98f038001003, version 2.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49177
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49176/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49176 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 50abc2a4-574d-40b3-9d66-ee4fd5fba076, version 5.0
Description : DNS Server
Windows process : dns.exe
Type : Remote RPC service
TCP Port : 49176
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49163/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49163 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 6b5bdd1e-528c-422c-af8c-a4079be4fe48, version 1.0
Description : Unknown RPC service
Annotation : Remote Fw APIs
Type : Remote RPC service
TCP Port : 49163
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-0123456789ab, version 1.0
Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe
Annotation : IPSec Policy agent endpoint
Type : Remote RPC service
TCP Port : 49163
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49161/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49161 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc59b4-4264-101a-8c59-08002b2f8426, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs Service
Type : Remote RPC service
TCP Port : 49161
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : d049b186-814f-11d1-9a3c-00c04fc9b232, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs API
Type : Remote RPC service
TCP Port : 49161
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a00c021c-2be2-11d2-b678-0000f87a8f8e, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : PERFMON SERVICE
Type : Remote RPC service
TCP Port : 49161
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49158/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49158 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49158
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49158
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49155/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49155 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
TCP Port : 49155
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49154/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49154 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Remote RPC service
TCP Port : 49154
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49153/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49153 :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service
Annotation : Event log TCPIP
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.180
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Remote RPC service
TCP Port : 49153
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port dce-rpc (49152/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available on TCP port 49152 :
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
TCP Port : 49152
IP : 192.168.1.180
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port cifs (445/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available remotely :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service
Annotation : Unimodem LRPC Endpoint
Type : Remote RPC service
Named pipe : \pipe\tapsrv
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Remote RPC service
Named pipe : \PIPE\atsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Remote RPC service
Named pipe : \PIPE\srvsvc
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service
Annotation : Event log TCPIP
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Remote RPC service
Named pipe : \pipe\eventlog
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\InitShutdown
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Remote RPC service
Named pipe : \PIPE\InitShutdown
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \PIPE\protected_storage
Netbios name : \\WIN-8BPIQBRO0CX
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Remote RPC service
Named pipe : \pipe\lsass
Netbios name : \\WIN-8BPIQBRO0CX
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port epmap (135/tcp)
Plugin ID: 10736
DCE Services Enumeration
Synopsis
A DCE/RPC service is running on the remote host.
List of Hosts Plugin Output
192.168.1.180
The following DCERPC services are available locally :
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service
Annotation : Unimodem LRPC Endpoint
Type : Local RPC service
Named pipe : tapsrvlpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2f5f6521-cb55-1059-b446-00df0bce31db, version 1.0
Description : Unknown RPC service
Annotation : Unimodem LRPC Endpoint
Type : Local RPC service
Named pipe : unimdmsvc
Object UUID : 58abe70e-dc51-4f6c-917d-e8cc4f13e1fd
UUID : 906b0ce0-c70b-1067-b317-00dd010662da, version 1.0
Description : Distributed Transaction Coordinator
Windows process : msdtc.exe
Type : Local RPC service
Named pipe : LRPC-3fbda57d0c4803ba9c
Object UUID : 6971a2ac-7f04-4ec5-8d8d-d1d88ee83c48
UUID : 906b0ce0-c70b-1067-b317-00dd010662da, version 1.0
Description : Distributed Transaction Coordinator
Windows process : msdtc.exe
Type : Local RPC service
Named pipe : LRPC-3fbda57d0c4803ba9c
Object UUID : a3b8b0c1-7f58-4ac6-a858-05237e74d876
UUID : 906b0ce0-c70b-1067-b317-00dd010662da, version 1.0
Description : Distributed Transaction Coordinator
Windows process : msdtc.exe
Type : Local RPC service
Named pipe : LRPC-3fbda57d0c4803ba9c
Object UUID : 71ebac49-c98f-40cf-b969-28879f258965
UUID : 906b0ce0-c70b-1067-b317-00dd010662da, version 1.0
Description : Distributed Transaction Coordinator
Windows process : msdtc.exe
Type : Local RPC service
Named pipe : LRPC-3fbda57d0c4803ba9c
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-0123456789ab, version 1.0
Description : IPsec Services (Windows XP & 2003)
Windows process : lsass.exe
Annotation : IPSec Policy agent endpoint
Type : Local RPC service
Named pipe : LRPC-64636b2001baa70a54
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc59b4-4264-101a-8c59-08002b2f8426, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs Service
Type : Local RPC service
Named pipe : OLE4D00800FB7224E3BA74F6D7F4A40
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc59b4-4264-101a-8c59-08002b2f8426, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs Service
Type : Local RPC service
Named pipe : LRPC-32c9434230805de61a
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : d049b186-814f-11d1-9a3c-00c04fc9b232, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs API
Type : Local RPC service
Named pipe : OLE4D00800FB7224E3BA74F6D7F4A40
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : d049b186-814f-11d1-9a3c-00c04fc9b232, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : NtFrs API
Type : Local RPC service
Named pipe : LRPC-32c9434230805de61a
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a00c021c-2be2-11d2-b678-0000f87a8f8e, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : PERFMON SERVICE
Type : Local RPC service
Named pipe : OLE4D00800FB7224E3BA74F6D7F4A40
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a00c021c-2be2-11d2-b678-0000f87a8f8e, version 1.0
Description : File Replication Service
Windows process : ntfrs.exe
Annotation : PERFMON SERVICE
Type : Local RPC service
Named pipe : LRPC-32c9434230805de61a
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0b6edbfa-4a24-4fc6-8a23-942b1eca65d1, version 1.0
Description : Unknown RPC service
Annotation : Spooler function endpoint
Type : Local RPC service
Named pipe : spoolss
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : ae33069b-a2a8-46ee-a235-ddfd339be281, version 1.0
Description : Unknown RPC service
Annotation : Spooler base remote object endpoint
Type : Local RPC service
Named pipe : spoolss
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 4a452661-8290-4b36-8fbe-7f4093a94978, version 1.0
Description : Unknown RPC service
Annotation : Spooler function endpoint
Type : Local RPC service
Named pipe : spoolss
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : dd490425-5325-4565-b774-7e27d6c09c24, version 1.0
Description : Unknown RPC service
Annotation : Base Firewall Engine API
Type : Local RPC service
Named pipe : LRPC-eb9e1c5180d5c63bde
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 7f9d11bf-7fb9-436b-a812-b2d50c5d4c03, version 1.0
Description : Unknown RPC service
Annotation : Fw APIs
Type : Local RPC service
Named pipe : LRPC-eb9e1c5180d5c63bde
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 2fb92682-6599-42dc-ae13-bd2ca89bd11c, version 1.0
Description : Unknown RPC service
Annotation : Fw APIs
Type : Local RPC service
Named pipe : LRPC-eb9e1c5180d5c63bde
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service
Annotation : NSI server endpoint
Type : Local RPC service
Named pipe : OLEC78F635656704CF5919BEF8848AE
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 7ea70bcf-48af-4f6a-8968-6a440754d5fa, version 1.0
Description : Unknown RPC service
Annotation : NSI server endpoint
Type : Local RPC service
Named pipe : LRPC-ccb919c378b80e784b
Object UUID : 666f7270-6c69-7365-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 736e6573-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 736e6573-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 0a74ef1c-41a4-4e06-83ae-dc74fb1cdd53, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 1ff70682-0a51-30e8-076d-740be8cee98b, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 378e52b0-c0a9-11cf-822d-00aa0051e40f, version 1.0
Description : Scheduler Service
Windows process : svchost.exe
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 86d35949-83c9-4044-b424-db363231fd0c, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : IUserProfile2
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : senssvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : a398e520-d59a-4bdd-aa7a-3c1e0303a511, version 1.0
Description : Unknown RPC service
Annotation : IKE/Authip API
Type : Local RPC service
Named pipe : OLE632D1E20A0E64CE68DBBD5A11A70
Object UUID : 6c637067-6569-746e-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-3c4ccad02b6d68ae95
Object UUID : 24d1f7c7-76af-4f28-9ccd-7f6cb6468601
UUID : 2eb08e3e-639f-4fba-97b1-14f878961076, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : LRPC-3c4ccad02b6d68ae95
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f6beaff7-1e19-4fbb-9f8f-b89e2018337c, version 1.0
Description : Unknown RPC service
Annotation : Event log TCPIP
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d5, version 1.0
Description : DHCP Client Service
Windows process : svchost.exe
Annotation : DHCP Client LRPC Endpoint
Type : Local RPC service
Named pipe : dhcpcsvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : eventlog
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : dhcpcsvc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 3c4728c5-f0ab-448b-bda1-6ce01eb0a6d6, version 1.0
Description : Unknown RPC service
Annotation : DHCPv6 Client LRPC Endpoint
Type : Local RPC service
Named pipe : dhcpcsvc6
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000001
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc0C3841
Object UUID : 52ef130c-08fd-4388-86b3-6edf00000001
UUID : 12e65dd8-887f-41ef-91bf-8d816c42c2e7, version 1.0
Description : Unknown RPC service
Annotation : Secure Desktop LRPC interface
Type : Local RPC service
Named pipe : WMsgKRpc0C3841
Object UUID : 6d726574-7273-0076-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-e873bdd3ada3ba61b1
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc0C24C0
Object UUID : b08669ee-8cb5-43a5-a017-84fe00000000
UUID : 76f226c3-ec14-4325-8a99-6a46348418af, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WindowsShutdown
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WMsgKRpc0C24C0
Object UUID : 765294ba-60bc-48b8-92e9-89fd77769d91
UUID : d95afe70-a6d5-4259-822e-2c84da1ddb0d, version 1.0
Description : Unknown RPC service
Type : Local RPC service
Named pipe : WindowsShutdown
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : audit
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00736665-0000-0000-0000-000000000000
UUID : c9ac6db5-82b7-4e55-ae8a-e464ed7b4277, version 1.0
Description : Unknown RPC service
Annotation : Impl friendly name
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : e3514235-4b06-11d1-ab04-00c04fc2dcd2, version 4.0
Description : Active Directory Replication Interface
Windows process : unknown
Annotation : MS NT Directory DRS Interface
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : f5cc5a18-4264-101a-8c59-08002b2f8426, version 56.0
Description : Active Directory Name Service Provider (NSP)
Windows process : unknown
Annotation : MS NT Directory NSP Interface
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ab, version 0.0
Description : Local Security Authority
Windows process : lsass.exe
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : audit
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : securityevent
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : protected_storage
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : dsrole
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : samss lpc
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : OLE062236B4F0EA45649DC7BB39D665
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345778-1234-abcd-ef00-0123456789ac, version 1.0
Description : Security Account Manager
Windows process : lsass.exe
Type : Local RPC service
Named pipe : NTDS_LPC
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : LRPC-d0c914802ad9e55611
Object UUID : 00000000-0000-0000-0000-000000000000
UUID : 12345678-1234-abcd-ef00-01234567cffb, version 1.0
Description : Network Logon Service
Windows process : lsass.exe
Type : Local RPC service
Named pipe : audit
Description
By sending a Lookup request to the portmapper (TCP 135 or epmapper
PIPE) it was possible to enumerate the Distributed Computing Environment
(DCE) services running on the remote port.
Using this information it is possible to connect and bind to
each service by sending an RPC request to the remote port/pipe.
Solution
N/A
Risk Factor
None
Plugin last modification date: 2011/03/04
Port www (8000/tcp)
Plugin ID: 39463
HTTP Server Cookies Set
Synopsis
Some cookies have been set by the web server.
List of Hosts Plugin Output
192.168.1.180
path = /
name = cval
value = 1184393488
version = 1
secure = 0
httponly = 0
path = /
name = session_id_8000
value = 3d1e277d48e7b0dd16377f65bc1dac5155fd0c78
version = 1
expires = Fri, 25 Mar 2011 04:02:30 GMT
secure = 0
httponly = 0
Description
HTTP cookies are pieces of information that are presented by web
servers and are sent back by the browser.
As HTTP is a stateless protocol, cookies are a possible mechanism to
keep track of sessions.
This plugin displays the list of the HTTP cookies that were set by the
web server when it was crawled.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/15
Port (0/tcp)
Plugin ID: 45590
Common Platform Enumeration (CPE)
Synopsis
It is possible to enumerate CPE names that matched on the remote
system.
List of Hosts Plugin Output
192.168.1.180
The remote operating system matched the following CPE :
cpe:/o:microsoft:windows_server_2008::sp1
Description
By using information obtained from a Nessus scan, this plugin reports
CPE (Common Platform Enumeration) matches for various hardware and
software products found on a host.
Note that if an official CPE is not available for the product, this
plugin computes the best possible CPE based on the information
available from the scan.
Solution
n/a
See also
http://cpe.mitre.org/
Risk Factor
None
Plugin last modification date: 2011/03/08
Port www (8089/tcp)
Plugin ID: 51891
SSL Session Resume Supported
Synopsis
The remote host allows resuming SSL sessions.
List of Hosts Plugin Output
192.168.1.180
This port supports resuming SSLv3/TLSv1 sessions.
Description
This script detects whether a host allows resuming SSL sessions by
performing a full SSL handshake to receive a session ID, and then
reconnecting with the previously used session ID. If the server
accepts the session ID in the second connection, the server maintains
a cache of sessions that can be resumed.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port (0/icmp)
Plugin ID: 10114
ICMP Timestamp Request Remote Date Disclosure
Synopsis
It is possible to determine the exact time set on the remote host.
List of Hosts Plugin Output
192.168.1.180
This host returns non-standard timestamps (high bit is set)
The ICMP timestamps might be in little endian format (not in network format)
The difference between the local and remote clocks is 38481 seconds.
Description
The remote host answers to an ICMP timestamp request. This allows an
attacker to know the date which is set on your machine.
This may help him to defeat all your time based authentication
protocols.
Solution
Filter out the ICMP timestamp requests (13), and the outgoing ICMP
timestamp replies (14).
Risk Factor
None
CVE
CVE-1999-0524
Plugin publication date: 1999/08/01
Plugin last modification date: 2011/03/21
Port ldap (389/tcp)
Plugin ID: 25701
LDAP Crafted Search Request Server Information Disclosure
Synopsis
It is possible to discover information about the remote LDAP server.
List of Hosts Plugin Output
192.168.1.180
[+]-namingContexts:
| DC=tx,DC=hec,DC=net
| CN=Configuration,DC=tx,DC=hec,DC=net
| CN=Schema,CN=Configuration,DC=tx,DC=hec,DC=net
| DC=DomainDnsZones,DC=tx,DC=hec,DC=net
| DC=ForestDnsZones,DC=tx,DC=hec,DC=net
Description
By sending a search request with a filter set to 'objectClass=*', it
is possible to extract information about the remote LDAP server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port cifs (445/tcp)
Plugin ID: 10785
Microsoft Windows SMB NativeLanManager Remote System Information Disclosure
Synopsis
It is possible to obtain information about the remote operating
system.
List of Hosts Plugin Output
192.168.1.180
The remote Operating System is : Windows Server (R) 2008 Standard 6001 Service Pack 1
The remote native lan manager is : Windows Server (R) 2008 Standard 6.0
The remote SMB Domain Name is : TX
Description
It is possible to get the remote operating system name and
version (Windows and/or Samba) by sending an authentication
request to port 139 or 445.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/17
Port www (8000/tcp)
Plugin ID: 10662
Web mirroring
Synopsis
Nessus crawled the remote web site.
List of Hosts Plugin Output
192.168.1.180
The following CGI have been discovered :
Syntax : cginame (arguments [default value])
/en-US/account/login (username [] return_to [/en-US/] cval [1184393488] password [] )
Description
This script makes a mirror of the remote web site(s) and extracts the
list of CGIs that are used by the remote host.
It is suggested that you change the number of pages to mirror in the
'Options' section of the client.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/31
Port (88/tcp)
Plugin ID: 43829
Kerberos Information Disclosure
Synopsis
The remote Kerberos server is leaking information.
List of Hosts Plugin Output
192.168.1.180
Nessus gathered the following information :
Server time : 2011-03-24 04:02:04 UTC
Realm : TX.HEC.NET
Description
Nessus was able to retrieve the realm name and/or server time of the
remote Kerberos server.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port cifs (445/tcp)
Plugin ID: 11011
Microsoft Windows SMB Service Detection
Synopsis
A file / print sharing service is listening on the remote host.
List of Hosts Plugin Output
192.168.1.180
A CIFS server is running on this port.
Description
The remote service understands the CIFS (Common Internet File System)
or Server Message Block (SMB) protocol, used to provide shared access
to files, printers, etc between nodes on a network.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port smb (139/tcp)
Plugin ID: 11011
Microsoft Windows SMB Service Detection
Synopsis
A file / print sharing service is listening on the remote host.
List of Hosts Plugin Output
192.168.1.180
An SMB server is running on this port.
Description
The remote service understands the CIFS (Common Internet File System)
or Server Message Block (SMB) protocol, used to provide shared access
to files, printers, etc between nodes on a network.
Solution
n/a
Risk Factor
None
Plugin last modification date: 2011/03/11
Port www (8000/tcp)
Plugin ID: 26194
Web Server Uses Plain Text Authentication Forms
Synopsis
The remote web server might transmit credentials in cleartext.
List of Hosts Plugin Output
192.168.1.180
Page : /en-US/account/login
Destination page : /en-US/account/login
Input name : password
Description
The remote web server contains several HTML form fields containing
an input of type 'password' which transmit their information to
a remote web server in cleartext.
An attacker eavesdropping the traffic between web browser and
server may obtain logins and passwords of valid users.
Solution
Make sure that every sensitive form transmits content over HTTPS.
Risk Factor
Medium/ CVSS Base Score: 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Plugin last modification date: 2011/03/18
| 192.168.1.180 | |
|---|---|
| Scan Time | |
| Start time: | Wed Apr 6 10:53:51 2011 |
| End time: | Wed Apr 6 10:57:02 2011 |
| Number of vulnerabilities | |
| High | 2 |
| Medium | 5 |
| Low | 49 |
| Remote Host Information | |
| Operating System: | Microsoft Windows Server 2008 Service Pack 1 |
| NetBIOS name: | WIN-8BPIQBRO0CX |
| MAC address: | 00:0c:29:9d:a1:c6 |